#networkrecovery kết quả tìm kiếm
Dear Telkom Indonesia, Semoga Network Restorasi dapat berjalan lancar. Tetap Semangat! #SatelitTelkom #Telkom1 #NetworkRecovery

At $17 million, #Atlanta #networkrecovery six times more expensive than estimated i.securitythinkingcap.com/QfC1hh

#NetworkRecovery is designed to prep a company for any #IT disaster. Learn why it is vital to your business: bit.ly/2uvfGlr

Wrong network deposit (e.g., ERC-20 to BSC)?Some bridges and services can reverse this. DM us! #NetworkRecovery #EthRecovery #CryptoHelpDesk #CryptoForensics

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ dell.to/3rX8ew3 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

ICYMI! The recording of VETRO's latest webinar: Accelerating Disaster Recovery with Fiber Network Design Tools is now live! ⭐You can access the video here: hubs.ly/Q02W9gpX0 #disasterrecovery #networkrecovery #ISP #fibernetwork

Featuring #BatteryModulation and #NetworkRecovery, #LAVA’s e Series #SimulCharge adapters can ensure your tablet-based hotel check-in kiosk run efficiently for years to come. Find out more about these Enterprise adapters, check out LAVA’s blog: bit.ly/3rhuhOz

Automated network repair drones could be tested for use in disconnected or hostile environments—using these islands as training grounds .#DroneTech #NetworkRecovery
Hit by a computer or network failure? 🛠️💻 Key2 is your go-to for all critical tech services. Don't let downtime derail your day. DM us for swift support! #TechHelp #Key2Services #NetworkRecovery
Testing your Network Recovery Plan is a smart move! bit.ly/2pJchws3 #BeProactive #WorkSmartNotHard #NetworkRecovery #Testing

“Stage2Data's NRaaS™️ - a seamless failover solution that keeps your networks intact, with zero modification.” – Petrus Human, President Stage2Data Read more about NRaaS™️ ow.ly/T8Th50PFzN2 #networkrecovery #failover #IP #NRaaS #cloudserviceprovider

Data corruption, cyberattacks and malware are more prevalent than ever. To stay ahead of the curve, consider NRaaS™. It’s a complete DR solution that includes your entire LAN/WAN. To learn more, get int touch ow.ly/KhOS50LONTj #data #DR #networkrecovery #LAN #WAN
Experts say that information backed up to and stored in the cloud is more secure than what is kept on your computer’s hard drive. Now is the best time to transfer everything to the cloud. #ITSupport #msp #networkrecovery #cloudcomputing hubs.la/Q01SZs8q0
andromeda-tech-solutions.com
How A Cloud Migration Can Transform Productivity and Security
Keep reading for info. on cloud computing, as well as ways you can leverage various services to increase productivity & security within your company!
If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

No More Outages We don’t wait for problems — we stop them. ✔ Instant alerts ✔ Rapid response ✔ Zero downtime focus 📞 877-328-2683 ✉ [email protected] 🌐 clintechsystems.com #ITHumor #NetworkRecovery #ClinTechSystems

Automated network repair drones could be tested for use in disconnected or hostile environments—using these islands as training grounds .#DroneTech #NetworkRecovery
🛠️ Network Down? Here's Your Comeback Plan! Read these 7 expert tips 🔗 zurl.co/Bmu9W to help businesses recover fast from outages—and avoid the next one from @kaspersky #NetworkRecovery #OutagePrevention #TechTips #ITNewsAfrica #HISA2025

Wrong network deposit (e.g., ERC-20 to BSC)?Some bridges and services can reverse this. DM us! #NetworkRecovery #EthRecovery #CryptoHelpDesk #CryptoForensics

Now hiring a Senior Associate in #NetworkRecovery at Ciena. Apply now: ciena.careers/npp #CienaCareers #riskmanagement #ukhiring bit.ly/4lfHO2A
ICYMI! The recording of VETRO's latest webinar: Accelerating Disaster Recovery with Fiber Network Design Tools is now live! ⭐You can access the video here: hubs.ly/Q02W9gpX0 #disasterrecovery #networkrecovery #ISP #fibernetwork

Hit by a computer or network failure? 🛠️💻 Key2 is your go-to for all critical tech services. Don't let downtime derail your day. DM us for swift support! #TechHelp #Key2Services #NetworkRecovery
“Stage2Data's NRaaS™️ - a seamless failover solution that keeps your networks intact, with zero modification.” – Petrus Human, President Stage2Data Read more about NRaaS™️ ow.ly/T8Th50PFzN2 #networkrecovery #failover #IP #NRaaS #cloudserviceprovider

