vic
@v1csec
Security researcher @Synacktiv — CTF organizer @sth4ck
You might like
Userland iOS aficionados, I released a simple IDA plugin that should improve your Objective-C experience. For now it removes ARC function calls in decompiled code (eg objc_retain) and helps listing candidate callers to a method. Check it out at github.com/synacktiv/objc…
The "Objective-C helper" IDA plugin presented during the @sth4ck talk "Demystifying Objective-C internals" given by @v1csec is now publicly available on GitHub at github.com/synacktiv/objc… The slides are also available on our website: synacktiv.com/sites/default/…
Have you ever wondered what the attack surface of Counter Strike: Global Offensive looks like? Our ninjas @myr463 and @v1csec studied it and found a server to client bug! Read more details about this research in our latest blogpost. synacktiv.com/publications/e…
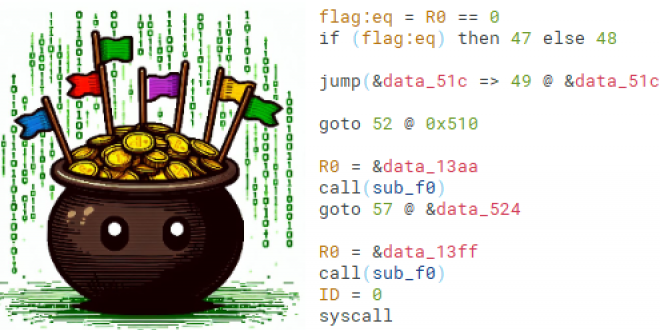
Our ninja @masthoon solved a tough challenge during @PotluckCTF with an ingenious approach: he built a decompiler for a custom ISA by lifting instructions to Binary Ninja IL. Read the "Pot of Gold" write-up (kudos to @bl4sty for creating the challenge): synacktiv.com/publications/l…
To facilitate reverse-engineering of large programs, vulnerability research and root-cause analysis on iOS, Android, and other major platforms, @myr463 and @Hexabeast released Frinet, a tool combining Frida with an enhanced version of Tenet. synacktiv.com/publications/f…
Sometimes simple is best. See how @SidewayRE exploited a 9-year-old Linux kernel bug at #Pwn2Own Vancouver 2023! synacktiv.com/publications/o…
[ZDI-23-900|CVE-2023-35001] (Pwn2Own) Linux Kernel nftables Incorrect Pointer Scaling Local Privilege Escalation Vulnerability (CVSS 7.8; Credit: Tanguy DUBROCA (@SidewayRE) from Synacktiv (@Synacktiv)) zerodayinitiative.com/advisories/ZDI…
🍏iOS is all the rage nowadays: that's where the good stuff is located for nation-state attackers and is gulping down every world-class researcher it can hire … Bootstrap your iOS research at #HEXACON2023 thanks to @v1csec and Etienne Helluy-Lafont: hexacon.fr/trainer/cutill…!

Watchout! CVE-2023-22809 on Sudo was patched today to prevent a privilege escalation on sudoedit. Read the security advisory by @aevy__ and @v1csec: synacktiv.com/sites/default/…

Definitely spent a very good time at @hexacon_fr! Amazing place, high quality talks and great people, what else could be said?
Today I share with you #RustHound🦀. A new AD collector written in #Rust for #BloodHound! It is cross-platform, cross-compiled and generates all json files needed. Other modules will be available as under development!🔥 Hope you will enjoy it! github.com/OPENCYBER-FR/R…
@OPENCYBER_FR release #RustHound as open-source. A new AD collector written in #Rust for #BloodHound! It is cross-platform, cross-compiled and generates all JSON files needed. Other modules will be available as under development! opencyber.com/rusthound-data… github.com/OPENCYBER-FR/R…
J'ai eu l'occasion de donner mon premier talk "Attacking SUID binaries" à RumpÀRennes mardi soir ! Merci à @securinsa pour cette première édition organisée avec soins, je reviendrai avec plaisir :)

.rar 0x1 c'est fini! Merci pour votre présence ! Nous remercions encore une fois @Synacktiv, qui nous a fait confiance, pour notre premier événement. Également les intervenants pour leur supers conférences. ⬇️👀📸@TheLaluka


[INTERNSHIPS 🇫🇷] We just published our offers for the 2022-2023 season! We're ready to be flooded by your resumes 😆 Apply now! #pentest #reverse #dev #infra #dfir synacktiv.com/nous-rejoindre…
Content de participer en tant que speaker à cette première édition de @securinsa ! Il est temps de partager l'expérience acquise à @Synacktiv :)
[J-13] À 20h25, on passera à “Attacking SUID binaries” qui sera présentée par @v1csec à 20h25.
![securinsa's tweet image. [J-13] À 20h25, on passera à “Attacking SUID binaries” qui sera présentée par @v1csec à 20h25.](https://pbs.twimg.com/media/FdrVg2GXkAAJ0JN.jpg)
SAVE THE DATE - Mardi 11 octobre 20h00 - 01h Pour prendre vos places, c'est ici à 18h: helloasso.com/associations/s…
SAVE THE DATE - Mardi 11 octobre 20h30 - 01h C'est avec plaisir que nous annonçons le premier event de Sécur'Insa: Rumps à Rennes. Au foyer de l'INSA Rennes le 11 octobre prochain 😎 Vous avez une idée de talk ? Alors stay tuned pour l'ouverture du CFP !

Croissants, red wine and high-quality offensive security talks in a wonderful place? That's all the Hexacon team is promising for October 2022. Details and Call For Papers are coming very soon... Until then, a bit more teasing for you folks: hexacon.fr #HEXACON2022

PhD candidate in Programming Languages nearing thesis submission looking for (ideally remote) positions from Oslo, Norway. Some topics I'm interested in are compilers, verification, security, and cryptography. DM for resume! RTs appreciated😊
We did it 😃! What a blast to be part of a team able to claim the title of Master of Pwn! Kudos to all other participants and to @thezdi for the flawless organization. Let’s wait for the patches, then we’ll share the technical details with the community 🤙
Here are the final Master of Pwn standings. Congrats to @Synacktiv on claiming the title. It was a close race, but they pull through.

United States Trends
- 1. Comey 59.7K posts
- 2. Thanksgiving 158K posts
- 3. Jimmy Cliff 29K posts
- 4. #WooSoxWishList 5,646 posts
- 5. Pentagon 11.1K posts
- 6. Lindsey Halligan 11.9K posts
- 7. DISMISSED 30.4K posts
- 8. #NutramentHolidayPromotion N/A
- 9. #IDontWantToOverreactBUT 1,463 posts
- 10. The Department of War 13.8K posts
- 11. Sen. Mark Kelly 17.9K posts
- 12. #MondayMotivation 14.6K posts
- 13. DOGE 244K posts
- 14. Ja'Kobi Gillespie N/A
- 15. TOP CALL 5,307 posts
- 16. #stayselcaday 4,984 posts
- 17. AI Alert 3,505 posts
- 18. Monad 184K posts
- 19. Hal Steinbrenner N/A
- 20. Hegseth 18.6K posts
You might like
Something went wrong.
Something went wrong.