Andre M. DiMino
@sempersecurus
Researcher w/ DeepEnd Research == DFIR, cybercrime, threat intelligence, malware & exploit studies. 1:Thess. 5:15 ✝ Open DMs
你可能會喜歡
"Prosecutors allege incident response pros used ALPHV/BlackCat to commit string of ransomware attacks" The trio are accused of carrying out the conspiracy from May 2023 through April 2025 cyberscoop.com/incident-respo…
The Smishing Triad's extensive, global phishing campaign exploits SMS messages to impersonate critical sectors - Campaign targets U.S. residents, expanding globally since April 2024. - Over 194,000 malicious domains identified, using decentralized infrastructure. - Aims to…
Official Xubuntu website compromised to serve malware helpnetsecurity.com/2025/10/21/xub…
A quarterly reminder that ransomware threat landscape is still growing and the 🇺🇸USA is the primary target of such attacks. 🧵1/4

Today, the @SecretService announced the dismantling of a network of electronic devices—located within 35 miles of the United Nations General Assembly—used to carry out a wide range of telecommunications attacks. The potential for disruption to our country’s telecommunications…
The Secret Service dismantled a network of more than 300 SIM servers and 100,000 SIM cards in the New York-area that were capable of crippling telecom systems and carrying out anonymous telephonic attacks, disrupting the threat before world leaders arrived for the UN General…



As we do every year, it is with a heavy heart that we pause to honor the lives lost and the families forever changed September 11, 2001. However, we are always grateful for the courage of first responders and the unity of our Nation in the face of unthinkable tragedy.…

People on here act like someone decides not to patch. Like there’s a guy who knows the service is vulnerable, knows it runs in prod, and just shrugs. That’s maybe 1% of the cases. The rest is messier: - No idea the service exists (no inventory) - No idea it’s vulnerable (no vuln…
A few days back at #DEFCON, I released the Garuda Threat Hunting Framework — crafted for manual threat hunting & detection. Here is the link: github.com/monnappa22/Gar… When integrated with LLMs, it enables AI-powered autonomous threat hunting. youtu.be/Sk_c5w1CEiY

youtube.com
YouTube
AI-Powered Threat Hunting Using Garuda Framework
"Clorox lawsuit says help-desk contractors handed over passwords in 2023 cyberattack" therecord.media/clorox-cyberat…
Write-up on our perspective at #Censys on ToolShell / CVE-2025-53770 exploit in SharePoint: censys.com/advisory/cve-2…

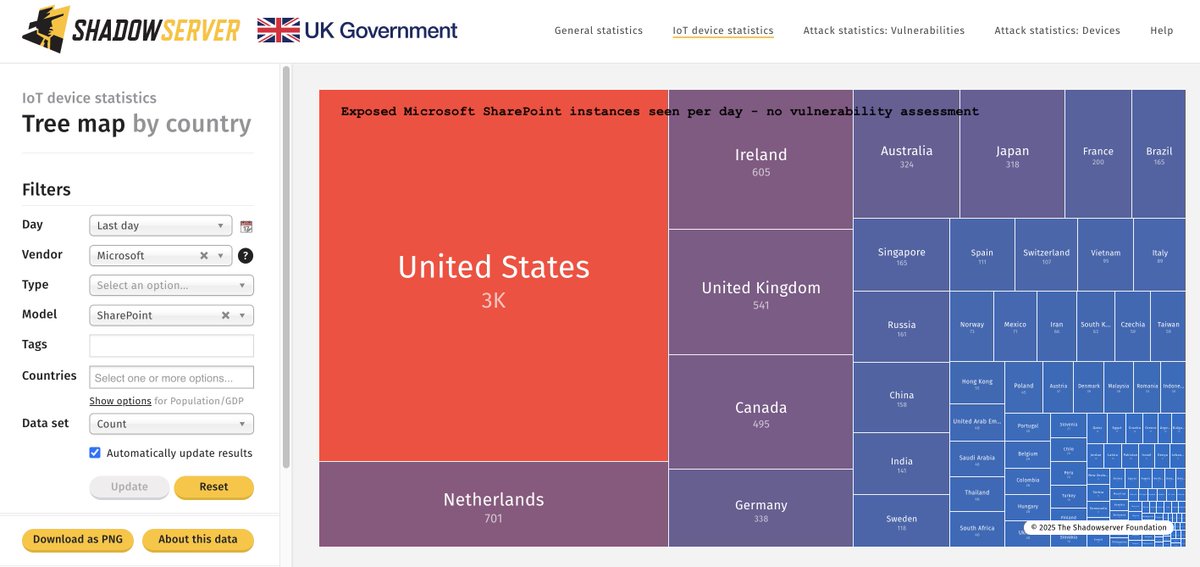
Alert: SharePoint CVE-2025-53770 incidents! In collaboration with @eyesecurity & @watchtowrcyber we are notifying compromised parties. Read: research.eye.security/sharepoint-und… ~9300 Sharepoint IPs seen exposed daily (just population, no vulnerability assessment): dashboard.shadowserver.org/statistics/iot…
"How China’s Patriotic ‘Honkers’ Became the Nation’s Elite Cyberspies" A new report traces the history of the early wave of Chinese hackers who became the backbone of the state's espionage apparatus. wired.com/story/china-ho…
If I were a threat actor, I'd live in Linux audio and video drivers. Nobody wants to patch them. Because doing so turns your stable box into a haunted carnival ride.
"US agencies assessed Chinese telecom hackers likely hit data center and residential internet providers" nextgov.com/cybersecurity/…
nextgov.com
US agencies assessed Chinese telecom hackers likely hit data center and residential internet...
Data center giant Digital Realty and mass media titan Comcast were documented as likely victims of the Salt Typhoon cyberespionage group, people familiar say, marking a potentially major expansion of...
It's a shame too. Blue Team is infinitely more interesting. I have deep respect and admiration for people who do DFIR, SOC, and DEVSECOPS, etc. I've learned more from defensive approaches than I have offensive. Blue Team just isn't as "flashy".
So, what just happened with the CVE program? - MITRE drops a letter saying funding ends tomorrow - Everyone panics, assumes no more CVE numbers - The community scrambles to organize - The CVE Foundation appears, positioned as a vendor-neutral non-profit - We all learn MITRE has…
Quinlan’s post hits the nail on the head - most SOC analysts are stuck doing monotonous work that’s far below their true potential. Watching endless alerts is mind-numbing; let’s be honest, a machine should do that. I totally agree with her point about the value of giving…

