#reachabilityanalysis search results
Happy 🎃 💀 👻! Don’t get caught in the dark 🔦 join @AppSec_Village for a @BackslashSec webinar on #ReachabilityAnalysis in #ApplicationSecurity! 👀 November 7 👀 to explore the future of vulnerability prioritization. Register now 👉 buff.ly/46XCDgP

ASPM Unveiled 🐰 🎩 Sending some ❤️ today to our friends @BackslashSec - their latest ebook on #ASPM provides unparalleled insights into #ReachabilityAnalysis techniques, esp ☁️native environments Check it out👉 buff.ly/48N3NZf

Larry Pesce traded the lab for the forest to remind us: Not every path leads out of the woods. Finite State’s #ReachabilityAnalysis cuts through CVE noise so you focus on what’s truly exploitable. Book a demo to learn more 👉 hubs.ly/Q03vPzXz0 #IoTSecurity #ProductSecurity
As the CTI for Application security loses pace, we have been focusing on techniques that add more context and help prioritize vulnerabilities, #ASPM #applicationsecurity #reachabilityanalysis #vulnerabilitymanagement

#ASPM in the ☁️ : Transforming AppSec Paradigms with @BackslashSec ASPM redefines security paradigms by integrating ☁️ context ⏩ prioritization and #reachabilityanalysis. Learn how to fortify your #AppSec intelligently with Backslash's latest ebook: buff.ly/48N3NZf

⏰ Webinar Reminder! ⏰ Don't forget to join our friends at @BackslashSec tomorrow, November 7th at 1 pm EST! Their webinar on #ReachabilityAnalysis in #ApplicationSecurity will explore the future of vulnerability prioritization. Register 👉 buff.ly/46XCDgP #AppSec

Prioritization is key in the ever-changing world of #appsec. @BackslashSec's new eBook is here to help! Learn how reachability analysis and cloud context could transform your AppSec strategy. Get the eBook here👉 buff.ly/48N3NZf #ASPM #ReachabilityAnalysis

Securing cloud environments demands a meticulous approach. Our friends at @BackslashSec have curated a comprehensive guide to #ReachabilityAnalysis in cloud contexts. Dive into the intricacies of code security prioritization ⏭️ buff.ly/48N3NZf #ASPM #AppSec

☁️ ASPM in the Cloud: Transforming AppSec Paradigms with @BackslashSec ☁️ ASPM redefines security paradigms by integrating cloud context into prioritization and #reachabilityanalysis. Learn how to fortify your AppSec intelligently. buff.ly/48N3NZf #AppSec #ASPM

Title: Polynomial Controller Synthesis of Nonlinear Systems With Continuous State Feedback Using Trust Regions Authors: Victor Gaßmann; Matthias Althoff Date of Publication: 2 Aug 2023 Link: ieeexplore.ieee.org/document/10202… #controlsystems #optimization #reachabilityanalysis

Start your Nov off on the right foot. Join @BackslashSec's webinar on #ReachabilityAnalysis in #ApplicationSecurity! Mark your 🗓️ for November 7 to explore the future of vulnerability prioritization. Register now to reserve your spot! 👉 buff.ly/46XCDgP #appsec

Missed last week's webinar from @BackslashSec on Reachability Analysis and Business Prioritization? Not to worry! You can now watch it on demand, and expand your mind ⏯️ buff.ly/477Kb0r #AppSec #ReachabilityAnalysis #ASPM #Sponsored

