TC
@tcs3c
father of three - h4ck3r of stuff - lover of life - singer of songs | pwning at @codewhitesec
قد يعجبك
Yes, we're beating a dead horse. But that horse still runs in corporate networks - and quietly gives attackers the keys to the kingdom. We're publishing what’s long been exploitable. Time to talk about it. #DSM #Ivanti code-white.com/blog/ivanti-de…
Better patch your Veeam Backup & Replication servers! Full system takeover via CVE-2024-40711, discovered by our very own @frycos - no technical details from us this time because this might instantly be abused by ransomware gangs code-white.com/public-vulnera…
We're pleased to announce that we donated a total of $29,500 from vulnerability disclosure rewards to charities this year. Thanks to all colleagues who made this possible and hacky christmas everybody!
l33t h4x0r??? Prove it! 😎
The return of Kurts Maultaschenfabrikle: have fun with our all new applicants challenge at apply-if-you-can.com #CTF
Wanna meet some of our team mates like @frycos @dhn_ @tcs3c @datenschrott in real life? Spot us at #OffensiveCon in Berlin over the next few days 🙋
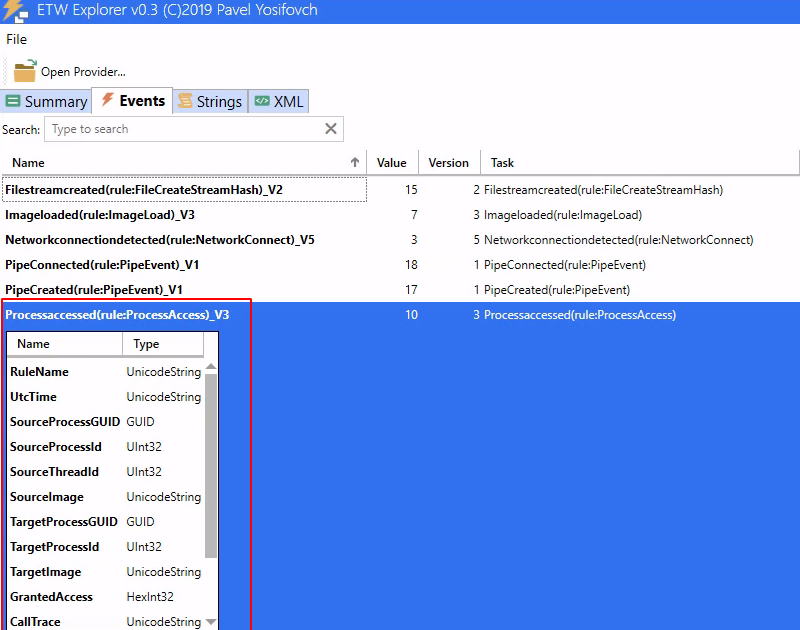
Even though JMX exploitation is well understood, @mwulftange and @qtc_de found new universal exploitation techniques & one of them allows to gain instant Remote Code Execution using TemplatesImpl (which is now implemented in #beanshooter) codewhitesec.blogspot.com/2023/03/jmx-ex…
codewhitesec.blogspot.com
CODE WHITE | Blog: JMX Exploitation Revisited
CODE WHITE | Blog: JMX Exploitation Revisited
If you're into client virtualization with #QubesOS, use #KeePassXC and #rofi, our very own @qtc_de has you covered with a nice frontend which makes your credential usage a little bit easier 😎 github.com/codewhitesec/q…
I call it "Golden Token": Skype for Business Server 2019 Built-in RCE, anytime after certificate leak (similar to Golden SAML) #persistence
Our powerintern @testert01 strikes again, teamed up with @thefLinkk and developed SysmonEnte: a hard to detect attack on Sysmon. Check out our new blogpost: codewhitesec.blogspot.com/2022/09/attack…
As part of our #x33fcon talk, @invist and @theflinkk release a socks4a proxy leveraging PIC, Websockets and static obfuscation on assembly level 😎 Check it out: github.com/codewhitesec/L…
Congratulations to all participants and a major thanks to all our supporters! @FraunhoferAISEC @tngtech @codewhitesec @heiseonline and @LixLab
Proud to be sponsoring the celebration dinner today for the finalists of the Cyber Security Challenge Germany 2022. Great to support the hacking community and get in touch with so many talented minds. Cheers to all winners! #CSCG #finestHacking #finestDining
We could waffle on about our distinctive service portfolios. We could brag about the perks we provide. We could present you with our outstanding team. But you know what? Apply if you can! apply-if-you-can.com
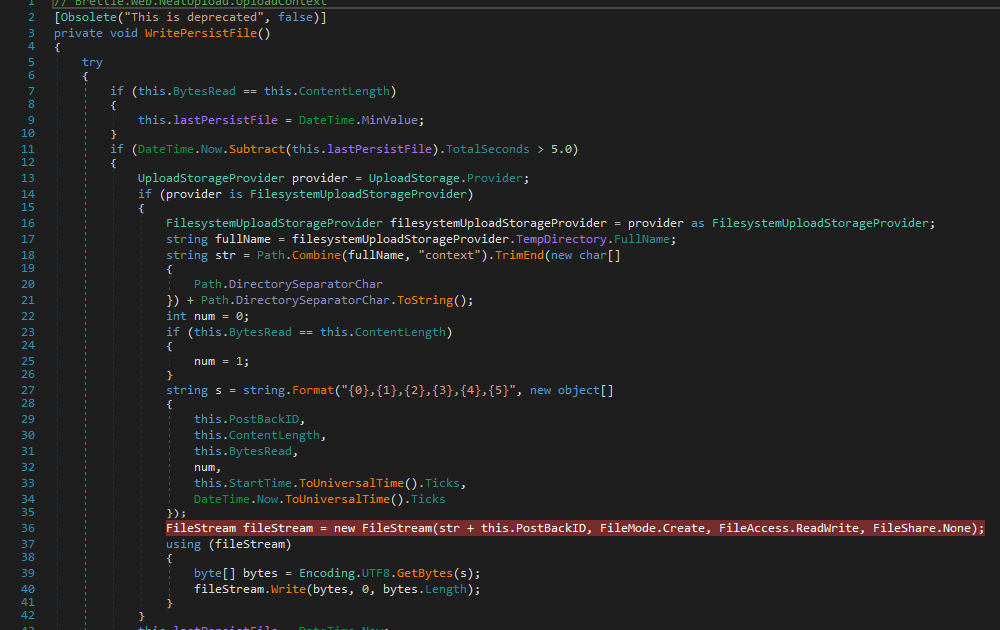
Bypassing .NET Serialization Binders: case studies for DevExpress (CVE-2022-28684) and Microsoft Exchange (CVE-2022-23277) by @mwulftange codewhitesec.blogspot.com/2022/06/bypass…
If you have #Citrix #ADM exposed, better patch than sorry. @frycos and @CaptnBanana found a hard to exploit but nonetheless nasty bug that could lead to an unauth'ed device brick/takeover: support.citrix.com/article/CTX460…
