#evilcrackz نتائج البحث
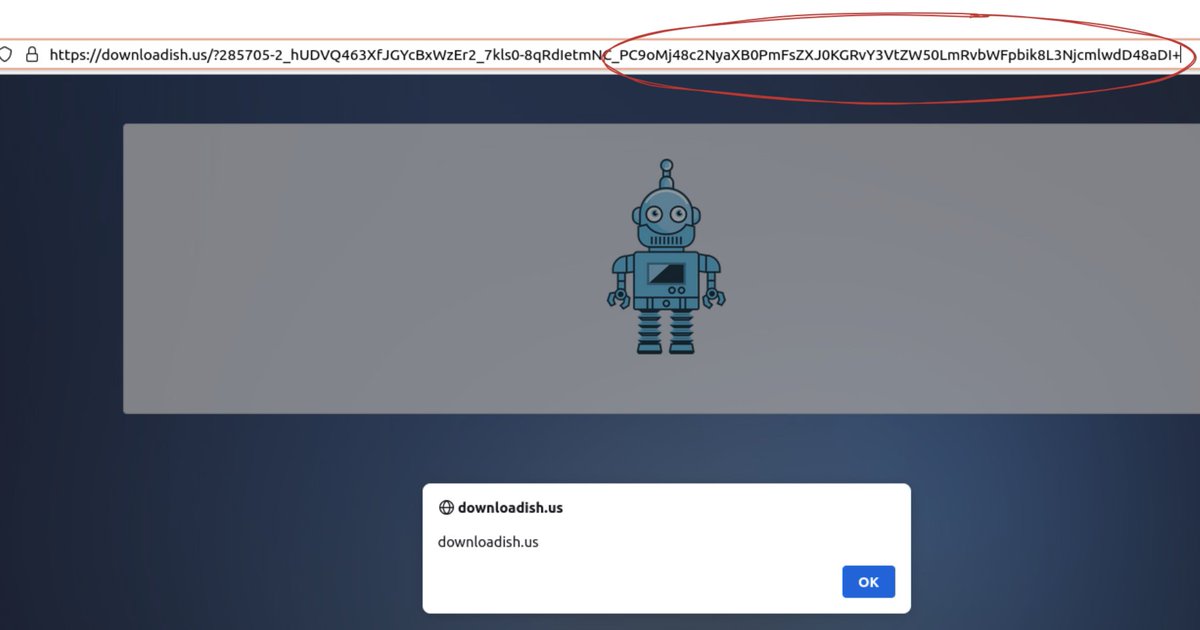
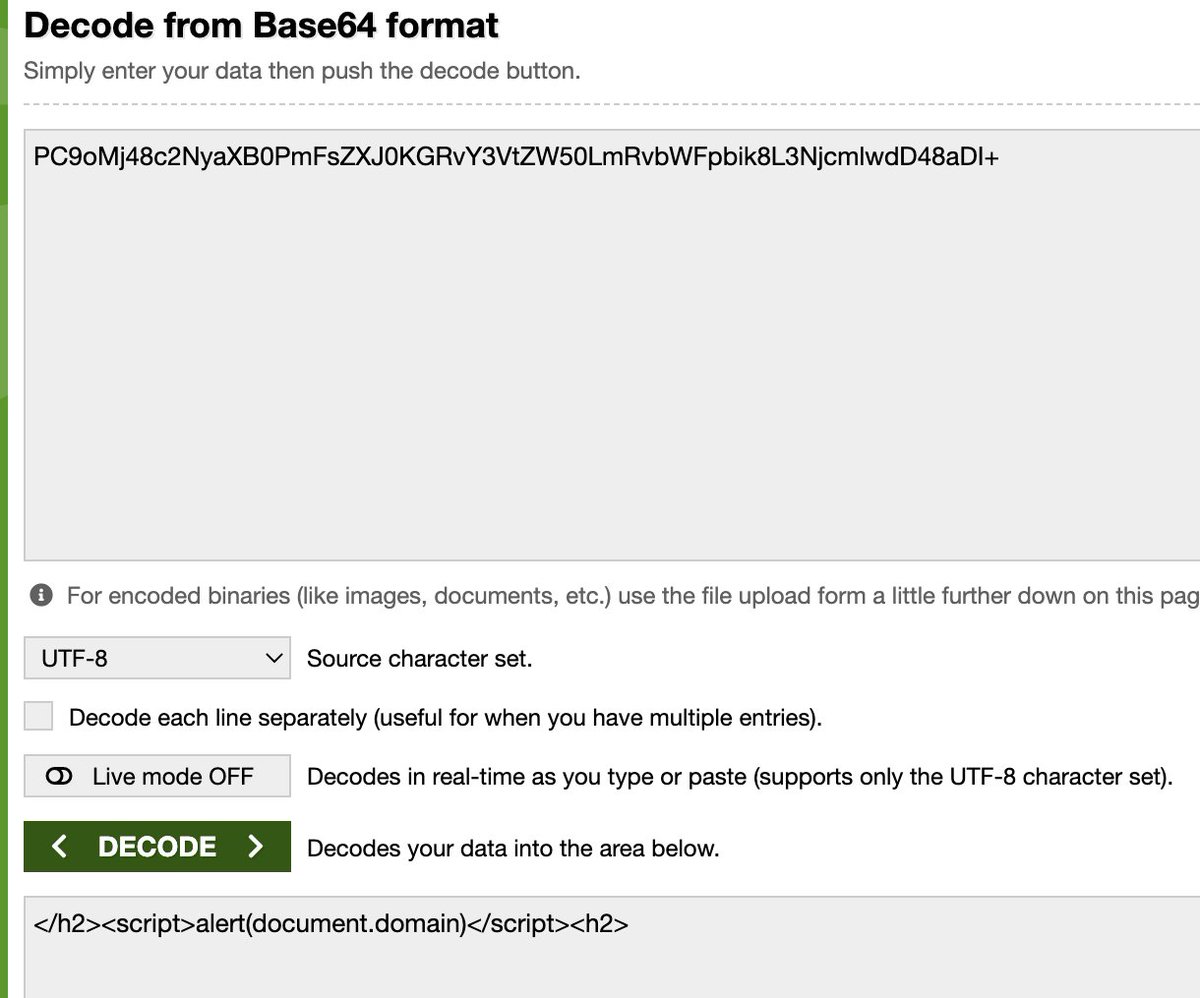
#Evilcrackz (#Vidar) malware has a dynamic page, which fools user to download malware with a message. Turns out that last parameter in URL after _ is base64 for message shown to the victim. Replacing this with "PC9oMj48c2..", which is base64 for document.domain,leads to XSS !
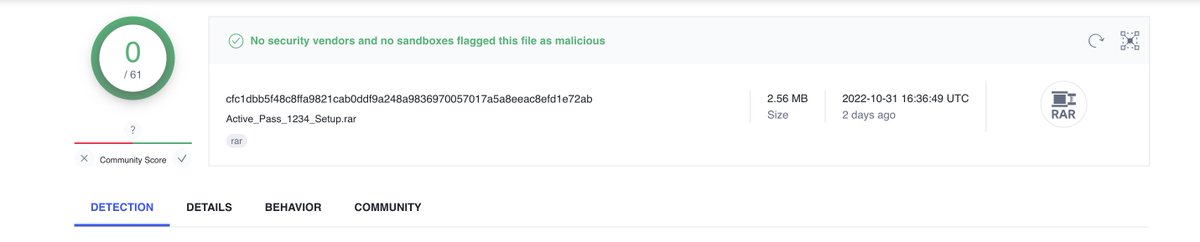
From last 10 days this person has been abusing Github to spread #Vidar ( #EvilCrackz ) These will be password protected but as the name says, the password is 1234. AV doesnt' know the password so its 0 on VT. But the victim knows 1234 and gets infected.