#RBM’s #NetworkRecovery is a safeguard that provides your tablet installation with a more reliable Ethernet connection. zurl.co/Djta
lavalink.com
What is DHCP and Network Recovery? - Blog by Lava
We’ve discussed recently how RBM protects mobile device batteries. However, it also includes Network Recovery! Read our latest article to learn about what DHCP is, how it impacts wired Ethernet, and...
Ever had a wired #Ethernet connection unexpectedly drop out? #NetworkRecovery can fix this issue. Learn more about how it works here: zurl.co/EoYr
lavalink.com
What is DHCP and Network Recovery? - Blog by Lava
We’ve discussed recently how RBM protects mobile device batteries. However, it also includes Network Recovery! Read our latest article to learn about what DHCP is, how it impacts wired Ethernet, and...
Experts say that information backed up to and stored in the cloud is more secure than what is kept on your computer’s hard drive. Now is the best time to transfer everything to the cloud. #ITSupport #msp #networkrecovery #cloudcomputing hubs.la/Q01SZs8q0
andromeda-tech-solutions.com
How A Cloud Migration Can Transform Productivity and Security
Keep reading for info. on cloud computing, as well as ways you can leverage various services to increase productivity & security within your company!
You do not want to struggle to get files restored after a disaster. You can’t wait hours and hours to restore a file you accidentally deleted. Your IT partner should ensuring your backups are humming all day every day. #ITSupport #msp #networkrecovery hubs.la/Q01S4yxj0
andromeda-tech-solutions.com
5 Critical Components For Any Professional Disaster Recovery Plan
Protect your business from disaster with these 5 critical components for a recovery plan. Ensure business continuity with Andromeda's expert support.
Why is LAVA the leading expert in #NetworkRecovery #technology? Because we understand that in a permanent installation where you can't easily access the power cable, an old-fashioned unplug to restart method is inefficient. Learn more about our solution: zurl.co/WC75
.@southwestair your operational performance is fodder for late night comedy… Why not listen to the #NetworkRecovery solutions offered by .@swapapilots ?? Actually… it’s been 3 years. How about new pay rates? Strike Authorization Vote is coming in May
Data corruption, cyberattacks and malware are more prevalent than ever. To stay ahead of the curve, consider NRaaS™. It’s a complete DR solution that includes your entire LAN/WAN. To learn more, get int touch ow.ly/KhOS50LONTj #data #DR #networkrecovery #LAN #WAN

At $17 million, #Atlanta #networkrecovery six times more expensive than estimated i.securitythinkingcap.com/QfC1hh

Dear Telkom Indonesia, Semoga Network Restorasi dapat berjalan lancar. Tetap Semangat! #SatelitTelkom #Telkom1 #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ dell.to/3rX8ew3 | #ThreatActors #Cybersecurity #NetworkRecovery

#NetworkRecovery is designed to prep a company for any #IT disaster. Learn why it is vital to your business: bit.ly/2uvfGlr

🛠️ Network Down? Here's Your Comeback Plan! Read these 7 expert tips 🔗 zurl.co/Bmu9W to help businesses recover fast from outages—and avoid the next one from @kaspersky #NetworkRecovery #OutagePrevention #TechTips #ITNewsAfrica #HISA2025

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

Testing your Network Recovery Plan is a smart move! bit.ly/2pJchws3 #BeProactive #WorkSmartNotHard #NetworkRecovery #Testing

Wrong network deposit (e.g., ERC-20 to BSC)?Some bridges and services can reverse this. DM us! #NetworkRecovery #EthRecovery #CryptoHelpDesk #CryptoForensics

Featuring #BatteryModulation and #NetworkRecovery, #LAVA’s e Series #SimulCharge adapters can ensure your tablet-based hotel check-in kiosk run efficiently for years to come. Find out more about these Enterprise adapters, check out LAVA’s blog: bit.ly/3rhuhOz

