#cyber2security search results
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw in Adobe ColdFusion to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. #cyber2security #cyberattack spixnet.com/cybersecurity-…

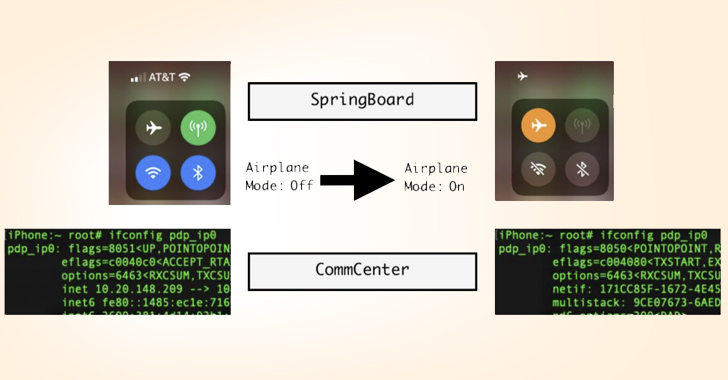
Cybersecurity researchers have documented a novel post-exploit persistence technique on iOS 16 that could be abused to fly under the radar and maintain access to an Apple device even when the victim believes it is offline. #cyber2security #cyberattack spixnet.com/cybersecurity-…
Data Security Posture Management is an approach to securing cloud data by ensuring that sensitive data always has the correct security posture - regardless of where it's been duplicated or moved to. So, what is DSPM? #cyber2security #cyberattack spixnet.com/cybersecurity-…

At a little overt halfway through 2023, credential theft is still a major thorn in the side of IT teams. The heart of the problem is the value of data to cybercriminals and the evolution of the techniques they use to get hold of it. #cyber2security spixnet.com/cybersecurity-…

Organizations in Italy are the target of a new phishing campaign that leverages a new strain of malware called WikiLoader with an ultimate aim to install a banking trojan, stealer, and spyware referred to as Ursnif (aka Gozi). #cyber2security spixnet.com/cybersecurity-…

Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new exploit, according to a new report from VulnCheck. Tracked as CVE-2023-32315 (CVSS score: 7.5), #cyber2security #cyberattack spixnet.com/cybersecurity-…

A high-severity security flaw has been disclosed in the WinRAR utility that could be potentially exploited by a threat actor to achieve remote code execution on Windows systems. Tracked as CVE-2023-40477 (CVSS score: 7.8), #cyber2security #cyberattack spixnet.com/cybersecurity-…

The Chinese threat actor known as APT31 (aka Bronze Vinewood, Judgement Panda, or Violet Typhoon) has been linked to a set of advanced backdoors that are capable of exfiltrating harvested sensitive information to Dropbox. #cyber2security #cyberattack spixnet.com/cybersecurity-…
The U.K. Electoral Commission on Tuesday disclosed a "complex" cyber attack on its systems that went undetected for over a year, allowing the threat actors to access years worth of voter data belonging to 40 million people. #cyber2security #cyberattack spixnet.com/cybersecurity-…

A nation-state actor with links to China is suspected of being behind a series of attacks against industrial organizations in Eastern Europe that took place last year to siphon data stored on air-gapped systems. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…
The threat actor known as Space Pirates has been linked to attacks against at least 16 organizations in Russia and Serbia over the past year by employing novel tactics and adding new cyber weapons to its arsenal. #cyber2security #cyberattack #cybercrim spixnet.com/cybersecurity-…

