#cybersecurity search results
🔒 October is Cybersecurity Awareness Month! Understanding cybersecurity is crucial as cyberattacks become more common. 🧟💻 From malware to phishing, learn how to protect yourself with our essential tips: experian.com/blogs/ask-expe… #Cybersecurity #StaySafeOnline…

The 12 Pillars of Cyber Security! 🛡️ Know your defense: from Encryption to API Security. Are you covering all 12? #CyberSecurity #InfoSec #SecurityFramework #digitalearn #DevOps

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

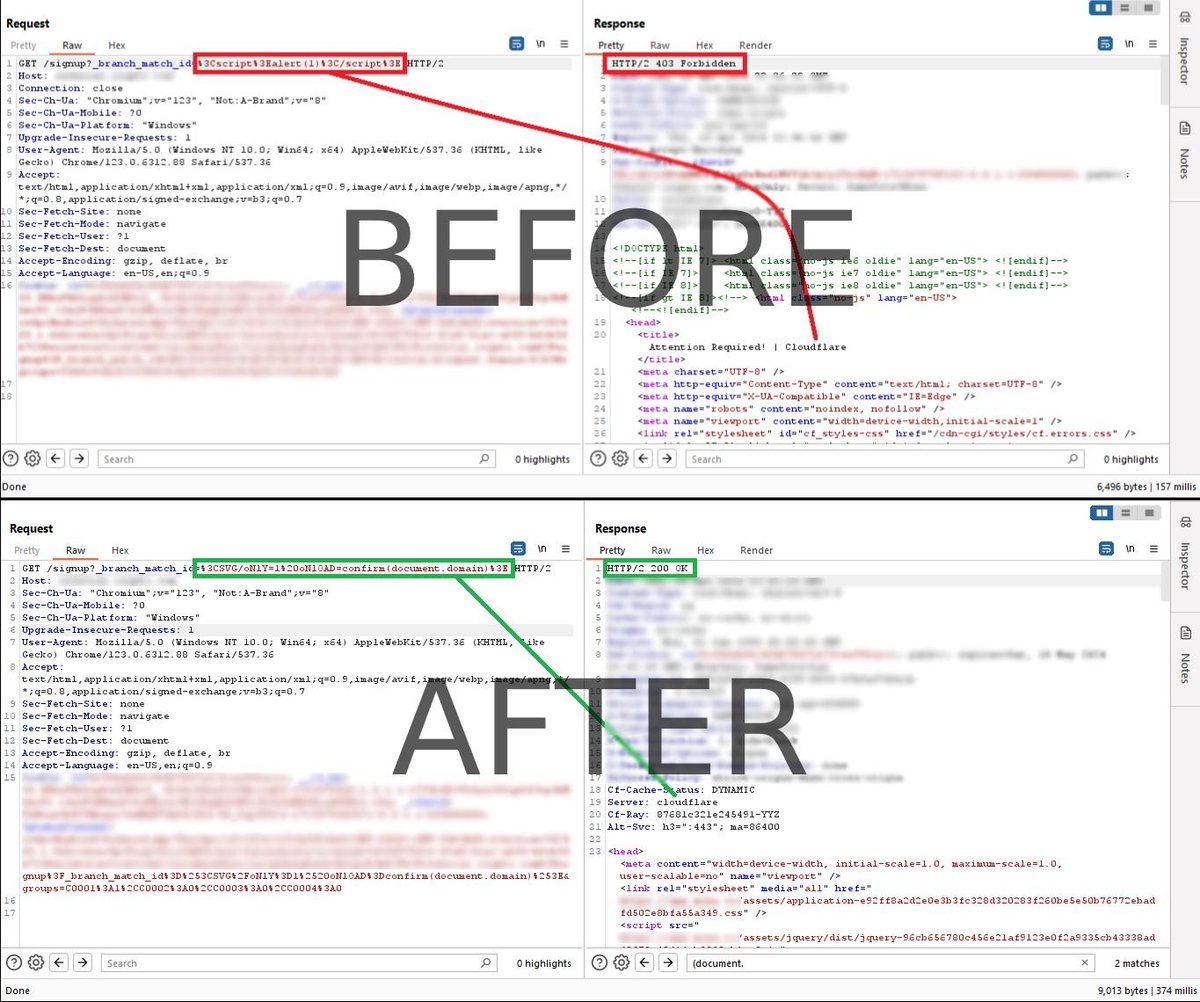
New XSS Bypass Cloudflare WAF 🧱 Payload : %3CSVG/oNlY=1%20ONlOAD=confirm(document.domain)%3E #BugBounty #XSS #Cybersecurity
Free Udemy #CyberSecurity Course Collection Access 30+ Video Courses and 1000 TB of Resources You will get: 💼 Cybersecurity 💼 Ethical Hacking 💼 Penetration Testing 💼 Many more To get access, simply: 1. Like & Retweet 2. Comment “Send” 3. Follow me (So I can DM you)

