#binaryninja 搜尋結果
#BinYars is now available via #BinaryNinja's plugin manager! BinYars allows you to write and test #YARA-X rules right inside of Binja. If you have access to Binja projects, you can also sort/group the binaries using YARA-X rules into folders. Check out github.com/xorhex/BinYars
و حالا BinDiff میاد از این داده ها، عملیات مقایسه و آنالیز گراف و ... رو ارائه میده. ابزار BinExport که بصورت پلاگین ارائه میشه، برای دیس اسمبلرهای #IDAPro و #BinaryNinja و #Ghidra بصورت متن باز در دسترس هستش. 3
I've been at the #BinaryNinja livestream to talk about detecting & analyzing modern code obfuscation with my Obfuscation Detection & Obfuscation Analysis plugins on real malware samples. Thanks for hosting me @vector35 ! Recording: youtube.com/watch?v=GQtX7S…

youtube.com
YouTube
Binary Ninja Live Stream: Nov 14th, 2025
Happy to share that later today (Friday, Nov 14, at 10:00 PM CET / 16:00 ET), I’ll be live on the #BinaryNinja livestream to talk about (anti-)reverse engineering & code (de)obfuscation. I'll also showcase some of my plugins.
Join us for another interview this Friday at 4pm ET with Tim Blazytko! As the instructor of Software Deobfuscation Techniques at RE//verse 2026, we'll be picking his brain about the role obfuscation and deobfuscation play a role in today's cybersecurity scene. What would you like…

If you're writing/editing shellcode or work towards OSED course like me, this #BinaryNinja plug in should come in handy 👇 github.com/CX330Blake/She…
Static pointer tracking is tricky. Just shipped some improvements to my #BinaryNinja plugin #Mole: it now tracks array and struct members more precisely. An example on how Mole does this: github.com/cyber-defence-… Binja's multiple ILs make precise analysis so much more powerful!

📚🦠Zero2Auto - Custom Sample - Stage 1 The first stage of the provided sample offers some interesting features that are excellent for reinforcing the content learnt so far in this course. #zero2auto #BinaryNinja #pestudio medium.com/@0x747863/zero…
- ساختار داده های پیچیده رو شناسایی و بازسازی میکنه. - نمایش گرافیکی قابل پیکربندی داره. - از دیکامپایلرهای #IDAPro , #Ghidra و #BinaryNinja پشتیبانی میکنه. - قابل اجرا روی #Windows، #Linux، و #macOS هستش.
The recording of our (CC @nicolodev) talk "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" at @reconmtl is now online! Recording: youtube.com/watch?v=QxSGWk… Slides: synthesis.to/presentations/… #BinaryNinja Plugin: github.com/mrphrazer/obfu…
The recording of our @defcon talk is now available. We shared our approach to reversing IoT and OT malware written in Go using a hybrid toolkit that blends AI with traditional analysis methods using #Radare2 , #Ghidra, and #BinaryNinja. youtu.be/TtPicirB6G4?si… #IoT #Reversing #AI

youtube.com
YouTube
DEF CON 33 - Go Malware Meets IoT - Challenges, Blind Spots, and...
The new version of my #BinaryNinja plugin Obfuscation Analysis (v1.2) adds recursive function inlining in the decompiler. It collapses call-heavy code into a single function; analysis, constant propagation, DCE and other analyses work across boundaries. github.com/mrphrazer/obfu…
Exciting! @vector35's excellent #BinaryNinja ships with built-in BinExport in the latest dev version! Here's how to use it with #BinDiff: dev-docs.binary.ninja/guide/binexpor…

New #BinaryNinja plugin: Obfuscation Analysis Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly. Co-authored by @nicolodev; available in the plugin manager. github.com/mrphrazer/obfu…
Jordan Wiens (@psifertex) is one of the co-founders of @vector35, and developers of #BinaryNinja. Jordan shares the techniques he uses to break decompilers, and a framework to evaluate existing techniques according to various properties. More info: linkedin.com/posts/off-by-o…

More details: @nicolodev and I discuss the current state of MBA (de)obfuscation and their applications @reconmtl We’ll also introduce a new #BinaryNinja plugin for simplifying MBAs in the decompiler. Details: cfp.recon.cx/recon-2025/fea…