At @codewhitesec the interns write their own C2 frameworks.. What‘s next?! 😎
@snyksec Tnx for your excellent analysis at snyk.io/blog/npm-depen… and don't worry, the "malicious actor" is one of our interns 😎 who was tasked to research dependency confusion as part of our continuous attack simulations for clients. (1/2)
snyk.io
Targeted npm dependency confusion attack caught red-handed | Snyk
Once in a while we encounter a truly malicious package that has a purpose, means, and is production-ready — this is a story about one found in npm: gxm-reference-web-auth-server.
Getting RCE with a Razor! Our walk-through of CVE-2021-22941 affecting Citrix ShareFile Storage Zones Controller by @mwulftange is now live codewhitesec.blogspot.com/2021/09/citrix…
Read about what @kaidentity does „on a rainy sunday afternoon when the kids are busy with someone else“. 😎 Finest #SAP exploitation - enjoy!
How the search for deser bugs in #SAP sent @kaidentity down a rabbit hole where he winded up stumbling upon a completely unrelated unauth'ed admin access #CVE-2021-21481 codewhitesec.blogspot.com/2021/06/about-…
Happy to announce that our talk 'PIC Your Malware' was accepted @BruCON! @thefLinkk and @b00n10 will share their experiences on leveraging fully position independent code to avoid suspicious memory artifacts & other useful techniques to stay under the radar of EDRs & BlueTeams 😎
Unauth'd admin access to #SAP #Netweaver? Our very own @kaidentity has you covered, see #CVE-2021-21481 and SAP Security Note 3022422. Better patch than sorry. Our customers got their heads-up already and we'll publish a detailed blog post when appropriate.
United States الاتجاهات
- 1. Toledo 9,109 posts
- 2. Arsenal 168K posts
- 3. Louisville 7,267 posts
- 4. Kepa 12.4K posts
- 5. Christmas Eve 113K posts
- 6. PGA Tour N/A
- 7. Dunesday N/A
- 8. #drwfirstgoal N/A
- 9. Brooks Koepka N/A
- 10. Insurrection Act 5,935 posts
- 11. Because Chicago 1,595 posts
- 12. Martinelli 16.9K posts
- 13. Dylan Stewart N/A
- 14. Karlsson N/A
- 15. Lacroix 8,613 posts
- 16. Benitez 13.2K posts
- 17. Hearn N/A
- 18. Miller Moss N/A
- 19. #ARSCRY 5,331 posts
- 20. Paterson 1,910 posts
قد يعجبك
-
 banane
banane
@CaptnBanana -
 David Elze
David Elze
@datenschrott -
 CODE WHITE GmbH
CODE WHITE GmbH
@codewhitesec -
 frycos
frycos
@frycos -
 Markus Wulftange
Markus Wulftange
@mwulftange -
 George Pranschke
George Pranschke
@cheorchie -
 Matthias Kaiser
Matthias Kaiser
@matthias_kaiser -
 Tobias Neitzel
Tobias Neitzel
@qtc_de -
 niph
niph
@niph_ -
 Ralf
Ralf
@rlfbrt -
 DTM
DTM
@dtmsecurity -
 esjay
esjay
@esj4y -
 Andreas Schmidt
Andreas Schmidt
@_znow -
 banana_bunny
banana_bunny
@bananabunny6 -
![HeinrichsH's profile picture. {"work": "leveraging full-spectrum cyber for @CrowdStrike", "interests": ["binary exploitation", "cryptography", "embedded hacking", "@EatSleepPwnRpt", "JSON"]}](https://pbs.twimg.com/profile_images/557293175443034113/sE7UCZv3.jpeg) HPH
HPH
@HeinrichsH
Something went wrong.
Something went wrong.














![HeinrichsH's profile picture. {"work": "leveraging full-spectrum cyber for @CrowdStrike", "interests": ["binary exploitation", "cryptography", "embedded hacking", "@EatSleepPwnRpt", "JSON"]}](https://pbs.twimg.com/profile_images/557293175443034113/sE7UCZv3_x96.jpeg)