#malwareanalysisforhedgehogs search results
🦔 📹 Video: Analysis of malicious NordVPN setup ➡️ beginner-suitable ➡️ sorry, no spoilers here ;) youtube.com/watch?v=5-OY3I… #MalwareAnalysisForHedgehogs

youtube.com
YouTube
Malware Analysis - Malicious NordVPN Setup, Beginner Sample
New Video: Writing x64dbg unpacking scripts 🦔 📹 #MalwareAnalysisForHedgehogs #x64dbg youtu.be/V1s5nAKo5uY?si…

youtube.com
YouTube
Malware Analysis - Writing x64dbg unpacking scripts
🦔 📹 Virut Part III: File infection analysis and bait file creation #MalwareAnalysisForHedgehogs #Virut youtube.com/watch?v=FcXPSp…

youtube.com
YouTube
Malware Analysis - Virut's file infection, part 3
🦔 📹 New Video: Unpacking Lumma Stealer We continue where we left off last time and unpack the Emmenhtal to Pure Crypter to Lumma Stealer chain. youtube.com/watch?v=aenOHA… #MalwareAnalysisForHedgehogs #LummaStealer

youtube.com
YouTube
Malware Analysis - Unpacking Lumma Stealer from Emmenhtal and Pure...
🦔 📹 Video: Learn how to write code based signatures ➡️ using privateloader as example ➡️ what to detect ➡️ where to set wildcards ➡️ how to test your rule on unpac me youtube.com/watch?v=oxC9sB… #MalwareAnalysisForHedgehogs #privateloader

youtube.com
YouTube
Malware Analysis - Writing Code Signatures
🦔 📹 YT Short: How to debloat malware #MalwareAnalysisForHedgehogs #debloat youtube.com/shorts/P0xCs-g…

youtube.com
YouTube
How to deal with bloated malware #malwareanalysis #debloat #shorts
Virut part II: process infection and NTDLL hooking 🦔📹 ➡️x64dbg scripting ➡️conditional breakpoints ➡️more import table resolving ➡️fixing control flow ➡️marking up hook code #MalwareAnalysisForHedgehogs #Virut youtube.com/watch?v=nuxnvj…

youtube.com
YouTube
Malware Analysis - Virut's NTDLL Hooking and Process Infection, Part 2
🦔 📹 New Video: Writing an unpacker with emulation ➡️ Python & speakeasy ➡️ unpacks 3-stage RunPE stub #MalwareAnalysisForHedgehogs #emulation youtube.com/watch?v=J6Rqxo…

youtube.com
YouTube
Writing an unpacker for a 3-stage stub with emulation via speakeasy
🦔 📹 New Video: There is more than Clean and Malicious ➡️ 7 file analysis verdicts and what they mean #MalwareAnalysisForHedgehogs #Verdicts youtube.com/watch?v=XwT23X…
youtube.com
YouTube
Analysis Verdicts: There is more than Clean and Malicious
🦔 📹New Video: Analysis of Virut - Part I ➡️ self-modifying code ➡️ Ghidra markup decryption stub ➡️ API resolving ➡️ unpacking #MalwareAnalysisForHedgehogs youtube.com/watch?v=250Bxe…

youtube.com
YouTube
Malware Analysis - Virut, Unpacking a Polymorphic File Infector, Part...
New Video: Why malware simulators cannot tell you if a malware or technique is detected by AV🦔📹 (... unless they were specifically made for that product) #MalwareAnalysisForHedgehogs youtube.com/watch?v=yJZCY2…

youtube.com
YouTube
Malware Simulators cannot test Antivirus Software
YT Short: Can PDFs be Malware? 🦔📹 #MalwareAnalysisForHedgehogs #PDFs youtube.com/shorts/rWjNDKz…

youtube.com
YouTube
Can PDFs be Malware? #malware #pdf #exploits #shorts
🦔 📹 New Video: ConfuserEx 2 deobfuscation with Python and dnlib #MalwareAnalysisForHedgehogs #ConfuserEx #Python #dnlib youtube.com/watch?v=Pjy50g…

youtube.com
YouTube
Malware Analysis - ConfuserEx 2 Deobfuscation with Python and dnlib,...
🦔 📹 Triaging 9 Samples on VirusTotal ➡️ Why does Bitdefender dominate the detection rate? ➡️ Why do launchers look so suspicious? ➡️ Why does well-known shellcode have a low detection rate? #MalwareAnalysisForHedgehogs #VirusTotal youtube.com/watch?v=v8fRus…
youtube.com
YouTube
Triaging Files on VirusTotal
🦔 📹 New Video: Binary Refinery deobfuscation of a LummaStealer loader (PowerShell, JScript) youtube.com/watch?v=kHU_sP… #MalwareAnalysisForHedgehogs #PowerShell #JScript

