#defendcon2019 search results
This advice about online storage applies no matter whether your "stuff" is in AWS, GCP, Azure, SaaS cloud content management, etc. #DefendCon #DefendCon2019

"FIM should always work in concert with application whitelisting." Also, take your application inventory seriously. #DefendCon #DefendCon2019

After a slide of Sisyphus pushing a boulder up a hill, this slide is all about proactive measures that reduce toil and act as digital "fire prevention." (this is a screenshot, lol) #DefendCon #DefendCon2019

Where on Earth is your "perimeter" in the cloud? It's defined by identity and access management. #DefendCon #DefendCon2019

TODAY'S the DAY! #Defendcon2019 registration starts in just a few hours. Then, it's two days of jammed packed fun: workshops, talks, keynotes, resume reviews, and conversations with peers!
Last but not least, some resources to go read more about Mac malware. The presenter says in her experience, vendors tend not to believe that Mac malware exists. #DefendCon #DefendCon2019

What makes for a process that can be automated? An unexpected bullet: a suitable process should tolerate some errors. #DefendCon #DefendCon2019

An open source .Net CORE fuzzer? Yessssss. #DefendCon2019 CC: @queenofcode @MaximRouiller @AbelSquidHead

You're going to hate it, but you absolutely have to scrutinize what your powerful service accounts are doing. "Code repos are the new sticky notes." #DefendCon #DefendCon2019

The value add for efficiency is tremendous: "18,000 tickets/year with 8 people." There's a second slide not included here on the positive impact to the talent pipeline. #DefendCon #DefendCon2019

Big love for Patrick Wardle and Objective-See on this slide. Don't forget that many malware families grep for Little Snitch, though. #DefendCon #DefendCon2019

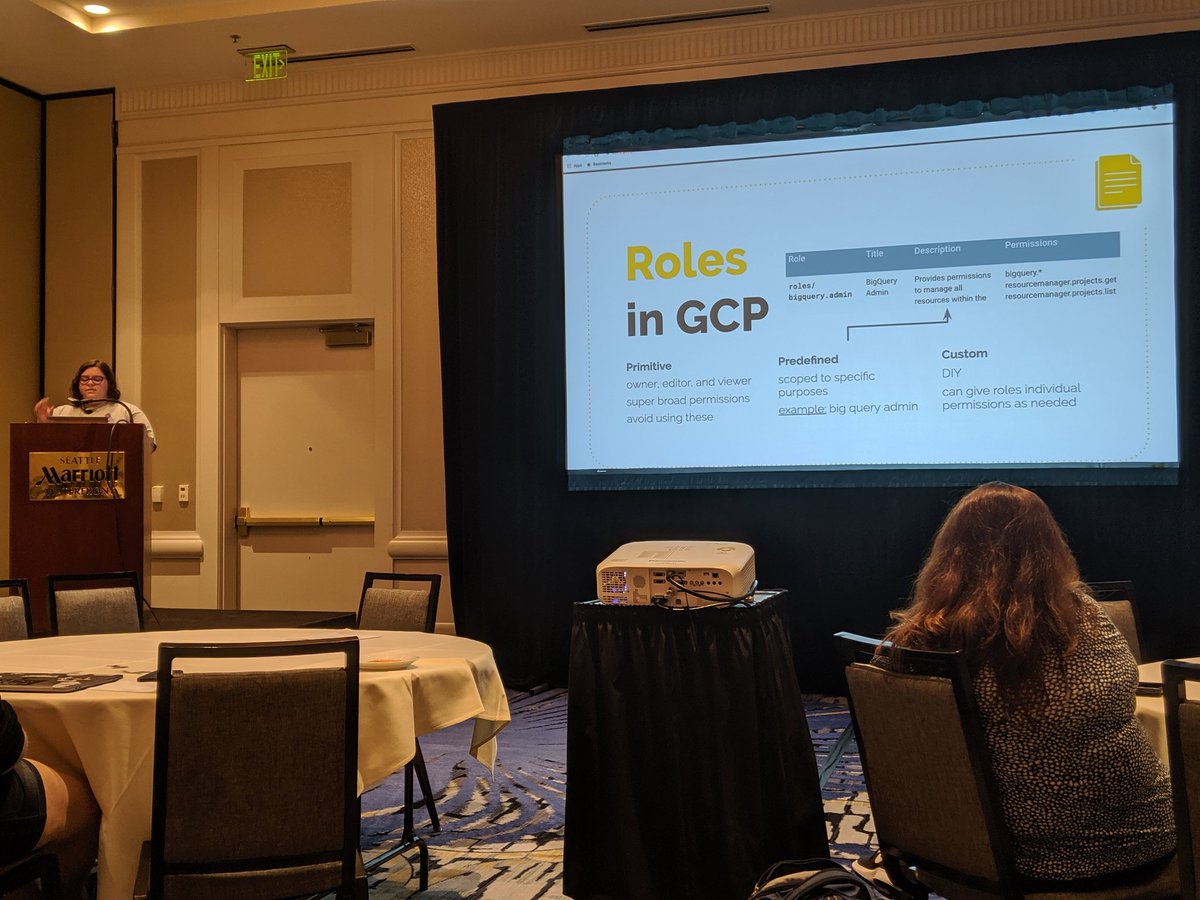
Architecting IAM effectively is going to be different depending on which cloud you're in. Here's the basics on how GCP defines roles. #DefendCon #DefendCon2019
SO grateful for #DefendCon2019. I spent the whole day in the CTF village and it was the BEST! Thank you to all the staff!