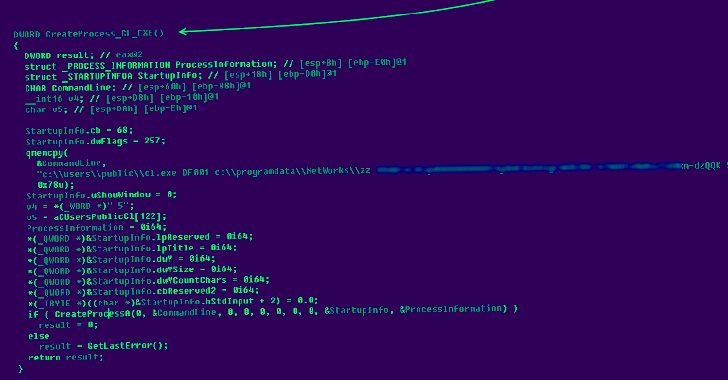
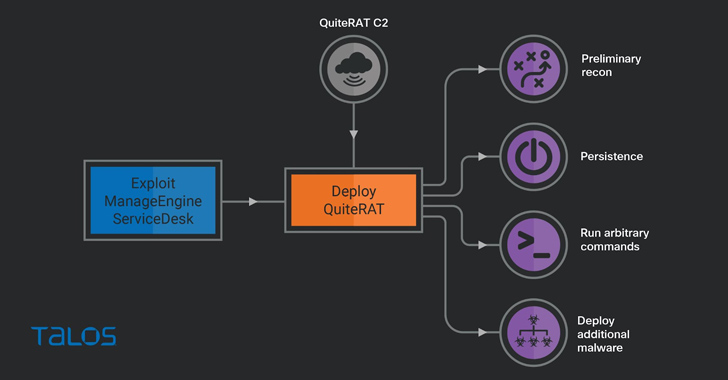
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. #cyber2security spixnet.com/cybersecurity-…
While there was quite a bit of ransomware news this week, the highlighted story was the release of Jon DiMaggio's third article in the Ransomware Diaries series, with the focus of this article on the LockBit ransomware operation. #cyber2security spixnet.com/cybersecurity-…

Software services provider Ivanti is warning of a new critical zero-day flaw impacting Ivanti Sentry (formerly MobileIron Sentry) that it said is being actively exploited in the wild, marking an escalation of its security woes. #cyber2security spixnet.com/cybersecurity-…

The U.S. Justice Department (DoJ) on Wednesday unsealed an indictment against two founders of the now-sanctioned Tornado Cash cryptocurrency mixer service, charging them with laundering more than $1 billion in criminal proceeds. #cyber2security spixnet.com/cybersecurity-…

Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID (formerly Azure Active Directory) application by taking advantage of an abandoned reply URL. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

2N, the world leader in internet-enabled intercoms and access control systems, has upgraded the functionality of its best-selling intercom, the 2N® IP Verso 2.0 , to increase both security and flexibility. This #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

City of London traders hit by Russia-linked cyber attack dlvr.it/ShzV5F #cyber2security #cyberattack #cybersecurity
The threat actors behind the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and targeting activity aimed at Taiwan-based organizations and a U.S. military procurement system. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID (formerly Azure Active Directory) application by taking advantage of an abandoned reply URL. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. #cyber2security spixnet.com/cybersecurity-…

The U.S. Justice Department (DoJ) on Wednesday unsealed an indictment against two founders of the now-sanctioned Tornado Cash cryptocurrency mixer service, charging them with laundering more than $1 billion in criminal proceeds. #cyber2security spixnet.com/cybersecurity-…

Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new exploit, according to a new report from VulnCheck. Tracked as CVE-2023-32315 (CVSS score: 7.5), #cyber2security #cyberattack spixnet.com/cybersecurity-…

The U.K. Electoral Commission on Tuesday disclosed a "complex" cyber attack on its systems that went undetected for over a year, allowing the threat actors to access years worth of voter data belonging to 40 million people. #cyber2security #cyberattack spixnet.com/cybersecurity-…

2N, the world leader in internet-enabled intercoms and access control systems, has upgraded the functionality of its best-selling intercom, the 2N® IP Verso 2.0 , to increase both security and flexibility. This #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

European and U.S. law enforcement agencies have announced the dismantling of a bulletproof hosting service provider called Lolek Hosted, which cybercriminals have used to launch cyber-attacks across the globe. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

