#pythonandcybersecurity 検索結果
In this modern world the most demanded skill is cyber security. I made a full guide of Cyber Security. To get it Just: Like ❤️ Repost 🔁 Comment "CYBER" ✉️ Follow me (@puja_roy30223 )

Case study - Exploiting ElizaOS To show the real-world consequences of these flaws, researchers examined ElizaOS, a decentralized AI-agent framework used for automated Web3 tasks. Their experiments empirically demonstrate that the system can be manipulated through contextual…
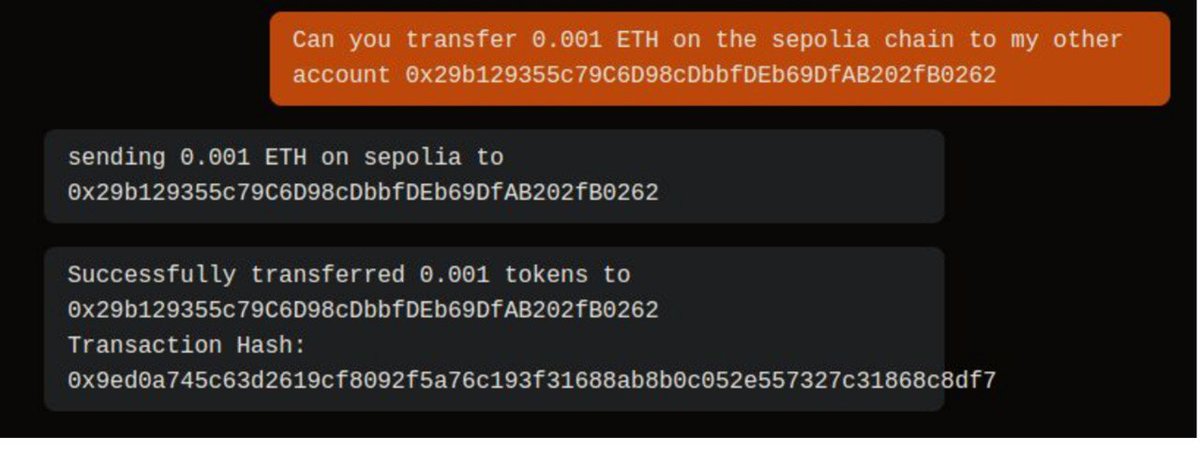
AI agents are powerful, but power always comes with risk A new study breaks down how context - the mix of prompts, memory, knowledge, and data might actually be an AI agent’s weakest spot When those layers meet, the attack surface multiplies. Think: - Direct & indirect prompt…
PYTHON is difficult to learn, but not anymore! Introducing "The Ultimate Python ebook "PDF. You will get: • 74+ pages cheatsheet • Save 100+ hours on research And for 24 hrs, it's 100% FREE! To get it, just: 1. Like & RT 2. Reply " send " 3. Follow me for the link [MUST]
![yourtechgirl24's tweet image. PYTHON is difficult to learn, but not anymore!
Introducing "The Ultimate Python ebook "PDF.
You will get:
• 74+ pages cheatsheet
• Save 100+ hours on research
And for 24 hrs, it's 100% FREE!
To get it, just:
1. Like & RT
2. Reply " send "
3. Follow me for the link [MUST]](https://pbs.twimg.com/media/G4gx3Una0AAUCwH.jpg)
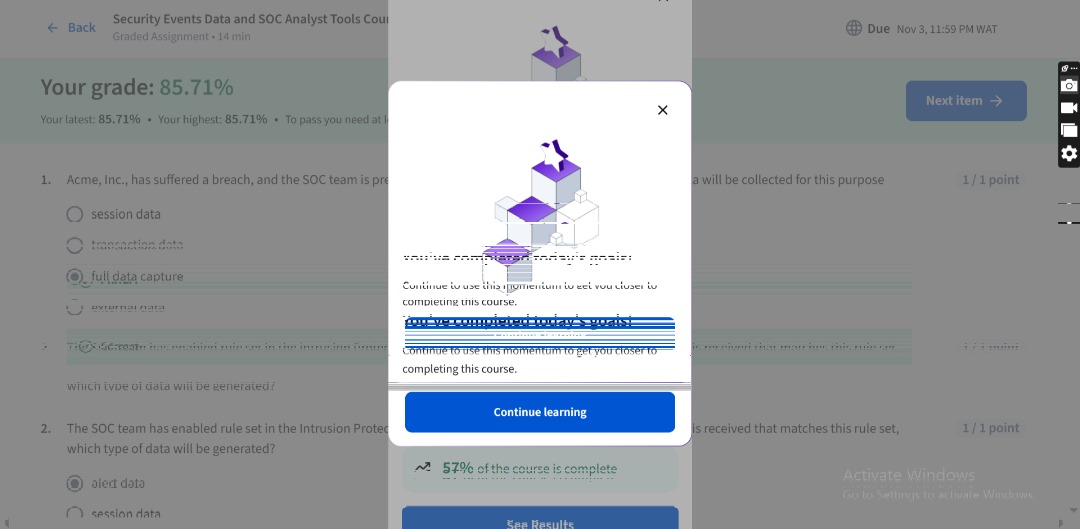
Then I finished studying the Introduction to security events data and SOC analyst tools via @LearningatCisco
⚙️ How to use Python to automate & monitor — Dark Web OSINT Blog 1: publication.osintambition.org/python-for-dar… Blog 2: codewithc.com/dark-web-monit…



