#safemath search results
#SafeMath# matters!The @UmbNetwork reward pools are drained at both @BNBCHAIN and @ethereum, leading to the ~$700K gain for the hacker! The hack is possible because of an unchecked underflow in withdraw() so that anyone can withdraw any amount even without any balance!


#EagleEyeAlert #SafeMath #BNB #ETH @UmbNetwork reward pools were drained due to underflow vulnerability. Beosin-trace analyzed the flow of funds and the profited addresses are listed below:

【 #ERC20 BatchOverflowバグ懸念について】 #REALBOOST は #safemath という機能を使っているのでこの問題は起きないよ♪ 安心してね♪ #イーサリアム #Ethereum

Our VP of Blockchain Development, Sam Hessenhaur tell us about the batch overflow bug on #Ethereum #ERC20 token contracts and #safemath #nanome #blockchain #token #erc20 buff.ly/2slWzaZ

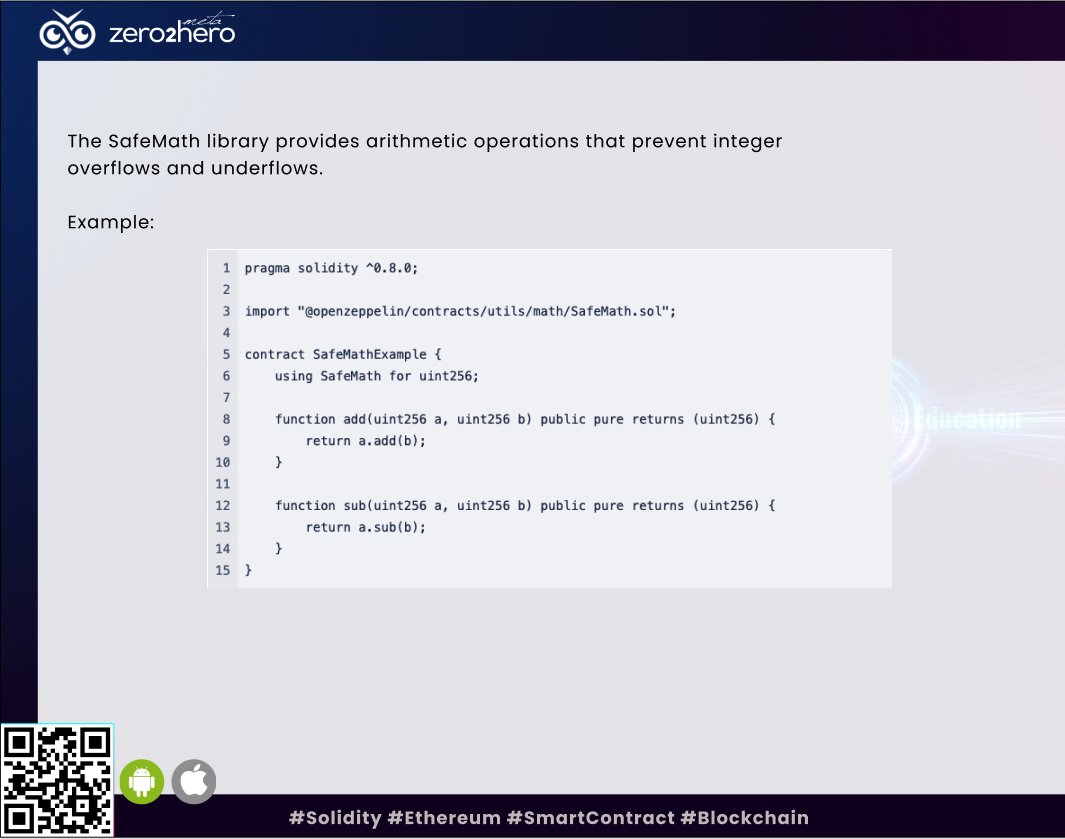
Prevention Method 2: Use Safe Math Libraries 🔢 Utilize well-tested math libraries, like OpenZeppelin's SafeMath, to handle arithmetic operations. They provide functions that prevent overflows, underflows, and other issues related to imprecision. 🛠️ #SafeMath #OpenZeppelin
Solidity Tip: Using SafeMath library for arithmetic operations #SafeMath #SoliditySecurity #SmartContractTips

#BlockSecTips 36) The values and math operations should be resistant to #overflows. Use #SafeMath library for arithmetic operations <0.8.0 Pay special attention to #unchecked fragments of code >0.8.0 SCSVS V5: Arithmetic buff.ly/2VYys53 #Math #code #solidity #contracts

