Mohammed | مُحَمَّد
@u0pattern_cs
Mobile Security R&D by day | Saudi nationalist politician by night, whose ambition is to see his country 🇸🇦 lead the region #the_saudi_cyber_arms_company_2035
Bạn có thể thích
ثغرة iOS 0click RCE "الواحدة" مع تخطياتها تضاعفت قيمتها اليوم في السوق الأبيض لتصل إلى 18 مليون ريال، ذا يعني راح تتضاعف في السوق الرمادي ايضا. سوق mobile security سوق قوي للخصخصه (ليس مقصور على ثغرات RCE) قادر يساهم في GDP وقوة الدولة في تنفيذ القانون. security.apple.com/blog/apple-sec…
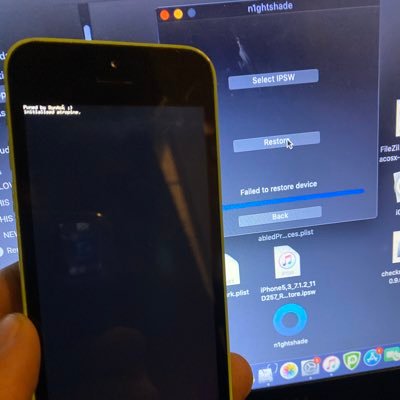
things are getting more ugly but the forbidden is desirable :) github.com/blacktop/ipsw-…
the blastdoor sandbox's giving the RawCamera the green light to do its magic :)

I diffed RawCamera on iOS 18.6.1 and 18.6.2 Here's full Diaphora diff: mediafire.com/file/e2yp7m27r… 18.6.1: 1DD8A36DC 18.6.2: 1DD8A3684 I'm concern that the exploit may using CGImageSource and CGImageSourceCreateImageAtIndex since it got removed on lastest version
الحمدلله، حصلت على شهادة OMSE بعد رحلة مع دراسة iOS/Android internals واستغلال ثغراتها مع تجاوز security mitigations (SPTM-TXM/RKP/PAC/kalloc_type) وتخطي RASPs و advanced obfuscations وصولًا إلى advanced forensics لأنظمة iOS/Android المُخترقة بثغرات n-days credly.com/badges/b13ca89…
and we are still waiting for the llvm.org/PR96099 to be fixed so we can define _LIBCPP_INSTRUMENTED_WITH_ASAN :)
Learn how to equip your C++ code with ASan annotations to catch more bugs. We also contributed to LLVM, including annotations to std::string and std::deque, custom allocators, and bug fixes in libc++. buff.ly/4glRVkw
zerodayengineering.com/insights/qualc… The analysis of this article is misleading others, this ITW patch chromium-review.googlesource.com/c/chromiumos/t…

As it turns out, compilers happily spill the index for indirect jumps through a jump table after bounds checking, creating a TOCTTOU race for arbitrary control-flow hijacking. Check out our @HexHiveEPFL @IEEESSP "WarpAttack" paper: nebelwelt.net/files/23Oaklan…



New version of my #binaryninja to identify obfuscated code. Besides major performance improvements it includes a new heuristic to detect frequently called functions which identifies string decryption and API hashing routines in #malware. Code: github.com/mrphrazer/obfu…

New blog post and updated #binaryninja plugin: "Statistical Analysis to Detect Uncommon Code" We use statistics to identify obfuscation in an #Anticheat, a mobile DRM, a #Windows kernel module & malware. Link: synthesis.to/2023/01/26/unc… Code: github.com/mrphrazer/obfu…