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

The grep command is like a spotlight for text. It instantly finds words, phrases, or patterns inside files or streams. Here is a quick grep cheatsheet 😎👇 Find pdf books with all my #Linux and #cybersecurity related infographics from study-notes.org

#CybersecurityAwarenessMonth - Seit über 20 Jahren steht der Oktober im Zeichen der #Cybersecurity. #CSAM - Software updaten, um Angriffsfläche zu reduzieren Ziel des Aktionsmonat ist es die Anwender über mögliche Bedrohungen aufzuklären. Dazu hat auch Netzpalaver einige…
The /proc filesystem in Linux is a virtual gateway to real-time system info, from hardware stats to kernel params, letting you monitor and tweak system on the fly 😎👇 Find pdf books with all my #Linux and #cybersecurity related infographics from study-notes.org

🚨 One of the most critical vulnerabilities I’ve found: ~50K records leaked — PII including names, phone numbers, addresses, order details, and more. Always look for misconfigured buckets and open storage. #BugBounty #CyberSecurity #DataLeak #InfoSec

🌍 @discord faces extortion after a Zendesk breach exposed 1.5 TB of data, including 2.18M age verification photos. Threat actors are selectively leaking info tied to users like Tyler Robinson. ~70,000 government ID photos may be compromised. #CyberSecurity #DataBreach…

Here’s What CEOs Need to Tell #Board Members About #Cybersecurity > buff.ly/t1Ok0ox #tech #security #cyberthreats #cyberattacks #databreaches #business #leadership #management #governance #regulation #compliance #GRC #CISO #CIO #CTO #CEO

Every click counts! 💻 Be cautious online — don’t reuse passwords, avoid unknown friend requests, and log out from shared devices. #CyberJagritBharat #IndianCERT #Cybersecurity #DigitalIndia #CSK

AI is replacing traditional coding with no-code programming solutions. #NoCode #FutureOfWork AI-enhanced cybersecurity systems are preventing global cyberattacks. #CyberSecurity #AIProtection
🔎 Unauthorized port scans 🔎 Mapped in realtime 🔎 Every 6 hours 🔎 #cybersecurity electricbrain.com.au/pages/analytic…