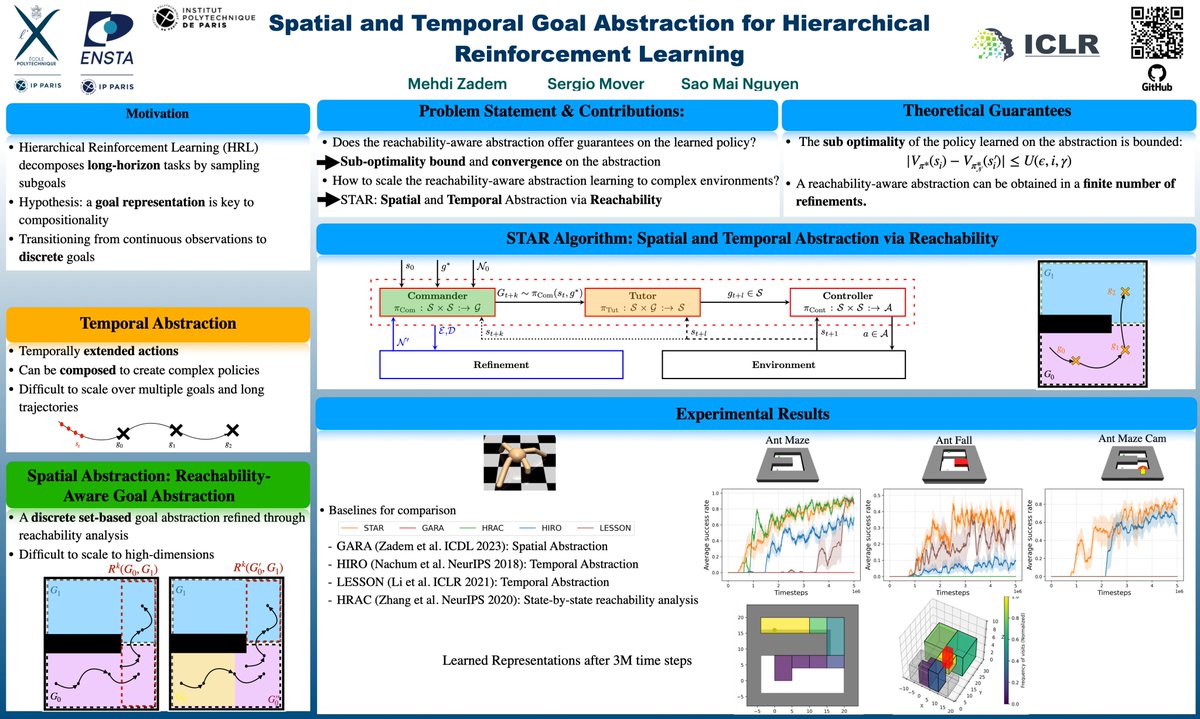
A symbolic representation of tasks is key for compositionality. How can it emerge when the sensorimotor space is continuous? Our goal-conditioned hierarchical #ReinforcementLearning algo enables the emergence of discrete structures #ReachabilityAnalysis 👉hal.science/hal-04401878v1

#Thread on #SciML using @SciML_Org and #ReachabilityAnalysis and the great composability of @JuliaLanguage packages Let's say we have solved a non-linear control problem (like e.g. here medium.com/swlh/neural-od…) and want to verify its behavior over time
Have you worked on drone safety or reachability analysis? Let’s chat! Or, if you’re curious, drop a question below. 🚀 #ReachabilityAnalysis #DroneSafety #ControlSystems #Zonotopes #AutonomousSystems #PhDResearch
A symbolic representation of tasks is key for compositionality. Our goal-conditioned hierarchical #ReinforcementLearning algo STAR learns online a discrete representation of continuous sensorimotor space #ReachabilityAnalysis #ContinualLearning #ICLR2024 👉openreview.net/pdf?id=odY3PkI…
📣 Missed our recent session led by Tru Shiralkar and Patrick Pushor? This webinar delves into the pivotal role of reachability analysis for today's AppSec teams. Watch it now at: youtube.com/watch?v=9YYo35… #AppSec #ReachabilityAnalysis
youtube.com
YouTube
Backslash Security : How Reachability Analysis Can Transform Your...
📅 Want to meet in person? Schedule a meeting with us in advance and enter for a chance to win a Back to the Future LEGO set! 🕹️ 👉 Let's meet: 26972561.hs-sites-eu1.com/rsa24-4 #OWASP #Appsec #reachabilityanalysis #codesecurity
❓ Missed our recent product session on Backslash Reachability Analysis capabilities led by Amit Bismut? 📽 Watch it now: youtube.com/watch?v=8uYfd6… #AppSec #ReachabilityAnalysis

youtube.com
YouTube
Backslash Reachability Analysis
Larry Pesce traded the lab for the forest to remind us: Not every path leads out of the woods. Finite State’s #ReachabilityAnalysis cuts through CVE noise so you focus on what’s truly exploitable. Book a demo to learn more 👉 hubs.ly/Q03vPzXz0 #IoTSecurity #ProductSecurity
As the CTI for Application security loses pace, we have been focusing on techniques that add more context and help prioritize vulnerabilities, #ASPM #applicationsecurity #reachabilityanalysis #vulnerabilitymanagement

📅 Want to meet in person? Schedule a meeting with us in advance and enter for a chance to win a Back to the Future LEGO set! 🕹️ 👉 Let's meet: 26972561.hs-sites-eu1.com/rsa24-4 #OWASP #Appsec #reachabilityanalysis #codesecurity
A symbolic representation of tasks is key for compositionality. Our goal-conditioned hierarchical #ReinforcementLearning algo STAR learns online a discrete representation of continuous sensorimotor space #ReachabilityAnalysis #ContinualLearning #ICLR2024 👉openreview.net/pdf?id=odY3PkI…