Anyone know anything about these? 134.122.197.17 eagleeyelegalservices [.] com ccapital-pros [.] com financednx-esomi [.] com ccapitalvips [.] com financednxesomi [.] com skyeyeattorneys [.] com skyeyelegal [.] com skyeyeassistance [.] com pisces-vips [.] com interactivebroker-us…
![sempersecurus's tweet image. Anyone know anything about these?
134.122.197.17
eagleeyelegalservices [.] com
ccapital-pros [.] com
financednx-esomi [.] com
ccapitalvips [.] com
financednxesomi [.] com
skyeyeattorneys [.] com
skyeyelegal [.] com
skyeyeassistance [.] com
pisces-vips [.] com
interactivebroker-us…](https://pbs.twimg.com/media/GmaJU28WMAAJWqu.jpg)
"Everything you say to your Echo will be sent to Amazon starting on March 28" arstechnica.com/gadgets/2025/0…
United States 趨勢
- 1. Seahawks 19.4K posts
- 2. Giants 65.5K posts
- 3. Bills 133K posts
- 4. Bears 58.3K posts
- 5. Caleb 47.6K posts
- 6. Dolphins 32K posts
- 7. Dart 25.3K posts
- 8. Daboll 11.2K posts
- 9. Jags 6,560 posts
- 10. Josh Allen 15.4K posts
- 11. Texans 37.2K posts
- 12. Russell Wilson 3,888 posts
- 13. Browns 36.9K posts
- 14. Rams 15.6K posts
- 15. Patriots 104K posts
- 16. Ravens 36.9K posts
- 17. Trevor Lawrence 2,438 posts
- 18. Henderson 16.9K posts
- 19. Bryce 15.4K posts
- 20. Drake Maye 15.5K posts
你可能會喜歡
-
 Seongsu Park
Seongsu Park
@unpacker -
 Bart
Bart
@bartblaze -
 Kimberly
Kimberly
@StopMalvertisin -
 Xylitol
Xylitol
@Xylit0l -
 Danny Quist
Danny Quist
@OpenMalware -
 Michael Ligh (MHL)
Michael Ligh (MHL)
@iMHLv2 -
Xavier Mertens @[email protected] 🇧🇪
@xme -
 Willi Ballenthin
Willi Ballenthin
@williballenthin -
 Jamie Levy🦉
Jamie Levy🦉
@gleeda -
 Evilcry_
Evilcry_
@Blackmond_ -
 The Shadowserver Foundation
The Shadowserver Foundation
@Shadowserver -
 Brian Baskin
Brian Baskin
@bbaskin -
 Giuseppe `N3mes1s`
Giuseppe `N3mes1s`
@gN3mes1s -
 Andrew Case
Andrew Case
@attrc -
Security4all
@security4all
Something went wrong.
Something went wrong.


















































































































