Happy to announce that @nicolodev and I will be giving a talk titled "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" at @reconmtl More information will follow in the coming days.
مهمان قسمت هفتم پادکست Behind the Binary آقای @psifertex ، یکی از هم بنیانگذاران Vector 35 و سازندگان #BinaryNinja هستش و در خصوص چشم انداز آینده #امنیت_سایبری، تاثیر #هوش_مصنوعی، توسعه ی Binary Ninja و شرکت در #CTF صحبت میکنن. اسپاتیفای : open.spotify.com/episode/6tMYu7…
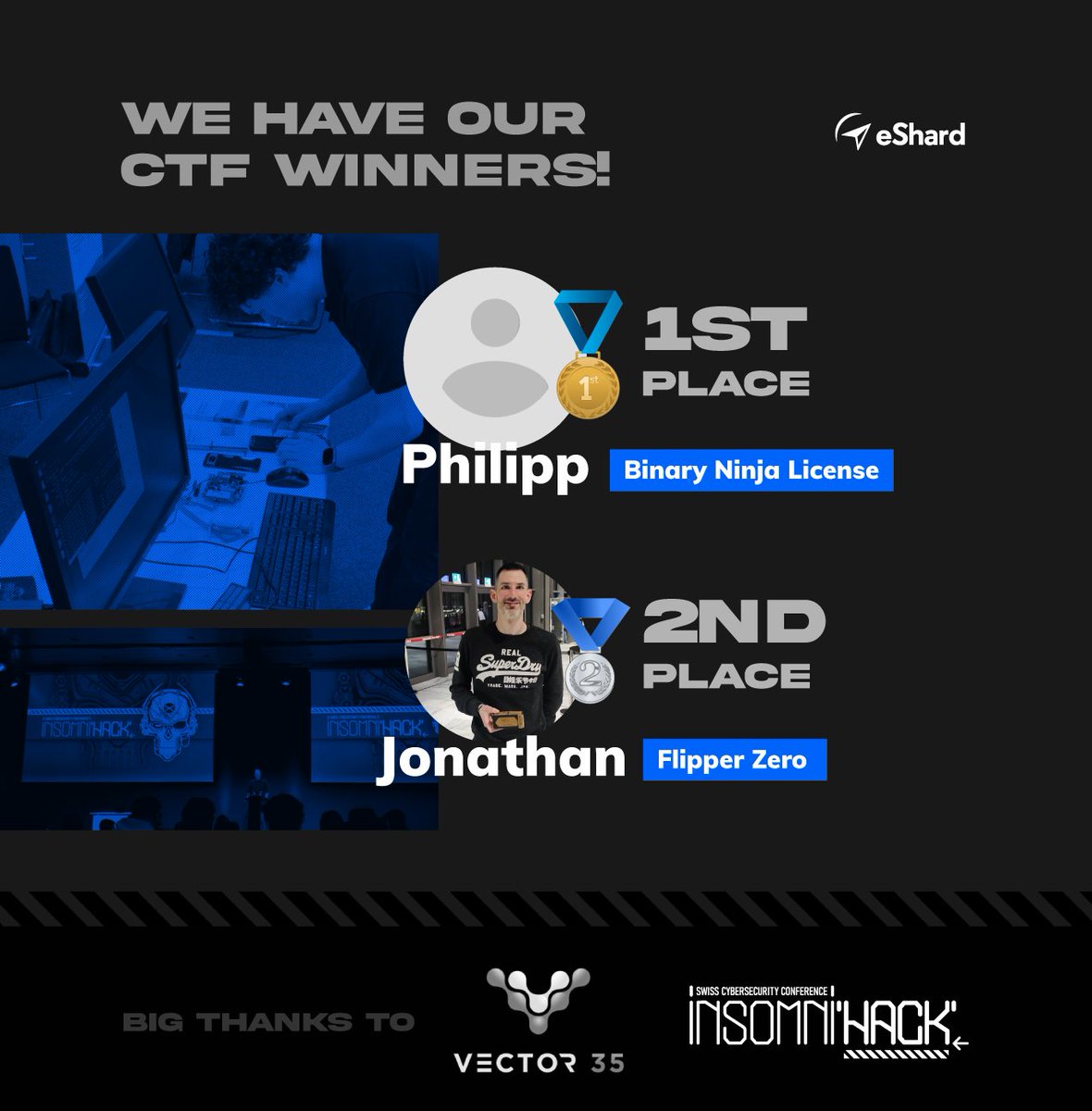
Huge thanks to @vector35 for supporting the challenge and offering a #BinaryNinja license to the first-place winner. 🏅
ابزار #BinaryNinja یک ابزار #مهندسی_معکوس و آنالیز باینری هستش که امکان اسکریپت نویسی با #پایتون برای خودکارسازی فرایندهارو فراهم میکنه. اگه فرصت نکردید، برنامه ضبط میشه و بعدا هم از همون لینکها قابل دسترسه.
Something went wrong.
Something went wrong.
United States Trends
- 1. #Supergirl 88.4K posts
- 2. Lobo 25.3K posts
- 3. The WET 38.7K posts
- 4. Disney 144K posts
- 5. Guardians of the Galaxy 2,083 posts
- 6. Noem 92.5K posts
- 7. Kilmar Abrego Garcia 11.2K posts
- 8. NASCAR 12.3K posts
- 9. Braves 10.3K posts
- 10. Krypto 17.3K posts
- 11. Bennie Thompson 15.4K posts
- 12. Michigan Man 8,993 posts
- 13. James Gunn 6,855 posts
- 14. Robert Suarez 2,762 posts
- 15. OpenAI 27.5K posts
- 16. GOTG 1,133 posts
- 17. Sora 52.4K posts
- 18. Godzilla 32.6K posts
- 19. #NXXT_VolumeRush N/A
- 20. Algorhythm Holdings 1,779 posts