Estafas en español: Cómo la IA personaliza los ataques buff.ly/RLverML #CyberSecurity
"Since October 8, 2025, GreyNoise has tracked a coordinated botnet operation involving over 100,000 unique IP addresses from more than 100 countries targeting Remote Desktop Protocol (RDP) services in the United States". #Cybersecurity #BotNet #RDP greynoise.io/blog/botnet-la…
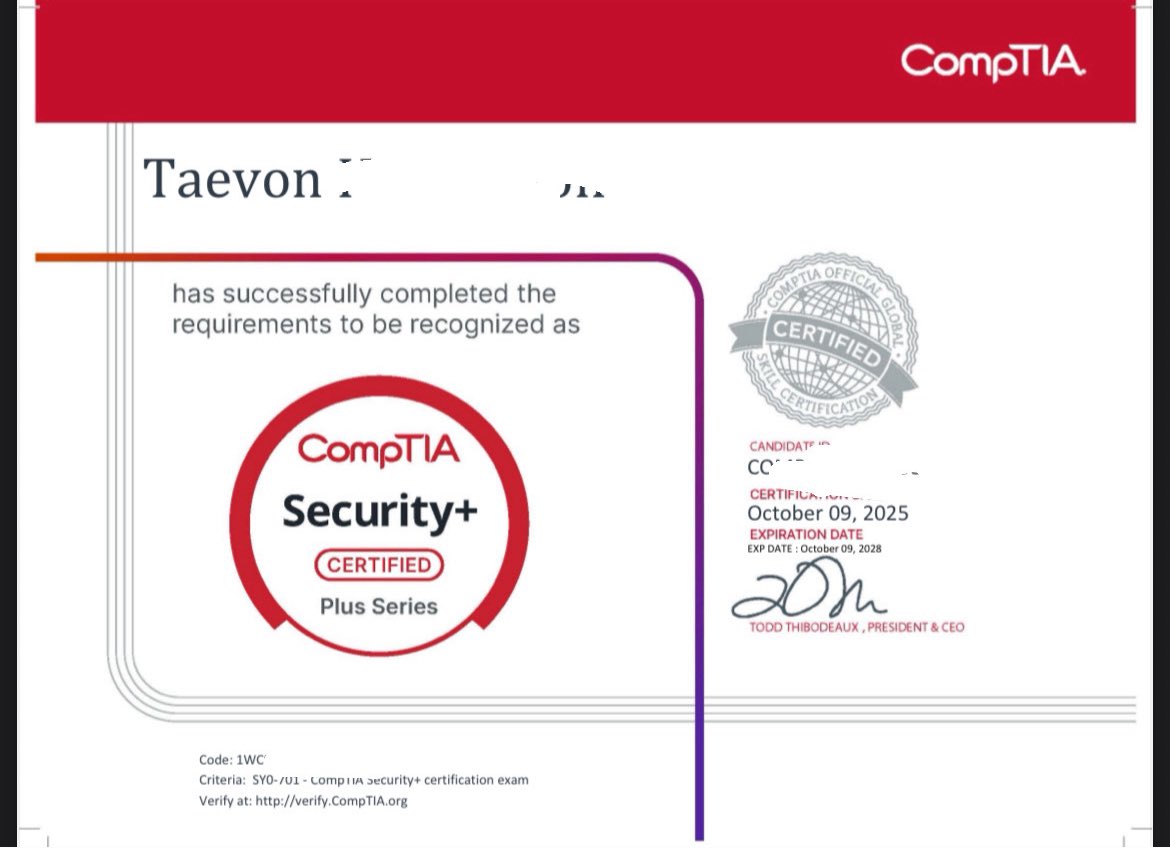
Ready to ace your CompTIA PenTest+ exam? 🎯 Our ultimate guide has you covered, from exam prep to career boost in #Cybersecurity! 🔗 Get certified: flashgenius.net/blog-article/u… #PenTestPlus #EthicalHacking #ITCertifications
Comment: 400GB of pilfered data is bad, but do you think Qilin also reads all those blood test results now? I wonder if they offer a second opinion service on the dark web? Asking for a ... #Cybersecurity buz.li/t/q9c8Zm
I’m starting a little side hustle: doing basic website security checks for small businesses, blogs, or personal sites. Even as a beginner, I can help make sure your site isn’t an easy target for hackers. 🛡️ #CyberSecurity #InfoSec #WebSecurity
AI Security Fact 🔐🤖 LLMs can 'leak' hidden system prompts just by clever wording, no hacking tools needed. It’s like social engineering, but for machines. The attacker talks the model into breaking its own rules. #AIsec #LLM #CyberSecurity #PromptInjection
How to Decrypt MD5 Passwords in PHP? infosecscout.com/decrypt-md5-php #kalilinux #hacking #cybersecurity