The Chinese threat actor known as APT31 (aka Bronze Vinewood, Judgement Panda, or Violet Typhoon) has been linked to a set of advanced backdoors that are capable of exfiltrating harvested sensitive information to Dropbox. #cyber2security #cyberattack spixnet.com/cybersecurity-…

At a little overt halfway through 2023, credential theft is still a major thorn in the side of IT teams. The heart of the problem is the value of data to cybercriminals and the evolution of the techniques they use to get hold of it. #cyber2security spixnet.com/cybersecurity-…

More and more organizations are choosing Google Workspace as their default employee toolset of choice. But despite the productivity advantages, this organizational action also incurs a new security debt. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

Multiple security vulnerabilities have been disclosed in AudioCodes desk phones and Zoom's Zero Touch Provisioning (ZTP) that could be potentially exploited by a malicious attacker to conduct remote attacks. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

Cybersecurity researchers have documented a novel post-exploit persistence technique on iOS 16 that could be abused to fly under the radar and maintain access to an Apple device even when the victim believes it is offline. #cyber2security #cyberattack spixnet.com/cybersecurity-…

At a little overt halfway through 2023, credential theft is still a major thorn in the side of IT teams. The heart of the problem is the value of data to cybercriminals and the evolution of the techniques they use to get hold of it. #cyber2security spixnet.com/cybersecurity-…

Microsoft on Thursday disclosed that it found a new version of the BlackCat ransomware (aka ALPHV and Noberus) that embeds tools like Impacket and RemCom to facilitate lateral movement and remote code execution. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

While there was quite a bit of ransomware news this week, the highlighted story was the release of Jon DiMaggio's third article in the Ransomware Diaries series, with the focus of this article on the LockBit ransomware operation. #cyber2security spixnet.com/cybersecurity-…

Software services provider Ivanti is warning of a new critical zero-day flaw impacting Ivanti Sentry (formerly MobileIron Sentry) that it said is being actively exploited in the wild, marking an escalation of its security woes. #cyber2security spixnet.com/cybersecurity-…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw in Adobe ColdFusion to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. #cyber2security #cyberattack spixnet.com/cybersecurity-…

A high-severity security flaw has been disclosed in the WinRAR utility that could be potentially exploited by a threat actor to achieve remote code execution on Windows systems. Tracked as CVE-2023-40477 (CVSS score: 7.8), #cyber2security #cyberattack spixnet.com/cybersecurity-…

From a user's perspective, OAuth works like magic. In just a few keystrokes, you can whisk through the account creation process and gain immediate access to whatever new app or integration you're seeking. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

The threat actors behind the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and targeting activity aimed at Taiwan-based organizations and a U.S. military procurement system. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

Data Security Posture Management is an approach to securing cloud data by ensuring that sensitive data always has the correct security posture - regardless of where it's been duplicated or moved to. So, what is DSPM? #cyber2security #cyberattack spixnet.com/cybersecurity-…

Organizations in Italy are the target of a new phishing campaign that leverages a new strain of malware called WikiLoader with an ultimate aim to install a banking trojan, stealer, and spyware referred to as Ursnif (aka Gozi). #cyber2security spixnet.com/cybersecurity-…

A nation-state actor with links to China is suspected of being behind a series of attacks against industrial organizations in Eastern Europe that took place last year to siphon data stored on air-gapped systems. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

The threat actor known as Space Pirates has been linked to attacks against at least 16 organizations in Russia and Serbia over the past year by employing novel tactics and adding new cyber weapons to its arsenal. #cyber2security #cyberattack #cybercrim spixnet.com/cybersecurity-…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw in Adobe ColdFusion to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. #cyber2security #cyberattack spixnet.com/cybersecurity-…