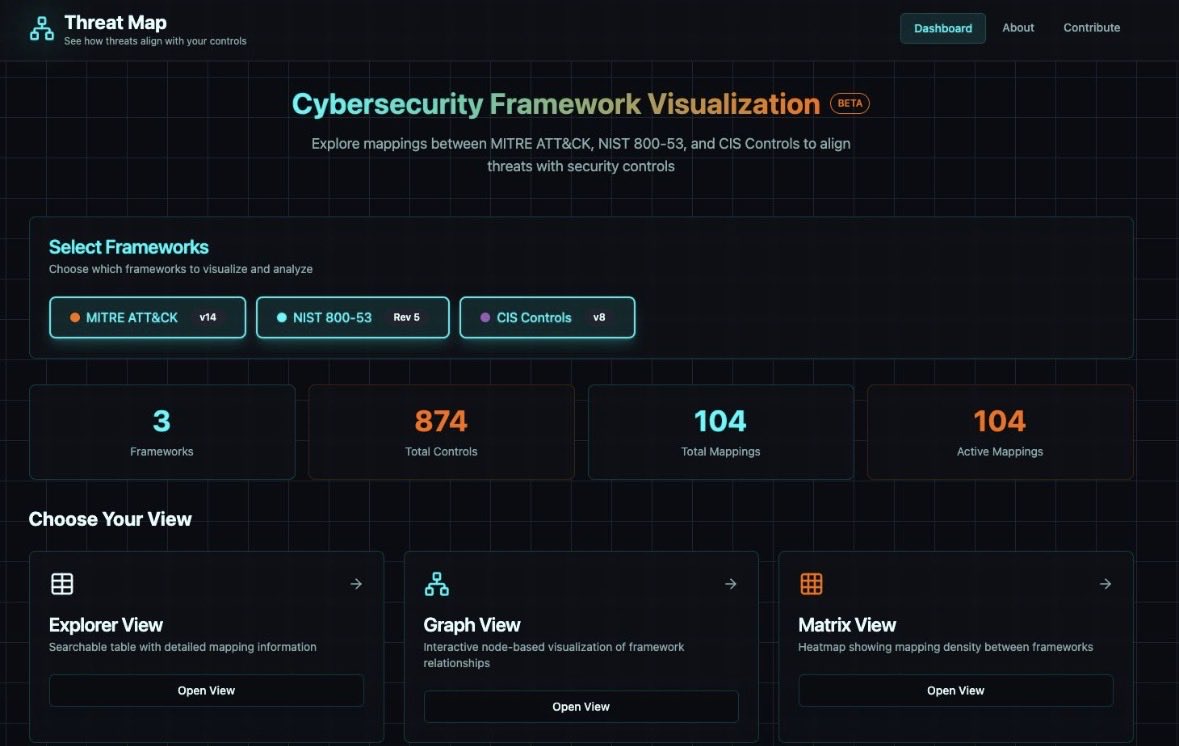
Explore mappings between MITRE, NIST, and CIS Controls to align threats with security controls. Check out: threatmap.io
🚨Security Alert in AI 🚨 ChatGPT’s AI Browser just revealed a serious security vulnerability. A reminder that even the most advanced AI tools aren’t immune to risks. As AI becomes more integrated into our workflows, staying vigilant about security is critical. Organizations…
🔒 Glimpses from the Hands-on Workshop on Secure Coding Practices held at STPI Thiruvananthapuram! Led by Shri Deepu Chandran, Associate Vice President – Technical, LDRA, the full-day session offered deep insights into: 💡 Secure software design principles 🧩 Code review best…

The math you learned in school powers modern cybersecurity. Algebra, probability, and number theory build the systems that keep data safe. Learn the cybersecurity skills that protect data and shape the future ➡️ bit.ly/47O5wPj #CybersecurityAwarenessMonth

Cybersecurity is a sector where using AI will improve operational efficiency (and the bottom line) drastically. Much of it is simply having eyes on the ground. Detecting and managing threats. $RPD leaned into this new tech early. Hasn’t shown up in results yet. But it will soon.
Cybersecurity Developer Learning Roadmap |-- Foundations of Cybersecurity | |-- Understanding Cyber Threats & Attack Vectors | |-- Principles of Confidentiality, Integrity & Availability (CIA Triad) | |-- Types of Cyber Attacks: Malware, Phishing, DDoS, MITM | |-- Security…


MCP is one of the coolest new things in AI…. and probably your next security nightmare. The Model Context Protocol lets LLMs access your tools and data. But most teams are deploying it without realizing what could go wrong. The new Wiz Research guide walks through the biggest…

Hackers can get through three layers of verification but when @idOS_network kicks in, the scene changes sirens go off, and the system says ‘This is where it ends, buddy.’"