youtube.com
YouTube
Malware Analysis - Binary Refinery URL extraction of Multi-Layered...
🦔 📹 New video: What breakpoints to set for unpacking malware? ➡️ Steps of unpacking stub ➡️ Breakpoint targets ➡️ VirtualAlloc from user to kernel mode #MalwareAnalysisForHedgehogs #Unpacking youtube.com/watch?v=fn8rAm…

youtube.com
YouTube
Malware Theory - What breakpoints to set for unpacking
🦔 📹 Video: Ghidra vs Binja vs IDA after 1.5 years using them ➡️ Which is the best for you? ➡️ Usability, interface, function recognition, API & scripting, decompiler, price ➡️ Are you at a disadvantage with free tools? #MalwareAnalysisForHedgehogs youtu.be/k2gzFV2-czc?si…

youtube.com
YouTube
IDA vs Binary Ninja vs Ghidra after 1.5 years using them
New video: Why antivirus software detects cracks as malware or PUP 🦔📹 #MalwareAnalysisForHedgehogs #cracks #antivirus youtube.com/watch?v=KA7R9r…

youtube.com
YouTube
The real reason antivirus software detects cracks
YT short: How to reverse engineer PyInstaller malware🦔 📹 #MalwareAnalysisForHedgehogs #PyInstaller #Python youtube.com/shorts/ETvzwJo…

youtube.com
YouTube
Reversing PyInstaller in 6 Steps #python #reverseengineering #pyins...
🦔 📹 Video: Analysis of malicious NordVPN setup ➡️ beginner-suitable ➡️ sorry, no spoilers here ;) youtube.com/watch?v=5-OY3I… #MalwareAnalysisForHedgehogs

youtube.com
YouTube
Malware Analysis - Malicious NordVPN Setup, Beginner Sample
🦔 📹 New video: What breakpoints to set for unpacking malware? ➡️ Steps of unpacking stub ➡️ Breakpoint targets ➡️ VirtualAlloc from user to kernel mode #MalwareAnalysisForHedgehogs #Unpacking youtube.com/watch?v=fn8rAm…

youtube.com
YouTube
Malware Theory - What breakpoints to set for unpacking
🦔 📹 New Video: There is more than Clean and Malicious ➡️ 7 file analysis verdicts and what they mean #MalwareAnalysisForHedgehogs #Verdicts youtube.com/watch?v=XwT23X…
youtube.com
YouTube
Analysis Verdicts: There is more than Clean and Malicious
🦔 📹 Virut Part III: File infection analysis and bait file creation #MalwareAnalysisForHedgehogs #Virut youtube.com/watch?v=FcXPSp…

youtube.com
YouTube
Malware Analysis - Virut's file infection, part 3
Virut part II: process infection and NTDLL hooking 🦔📹 ➡️x64dbg scripting ➡️conditional breakpoints ➡️more import table resolving ➡️fixing control flow ➡️marking up hook code #MalwareAnalysisForHedgehogs #Virut youtube.com/watch?v=nuxnvj…

youtube.com
YouTube
Malware Analysis - Virut's NTDLL Hooking and Process Infection, Part 2
🦔 📹New Video: Analysis of Virut - Part I ➡️ self-modifying code ➡️ Ghidra markup decryption stub ➡️ API resolving ➡️ unpacking #MalwareAnalysisForHedgehogs youtube.com/watch?v=250Bxe…

youtube.com
YouTube
Malware Analysis - Virut, Unpacking a Polymorphic File Infector, Part...
🦔 📹 New Video: Unpacking Lumma Stealer We continue where we left off last time and unpack the Emmenhtal to Pure Crypter to Lumma Stealer chain. youtube.com/watch?v=aenOHA… #MalwareAnalysisForHedgehogs #LummaStealer

youtube.com
YouTube
Malware Analysis - Unpacking Lumma Stealer from Emmenhtal and Pure...
🦔 📹 New Video: Binary Refinery deobfuscation of a LummaStealer loader (PowerShell, JScript) youtube.com/watch?v=kHU_sP… #MalwareAnalysisForHedgehogs #PowerShell #JScript

