You might like
Hey, what's up folks? 10 years ago I signed up on Twitter how quickly time passes
Mining cryptocurrency with energy from the solar rays of the Sun, bouncing our packets through the ionosphere w/@Jennifer_Arcuri



If you are hard at work scanning the internet for CVE-2021-41773 (apache 2.4.49 path traversal thing).. also try /icons instead of just /cgi-bin, enjoy the increased success rate. :-P
How malware gets into the App Store and why Apple can't stop that #MobileSecurity #iOSsecurity by @illusionofcha0s habr.com/ru/amp/post/58…
Out of bounds write in V8 | Tested against Samsung Internet Browser v15.0.2.47, which does not yet have Google's patch (PoC CVE-2021-30632) #MobileSecurity #AndroidSecurity by @Zeusb0x pastebin.com/wCNA6UAB
Cool Windows Internals trick I found over the weekend. If you name a folder "anything.{D2035EDF-75CB-4EF1-95A7-410D9EE17170}", Explorer will crash when you try to enter that folder.
Ever wondered which flags you should use for your C compiler to: - detect the maximum number of bugs or potential security problems? - enable security mitigations in binaries? - enable runtime sanitizers? We got you covered for GCC, Clang and MSVC! airbus-seclab.github.io/c-compiler-sec…

I've published the article covering my talk at @ZeroNights! Improving the exploit for CVE-2021-26708 in the Linux kernel to bypass LKRG a13xp0p0v.github.io/2021/08/25/lkr… Slides: a13xp0p0v.github.io/img/CVE-2021-2… PoC exploit demo video: youtube.com/watch?v=O6rsuG… Enjoy!

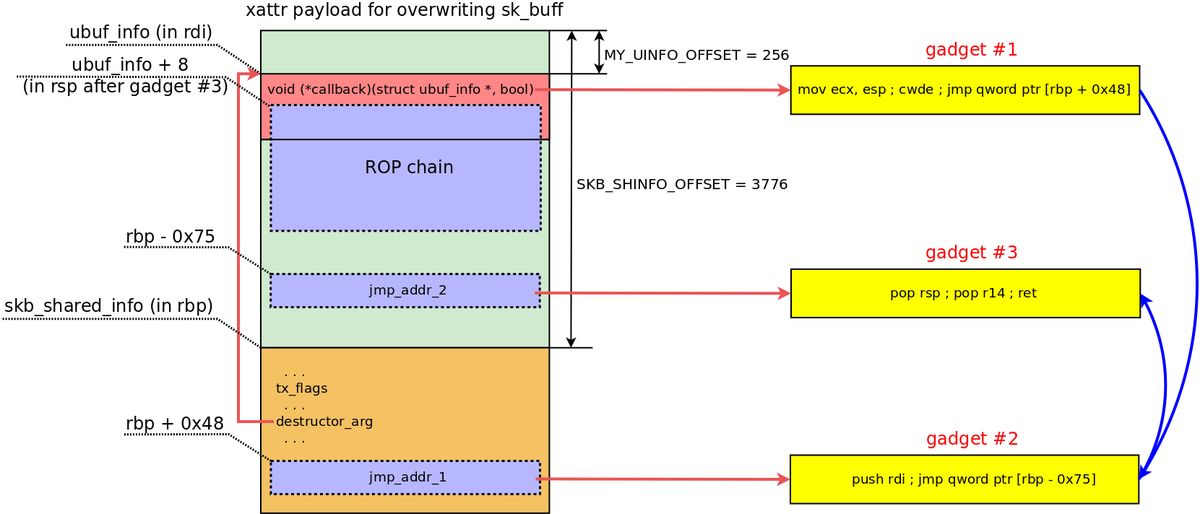

Ever wanted to exploit Windows 10 with CVE-2021-31956? Obsessive about kernel memory layouts? research.nccgroup.com/2021/08/17/cve… is now up focusing on exploit reliability, stability and detection! #windows
Blog: CVE-2021-31956 Exploiting the Windows Kernel (NTFS with WNF) - Part 2 - including thoughts on detection by @alexjplaskett research.nccgroup.com/2021/08/17/cve…
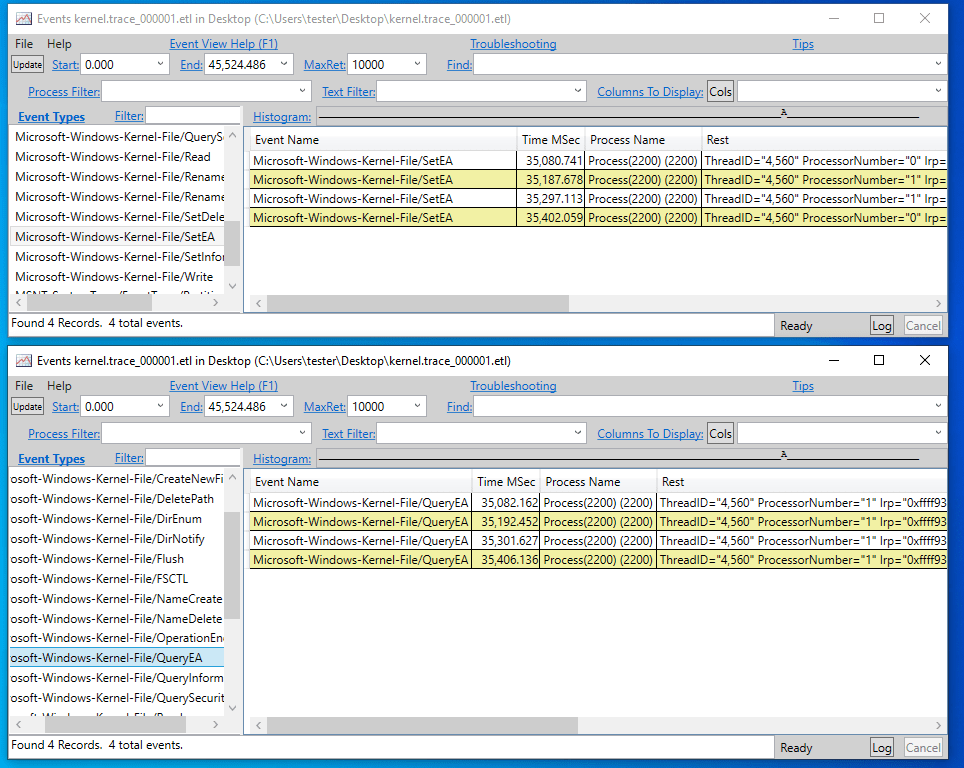
Here is my PoC for exploiting the @Razer device driver installation LPE using a generic Android phone instead of a stock Razer device. gist for the gadget setup: gist.github.com/tothi/3cdec3ac… Original version using a Razer device was presented by @j0nh4t. Awesome finding, I like it.
curious how Android phones interact with embedded hardware (camera, sensors, etc) natively? libhardware tests show how it’s done. why does this matter? APTs persist (or re-exploit) as root and *not* as an individual app. it’s much harder to detect. android.googlesource.com/platform/hardw…
Google CTF Fullchain has been a good opportunity for me to learn PartitionAlloc and Chrome SBX. We did not solve the challenge in time, but finished it nonetheless. Find our write-up (with @ntrung03) here! ret2.life/posts/Google-C… trungnguyen1909.github.io/blog/post/GGCT…
I wrote a 1day exploit for chrome CVE-2020-16040. It includes a typer hardening bypass. Works for chrome version <= 87.0.4280.88 github.com/r4j0x00/exploi…