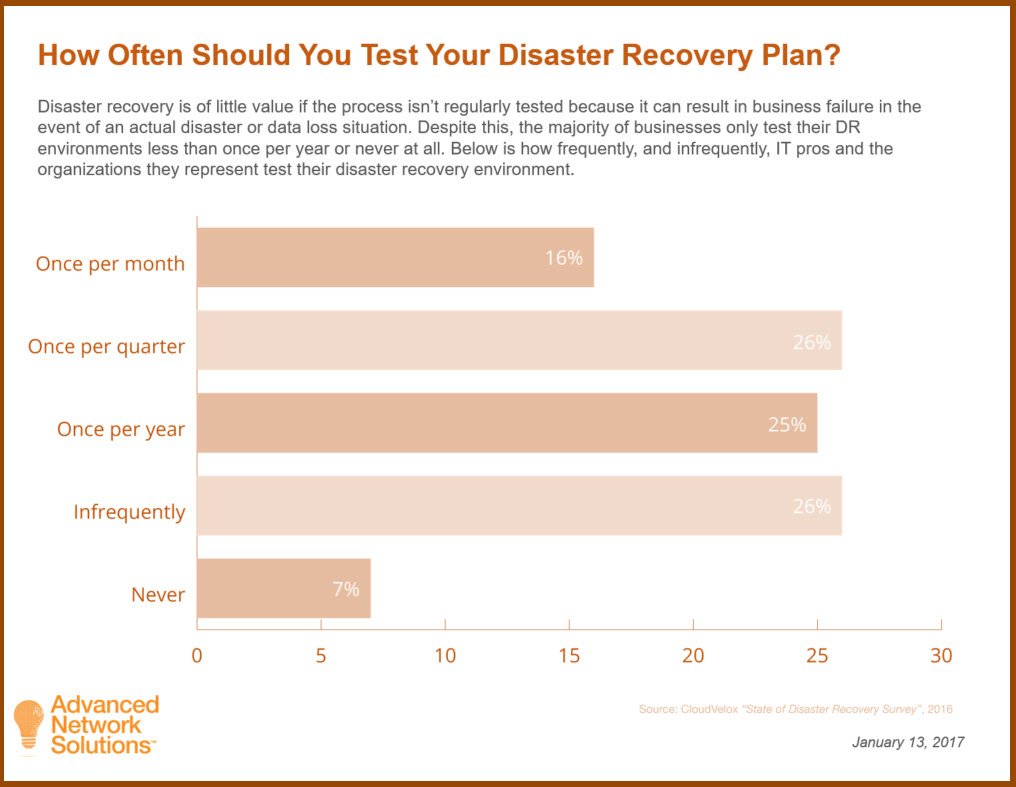
Do you know if your #NetworkRecovery plan will actually work? How often do you test the plan? bit.ly/2wPydIM #SMB #BDR #continuity
If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

“Stage2Data's NRaaS™️ - a seamless failover solution that keeps your networks intact, with zero modification.” – Petrus Human, President Stage2Data Read more about NRaaS™️ ow.ly/T8Th50PFzN2 #networkrecovery #failover #IP #NRaaS #cloudserviceprovider

Data corruption, cyberattacks and malware are more prevalent than ever. To stay ahead of the curve, consider NRaaS™. It’s a complete DR solution that includes your entire LAN/WAN. To learn more, get int touch ow.ly/KhOS50LONTj #data #DR #networkrecovery #LAN #WAN

ICYMI! The recording of VETRO's latest webinar: Accelerating Disaster Recovery with Fiber Network Design Tools is now live! ⭐You can access the video here: hubs.ly/Q02W9gpX0 #disasterrecovery #networkrecovery #ISP #fibernetwork

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

If threat actors breach your network, they wreak havoc on meetings, messages, and servers, disrupting employees and customers. Here are 5 steps to ensure a secure network recovery ⬇️ bit.ly/3Il3974 | #ThreatActors #Cybersecurity #NetworkRecovery

Something went wrong.
Something went wrong.
United States Trends
- 1. $NVDA 74.3K posts
- 2. Jensen 23.1K posts
- 3. GeForce Season 5,504 posts
- 4. Peggy 38.6K posts
- 5. #ใครในกระจกEP5 9,412 posts
- 6. Sumrall 2,308 posts
- 7. Stargate 6,728 posts
- 8. Saba 11K posts
- 9. #WickedWaysToMakeABuck N/A
- 10. Martha 20K posts
- 11. #WWESuperCardNewSeason 1,062 posts
- 12. Comey 57.6K posts
- 13. Kwame 6,695 posts
- 14. Poverty 53.6K posts
- 15. NASA 53.8K posts
- 16. #2Kgiveaway 1,064 posts
- 17. Arabic Numerals 3,124 posts
- 18. Jason Crow 3,077 posts
- 19. EPS of $1.30 N/A
- 20. Halligan 29.1K posts