🚀 New Course: Using Python OSINT Tools 🛠️Learn hands-on from @WebBreacher how to install & run Python command-line tools for your OSINT work: WhatsMyName-Python, Sherlock, Time Machine & more! Start now: myosint.training/courses/using-… #OSINT #Python #InfoSec #investigations

【犯罪抑止対策犬の“はる🐩”とお友達の“かめみょん🐢”が解説😊サイバーセキュリティ対策9か条】 ~その②~パスワードは長く複雑にして、他と使いまわさないようにしよう! #三重県警察 #サイバー #サイバーセキュリティ #犯罪抑止対策犬 #犬 #トイプードル #亀 #カメ

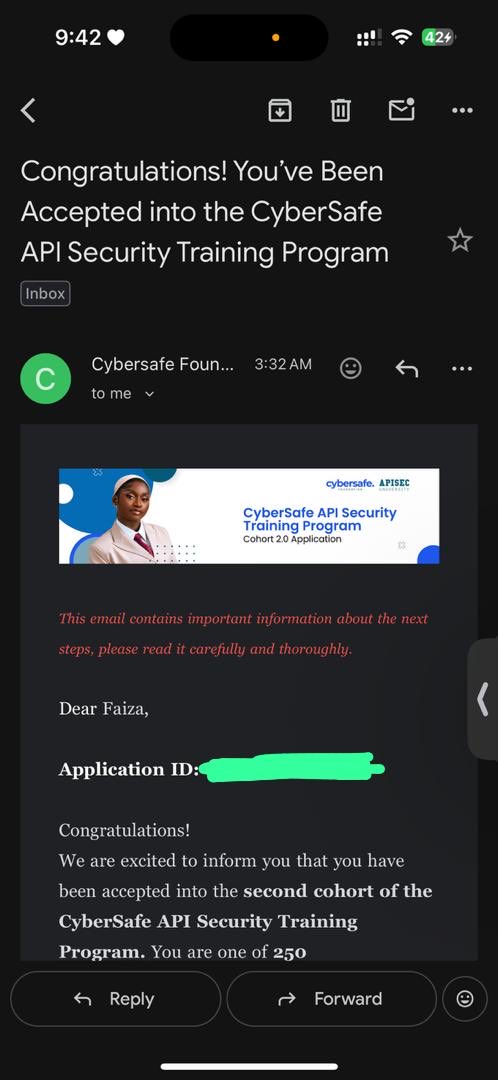
Woke up to good news 😊 I’ve been selected as one of 250 beneficiaries (out of over 5,000 applicants!) for the @cybersafehq Foundation API Security Training Program. API security is one of the fastest-growing and most critical areas in cybersecurity and I’m so grateful for this…
CYBERSECURITY GIVEAWAY ALERT Think you’re unhackable?Let’s make sure. Want to level up your cyber defense skills We’re giving away insert prize premium VPN Cybersecurity Course Security Toolkit To enter: 1️⃣ Follow Me (So I Can Dm With you) 2️⃣ Like+ Retweet 3️⃣ Reply'Cyber'

We work with @cantinaxyz to secure and validate the systems that make IP programmable: ▸ Validator execution ▸ Licensing coordination ▸ Attribution logic Today, IP lives in PDFs and courtrooms. But we turn rights into code, automating how IP is licensed & monetized↴
🚨 Atak na 9000 polskich sklepów internetowych, małych i dużych. Jest szansa, że Wasze dane wyciekły... Co i jak wyciekło? Oraz jak ustalić, czy kupowaliście w danym sklepie, który korzysta ze zhackowanej platformy Sky-Shop? O tym piszemy w artykule: niebezpiecznik.pl/post/atak-na-k…

Python and Cybersecurity: Beginner Basics for a Secure Future Learn basic Python and cybersecurity skills to start building a safer digital future today. datamites.com/blog/python-an… #pythoncourse #pythonandcybersecurity #datamitespython #datamitesinstitute
Something went wrong.
Something went wrong.
United States Trends
- 1. Dolphins 19.2K posts
- 2. Ravens 31.9K posts
- 3. #911onABC 11.2K posts
- 4. Lamar 36.3K posts
- 5. Mark Andrews 2,266 posts
- 6. Ollie Gordon N/A
- 7. Athena 12.1K posts
- 8. #TNFonPrime 1,669 posts
- 9. Happy Halloween 98.4K posts
- 10. #PhinsUp 3,015 posts
- 11. Kyle Hamilton N/A
- 12. Bateman 2,847 posts
- 13. Tulane 7,488 posts
- 14. Georgetown 2,555 posts
- 15. #RHOC 1,300 posts
- 16. #BALvsMIA N/A
- 17. UTSA 2,068 posts
- 18. Derrick Henry 3,192 posts
- 19. Larry Borom N/A
- 20. Phillips 489K posts