Hmmmmm, could it be weird that your average crack download site has more than 6k inbound links ? #SEOpoisoning #EvilCrackz

Current stats for #EvilCrackz: - 462 malicious initial sides found - nearly 10.000 websites manually categorized into good, evil and suspicious - Custom crawler running to hunt new initial pages. - Several important pieces of intel collected. And the hunt continues 😈

Me thinking I could clean my logs of all the #SEO poisoning the #EvilCrackz sites throw at me I am kinda giving up on this... Anybody a better idea for filtering ? 1 in 20 links might be important, so a block based tld is impossible @malwrhunterteam @KevTheHermit @Ledtech3

#EvilCrackz with another change in #TTP s. Today coming in with Eziriz's .Net Reactor loading 3 different #payload s . tria.ge/221220-agsp7sb… Seems like: #Vidar #Stealer + #Laplas #Clipper + 1 more ? Anybody can help identify bebra.exe ? tria.ge/221220-aqymtab… IoC below.

For more info see: tria.ge/230221-nla8lsg… #Pikabot #EvilCrackz cc: @aaqeel87 @crep1x @ankit_anubhav @0xToxin @James_inthe_box
I can further confirm that I have seen log collections and victim counts of 45.000 victims with one campaign of #EvilCrackz and 85.000 logs in a recent #SectopRat campaign observed. If you have not read it, the link is here: link.medium.com/rqt9LE5y1wb
link.medium.com
A long way to SectopRat
Investigating a highly obfuscated stealer sample
bazaar.abuse.ch/sample/837d4db… Sample for reference Pass = 1234 Vidar Version 55.8 #EvilCrackz
First time i observe #LummaC2 #Stealer being spread via #EvilCrackz. tria.ge/230303-y6p8daa… #C2: hxxp://82.118.23.50/c2sock cc: @aaqeel87 @crep1x @0xToxin @ankit_anubhav @AnFam17 @James_inthe_box
Today for the first time I observe #EvilCrackz using #Discord CDN. hxxps://cdn.discordapp.com/attachments/1073630551627542569/1086965268653289543/The_LatestApps_There.zip is #Raccoonv2 / #RecordBreaker #Stealer tria.ge/230319-pnfrjsa… Sample template:…
Observing an unknown binary being pushed as part of a #Raccoonv2 / #RecordBreaker campaign since yesterday. VT is also not really helpful. Anybody an idea what this is? Campaign: tria.ge/230303-y6mr9ab… Binary: tria.ge/230303-zksbaab… #EvilCrackz
#cryptbot sample found. Tria.ge: tria.ge/230102-ahyylsg… C2: hxxp://luvasm712.top/gate.php Something for you to investigate @500mk500 ;) And for others to block ! #EvilCrackz
More #cryptbot tria.ge/230112-28e2zaf… C2: hxxp://avosma45.top/gate.php @500mk500 you know the drill ;) Part of #EvilCrackz
If I was to release some research into SEO-poisend #malware sharing sites, would you rather like: #EvilCrackz
New #cryptbot #C2 observed as part of #EvilCrackz: C2: hxxp://tystne110[.]top/gate.php Additional #ioc / #payload : hxxp://pabryd01[.]top/firlot.dat
This is part of the #EvilCrackz campaign I am currently investigating... Its only the tip of the Iceberg...
There are also many more things to come on the #EvilCrackz research which is now on and going for several months. I hope I can bring it to an end soon, sadly Twitter is only place 3 in my daily obligations besides work and university. But there is a lot done already. 6/x
Today for the first time I observe #EvilCrackz using #Discord CDN. hxxps://cdn.discordapp.com/attachments/1073630551627542569/1086965268653289543/The_LatestApps_There.zip is #Raccoonv2 / #RecordBreaker #Stealer tria.ge/230319-pnfrjsa… Sample template:…
Observing an unknown binary being pushed as part of a #Raccoonv2 / #RecordBreaker campaign since yesterday. VT is also not really helpful. Anybody an idea what this is? Campaign: tria.ge/230303-y6mr9ab… Binary: tria.ge/230303-zksbaab… #EvilCrackz
First time i observe #LummaC2 #Stealer being spread via #EvilCrackz. tria.ge/230303-y6p8daa… #C2: hxxp://82.118.23.50/c2sock cc: @aaqeel87 @crep1x @0xToxin @ankit_anubhav @AnFam17 @James_inthe_box
For more info see: tria.ge/230221-nla8lsg… #Pikabot #EvilCrackz cc: @aaqeel87 @crep1x @ankit_anubhav @0xToxin @James_inthe_box
There are also many more things to come on the #EvilCrackz research which is now on and going for several months. I hope I can bring it to an end soon, sadly Twitter is only place 3 in my daily obligations besides work and university. But there is a lot done already. 6/x
I can further confirm that I have seen log collections and victim counts of 45.000 victims with one campaign of #EvilCrackz and 85.000 logs in a recent #SectopRat campaign observed. If you have not read it, the link is here: link.medium.com/rqt9LE5y1wb
link.medium.com
A long way to SectopRat
Investigating a highly obfuscated stealer sample
Did some statistics today. During the last months I have sorted more than 14.000 websites visiting each individual website to look at its content. I judged around 12.000 as clean, but more than 1100 are part of #EvilCrackz related campaigns. And many still to crawl and sort...
More #cryptbot tria.ge/230112-28e2zaf… C2: hxxp://avosma45.top/gate.php @500mk500 you know the drill ;) Part of #EvilCrackz
Seems I have stubled upon #NullMixer #Loader spreading through some #EvilCrackz sites. There is actually an article by @Securelist from 09.2022 that describes this behavior. Some IoC align securelist.com/nullmixer-oodl… Sadly it seems they opted for VMprotect. tria.ge/230111-r37jxsd…
@crep1x have you seen that some #EvilCrackz actors are opting for a download of a .txt file with url for the download in it plus password ? Wondering why they opt for this technique...
Btw I have to give a huge shoutout to: arraythis.com by #populu It got so useful while working on #EvilCrackz that I actually have a makro key to open it now ^^
Yep, will add the missing ones to my list of more than 460 initial domains. This is what I call #EvilCrackz :)
Current stats for #EvilCrackz: - 462 malicious initial sides found - nearly 10.000 websites manually categorized into good, evil and suspicious - Custom crawler running to hunt new initial pages. - Several important pieces of intel collected. And the hunt continues 😈