Big thanks to Francis Odum and Nipun Gupta for featuring Backslash in their latest newsletter! It spotlights Backslash reachability capabilities and how we prioritize alerts. Read more: softwareanalyst.substack.com/p/defining-a-s… #AppSec #ReachabilityAnalysis #SAST #SCA
A symbolic representation of tasks is key for compositionality. How can it emerge when the sensorimotor space is continuous? Our goal-conditioned hierarchical #ReinforcementLearning algo enables the emergence of discrete structures #ReachabilityAnalysis 👉hal.science/hal-04401878v1

❓ Missed our recent product session on Backslash Reachability Analysis capabilities led by Amit Bismut? 📽 Watch it now: youtube.com/watch?v=8uYfd6… #AppSec #ReachabilityAnalysis

youtube.com
YouTube
Backslash Reachability Analysis
Missed last week's webinar from @BackslashSec on Reachability Analysis and Business Prioritization? Not to worry! You can now watch it on demand, and expand your mind ⏯️ buff.ly/477Kb0r #AppSec #ReachabilityAnalysis #ASPM #Sponsored

☁️ ASPM in the Cloud: Transforming AppSec Paradigms with @BackslashSec ☁️ ASPM redefines security paradigms by integrating cloud context into prioritization and #reachabilityanalysis. Learn how to fortify your AppSec intelligently. buff.ly/48N3NZf #AppSec #ASPM

ASPM Unveiled 🐰 🎩 Sending some ❤️ today to our friends @BackslashSec - their latest ebook on #ASPM provides unparalleled insights into #ReachabilityAnalysis techniques, esp ☁️native environments Check it out👉 buff.ly/48N3NZf

📣 Missed our recent session led by Tru Shiralkar and Patrick Pushor? This webinar delves into the pivotal role of reachability analysis for today's AppSec teams. Watch it now at: youtube.com/watch?v=9YYo35… #AppSec #ReachabilityAnalysis
youtube.com
YouTube
Backslash Security : How Reachability Analysis Can Transform Your...
#ASPM in the ☁️ : Transforming AppSec Paradigms with @BackslashSec ASPM redefines security paradigms by integrating ☁️ context ⏩ prioritization and #reachabilityanalysis. Learn how to fortify your #AppSec intelligently with Backslash's latest ebook: buff.ly/48N3NZf

⏰ Webinar Reminder! ⏰ Don't forget to join our friends at @BackslashSec tomorrow, November 7th at 1 pm EST! Their webinar on #ReachabilityAnalysis in #ApplicationSecurity will explore the future of vulnerability prioritization. Register 👉 buff.ly/46XCDgP #AppSec

Securing cloud environments demands a meticulous approach. Our friends at @BackslashSec have curated a comprehensive guide to #ReachabilityAnalysis in cloud contexts. Dive into the intricacies of code security prioritization ⏭️ buff.ly/48N3NZf #ASPM #AppSec

Start your Nov off on the right foot. Join @BackslashSec's webinar on #ReachabilityAnalysis in #ApplicationSecurity! Mark your 🗓️ for November 7 to explore the future of vulnerability prioritization. Register now to reserve your spot! 👉 buff.ly/46XCDgP #appsec

Happy 🎃 💀 👻! Don’t get caught in the dark 🔦 join @AppSec_Village for a @BackslashSec webinar on #ReachabilityAnalysis in #ApplicationSecurity! 👀 November 7 👀 to explore the future of vulnerability prioritization. Register now 👉 buff.ly/46XCDgP

Prioritization is key in the ever-changing world of #appsec. @BackslashSec's new eBook is here to help! Learn how reachability analysis and cloud context could transform your AppSec strategy. Get the eBook here👉 buff.ly/48N3NZf #ASPM #ReachabilityAnalysis

Title: Polynomial Controller Synthesis of Nonlinear Systems With Continuous State Feedback Using Trust Regions Authors: Victor Gaßmann; Matthias Althoff Date of Publication: 2 Aug 2023 Link: ieeexplore.ieee.org/document/10202… #controlsystems #optimization #reachabilityanalysis

