#datasecuritydemo 검색 결과
Proactive security starts with visibility. Source-to-destination data lineage simplifies reporting for regulations like GDPR and HIPAA, to keep business moving. Register for Risk in Real Time: Data Security: Spot Data Threats in Moments, Not Days at spr.ly/60137nqkf
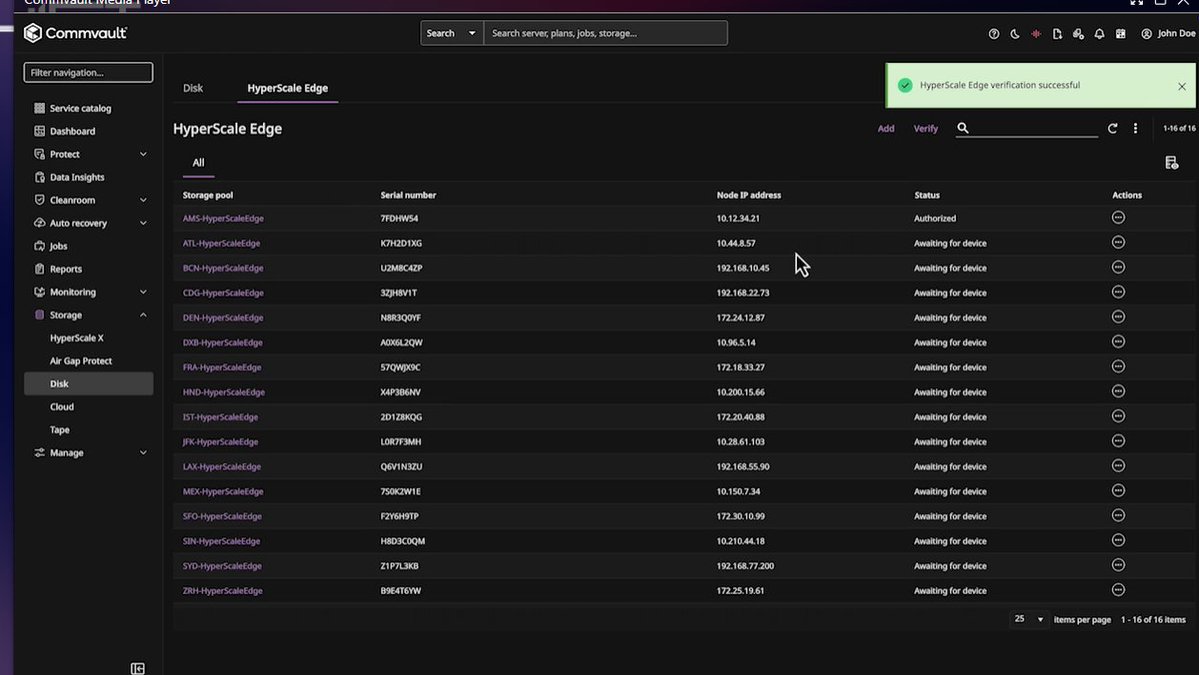
⚠️ The ransomware investigation reality: Data Manager's new security analysis page offers a centralized dashboard, actionable workflows, and saves hours with minutes-long processes. Speed matters: del.ly/601875bzu #CyberResilience #iwork4dell

⚠️ The ransomware investigation reality: Data Manager's new security analysis page offers a centralized dashboard, actionable workflows, and saves hours with minutes-long processes. Speed matters: del.ly/601975XX7 #CyberResilience #iwork4dell

