Sparc Flow
@sparcFlow
H4cker, author of How to Hack Like a Pornstar http://amazon.com/dp/B01MTDLGQQ & How to Hack Like a Ghost http://amazon.com/dp/B08FH9SQNG https://sparcflow.substack.com
قد يعجبك
My new book Blitzscaling Security is now available. Dive into the mind of Alex, the first security engineer at a scale-up, & experience the brutal truth behind designing a security that protects and boosts the business The gloves are off with this one :) amazon.com/dp/B0C4LC4FDW
Docker probably did more for Security than half of the “security products” out there.
If Security is known as the “no department,” it loses credibility and value to execs. Reframe every “can we” into “how can we,” and you go from hall monitor to business enabler. From buzzkill to visionary. That's how you make Security matter.
Security metrics are vanity dashboards: vuln counts, patch SLAs, compliance scores. You're grading paperwork. Measure attacker economics instead: minutes to first signal, time-to-contain, single-cred blast radius. If it doesn't change an op, drop it
Bug bounties were supposed to bridge researchers and companies. Instead, low-effort mass submitters have turned them into inbox noise of "critical open redirect" reports.
Outsourcing your SOC = outsourcing your security. At that point, you’re just renting alerts, not owning defense.
Cybersecurity isn’t just about walls, it’s about funnels. Good hardening doesn’t block everything, it forces attackers down a path you control. That path should be full of traps.
People worry that chatgpt will replace search. There is a good to fair chance it replaces the whole Web. « Wire $100 from my Chase account to Sylvia » « Send an emall to John » Etc. The internet will be the current brick and mortar. For old people that still remember the « good…
Shopify merchants will be able to sell directly in ChatGPT. We’ve been working with @OpenAI for quite some time so people can search and buy products in chat, and it’s something we’ve had a hard time keeping quiet. Rollout is coming very very soon.
In security, doing the work is hard. Proving you did the work to a skeptical auditor/regulator ? 100x harder. That’s why compliance devolves into checkboxes and process theater.
Security compliance is great, but it can also become terrible. It starts from a good place of "Are you doing the right things" but once it devolves into checkboxes and checklists, and a lack of using your own risk judgement, then all bets are off.
In a world of ever-smarter AI models, I don’t get MCPs. Why build & maintain two APIs when the model can read the docs and call the one you already have? The future belongs to smarter models, not more plumbing.
C makes it easy to shoot yourself in the foot. assembly makes it hard to miss.
AWS tip: Use VPC Endpoints (vpce). ✅ Restrict IAM policies to your endpoint ✅ Spot attempts coming from outside your infra ✅ Save $$ on egress traffic Protection + detection + cost reduction.
Cybersecurity isn’t just about walls, it’s about funnels. Good hardening doesn’t block everything, it forces attackers down a path you control. That path should be full of traps.
Replace CEO with CISO and CFO/Marketing with Compliance and it would be perfectly true for Cybersecurity as well….or any field for that matter. Can’t lead and consistently build decent strategies without care and expertise.