By the numbers, this pipeline has been great for bringing in diverse talent. One hypothesis on why this has been effective: this pipeline can "get people before they leave the industry." #DefendCon #DefendCon2019

"I assume all of my code is insecure, until proven otherwise. I've never been proven otherwise." @queenofcode is teaching us and making us laugh at the same time. #DefendCon2019

Up first APPLYING EPHEMERALITY to Cloud Access Management youtube.com/watch?v=U8b-TY… @Snapchat #defendcon2019
PSSSST Guess what we just got!!!! Videos from #DefendCon2019. I'll be uploading them to my Youtube channel over the next few days so check them out! #womenintech #womenincyber #womenwhocode #diversitymatters youtu.be/0PGQbf0EDfc
If you're bummed you missed out on #defendcon #defendcon2019 like I am, check out @infosecmagic's great live tweets of several talks
Really enjoyed #DefendCon2019! It was my first security conference and I learned quite a bit, as well as participated in my first CTF! :D
Really like this anti-binary, pro-collaboration take on #cybersecurity defense. Slides below. (Standby for next tweet, down the gender politics rathole and maybe NSFW too.) HT 🏆🥇🎉 @shehackspurple @infosecmagic @DefendCon @kuppingercole #cybersec #defendcon2019
Full slides are here!! #DefendCon #DefendCon2019 slideshare.net/TanyaJanca/pur…
*merges track 1 and track 2 together from 2:30-3:30 PM* It's time for our AMA panel on marginalized ethnicity, marginalized gender and other pressing issues in the technology space. It's a safe space to ask questions, grow, and learn together. #DefendCon2019

"Apply to any security job: Many want 3 years experience but apply anyway." #DefendCon #DefendCon2019
By the numbers, this pipeline has been great for bringing in diverse talent. One hypothesis on why this has been effective: this pipeline can "get people before they leave the industry." #DefendCon #DefendCon2019

The value add for efficiency is tremendous: "18,000 tickets/year with 8 people." There's a second slide not included here on the positive impact to the talent pipeline. #DefendCon #DefendCon2019

What makes for a process that can be automated? An unexpected bullet: a suitable process should tolerate some errors. #DefendCon #DefendCon2019

Partial notes on how Google's program takes entry level folks and turns them into security engineers. First up: the current problems with security hiring #DefendCon #DefendCon2019

Next set of talks at #DefendCon2019 day two from 1-2 PM: Track 1 • Adventures in Apple Watch Jailbreaking Track 2 • Targeted Advertising – The vicious internet economy at the cost of our privacy • Noobs: How to Train Security Engineers
Last but not least, some resources to go read more about Mac malware. The presenter says in her experience, vendors tend not to believe that Mac malware exists. #DefendCon #DefendCon2019

🤗. So many awesome humans at #DefendCon2019!
Running strings on the second Shlayer sample downloads kittens[.]zip from somewhere (!!!) Why didn't they name this malware Kittens.dmg? #DefendCon #DefendCon2019
The script hardcoded a URL base to curl the second-stage. From me, here's some IOCs from about 8 months ago for Shlayer released by Carbon Black's TAU. #DefendCon #DefendCon2019 github.com/carbonblack/ta…
It was only today that I found out that Shlayer's code to download the second-stage is written in Python. This makes the static analysis pretty straightforward, the authors even used pylint. #DefendCon #DefendCon2019
Want to open a .plist with Python? plistlib is your friend. (Note from me: if you're not up to using Python, a text editor is fine) #DefendCon #DefendCon2019
Big love for Patrick Wardle and Objective-See on this slide. Don't forget that many malware families grep for Little Snitch, though. #DefendCon #DefendCon2019

