#blindsql arama sonuçları
🧠 Blind Time-Based SQLi 1️⃣ No error/data output 2️⃣ Uses time delays like IF(SUBSTRING((SELECT pwd FROM users WHERE id=1),1,1)='a', SLEEP(5),0) 3️⃣ Measures response time to infer data char-by-char 🎯 Extracts secrets without visible leaks #bugbounty #sqlinjection #blindsql

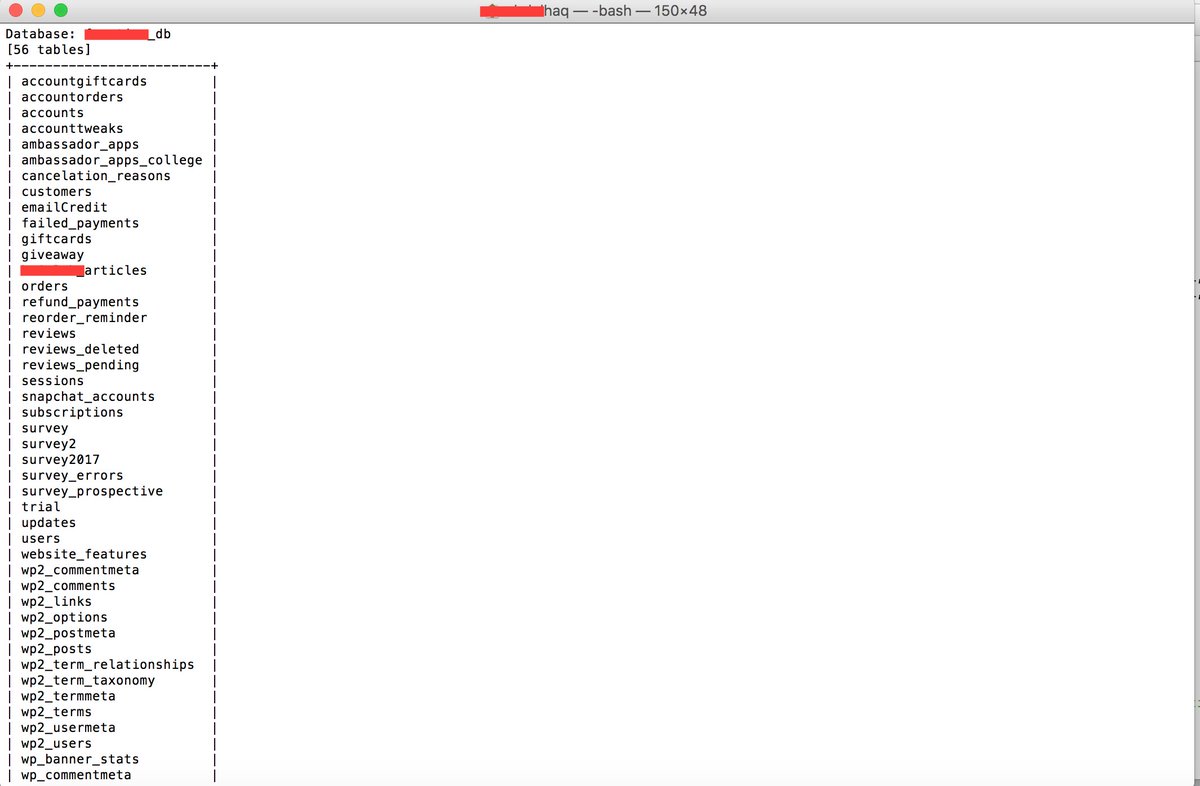
Blind SQL Injection in Private website. 8 Database , 56 tables in 1 Database opss! Bug has been report :) #Bugbounty #BlindSQL #HappyforHelp
#Barracuda Networks was latest victim of a #BlindSQL injection #hack that exposed partner contact information. #infose…http://lnkd.in/uBSNHd
I just published Blind SQL injection with conditional responses (From PortSwigger) #blindsql #sqlinjection link.medium.com/iWRaNwL4tEb
@Contact_Left @_RastaMouse @VulnHub @Q3rv0 #Nosql #blindsql haaaa haaaa totally stuck with this.
Hacker Trick: Blind SQL Injection Blind SQL Injection is like guessing what’s inside a box by listening to it shake. ❌ No error messages ❌ No visible data ✅ Just clever guesses and indirect clues. 👉 Read now before silent breaches happen: infosectrain.com/blog/blind-sql… #blindsql
HackwithGithub: Duncan - Blind SQL injector skeleton cc SilentSignalHU github.com/silentsignal/d… #BlindSQL
Eventually finished this room after extensive searching for a table and sql payload. Completed Room : Priorities TryHackMe #sqlinjection #blindsql lnkd.in/denpMyaY
Has anyone reviewed the delayed response from the #Azure API when provisioning a @megaportnetwork and other network ports? It appears that valid and unallocated keys respond differently. Similar to #BlindSQL injection. #infosec
🧠 Blind Time-Based SQLi 1️⃣ No error/data output 2️⃣ Uses time delays like IF(SUBSTRING((SELECT pwd FROM users WHERE id=1),1,1)='a', SLEEP(5),0) 3️⃣ Measures response time to infer data char-by-char 🎯 Extracts secrets without visible leaks #bugbounty #sqlinjection #blindsql

Hacker Trick: Blind SQL Injection Blind SQL Injection is like guessing what’s inside a box by listening to it shake. ❌ No error messages ❌ No visible data ✅ Just clever guesses and indirect clues. 👉 Read now before silent breaches happen: infosectrain.com/blog/blind-sql… #blindsql
🧠 Blind Time-Based SQLi 1️⃣ No error/data output 2️⃣ Uses time delays like IF(SUBSTRING((SELECT pwd FROM users WHERE id=1),1,1)='a', SLEEP(5),0) 3️⃣ Measures response time to infer data char-by-char 🎯 Extracts secrets without visible leaks #bugbounty #sqlinjection #blindsql

Blind SQL Injection in Private website. 8 Database , 56 tables in 1 Database opss! Bug has been report :) #Bugbounty #BlindSQL #HappyforHelp

Something went wrong.
Something went wrong.
United States Trends
- 1. Cheney 80.3K posts
- 2. Sedition 156K posts
- 3. Lamelo 4,450 posts
- 4. First Take 46.3K posts
- 5. Seditious 86.1K posts
- 6. Jeanie 1,814 posts
- 7. Constitution 109K posts
- 8. Mark Walter 1,339 posts
- 9. Coast Guard 21.1K posts
- 10. Seager N/A
- 11. Commander in Chief 49.3K posts
- 12. Trump and Vance 36.1K posts
- 13. Elon Musk 278K posts
- 14. Cam Newton 4,229 posts
- 15. UNLAWFUL 74.5K posts
- 16. Shayy 13.2K posts
- 17. Nano Banana Pro 23.4K posts
- 18. #WeekndTourLeaks 1,447 posts
- 19. UCMJ 9,721 posts
- 20. Dameon Pierce N/A



![TwiBow's profile picture. Good information enriched, bad impoverished || #[A-Z]+aaS | #CyberSecurity | Zenk Security Member || #RSSI #CISO || GPG KeyID : 0x5845f8dcd97a4d12](https://pbs.twimg.com/profile_images/1438428836971089934/BimbSR2Z.jpg)