The dark web isn't mysterious—it's a marketplace. Your stolen credentials are probably for sale right now. Check haveibeenpwned.com. #DarkWeb #Cybersecurity #DataBreach
Security researchers reveal active exploitation against Service Finder WordPress theme #cybersecurity #vulnerabilitymanagement #ServiceFinder bleepingcomputer.com/news/security/…
bleepingcomputer.com
Hackers exploit auth bypass in Service Finder WordPress theme
Threat actors are actively exploiting a critical vulnerability in the Service Finder WordPress theme that allows them to bypass authentication and log in as administrators.
Possible Phishing 🎣 on: ⚠️hxxps[:]//sites[.]google[.]com/view/ccorbl1 🧬 Analysis at: urldna.io/scan/68eadfbd3… #cybersecurity #phishing #infosec #urldna #scam #infosec @urldna
![urldna_bot's tweet image. Possible Phishing 🎣
on: ⚠️hxxps[:]//sites[.]google[.]com/view/ccorbl1
🧬 Analysis at: urldna.io/scan/68eadfbd3…
#cybersecurity #phishing #infosec #urldna #scam #infosec @urldna](https://pbs.twimg.com/media/G3BKqRCWcAAXbro.jpg)
Continuous trust is key. Check users’ sessions regularly—don’t just trust a single login. #CyberSecurity #ZeroTrust #HostingAdvice