The Digital Safety Deposit Box (dSDB) Demo youtu.be/0n5m3j1Egzk?si… via @YouTube
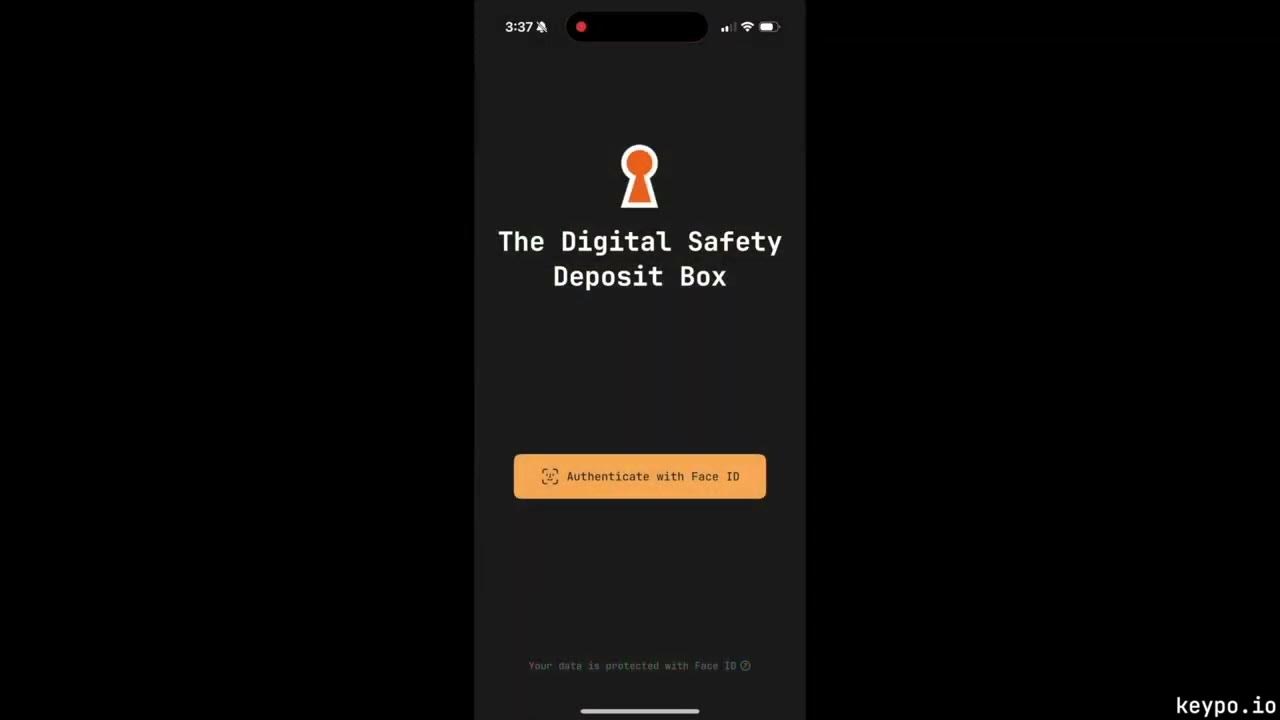
youtube.com
YouTube
The Digital Safety Deposit Box (dSDB) Demo
You’re 25 minutes away from clarity and control. Discover and classify sensitive data across endpoint and cloud environments with greater visibility with @TrendMicro. Register for Risk in Real Time: Data Security: Spot Data Threats in Moments, Not Days bit.ly/4m9R2xX
#WebinarAlert 🚀 What if you didn’t have to choose between data access & security? Join us to learn how a security-by-design architecture makes your data safe, accessible & AI-ready. 📆 Nov 20 | 11 AM ET 🔗 Register: hubs.ly/Q03TvfRJ0 #AI #DataSecurity #Conduktor

Join us at The #CISOChapterUK 2025 this Nov. Visit our stand to see how Securiti's DataAI command center secures data AI to drive innovation. Don’t miss our masterclass on “Data Everywhere, Control Nowhere: Why #DSPM Matters when Securing Data & AI at Scale” #DataSecurity

You Can’t Protect What You Can’t See 👁️🛡️ Without discovery, your data risks multiply silently — across mailboxes, endpoints, databases, and the cloud. 👉 Request a PoC at support.decesoftware.com/geodi-dspm #DSPM #DataDiscovery #DataSecurity #Compliance #GEODI #Governance