youtube.com
YouTube
Malware Analysis - Binary Refinery URL extraction of Multi-Layered...
🦔 📹 Video: Learn how to write code based signatures ➡️ using privateloader as example ➡️ what to detect ➡️ where to set wildcards ➡️ how to test your rule on unpac me youtube.com/watch?v=oxC9sB… #MalwareAnalysisForHedgehogs #privateloader

youtube.com
YouTube
Malware Analysis - Writing Code Signatures
New Video: Writing x64dbg unpacking scripts 🦔 📹 #MalwareAnalysisForHedgehogs #x64dbg youtu.be/V1s5nAKo5uY?si…

youtube.com
YouTube
Malware Analysis - Writing x64dbg unpacking scripts
🦔 📹 New Video: ConfuserEx 2 deobfuscation with Python and dnlib #MalwareAnalysisForHedgehogs #ConfuserEx #Python #dnlib youtube.com/watch?v=Pjy50g…

youtube.com
YouTube
Malware Analysis - ConfuserEx 2 Deobfuscation with Python and dnlib,...
🦔 📹 New Video: Writing an unpacker with emulation ➡️ Python & speakeasy ➡️ unpacks 3-stage RunPE stub #MalwareAnalysisForHedgehogs #emulation youtube.com/watch?v=J6Rqxo…

youtube.com
YouTube
Writing an unpacker for a 3-stage stub with emulation via speakeasy
🦔 📹 Video: Ghidra vs Binja vs IDA after 1.5 years using them ➡️ Which is the best for you? ➡️ Usability, interface, function recognition, API & scripting, decompiler, price ➡️ Are you at a disadvantage with free tools? #MalwareAnalysisForHedgehogs youtu.be/k2gzFV2-czc?si…

youtube.com
YouTube
IDA vs Binary Ninja vs Ghidra after 1.5 years using them
New video: Why antivirus software detects cracks as malware or PUP 🦔📹 #MalwareAnalysisForHedgehogs #cracks #antivirus youtube.com/watch?v=KA7R9r…

youtube.com
YouTube
The real reason antivirus software detects cracks
🦔 📹 YT Short: How to debloat malware #MalwareAnalysisForHedgehogs #debloat youtube.com/shorts/P0xCs-g…

youtube.com
YouTube
How to deal with bloated malware #malwareanalysis #debloat #shorts
🦔 📹 New Video: D3fack loader analysis ➡️ Inno Setup pascal script analysis ➡️ string deobfuscation with binary refinery ➡️ JPHP decompilation Sample was first described by @RussianPanda9xx youtube.com/watch?v=y09Zre… #MalwareAnalysisForHedgehogs #D3fackLoader

youtube.com
YouTube
Malware Analysis - D3f@ck loader from Inno Setup to JPHP
YT short: How to reverse engineer PyInstaller malware🦔 📹 #MalwareAnalysisForHedgehogs #PyInstaller #Python youtube.com/shorts/ETvzwJo…

youtube.com
YouTube
Reversing PyInstaller in 6 Steps #python #reverseengineering #pyins...
YT Short: Can PDFs be Malware? 🦔📹 #MalwareAnalysisForHedgehogs #PDFs youtube.com/shorts/rWjNDKz…

youtube.com
YouTube
Can PDFs be Malware? #malware #pdf #exploits #shorts
New Video: Why malware simulators cannot tell you if a malware or technique is detected by AV🦔📹 (... unless they were specifically made for that product) #MalwareAnalysisForHedgehogs youtube.com/watch?v=yJZCY2…

youtube.com
YouTube
Malware Simulators cannot test Antivirus Software
🦔 📹 Triaging 9 Samples on VirusTotal ➡️ Why does Bitdefender dominate the detection rate? ➡️ Why do launchers look so suspicious? ➡️ Why does well-known shellcode have a low detection rate? #MalwareAnalysisForHedgehogs #VirusTotal youtube.com/watch?v=v8fRus…
youtube.com
YouTube
Triaging Files on VirusTotal
Blog post: File Type Analysis and Code Extraction from Malicious Document #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/06/traini…

Blog post: Malware Lab Setup for Static Analysis #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/06/malwar…

New Blog Article: File Infection Strategies of Viruses (as defined by Péter Szőr) 🦔 #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/11/file-i…

Blog post: Malware Lab Setup for Dynamic Analysis #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/06/malwar…

Blog post: Unpacking Locky. Presents an alternative way to the video with same name. #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/08/unpack…

Work in progress for upcoming video. Oligomorphic , polymorphic and metamorphic viruses. #MalwareAnalysisForHedgehogs


