#defendcon search results
This advice about online storage applies no matter whether your "stuff" is in AWS, GCP, Azure, SaaS cloud content management, etc. #DefendCon #DefendCon2019

After a slide of Sisyphus pushing a boulder up a hill, this slide is all about proactive measures that reduce toil and act as digital "fire prevention." (this is a screenshot, lol) #DefendCon #DefendCon2019

"FIM should always work in concert with application whitelisting." Also, take your application inventory seriously. #DefendCon #DefendCon2019

Okay #DefendCon you been really good me. I enjoyed the lock picking village today and hope to be back next year. Now OFF to Atlanta I go time to start my Birthday shenanigans 🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳😁🥳😁😁😁
#DefendCon was amazing - but now it’s time to head to #STARWEST to do some more work on breaking down silos between dev + test + security + DevOps. See you soon??

Where on Earth is your "perimeter" in the cloud? It's defined by identity and access management. #DefendCon #DefendCon2019

Last but not least, some resources to go read more about Mac malware. The presenter says in her experience, vendors tend not to believe that Mac malware exists. #DefendCon #DefendCon2019

What makes for a process that can be automated? An unexpected bullet: a suitable process should tolerate some errors. #DefendCon #DefendCon2019

DefendCon 2019 was tons of fun! 5th place in the CTF. Lesson learned: I need to work on SQL injections. #defendcon #cmdnctrl #redteam

If you're bummed you missed out on #defendcon #defendcon2019 like I am, check out @infosecmagic's great live tweets of several talks
#DefendCon was amazing - but now it’s time to head to #STARWEST to do some more work on breaking down silos between dev + test + security + DevOps. See you soon??

In this picture there is a queer person, a Latina, a mom, a student, a veteran, a trans person, a neurodiverse person, a Jewish person, and the three incredible women of @ioactive who presented at #defendcon this week. Beyond proud of us for representing 💜 @FreqyXin @dawnisabel

I had an amazing time at #DefendCon honestly this has been an amazing conference with people who look like me!!! I learned so much and made some really awesome connections. This conference is something special.
Okay #DefendCon you been really good me. I enjoyed the lock picking village today and hope to be back next year. Now OFF to Atlanta I go time to start my Birthday shenanigans 🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳🥳😁🥳😁😁😁
"Apply to any security job: Many want 3 years experience but apply anyway." #DefendCon #DefendCon2019
By the numbers, this pipeline has been great for bringing in diverse talent. One hypothesis on why this has been effective: this pipeline can "get people before they leave the industry." #DefendCon #DefendCon2019

The value add for efficiency is tremendous: "18,000 tickets/year with 8 people." There's a second slide not included here on the positive impact to the talent pipeline. #DefendCon #DefendCon2019

What makes for a process that can be automated? An unexpected bullet: a suitable process should tolerate some errors. #DefendCon #DefendCon2019

Partial notes on how Google's program takes entry level folks and turns them into security engineers. First up: the current problems with security hiring #DefendCon #DefendCon2019

Really enjoying listening to Dawn talk about her adventures in getting an Apple Watch jailbreak, so interesting #DefendCon
My #DefendCon FOMO was at a manageable level until I say this thread, soooooo much YES YES YES 🤩 in these slides!
Last but not least, some resources to go read more about Mac malware. The presenter says in her experience, vendors tend not to believe that Mac malware exists. #DefendCon #DefendCon2019

Running strings on the second Shlayer sample downloads kittens[.]zip from somewhere (!!!) Why didn't they name this malware Kittens.dmg? #DefendCon #DefendCon2019
The script hardcoded a URL base to curl the second-stage. From me, here's some IOCs from about 8 months ago for Shlayer released by Carbon Black's TAU. #DefendCon #DefendCon2019 github.com/carbonblack/ta…
It was only today that I found out that Shlayer's code to download the second-stage is written in Python. This makes the static analysis pretty straightforward, the authors even used pylint. #DefendCon #DefendCon2019
Want to open a .plist with Python? plistlib is your friend. (Note from me: if you're not up to using Python, a text editor is fine) #DefendCon #DefendCon2019
Big love for Patrick Wardle and Objective-See on this slide. Don't forget that many malware families grep for Little Snitch, though. #DefendCon #DefendCon2019