"It takes ten years for the culture of a great company to fall apart once the CEO seat is given to someone without an engineering or product background. That's been the story of Boeing, Intel, and now Apple." world.hey.com/dhh/the-great-…
Insane because Microsoft uses a tool like dnstwist to find lookalike domains in Defender for Office 365... but you have to pay for it The good news is this tool is FREE, so everyone can and should monitor for lookalike domains: dnstwist.it github.com/elceef/dnstwist
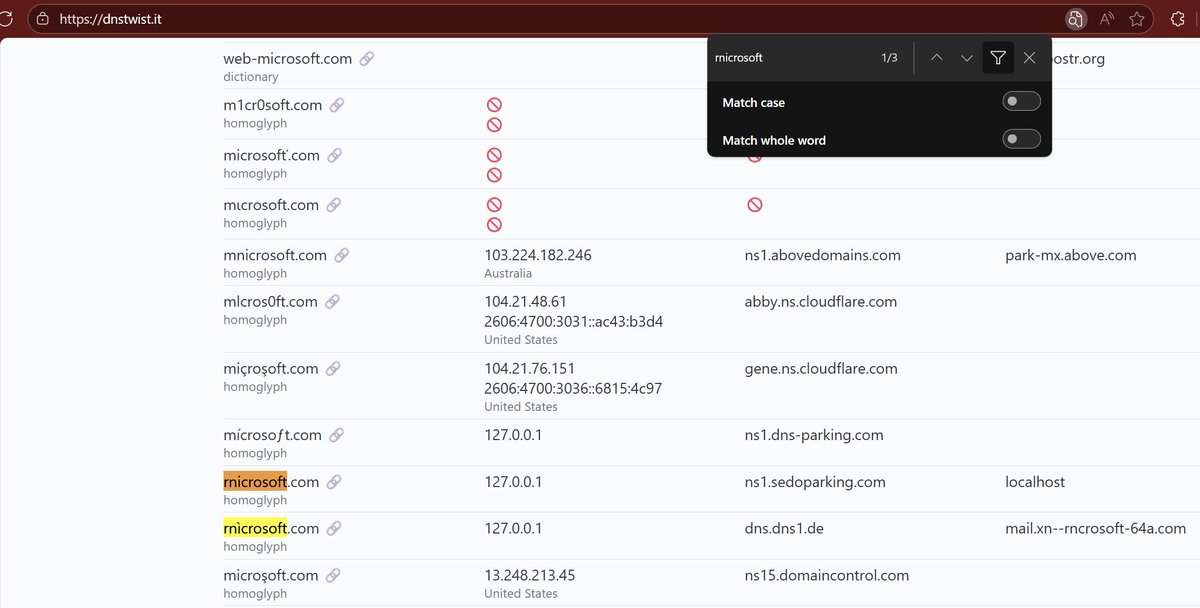
Crazy stuff that I saw online! 😂 rnicrosoft 🔥

The most powerful security principle i know : defense in depth. i.e, at least two or more security layers on any threat path. * Password + MFA for employees * Bearer/Oauth Token + IP whitelisting * WAF + Static code analysis + rootless prod environment * VPN + app authentication…
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
Let’s talk about npm and package registries. How do you deal with infected dependencies ? * L1: dependabot/renovatebot to wait 7 days before pulling a release * L2: disable lifecycle scripts if possible * L3: CI running in a tight env with egress filtering, auditd/falco, job…
SOC should spend more time on detection engineering and siem tuning than on treating alerts. Yet somehow we normalized an army of juniors treating noise 24/7 and then wonder why they missed that one signal that one time
United States الاتجاهات
- 1. Jets 98.4K posts
- 2. Jets 98.4K posts
- 3. Justin Fields 18K posts
- 4. Aaron Glenn 7,369 posts
- 5. London 204K posts
- 6. Sean Payton 3,438 posts
- 7. George Pickens 1,525 posts
- 8. Tyler Warren 1,689 posts
- 9. Garrett Wilson 4,451 posts
- 10. Jerry Jeudy N/A
- 11. Bo Nix 4,517 posts
- 12. #Pandu N/A
- 13. #HardRockBet 3,591 posts
- 14. Tyrod 2,498 posts
- 15. HAPPY BIRTHDAY JIMIN 191K posts
- 16. #DENvsNYJ 2,567 posts
- 17. #JetUp 2,547 posts
- 18. #HereWeGo 1,867 posts
- 19. Waddle 1,915 posts
- 20. Pop Douglas N/A
قد يعجبك
-
 Will Schroeder
Will Schroeder
@harmj0y -
 Zero-Point Security
Zero-Point Security
@_ZeroPointSec -
 Beau Bullock
Beau Bullock
@dafthack -
 SpecterOps
SpecterOps
@SpecterOps -
 Matt Hand
Matt Hand
@matterpreter -
 Steven
Steven
@0xthirteen -
 LuemmelSec
LuemmelSec
@theluemmel -
 Swissky
Swissky
@pentest_swissky -
 Pixis
Pixis
@HackAndDo -
 BC Security
BC Security
@bcsecurity -
 Patrick Wardle
Patrick Wardle
@patrickwardle -
 mpgn
mpgn
@mpgn_x64 -
 Ryan Cobb
Ryan Cobb
@cobbr_io -
 ippsec
ippsec
@ippsec -
 Mr.Un1k0d3r
Mr.Un1k0d3r
@MrUn1k0d3r
Something went wrong.
Something went wrong.