#macrosheet search results
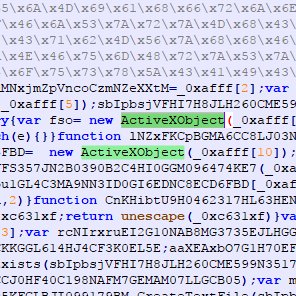
malicious #xls (VT 0/60) #obfuscated macro in a very hidden #macrosheet -> #urlmon -> load dll (#rundll32 #DllRegisterServer) No webquery obj -> seems a shift hxxps://pxdgcvnsb.xyz/ajt1eg4fh (active) xls: 1ed44778fbb022f6ab1bb8bd30849c9e4591dc16f9c0ac9d99cbf2fa3195b326



#yara rule to find #xls documents with hidden/very-hidden #macrosheet|s containing macro obfuscated by utilizing CHAR function (e.g. #Zloader excel documents): pastebin.com/V8SGgdZL


#malicious #xls (Excel 4.0 macro) has 3 #macrosheet|s. Uses CONCATENATE to create #msiexec command to dl & exec a msi file (hxxp://slemend.com/cykom1) hybrid-analysis.com/sample/59fbcd1… #PE in msi virustotal.com/#/file/2ca2285…




#malicious #xls (VT 5/57) with a hidden #macrosheet (no vba macro) -> #msiexec to dl & install a #msi file Similar to the instance that we analyzed here: blog.inquest.net/blog/2019/01/2… New: used concatenate func to evade but seems to be a failure (pic2) virustotal.com/#/file/9d218e9…


#OOXML #Macrosheet|s always start with <xm:macrosheet> elm? Not really, the root elm can also be <worksheet>! #Emottet 9ddac5c4281f20c330439fae9bcbd8d6693b80083fa10894bb9ce002c2015399 Update #xlmdeobfuscator #PyPI github.com/DissectMalware… H/T @bigmacjpg for raising the issue



Can we run a command with a #XLSM doc without using #VBA? Yes, #macrosheet (it supports Excel 4.0 formula macros! macro is in plaintext) What about SYmbolic LinK? #SLK also support formula macros! related: HT @decalage2 cc: @pedramamini @InQuest



Interesting #malicious #excel (virustotal.com/en/file/98e469…) uses #xlm #microsheet, an outdates technology, to run commands (no #vba). @pedramamini and I did an in-depth study on it. We also tried to demystify the xlm macrosheet internals (the format). Please read our article.
Seems sbody is listening new #malicious #xls attempts to evade No 'very hidden (02)' #macrosheet and no saved default values hxxp://167.179.86.255/rb1 Improved over But still I found U! hybrid-analysis.com/sample/90c7f59… cc: @DidierStevens @pedramamini @InQuest




Interesting vba-less malicious excel file with interesting excel macro (macrosheet). Relied on concatenate func to construct its msiexec command but it is a failure as the whole command has already precomputed and saved in the excel file
"RT RT InQuest: #malicious #xls (VT 5/57) with a hidden #macrosheet (no vba macro) -> #msiexec to dl & install a #msi file Similar to the instance that we analyzed here: blog.inquest.net/blog/2019/01/2… New: used concatenate func to evade but seems to be a fai… https://t.co/ZSBWrzTvnw"


outdated* #macrosheet* to my future self: at least read twice looking for typos before hitting tweet button!
Another short video is out: youtube.com/watch?v=QBoj6G… Deobfuscating macro in a very hidden #macrosheet (#Zloader) using two methods: 1⃣using Notepad++ with macros 2⃣executing XLM macro in a controlled way #xls 889a2d77eeb14a6f1273c5c6d2544a56f40835be94925be4edc57ed95a0849e6

youtube.com
YouTube
Malware Analysis in Action - Episode 2
Konfigurationsvarianten schnell und einfach erzeugen mit dem DPS MacroSheet Konfigurator für SOLIDWORKS. Mehr Informationen und Download:bit.ly/2BkAjkf#SOLIDW… #DPS #MacroSheet #Konfigurator lnkd.in/deNmNmk lnkd.in/eqK6Tcc
#yara rule to find #xls documents with hidden/very-hidden #macrosheet|s containing macro obfuscated by utilizing CHAR function (e.g. #Zloader excel documents): pastebin.com/V8SGgdZL


Another short video is out: youtube.com/watch?v=QBoj6G… Deobfuscating macro in a very hidden #macrosheet (#Zloader) using two methods: 1⃣using Notepad++ with macros 2⃣executing XLM macro in a controlled way #xls 889a2d77eeb14a6f1273c5c6d2544a56f40835be94925be4edc57ed95a0849e6

youtube.com
YouTube
Malware Analysis in Action - Episode 2
malicious #xls (VT 0/60) #obfuscated macro in a very hidden #macrosheet -> #urlmon -> load dll (#rundll32 #DllRegisterServer) No webquery obj -> seems a shift hxxps://pxdgcvnsb.xyz/ajt1eg4fh (active) xls: 1ed44778fbb022f6ab1bb8bd30849c9e4591dc16f9c0ac9d99cbf2fa3195b326



#malicious #xls (Excel 4.0 macro) has 3 #macrosheet|s. Uses CONCATENATE to create #msiexec command to dl & exec a msi file (hxxp://slemend.com/cykom1) hybrid-analysis.com/sample/59fbcd1… #PE in msi virustotal.com/#/file/2ca2285…




Seems sbody is listening new #malicious #xls attempts to evade No 'very hidden (02)' #macrosheet and no saved default values hxxp://167.179.86.255/rb1 Improved over But still I found U! hybrid-analysis.com/sample/90c7f59… cc: @DidierStevens @pedramamini @InQuest