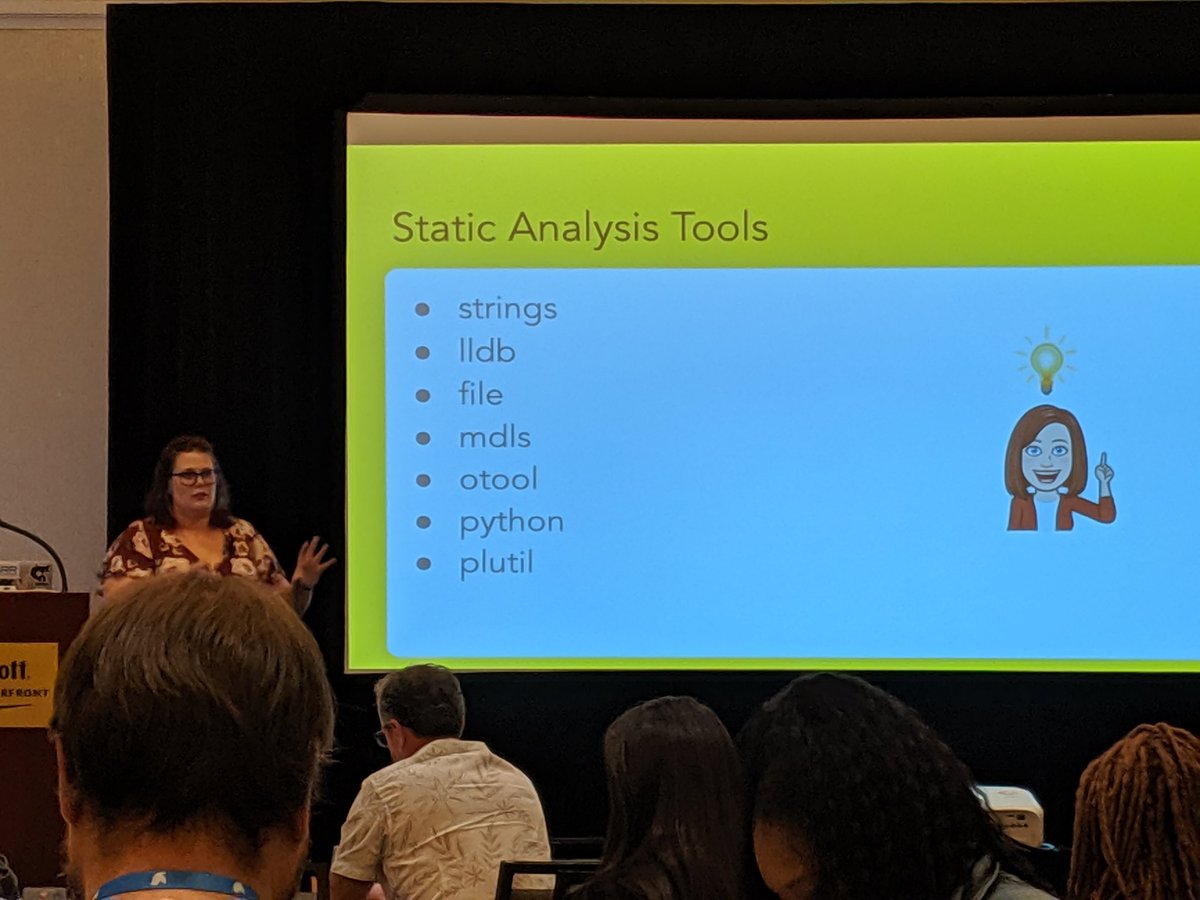
Static analysis tools for Mac malware. Python can script many of these tasks for you, though individual projects are outside of the scope of this talk. #DefendCon #DefendCon2019
Something went wrong.
Something went wrong.
United States Trends
- 1. Clay Higgins 20.5K posts
- 2. Grisham 2,985 posts
- 3. Saudi 243K posts
- 4. Peggy 6,381 posts
- 5. Dominguez 3,096 posts
- 6. #UNBarbie 13.9K posts
- 7. Cashman N/A
- 8. Bellinger 2,074 posts
- 9. Gemini 3 48.7K posts
- 10. Mary Bruce 4,041 posts
- 11. Nicki 115K posts
- 12. Jamal Khashoggi 32.8K posts
- 13. The House 544K posts
- 14. Gleyber Torres 1,159 posts
- 15. Shota 8,957 posts
- 16. Salman 76.6K posts
- 17. Woodruff 1,162 posts
- 18. #UnitedNationsBarbie 12.1K posts
- 19. Scotland 42.3K posts
- 20. Robinhood 5,413 posts