#cryptbot sample found. Tria.ge: tria.ge/230102-ahyylsg… C2: hxxp://luvasm712.top/gate.php Something for you to investigate @500mk500 ;) And for others to block ! #EvilCrackz
Current and previous #C2 from #Vidar 634: hxxps://t.me/robloxblackl hxxps://steamcommunity.com/profiles/76561199458928097 <- Look at previous names 116.202.4[.]70:80 157.90.244[.]205:80 116.203.3[.]152:80 Triage: tria.ge/230101-s3fa4sc… #EvilCrackz
Some pretty #evasive #EvilCrackz here: tria.ge/221223-tzarwsb… Anybody with some #Intel on 94.131.98[.]99 94.131.98[.]100 ? VT has literally nothing :/ @0xToxin @ankit_anubhav @crep1x
Finally back to sorting #EvilCrackz #SEO websites. Amazing to see how many #CAD programs are out there... And don't even get me started in Music Studio Software... 👀
#EvilCrackz with another change in #TTP s. Today coming in with Eziriz's .Net Reactor loading 3 different #payload s . tria.ge/221220-agsp7sb… Seems like: #Vidar #Stealer + #Laplas #Clipper + 1 more ? Anybody can help identify bebra.exe ? tria.ge/221220-aqymtab… IoC below.

Interesting #malware infection chain of an #EvilCrackz sample. Guessing it is #Vidar, however despite the usual there is an intermediate step using #hastebin. Chain: mega uplaod -> pw protected .zip -> hastebin -> #Vidar #Stealer ? Tweet 2 with the IoC below! 1/2
What are #Traffers ? @sekoia_io published a post on this back in August 2022. It makes pretty clear what #EvilCrackz is part of. Nice read and a good explanation. @ankit_anubhav @crep1x @0xToxin
#Evilcrackz (#Vidar) malware has a dynamic page, which fools user to download malware with a message. Turns out that last parameter in URL after _ is base64 for message shown to the victim. Replacing this with "PC9oMj48c2..", which is base64 for document.domain,leads to XSS !


From last 10 days this person has been abusing Github to spread #Vidar ( #EvilCrackz ) These will be password protected but as the name says, the password is 1234. AV doesnt' know the password so its 0 on VT. But the victim knows 1234 and gets infected.


Current stats for #EvilCrackz: - 462 malicious initial sides found - nearly 10.000 websites manually categorized into good, evil and suspicious - Custom crawler running to hunt new initial pages. - Several important pieces of intel collected. And the hunt continues 😈

Hmmmmm, could it be weird that your average crack download site has more than 6k inbound links ? #SEOpoisoning #EvilCrackz

#EvilCrackz with another change in #TTP s. Today coming in with Eziriz's .Net Reactor loading 3 different #payload s . tria.ge/221220-agsp7sb… Seems like: #Vidar #Stealer + #Laplas #Clipper + 1 more ? Anybody can help identify bebra.exe ? tria.ge/221220-aqymtab… IoC below.

Me thinking I could clean my logs of all the #SEO poisoning the #EvilCrackz sites throw at me I am kinda giving up on this... Anybody a better idea for filtering ? 1 in 20 links might be important, so a block based tld is impossible @malwrhunterteam @KevTheHermit @Ledtech3

Something went wrong.
Something went wrong.
United States Trends
- 1. Bears 89.3K posts
- 2. Jake Moody 13.7K posts
- 3. Snell 24.3K posts
- 4. Caleb 49.2K posts
- 5. Falcons 51.3K posts
- 6. Bills 141K posts
- 7. Josh Allen 26.6K posts
- 8. Jayden 22.9K posts
- 9. #BearDown 2,369 posts
- 10. phil 175K posts
- 11. Swift 290K posts
- 12. Happy Birthday Charlie 8,474 posts
- 13. Ben Johnson 4,433 posts
- 14. Joji 29.7K posts
- 15. #Dodgers 15.3K posts
- 16. Turang 4,321 posts
- 17. Troy Aikman 6,517 posts
- 18. Roki 6,101 posts
- 19. Bijan 32.9K posts
- 20. Brewers 48.5K posts