Solidity Tip: Using OpenZeppelin's SafeMath library for arithmetic operations #SafeMath #OpenZeppelin #ArithmeticOperations
4/6 🔢 Integer Overflow & Underflow: A major issue where numbers exceed their defined range, leading to unexpected outcomes. ✅ Good news: Solidity 0.8.0+ automatically checks this. For older versions, use #SafeMath library.
3/10 🚀 Tip: Use Solidity 0.8 or above for built-in overflow/underflow protection. If using older versions, be sure to install SafeMath. #SafeMath #SolidityBestPractices
7/10 🦺 Avoid unchecked arithmetic operations! Solidity’s arithmetic doesn’t automatically check for overflow or underflow in older versions. Always use SafeMath (or Solidity 0.8+). #SafeMath #SmartContractSecurity
Practicing #SafeMath with #blockchain... medium.com/coinmonks/prac…
#SafeMath, built by #OpenZeppelin and designed to allow safe math operations that assist prevent overflow, is one of the most widely used libraries. docs.openzeppelin.com/contracts/2.x/…
It’s highly recommended to perform careful testing of functions that include math operations and use specific libraries, such as #SafeMath if smart contracts are compiled using older compiler versions.
🛠️ Overflows and underflows can be costly. Always use safe math libraries when performing arithmetic operations. 🚀 #SafeMath #ConfluxTips
#SafeMath memo: basic usage .add() .sub() etc... I was confused about SafeMath of #openzeppelin because while add() is defined as taking two arguments like function add(uint a, uint b) ... {...} , you just pass one argument and chain it to a number when using it hmmm?
5/5: Solidity developers, don't leave your contracts vulnerable to arithmetic errors. Incorporate SafeMath library into your smart contracts today to ensure secure and robust arithmetic operations. #safemath #solidity #smartconacts
"Keep your Solidity smart contracts secure and efficient by using SafeMath library. It helps prevent overflow and underflow attacks in your smart contracts. Stay safe with #SafeMath! #SmartContracts #Ethereum #Solidity #Blockchain #CodingTip"
4/6 🔢 Integer Overflow & Underflow: A major issue where numbers exceed their defined range, leading to unexpected outcomes. ✅ Good news: Solidity 0.8.0+ automatically checks this. For older versions, use #SafeMath library.
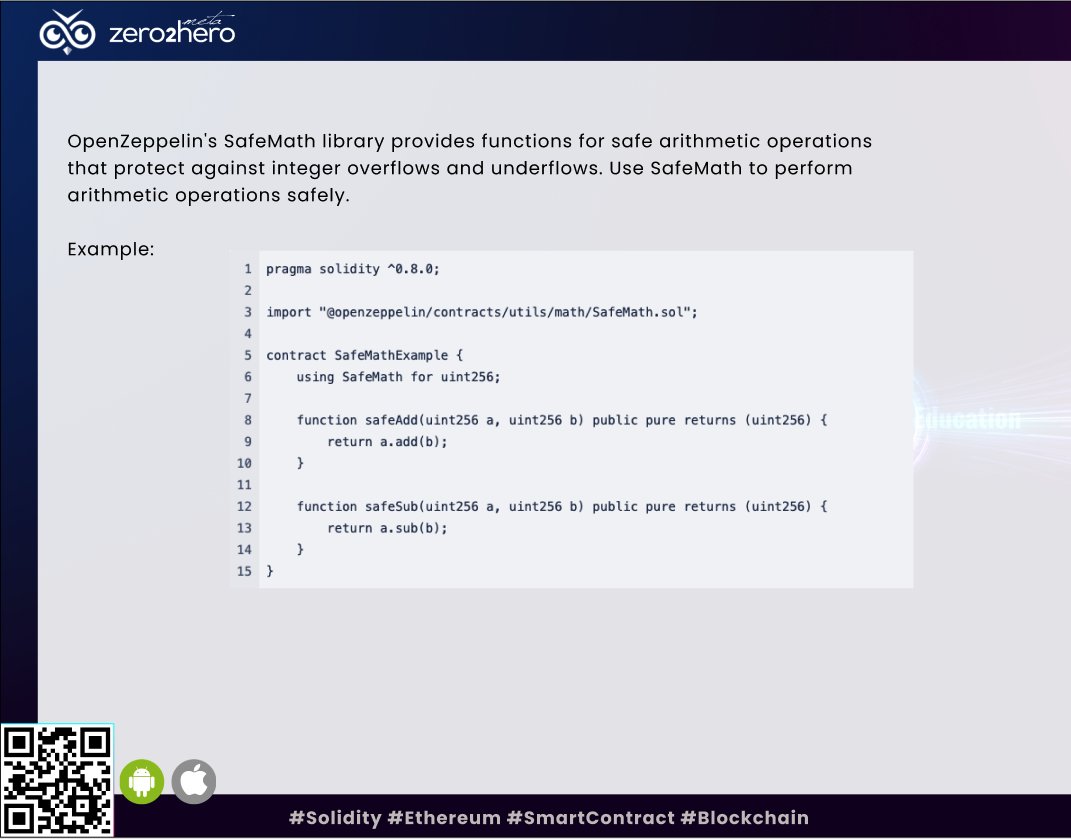
How to protect your contracts? 🛡️ 1️⃣ Use the SafeMath Library from @openzeppelin. It provides safe arithmetic functions that throw errors on overflows/underflows. #SafeMath
Solidity Tip: Using OpenZeppelin's SafeMath library for arithmetic operations #SafeMath #OpenZeppelin #ArithmeticOperations

🛠️ Overflows and underflows can be costly. Always use safe math libraries when performing arithmetic operations. 🚀 #SafeMath #ConfluxTips
2/7💡 Tip 2: Be wary of integer overflows/underflows. Use the latest #Solidity version to prevent them automatically. For older versions, implement checks or use libraries like #SafeMath. 📚
Solidity Tip: Using SafeMath library for arithmetic operations #SafeMath #SoliditySecurity #SmartContractTips

5/ To prevent such vulnerabilities, it's important to thoroughly #test and #audit your code before deploying it. Additionally, you can use libraries like #SafeMath, which provide secure arithmetic operations and help prevent arithmetic overflow and underflow.
It’s highly recommended to perform careful testing of functions that include math operations and use specific libraries, such as #SafeMath if smart contracts are compiled using older compiler versions.