#Thread on #SciML using @SciML_Org and #ReachabilityAnalysis and the great composability of @JuliaLanguage packages Let's say we have solved a non-linear control problem (like e.g. here medium.com/swlh/neural-od…) and want to verify its behavior over time
Title: Polynomial Controller Synthesis of Nonlinear Systems With Continuous State Feedback Using Trust Regions Authors: Victor Gaßmann; Matthias Althoff Date of Publication: 2 Aug 2023 Link: ieeexplore.ieee.org/document/10202… #controlsystems #optimization #reachabilityanalysis

⏰ Webinar Reminder! ⏰ Don't forget to join our friends at @BackslashSec tomorrow, November 7th at 1 pm EST! Their webinar on #ReachabilityAnalysis in #ApplicationSecurity will explore the future of vulnerability prioritization. Register 👉 buff.ly/46XCDgP #AppSec

ASPM Unveiled 🐰 🎩 Sending some ❤️ today to our friends @BackslashSec - their latest ebook on #ASPM provides unparalleled insights into #ReachabilityAnalysis techniques, esp ☁️native environments Check it out👉 buff.ly/48N3NZf

Happy 🎃 💀 👻! Don’t get caught in the dark 🔦 join @AppSec_Village for a @BackslashSec webinar on #ReachabilityAnalysis in #ApplicationSecurity! 👀 November 7 👀 to explore the future of vulnerability prioritization. Register now 👉 buff.ly/46XCDgP

Prioritization is key in the ever-changing world of #appsec. @BackslashSec's new eBook is here to help! Learn how reachability analysis and cloud context could transform your AppSec strategy. Get the eBook here👉 buff.ly/48N3NZf #ASPM #ReachabilityAnalysis

Securing cloud environments demands a meticulous approach. Our friends at @BackslashSec have curated a comprehensive guide to #ReachabilityAnalysis in cloud contexts. Dive into the intricacies of code security prioritization ⏭️ buff.ly/48N3NZf #ASPM #AppSec

☁️ ASPM in the Cloud: Transforming AppSec Paradigms with @BackslashSec ☁️ ASPM redefines security paradigms by integrating cloud context into prioritization and #reachabilityanalysis. Learn how to fortify your AppSec intelligently. buff.ly/48N3NZf #AppSec #ASPM

#ASPM in the ☁️ : Transforming AppSec Paradigms with @BackslashSec ASPM redefines security paradigms by integrating ☁️ context ⏩ prioritization and #reachabilityanalysis. Learn how to fortify your #AppSec intelligently with Backslash's latest ebook: buff.ly/48N3NZf

Start your Nov off on the right foot. Join @BackslashSec's webinar on #ReachabilityAnalysis in #ApplicationSecurity! Mark your 🗓️ for November 7 to explore the future of vulnerability prioritization. Register now to reserve your spot! 👉 buff.ly/46XCDgP #appsec

Missed last week's webinar from @BackslashSec on Reachability Analysis and Business Prioritization? Not to worry! You can now watch it on demand, and expand your mind ⏯️ buff.ly/477Kb0r #AppSec #ReachabilityAnalysis #ASPM #Sponsored

A symbolic representation of tasks is key for compositionality. Our goal-conditioned hierarchical #ReinforcementLearning algo STAR learns online a discrete representation of continuous sensorimotor space #ReachabilityAnalysis #ContinualLearning #ICLR2024 👉openreview.net/pdf?id=odY3PkI…

A symbolic representation of tasks is key for compositionality. How can it emerge when the sensorimotor space is continuous? Our goal-conditioned hierarchical #ReinforcementLearning algo enables the emergence of discrete structures #ReachabilityAnalysis 👉hal.science/hal-04401878v1

As the CTI for Application security loses pace, we have been focusing on techniques that add more context and help prioritize vulnerabilities, #ASPM #applicationsecurity #reachabilityanalysis #vulnerabilitymanagement

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 104K posts
- 2. Packers 61.8K posts
- 3. Packers 61.8K posts
- 4. Jordan Love 9,248 posts
- 5. John Cena 85.5K posts
- 6. Patullo 6,143 posts
- 7. Jalen 19.8K posts
- 8. Pistons 13.9K posts
- 9. #GoPackGo 6,108 posts
- 10. #MondayNightFootball 1,567 posts
- 11. Jenkins 5,227 posts
- 12. #RawOnNetflix 2,545 posts
- 13. Matt LaFleur 2,368 posts
- 14. Nikki Bella 6,622 posts
- 15. AJ Brown 2,960 posts
- 16. Lane Johnson 1,620 posts
- 17. Bo Melton N/A
- 18. Green Bay 13.9K posts
- 19. Desmond Bane 3,505 posts
- 20. Gunther 6,743 posts