Cybersecurity researchers have documented a novel post-exploit persistence technique on iOS 16 that could be abused to fly under the radar and maintain access to an Apple device even when the victim believes it is offline. #cyber2security #cyberattack spixnet.com/cybersecurity-…

At a little overt halfway through 2023, credential theft is still a major thorn in the side of IT teams. The heart of the problem is the value of data to cybercriminals and the evolution of the techniques they use to get hold of it. #cyber2security spixnet.com/cybersecurity-…

Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new exploit, according to a new report from VulnCheck. Tracked as CVE-2023-32315 (CVSS score: 7.5), #cyber2security #cyberattack spixnet.com/cybersecurity-…

A high-severity security flaw has been disclosed in the WinRAR utility that could be potentially exploited by a threat actor to achieve remote code execution on Windows systems. Tracked as CVE-2023-40477 (CVSS score: 7.8), #cyber2security #cyberattack spixnet.com/cybersecurity-…

The Chinese threat actor known as APT31 (aka Bronze Vinewood, Judgement Panda, or Violet Typhoon) has been linked to a set of advanced backdoors that are capable of exfiltrating harvested sensitive information to Dropbox. #cyber2security #cyberattack spixnet.com/cybersecurity-…

The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. #cyber2security spixnet.com/cybersecurity-…

The U.K. Electoral Commission on Tuesday disclosed a "complex" cyber attack on its systems that went undetected for over a year, allowing the threat actors to access years worth of voter data belonging to 40 million people. #cyber2security #cyberattack spixnet.com/cybersecurity-…

While there was quite a bit of ransomware news this week, the highlighted story was the release of Jon DiMaggio's third article in the Ransomware Diaries series, with the focus of this article on the LockBit ransomware operation. #cyber2security spixnet.com/cybersecurity-…

Software services provider Ivanti is warning of a new critical zero-day flaw impacting Ivanti Sentry (formerly MobileIron Sentry) that it said is being actively exploited in the wild, marking an escalation of its security woes. #cyber2security spixnet.com/cybersecurity-…

The U.S. Justice Department (DoJ) on Wednesday unsealed an indictment against two founders of the now-sanctioned Tornado Cash cryptocurrency mixer service, charging them with laundering more than $1 billion in criminal proceeds. #cyber2security spixnet.com/cybersecurity-…

Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID (formerly Azure Active Directory) application by taking advantage of an abandoned reply URL. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

2N, the world leader in internet-enabled intercoms and access control systems, has upgraded the functionality of its best-selling intercom, the 2N® IP Verso 2.0 , to increase both security and flexibility. This #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

The threat actors behind the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and targeting activity aimed at Taiwan-based organizations and a U.S. military procurement system. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

From a user's perspective, OAuth works like magic. In just a few keystrokes, you can whisk through the account creation process and gain immediate access to whatever new app or integration you're seeking. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

Microsoft on Thursday disclosed that it found a new version of the BlackCat ransomware (aka ALPHV and Noberus) that embeds tools like Impacket and RemCom to facilitate lateral movement and remote code execution. #cyber2security #cyberattack #cybercrime spixnet.com/cybersecurity-…

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Sunday 58.6K posts
- 2. Klay 25.4K posts
- 3. McLaren 107K posts
- 4. #sundayvibes 4,686 posts
- 5. Lando 138K posts
- 6. #FelizCumpleañosPresidente 3,226 posts
- 7. #FelizCumpleañosNico 3,489 posts
- 8. For the Lord 30.2K posts
- 9. Ja Morant 11.6K posts
- 10. #AEWFullGear 73.2K posts
- 11. Tottenham 42.1K posts
- 12. Oscar 129K posts
- 13. Max Verstappen 68.2K posts
- 14. Piastri 78.7K posts
- 15. #LasVegasGP 234K posts
- 16. Childish Gambino 2,779 posts
- 17. South Asia 38.9K posts
- 18. Arsenal 167K posts
- 19. Swerve 6,921 posts
- 20. Hangman 11K posts