A little late but I finally finished the writeup for the intended solution of my v8 pwnable. You can find my writeup here: ju256.de/posts/kitctfct… tldr: v8 sandbox escape by utilizing the memory corruption API and without the usual JIT technique.
If you ever wanted to get into v8 exploitation, you still have ~9h to check out my v8 pwn challenge "Date" for KITCTFCTF (ctf.kitctf.me/challenges#Dat…). Get first blood now before it's too late 🔥
New blog post on the @pypyproject blog: "Finding JIT Optimizer Bugs using SMT Solvers and Fuzzing" pypy.org/posts/2022/12/… My first time using Z3! Thanks to @saambarati, @tekknolagi & others for great feedback on drafts. Thanks to @regehr for getting me to write it!
Here are some slides about the V8 Sandboxing project that I prepared for an internal talk but figured I could also share more widely: docs.google.com/presentation/d…
🥇 My paper: cyberhub.sa/posts/106 Thank you @CyberhubSa
Me and Billy ( @st424204 ) created a series of pwn challenges called Fourchain for this year's HITCON CTF. Here are the posts about the Browser & Hypervisor part of the challenge: Browser : bruce30262.github.io/hitcon-ctf-202… Hypervisor: bruce30262.github.io/hitcon-ctf-202… Enjoy ! #HITCONCTF2022
Actually BlackHat Mea is really better than the DEFCON CTF at all
In this short article I explain how I managed to bypass Advanced Threat Protection (ATP) -EDR- from Microsoft and dump the LSASS process without being detected. blog.0x4.xyz/bypassing-wind… Proof of Concept (PoC) github.com/0xAbdullah/Off…
I am truly puzzled by all these hot takes on using Rust for everything. I have been working on NT kernel development for few months now and I see no scenarios in which Rust would have been helpful. Been able to develop and address all the problem just with C.
Happy to announce that our paper "Efficient Deobfuscation of Linear Mixed Boolean-Arithmetic Expressions" has been accepted for presentation at CheckMATE'22 workshop (co-located with @acm_ccs) arxiv.org/abs/2209.06335
United States Xu hướng
- 1. Branch 37.9K posts
- 2. Red Cross 59.8K posts
- 3. #njkopw 11.5K posts
- 4. Chiefs 113K posts
- 5. Knesset 21K posts
- 6. Lions 89.6K posts
- 7. Exceeded 5,783 posts
- 8. Binance DEX 5,137 posts
- 9. Rod Wave 1,756 posts
- 10. Mahomes 35.1K posts
- 11. Air Force One 60.6K posts
- 12. Use GiveRep N/A
- 13. #LaGranjaVIP 84.8K posts
- 14. Eitan Mor 19.6K posts
- 15. #LoveCabin 1,414 posts
- 16. Ziv Berman 23.1K posts
- 17. Alon Ohel 20.5K posts
- 18. All 20 45.6K posts
- 19. Tel Aviv 61.8K posts
- 20. #TNABoundForGlory 61.2K posts
Bạn có thể thích
-
 ميمز سكيورتي 🛡️
ميمز سكيورتي 🛡️
@m3m353c -
 Mohammed 🇸🇦
Mohammed 🇸🇦
@u0pattern_old -
 HitmanAlharbi
HitmanAlharbi
@HitmanF15 -
 Z0ldyck
Z0ldyck
@electronicbots -
 𝐱𝐫𝟎𝐨𝟎𝐭𝐱 🇸🇦
𝐱𝐫𝟎𝐨𝟎𝐭𝐱 🇸🇦
@xr0o0tx -
 Ali Alwashali
Ali Alwashali
@ali_alwashali -
 Mesh3l
Mesh3l
@Mesh3l_911 -
 Diefunction
Diefunction
@Diefunction -
 0xRaw
0xRaw
@0xRaw -
 BugsBunny
BugsBunny
@0xiMazen -
 Nawaf Almutairi
Nawaf Almutairi
@N4waF_Almutairi -
 Abdulaziz almisfer 🇸🇦
Abdulaziz almisfer 🇸🇦
@3almisfer -
 Ahmed Alshammari
Ahmed Alshammari
@ahmed_vapt -
 Nasser Albarrak
Nasser Albarrak
@nass3r000 -
 سعود العنزي
سعود العنزي
@Dmaral3noz
Something went wrong.
Something went wrong.




















![u0pattern_cs's tweet card. Consider this program: % cat repro.mm #include [[gnu::noinline]] void use_string(const std::string&) {} typedef void(^B)(); [[gnu::noinline]] void use_block(B&& b) {} int...](https://pbs.twimg.com/card_img/1975488745475305472/EaEGq8Nf?format=png&name=orig)