CVE-2021-1732 Exploit Windows Win32k Elevation of Privilege Vulnerability github.com/KaLendsi/CVE-2… Poc & Exp report: bbs.pediy.com/thread-266362.…

Patch sudo. (Have backups prepped just in case you, you know, break everything) wget sudo.ws/dist/sudo-1.9.… tar xzvf sudo-1.9.5p2.tar.gz cd sudo-1.9.5p2 ./configure make && sudo make install bash -c "sudo --version"
Google's ReCAPTCHA will automatically fingerprint Burp Suite Proxy and raise the challenge difficulty to the maximum, making analysis of the app very irritating. To fix this, go into your Burp Suite Project Configurations and activate TLS Passthrough for google.com

[UPDATE] AppSync Unified 90.0 — Massive rewrite of AppSync Unified that now fully supports all current iOS 14.x versions, while also improving the experience for all other iOS versions (even iOS 5/6!) reddit.com/r/jailbreak/co…
do you want to know about? integer overflow integer underflow Out of bound Read Out of bound Write Double Free Use After Free Memory leaks here is the damn vulnerable c program i coded to explain AFL fuzzing in my videos: github.com/hardik05/Damn_… fuzz it using AFL and see :)
We've confirmed exploitability of Windows Pre-Auth RDP bug (CVE-2019-0708) patched yesterday by Microsoft. Exploit works remotely, without authentication, and provides SYSTEM privileges on Windows Srv 2008, Win 7, Win 2003, XP. Enabling NLA mitigates the bug. Patch now or GFY!
United States Trends
- 1. Good Wednesday 24.7K posts
- 2. #wednesdaymotivation 2,011 posts
- 3. Hump Day 8,210 posts
- 4. Immanuel 2,894 posts
- 5. Oslo 251K posts
- 6. #MerryChristmasJustin 7,207 posts
- 7. Happy Hump 5,417 posts
- 8. #ดีว่าราวีวันนี้ในโรงภาพยนตร์ 599K posts
- 9. #FairiesLingOrmAtTheMall 295K posts
- 10. LINGORM CHRISTMAS FAIRIES 258K posts
- 11. María Corina Machado 206K posts
- 12. percy 27.8K posts
- 13. #HumanRightsDay 20.3K posts
- 14. Therefore the Lord 1,826 posts
- 15. Waffle House 2,876 posts
- 16. grover 3,346 posts
- 17. annabeth 8,681 posts
- 18. clarisse 1,660 posts
- 19. Nobel de la Paz 174K posts
- 20. Gowdy 6,394 posts
You might like
-
 Donato Scaramuzzo
Donato Scaramuzzo
@ramirezVII -
 Seongsu Park
Seongsu Park
@unpacker -
 G. Geshev
G. Geshev
@munmap -
 Giuseppe `N3mes1s`
Giuseppe `N3mes1s`
@N3mes1s -
 Ivan at Wallarm / API security solution
Ivan at Wallarm / API security solution
@d0znpp -
 Ionut Popescu
Ionut Popescu
@NytroRST -
 maldevel ☣
maldevel ☣
@maldevel -
 Evilcry_
Evilcry_
@Blackmond_ -
 Кириакос Экономоу
Кириакос Экономоу
@kyREcon -
 Chris Mallz
Chris Mallz
@vvalien1 -
 TinySec
TinySec
@TinySecEx -
 invisiblebyte
invisiblebyte
@invisiblebyte -
 emdel
emdel
@emd3l -
 Ronnie Salomonsen bsky @r0ns3n.dk
Ronnie Salomonsen bsky @r0ns3n.dk
@r0ns3n -
 TS-WAY 🇮🇹
TS-WAY 🇮🇹
@TS_WAY_SRL
Something went wrong.
Something went wrong.