Blog post: Tips and Tricks for Dynamic Screenlocker Analysis #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/07/dynami…

Blog article: Basic Dynamic Analysis of a Screenlocker #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/07/traini…

Blog article: Analysing the Basics of PE Metadata and .NET #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/06/traini…

Blog post: Extracting Metadata and Embedded File from a Malware Dropper #MalwareAnalysisForHedgehogs struppigel.blogspot.de/2017/06/traini…

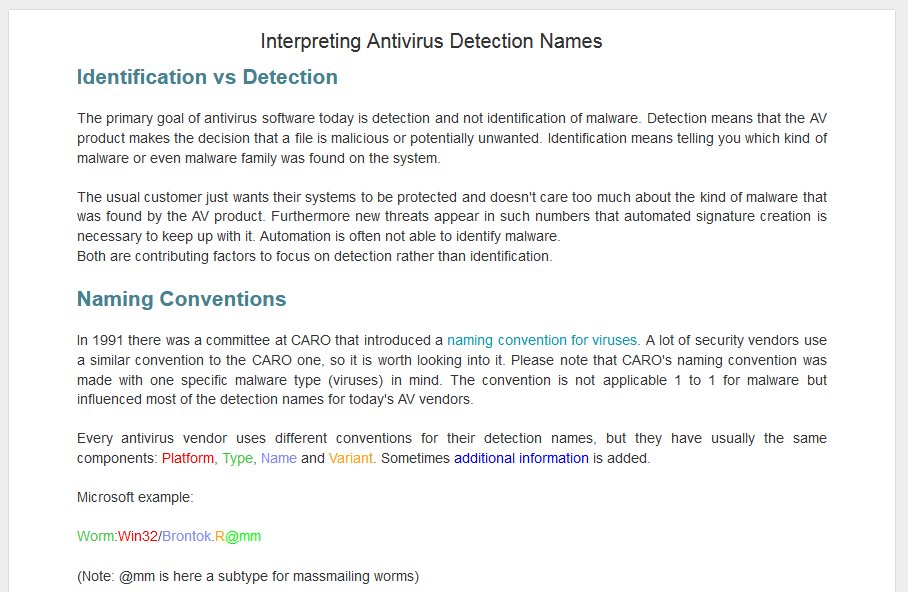
New Blog Article: Interpreting Antivirus Detection Names. #MalwareAnalysisForHedgehogs 🦔 Thanks to @k_sec and @fwosar for additional information that I added to this article. @hexwaxwing You wanted this. 🙂 struppigel.blogspot.de/2018/01/interp…
#Malware101 #MalwareAnalysisForHedgehogs Why does malware often use batch commands or files that ping 8.8.8.8 a few times and then delete an executable? ➡️ ping is used equivalent to a sleep() call here. It passes time before the next command is executed

I realized it just now: I got more than 1000 subscribers at #MalwareAnalysisForHedgehogs youtube.com/channel/UCVFXr…

I got this graphics tablet. New equipment for upcoming videos with more theoretical content. 😀 #MalwareAnalysisForHedgehogs 🐾

Wait, what happened to the women from the last 2 years? Could it be that my transition made the percentage go to zero? 🤔 #YoutubeAnalytics #MalwareAnalysisForHedgehogs

The bug has been fixed as it seems. Women are counted again. Referring to: #MalwareAnalysisForHedgehogs

Wait, what happened to the women from the last 2 years? Could it be that my transition made the percentage go to zero? 🤔 #YoutubeAnalytics #MalwareAnalysisForHedgehogs

Something went wrong.
Something went wrong.
United States Trends
- 1. LINGORM HER AND HERS FANCON 206K posts
- 2. #BUNCHITA 1,461 posts
- 3. Frankenstein 80.6K posts
- 4. Tulane 4,437 posts
- 5. #SmackDown 47.4K posts
- 6. Giulia 15.3K posts
- 7. taylor york 8,651 posts
- 8. Supreme Court 180K posts
- 9. Aaron Gordon 4,801 posts
- 10. #TheLastDriveIn 4,011 posts
- 11. #River 4,666 posts
- 12. Pluribus 30.8K posts
- 13. Russ 14.1K posts
- 14. #TheFutureIsTeal N/A
- 15. Justice Jackson 5,979 posts
- 16. Connor Bedard 3,166 posts
- 17. Gozyuger 2,080 posts
- 18. Brown Jackson 5,598 posts
- 19. Tatis 2,201 posts
- 20. Guillermo del Toro 25.6K posts



