#jscript search results
🚨 #Alert: Multi-stage payload reflectively loads backdoored TaskScheduler.dll vmray.com/analyses/_vt/4… 🔍 A #JScript file with low detection rates on VT retrieves additional payloads via the Pastebin alternative "paste.ee" and a JPG file hosted on Google Drive.…




Find your festive flick! 🎬 Search for holiday classics with this fun Christmas Movie Finder! Explore your favorite Christmas movies, and let the festive magic begin. 👉 What’s your favorite holiday movie? #webdev #jscript #CodingChallenge
Wish this was happening sooner, but looks like disabling #VBScript prevents #Gootloader from running (even though it is coded in #JScript .js) bleepingcomputer.com/news/microsoft…

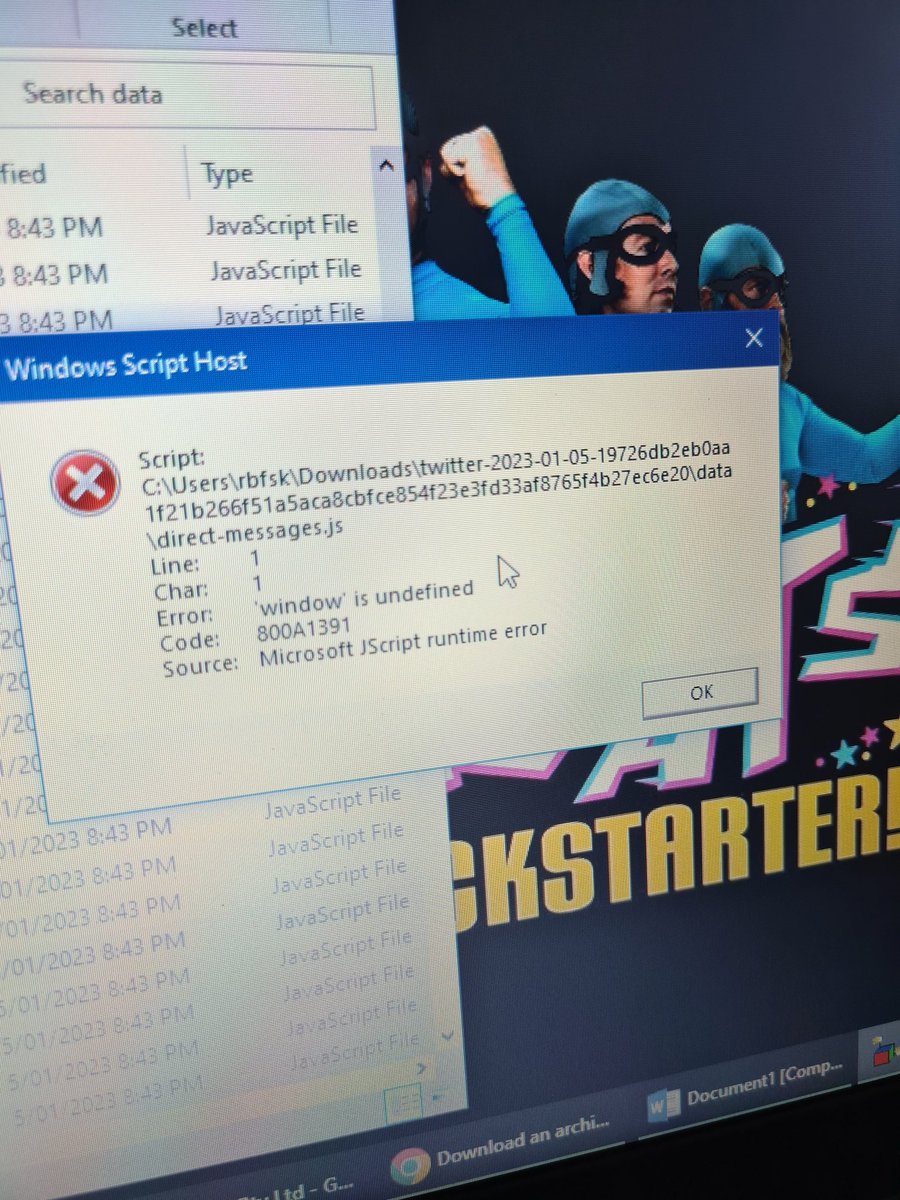
OK, people smarter then me, I downloaded my twitter archive, but when I try and open a file, this comes up. How do I fix? #twitter #jscript #help
I MIGHT BE SLOW, BUT I DON'T STOP MOVING 🐌 One day it will be worthy! #jscript #learning #scrimba #freecodecamp

🦔 📹 New Video: Binary Refinery deobfuscation of a LummaStealer loader (PowerShell, JScript) youtube.com/watch?v=kHU_sP… #MalwareAnalysisForHedgehogs #PowerShell #JScript

youtube.com
YouTube
Malware Analysis - Binary Refinery URL extraction of Multi-Layered...
The pain and time I go through just for a bit of user friendly ajax . Will be going back to php and auto_refresh page soon.. This is bullshit #jscript
La estandarización no estuvo exenta de desafíos. Microsoft desarrolló su propia versión llamada JScript para competir con Netscape. La falta de una especificación oficial llevó a la necesidad de estandarizar el lenguaje para garantizar la compatibilidad. #JScript #WebStandards
Just learning #jscript after php Variables = let variable So iam so going be calling all my variables Let $variable . Having no symbol is just spaghetti when reading through the code
I think it's high time I took my coding seriously #100dayscoding #python #jscript
#cybersecurityworkshop #AMSI #JScript #malwareevasion #memorymanagement #Reflectiontechnique buff.ly/3zz12Kt

github.com/GOD-lang/LOSAN…. Develop a landing page using #HTML #CSS #JScript for company #Frontend developer

#cybersecurityworkshop #AMSI #JScript #malwareevasion #memorymanagement #Reflectiontechnique buff.ly/3zz12Kt

微软宣布在 Windows 11 中默认启用 JScript9Legacy 脚本引擎替换此前的 #JScript,新版本提供更好的性能和安全性。 JScript 是 IE 3.0 时代的产物,由于还有企业需要使用该引擎,所以微软停用 JScript 的同时发布新版本进行替代,确保特定场景下继续安全可用。 查看全文:ourl.co/109753
landiannews.com
微软在Windows 11中推出新版JScript引擎 提供更好的性能和安全性 – 蓝点网
#系统资讯 微软宣布在 Windows 11 24H2 版中默认启用 JScript9Legacy 脚本引擎替换此前的 JScrip…
Something went wrong.
Something went wrong.
United States Trends
- 1. #UFC323 119K posts
- 2. Indiana 104K posts
- 3. Merab 41.5K posts
- 4. Roach 30K posts
- 5. Mendoza 40.4K posts
- 6. Petr Yan 23.8K posts
- 7. Ohio State 62.7K posts
- 8. Pantoja 34K posts
- 9. Bama 85.7K posts
- 10. Joshua Van 9,968 posts
- 11. Curt Cignetti 10.8K posts
- 12. Heisman 19K posts
- 13. Manny Diaz 2,842 posts
- 14. Miami 309K posts
- 15. #iufb 8,500 posts
- 16. The ACC 37.1K posts
- 17. Tulane 18.2K posts
- 18. Virginia 46.3K posts
- 19. Fielding 8,691 posts
- 20. Georgia 86.4K posts





















