🔒 October is Cybersecurity Awareness Month! Understanding cybersecurity is crucial as cyberattacks become more common. 🧟💻 From malware to phishing, learn how to protect yourself with our essential tips: experian.com/blogs/ask-expe… #Cybersecurity #StaySafeOnline…

The 12 Pillars of Cyber Security! 🛡️ Know your defense: from Encryption to API Security. Are you covering all 12? #CyberSecurity #InfoSec #SecurityFramework #digitalearn #DevOps

New XSS Bypass Cloudflare WAF 🧱 Payload : %3CSVG/oNlY=1%20ONlOAD=confirm(document.domain)%3E #BugBounty #XSS #Cybersecurity

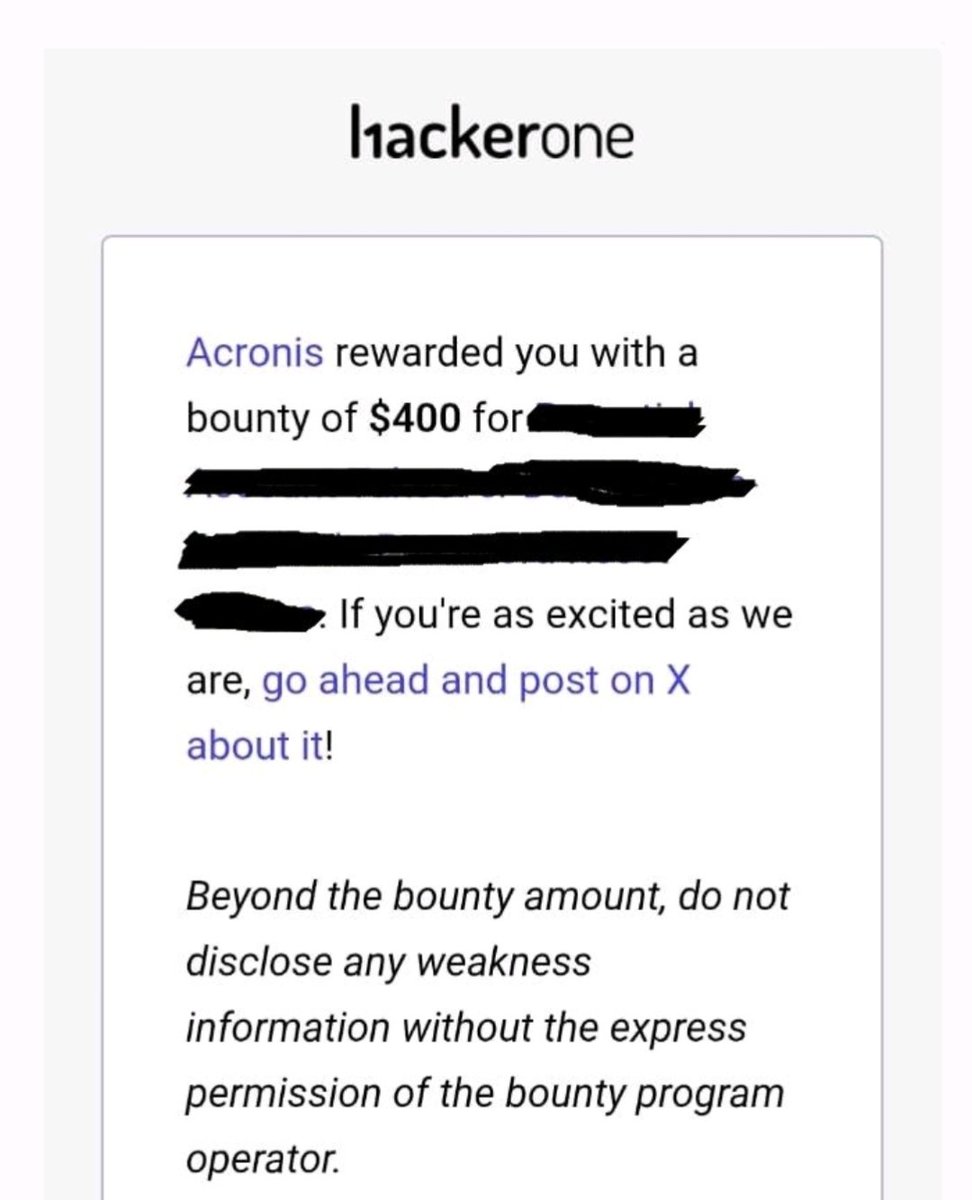
Alhamdulillah I was Awarded a $400 Bounty on HackerOne 💥 #bugbountytips #bugbounty #CyberSecurity #Hacked #hackingtools
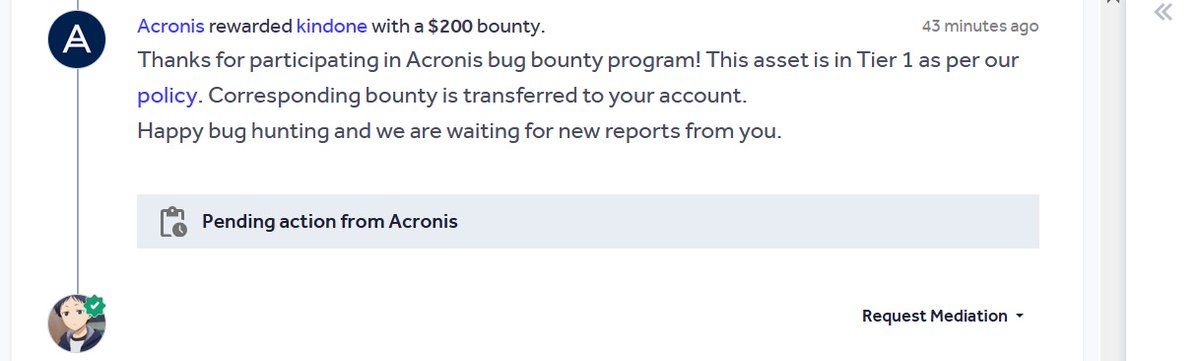
Alhamdulillah I was Awarded a $200 Bounty on HackerOne 💥 #bugbountytips #bugbounty #CyberSecurity #Hacked #hackingtools #BugTrio
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Beginners intro to Linux kernel fuzzing and vulnerability research by @slava_moskvin_ Part 1: slavamoskvin.com/hunting-bugs-i… Part 2: slavamoskvin.com/finding-bugs-i… Part 3: slavamoskvin.com/finding-bugs-i… #Linux #cybersecurity


Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

The grep command is like a spotlight for text. It instantly finds words, phrases, or patterns inside files or streams. Here is a quick grep cheatsheet 😎👇 Find pdf books with all my #Linux and #cybersecurity related infographics from study-notes.org

Here’s What CEOs Need to Tell #Board Members About #Cybersecurity > buff.ly/t1Ok0ox #tech #security #cyberthreats #cyberattacks #databreaches #business #leadership #management #governance #regulation #compliance #GRC #CISO #CIO #CTO #CEO

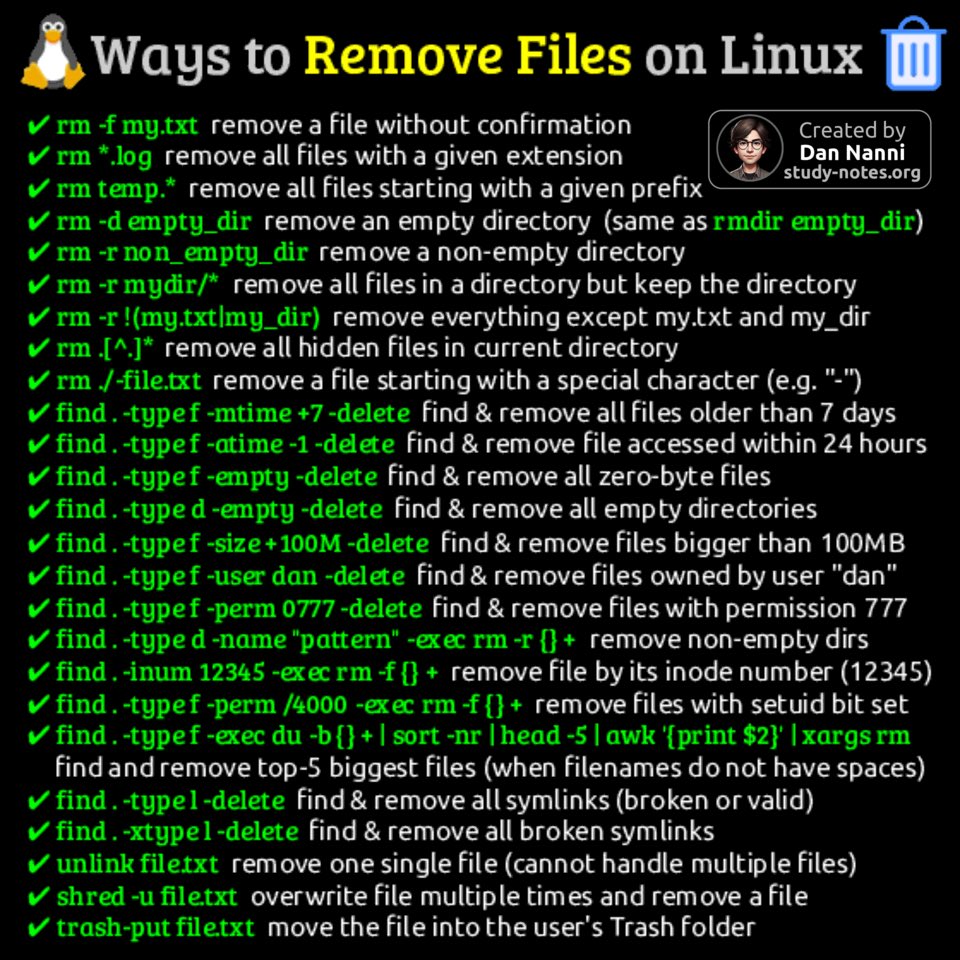
There are various ways to remove files and directories on Linux, based on filenames, creation/access time, size, ownership, permissions, or security needs 😎👇 #sysadmin Find pdf books with all my #Linux and #cybersecurity related infographics from study-notes.org
How to Spot a Pentester 🔥 Telegram: t.me/hackinarticles #CyberSecurity #InfoSec #PenetrationTesting #EthicalHacking #BugBounty #ThreatIntelligence #RedTeam #BlueTeam #CloudSecurity #DataSecurity #ZeroTrust #CyberSecurityJobs #CyberSecurityAwareness

First Boolean‑based SQLi, still shaking 😭🔥! Reported and paused let’s goooo!, thanks for continuous support Everyone. #BugBounty #CyberSecurity #infosec #sql #web #bugbountytips @bugcrowd #Hacking

Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

October is #CyberSecurity Awareness Month 🔐 — be proactive in protecting your child’s #DataPrivacy by familiarizing yourself with the types of data popular digital devices/platforms collect with the “Data Privacy and Children” Research-at-a-Glance today! Download now ⏬…




Something went wrong.
Something went wrong.
United States Trends
- 1. Penn State 23.9K posts
- 2. James Franklin 12K posts
- 3. Indiana 44.2K posts
- 4. Oregon 66.6K posts
- 5. #UFCRio 27.4K posts
- 6. Auburn 10.4K posts
- 7. Diane Keaton 196K posts
- 8. #iufb 7,531 posts
- 9. Mateer 12.5K posts
- 10. Northwestern 9,370 posts
- 11. Drew Allar 5,727 posts
- 12. Makai Lemon N/A
- 13. Georgia 48.6K posts
- 14. Cignetti 8,089 posts
- 15. Hoosiers 9,276 posts
- 16. Luque 16.3K posts
- 17. #HookEm 8,530 posts
- 18. Texas 136K posts
- 19. Nuss 3,762 posts
- 20. #AEWCollision 5,435 posts