Interesting vba-less malicious excel file with interesting excel macro (macrosheet). Relied on concatenate func to construct its msiexec command but it is a failure as the whole command has already precomputed and saved in the excel file
"RT RT InQuest: #malicious #xls (VT 5/57) with a hidden #macrosheet (no vba macro) -> #msiexec to dl & install a #msi file Similar to the instance that we analyzed here: blog.inquest.net/blog/2019/01/2… New: used concatenate func to evade but seems to be a fai… https://t.co/ZSBWrzTvnw"


#malicious #xls (VT 5/57) with a hidden #macrosheet (no vba macro) -> #msiexec to dl & install a #msi file Similar to the instance that we analyzed here: blog.inquest.net/blog/2019/01/2… New: used concatenate func to evade but seems to be a failure (pic2) virustotal.com/#/file/9d218e9…


Can we run a command with a #XLSM doc without using #VBA? Yes, #macrosheet (it supports Excel 4.0 formula macros! macro is in plaintext) What about SYmbolic LinK? #SLK also support formula macros! related: HT @decalage2 cc: @pedramamini @InQuest



Interesting #malicious #excel (virustotal.com/en/file/98e469…) uses #xlm #microsheet, an outdates technology, to run commands (no #vba). @pedramamini and I did an in-depth study on it. We also tried to demystify the xlm macrosheet internals (the format). Please read our article.
outdated* #macrosheet* to my future self: at least read twice looking for typos before hitting tweet button!
Konfigurationsvarianten schnell und einfach erzeugen mit dem DPS MacroSheet Konfigurator für SOLIDWORKS. Mehr Informationen und Download:bit.ly/2BkAjkf#SOLIDW… #DPS #MacroSheet #Konfigurator lnkd.in/deNmNmk lnkd.in/eqK6Tcc
malicious #xls (VT 0/60) #obfuscated macro in a very hidden #macrosheet -> #urlmon -> load dll (#rundll32 #DllRegisterServer) No webquery obj -> seems a shift hxxps://pxdgcvnsb.xyz/ajt1eg4fh (active) xls: 1ed44778fbb022f6ab1bb8bd30849c9e4591dc16f9c0ac9d99cbf2fa3195b326



#yara rule to find #xls documents with hidden/very-hidden #macrosheet|s containing macro obfuscated by utilizing CHAR function (e.g. #Zloader excel documents): pastebin.com/V8SGgdZL


#malicious #xls (Excel 4.0 macro) has 3 #macrosheet|s. Uses CONCATENATE to create #msiexec command to dl & exec a msi file (hxxp://slemend.com/cykom1) hybrid-analysis.com/sample/59fbcd1… #PE in msi virustotal.com/#/file/2ca2285…




#OOXML #Macrosheet|s always start with <xm:macrosheet> elm? Not really, the root elm can also be <worksheet>! #Emottet 9ddac5c4281f20c330439fae9bcbd8d6693b80083fa10894bb9ce002c2015399 Update #xlmdeobfuscator #PyPI github.com/DissectMalware… H/T @bigmacjpg for raising the issue



Can we run a command with a #XLSM doc without using #VBA? Yes, #macrosheet (it supports Excel 4.0 formula macros! macro is in plaintext) What about SYmbolic LinK? #SLK also support formula macros! related: HT @decalage2 cc: @pedramamini @InQuest



Interesting #malicious #excel (virustotal.com/en/file/98e469…) uses #xlm #microsheet, an outdates technology, to run commands (no #vba). @pedramamini and I did an in-depth study on it. We also tried to demystify the xlm macrosheet internals (the format). Please read our article.
Seems sbody is listening new #malicious #xls attempts to evade No 'very hidden (02)' #macrosheet and no saved default values hxxp://167.179.86.255/rb1 Improved over But still I found U! hybrid-analysis.com/sample/90c7f59… cc: @DidierStevens @pedramamini @InQuest




Interesting vba-less malicious excel file with interesting excel macro (macrosheet). Relied on concatenate func to construct its msiexec command but it is a failure as the whole command has already precomputed and saved in the excel file
#malicious #xls (VT 5/57) with a hidden #macrosheet (no vba macro) -> #msiexec to dl & install a #msi file Similar to the instance that we analyzed here: blog.inquest.net/blog/2019/01/2… New: used concatenate func to evade but seems to be a failure (pic2) virustotal.com/#/file/9d218e9…


"RT RT InQuest: #malicious #xls (VT 5/57) with a hidden #macrosheet (no vba macro) -> #msiexec to dl & install a #msi file Similar to the instance that we analyzed here: blog.inquest.net/blog/2019/01/2… New: used concatenate func to evade but seems to be a fai… https://t.co/ZSBWrzTvnw"


Something went wrong.
Something went wrong.
United States Trends
- 1. Good Thursday 20.1K posts
- 2. #River 5,713 posts
- 3. Rejoice in the Lord 1,399 posts
- 4. Jokic 28.6K posts
- 5. Namjoon 77.8K posts
- 6. Lakers 51.9K posts
- 7. FELIX VOGUE COVER STAR 11.1K posts
- 8. #FELIXxVOGUEKOREA 11.7K posts
- 9. #FELIXxLouisVuitton 10.7K posts
- 10. #WorldKindnessDay 6,525 posts
- 11. #ReasonableDoubtHulu N/A
- 12. New Zealand 14.4K posts
- 13. Mikey 61.6K posts
- 14. Clippers 15.5K posts
- 15. Shai 16.4K posts
- 16. Nemec 3,633 posts
- 17. Thunder 38.5K posts
- 18. Ty Lue 1,330 posts
- 19. Valve 64.4K posts
- 20. Raising Arizona 1,031 posts