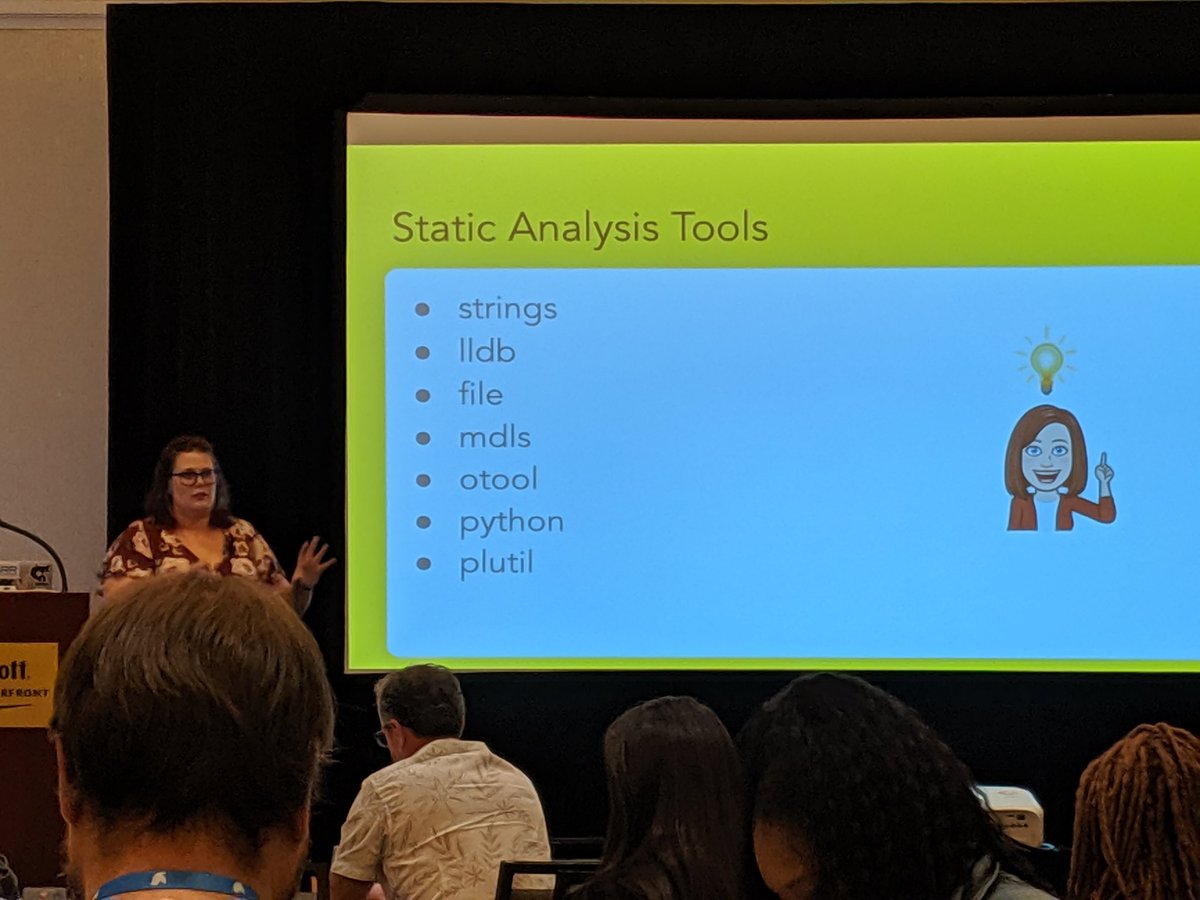
Static analysis tools for Mac malware. Python can script many of these tasks for you, though individual projects are outside of the scope of this talk. #DefendCon #DefendCon2019
This advice about online storage applies no matter whether your "stuff" is in AWS, GCP, Azure, SaaS cloud content management, etc. #DefendCon #DefendCon2019

HEY! Come join us at our networking event at Lucky Strike in Bellevue for fun games and networking! #Defendcon #womenintech #womeninstem #networking #diversitymatters #securityconference

You can do it! Get your logs flowing, take appropriate measures to prepare. #DefendCon #DefendCon2019

Are containers being attacked? Indeed! The interesting thing is that the target is the compute, not the containers themselves @annnwallace #DefendCon

Your options for mitigating something strange in a container, in order from low to high impact #DefendCon #DefendCon2019

Keystone of the talk: 4 kinds of logs that you need to collect and understand for container forensics #DefendCon #DefendCon2019

After a slide of Sisyphus pushing a boulder up a hill, this slide is all about proactive measures that reduce toil and act as digital "fire prevention." (this is a screenshot, lol) #DefendCon #DefendCon2019

"FIM should always work in concert with application whitelisting." Also, take your application inventory seriously. #DefendCon #DefendCon2019

Rocking my #DefendCon shirt today. Couldn’t make it to the con (yay work!) but super proud to support such a badass group! If you are at the con today , make sure to thank @datSecuritychic for all her talent and efforts to make it all happen! #secConf

Where on Earth is your "perimeter" in the cloud? It's defined by identity and access management. #DefendCon #DefendCon2019

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 111K posts
- 2. Packers 66.9K posts
- 3. Packers 66.9K posts
- 4. Jordan Love 10.6K posts
- 5. Patullo 7,911 posts
- 6. Jalen 20.7K posts
- 7. John Cena 90.1K posts
- 8. Pistons 14K posts
- 9. #GoPackGo 6,679 posts
- 10. Bo Melton N/A
- 11. #MondayNightFootball 1,691 posts
- 12. Matt LaFleur 2,959 posts
- 13. Green Bay 14.9K posts
- 14. AJ Brown 4,103 posts
- 15. Jenkins 5,448 posts
- 16. #RawOnNetflix 2,604 posts
- 17. Nikki Bella 7,227 posts
- 18. Cavs 9,253 posts
- 19. Gunther 7,181 posts
- 20. Donovan Mitchell 2,496 posts



