Join Niki Dave on 18th Nov at 3 PM for a LIVE BLACKbox DEMO on essential data security for MSMEs. Learn to: Prevent leakage, ensure secure WFH, & instantly recover data—all while making IT costs predictable! Register Now: synersoft.in/webinars/18thN… #MSME #DataSecurity #BLACKbox

“Retrieving data. Wait a few seconds and try to cut or copy again.” 😬 When your data matters, you can’t afford to wait. Trust DES Technologies for secure, reliable, and instant access to your information. 🔗 des3tech.com #DataSecurity #DataRecovery #DES3Tech
“Retrieving data. Wait a few seconds and try to cut or copy again.” 😬 When it’s your business on the line, a few seconds can cost a lot. Trust DES Technologies for reliable, secure data solutions. 🔗 des3tech.com #DataSecurity #Backup

📊 See you at @AWSreInvent Dec 1 to 4 Lets fiind time to chat: hubs.li/Q03T2Sy00 DataDefender is a DSPM for cloud storage See live inventory, classification, activity, checks and evidence at Booth 1221 #AWSreInvent #AWSPartner #DSPM

Cost-effective pricing ✔️No hidden costs—no analysts, no hardware ✔️Fast deployment (under 15 minutes) ✔️Helps meet CMMC and NIST 800-171 requirements ✔️Proactive breach detection that protects your business and reputation Ready to see the ROI for yourself?…
Discover how Dell’s PowerProtect Data Domain elevates logical air gaps against data attackers. 🔒 Immutability that locks your data down 🛡️ Zero Trust Architecture to keep threats out 🧠 Advanced analytics to help ensure clean recovery del.ly/60177X4JR #iwork4dell

They showcased how vulnerable applications and exposed device lists can create serious risks for businesses, from data loss to account compromise. The demo highlighted both client-side prevention techniques and server-side monitoring, illustrating how layered security measures…



Data Domain is the world’s most secure and reliable foundation for cyber resilience. Strengthen your Zero Trust posture. Detect threats faster. Recover with confidence. del.ly/60177XZiV #iwork4dell

Today’s demo showcased one core truth: Security must be secure by design. It cannot be an afterthought. Build with security upfront, and constantly test for vulnerabilities across your entire IT estate. #SafaricomCyberSecuritySummit2025

Data Domain is the world’s most secure and reliable foundation for cyber resilience. Strengthen your Zero Trust posture. Detect threats faster. Recover with confidence. del.ly/60197n2Ff #iwork4dell

#WebinarAlert 🚀 What if you didn’t have to choose between data access & security? Join us to learn how a security-by-design architecture makes your data safe, accessible & AI-ready. 📆 Nov 20 | 11 AM ET 🔗 Register: hubs.ly/Q03SP3Jv0 #AI #DataSecurity #Conduktor

Something went wrong.
Something went wrong.
United States Trends
- 1. #FaithFreedomNigeria 1,002 posts
- 2. Good Wednesday 28.6K posts
- 3. Peggy 23.5K posts
- 4. #wednesdaymotivation 6,190 posts
- 5. #LosVolvieronAEngañar 1,073 posts
- 6. Hump Day 12.4K posts
- 7. #Wednesdayvibe 1,981 posts
- 8. Dearborn 295K posts
- 9. #hazbinhotelseason2 85.4K posts
- 10. Jessica Tisch N/A
- 11. Happy Hump 7,981 posts
- 12. Cory Mills 14.8K posts
- 13. For God 217K posts
- 14. Gettysburg Address N/A
- 15. $TGT 4,272 posts
- 16. Abel 17K posts
- 17. Grayson 7,719 posts
- 18. Ternopil 33.1K posts
- 19. Sewing 6,231 posts
- 20. Lilith 13.8K posts