✅Day 80 #WTF23 I have missed updating on some days, but I'mma keep counting. Day 78-timelock hack prevention using #safemath; Day 79- hacking a smartcontract using selfdestruct & its prevention. Day 80- Denial of Service attacks & its prevention. 👌 @fawole141 @Tech4DevHQ
#SafeMath, built by #OpenZeppelin and designed to allow safe math operations that assist prevent overflow, is one of the most widely used libraries. docs.openzeppelin.com/contracts/2.x/…
#FAUNTool 🛠️ alexroan/chuff : Common Solidity contract patterns, based on OpenZeppelin's contract library, implemented in the Huff language GET IT HERE 👉 from.faun.to/r?s=Z0FBQUFBQm… #solidity #safemath #huff
For a global financial system the coding language we use should not be prone to such bugs in the first place #safemath the EVM sucks. last time i ever use it.
ALREADY IN: 11539 ETH locked permanently in the Akutar @AkuDreams auction contract due to the careless one line of the code: the number of auction addresses (refundProgress) is strictly less than the number of bids (totalBids). 11k ETH burned. etherscan.io/address/0xf42c….

#EagleEyeAlert #SafeMath #BNB #ETH @UmbNetwork reward pools were drained due to underflow vulnerability. Beosin-trace analyzed the flow of funds and the profited addresses are listed below:

#SafeMath# matters!The @UmbNetwork reward pools are drained at both @BNBCHAIN and @ethereum, leading to the ~$700K gain for the hacker! The hack is possible because of an unchecked underflow in withdraw() so that anyone can withdraw any amount even without any balance!

Evet haklısın taşma sorunu kontrollerinde 0.7.6 ya kadar #safeMath gerekli, sonrasında safeMath görevi gören internal kontroller eklendi. Bu bağlamda kodda matematiksel işlem sırası önceliğiyle bu librarye gerek kalmıyor. Ben 0.8.12 'de dahil kullanıyorum kendi alışkanlığım.
Finally some #SocialExperiment progress - updated contracts to #Solidity 0.8.10 Still fixing some minor issues from ditching #SafeMath...

【 #ERC20 BatchOverflowバグ懸念について】 #REALBOOST は #safemath という機能を使っているのでこの問題は起きないよ♪ 安心してね♪ #イーサリアム #Ethereum

#SafeMath# matters!The @UmbNetwork reward pools are drained at both @BNBCHAIN and @ethereum, leading to the ~$700K gain for the hacker! The hack is possible because of an unchecked underflow in withdraw() so that anyone can withdraw any amount even without any balance!

Our VP of Blockchain Development, Sam Hessenhaur tell us about the batch overflow bug on #Ethereum #ERC20 token contracts and #safemath #nanome #blockchain #token #erc20 buff.ly/2slWzaZ

Solidity Tip: Using SafeMath library for arithmetic operations #SafeMath #SoliditySecurity #SmartContractTips

#BlockSecTips 36) The values and math operations should be resistant to #overflows. Use #SafeMath library for arithmetic operations <0.8.0 Pay special attention to #unchecked fragments of code >0.8.0 SCSVS V5: Arithmetic buff.ly/2VYys53 #Math #code #solidity #contracts

Solidity Tip: Using OpenZeppelin's SafeMath library for arithmetic operations #SafeMath #OpenZeppelin #ArithmeticOperations

#EagleEyeAlert #SafeMath #BNB #ETH @UmbNetwork reward pools were drained due to underflow vulnerability. Beosin-trace analyzed the flow of funds and the profited addresses are listed below:

Something went wrong.
Something went wrong.
United States Trends
- 1. #GRAMMYs 211K posts
- 2. Clipse 7,857 posts
- 3. addison rae 12.7K posts
- 4. olivia dean 7,617 posts
- 5. #FanCashDropPromotion 2,813 posts
- 6. gaga 69.6K posts
- 7. Dizzy 7,525 posts
- 8. Katseye 75.7K posts
- 9. Leon Thomas 9,115 posts
- 10. Kehlani 24.8K posts
- 11. ravyn lenae N/A
- 12. lorde 8,844 posts
- 13. #FridayVibes 5,984 posts
- 14. AOTY 12.5K posts
- 15. Album of the Year 37.9K posts
- 16. Best New Artist 13.8K posts
- 17. GAME DAY 27.8K posts
- 18. Good Friday 65.3K posts
- 19. Benito 5,853 posts
- 20. Durand 3,093 posts