#safeprogramming kết quả tìm kiếm
🛡️ Why Your #AI Safety Framework is a Hacker's Playground: From Asimov's Laws to Behavioral Integrity undercodetesting.com/why-your-ai-sa… Educational Purposes!
Open source. AI-generated code. Third-party components. Software supply chain attacks are up. Are you ready? runsafe.ly/4rqI9Dt

Your Java Code Is a Security Risk: Fix These 7 Things NOW- Be Smart opensourcesoftwarenews.com/redirect/13603/
Watch @lauriewired’s video about it. She explains how it is. Nevertheless, a competent C++ programmer can make it safe for 99% of use cases without the false sense of security that comes with 2,937 uses of the unsafe keyword.
LLMs often detect malicious intent, but structured inputs leave them no safe choice. ⚠️ Safe Harbor fixes that. 🚢 An open source safety path that lets agents abort unsafe workflows in real time. Developer-friendly. Real protection. 🛡️ Explore now ➡️ eu1.hubs.ly/H0q9MzG0

“We’re going to make our programs safe, reliable, and as efficient as possible given our constraints.” Modern programmers:
Picture this: AI glitches, but your plant doesn't spiral into chaos! The secret? Fail-safe design. When AI stumbles, your system defaults to SAFE. Seen this in action? #AISafety #OTSecurity
Online Code Formatters Are Not Safe #technews #cybersecurity @endingwithali buff.ly/uC87JwF

youtube.com
YouTube
Online Code Formatters Are Not Safe #technews #cybersecurity @endin...
Security isn’t achieved with one technique– it’s a layered strategy. 🧰 In traditional testing, developers use heuristics: code reviews for intuition, fuzzing for unexpected behavior, threat modeling for architectural insight. Rust adds memory safety rules that can eliminate…

Writing code to keep people safe: Lessons building secure applications in the AI age Find out more: techcabal.com/2025/12/02/bui…
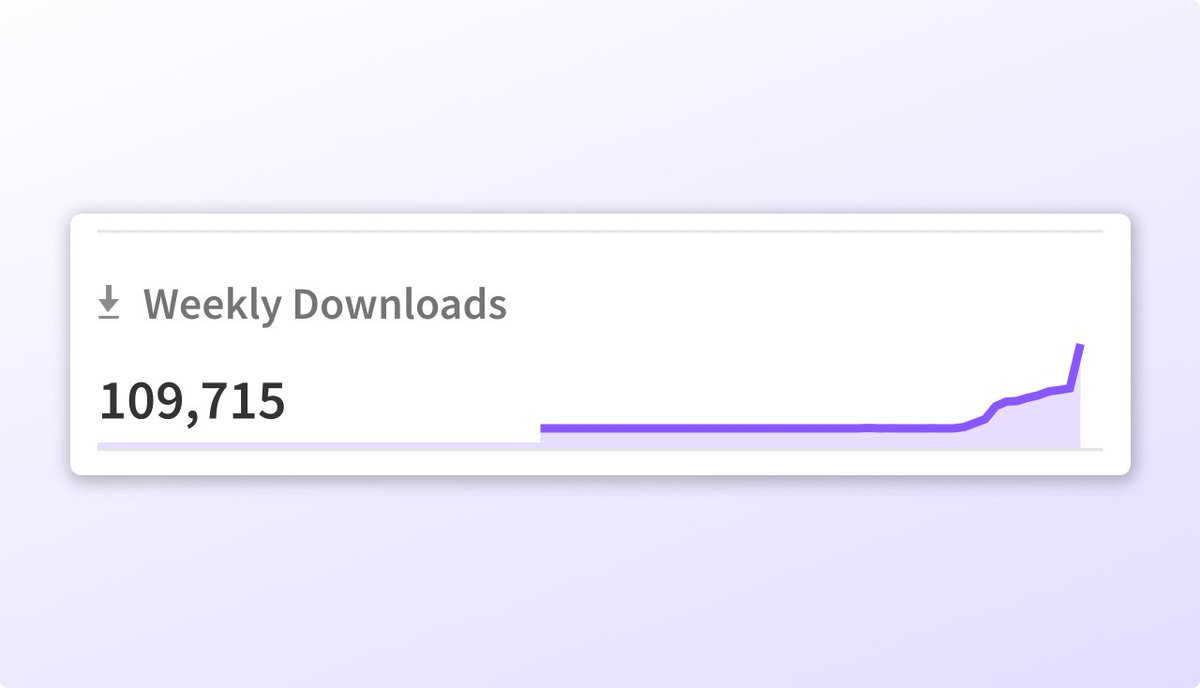
Now at 100k+ weekly downloads, Safe chain is the safe default for devs. Free to use. Open source. Protects against malware before install. -> github.com/AikidoSec/safe…
Have you looked at fil-c? @filpizlo is doing exceptional work making c/c++ safe by default
> the end user program is what protects the underlying libraries from exposing vulnerabilities That’s definitely not true. It’s the opposite: if you have code written in a type safe language calling APIs written in an unsafe language and those APIs are stateful, then a mistake…
The Fil-C hype is getting too much Crashing your program on a memory error definitely makes it safer, but it doesn't help you eliminate such bugs before you encounter them Runtime safety is just insurance... Compiletime safety is a guardrail that you cannot jump over...
We can define macro SAFE and mark code block that we are absolutely sure is tested and safe.
It doesn't launch a nuclear bomb, so indeed very safe! Burning through CPU time without the potential for further bugs is also a very safe strategy for Microsoft to earn money. Also, writing this should also be a very safe way to get fired.
Something went wrong.
Something went wrong.
United States Trends
- 1. The BONK 278K posts
- 2. FINALLY DID IT 583K posts
- 3. Namjoon 55K posts
- 4. Good Saturday 20.9K posts
- 5. #AAA2025 124K posts
- 6. The EU 355K posts
- 7. Cocona 140K posts
- 8. Gunther 26.3K posts
- 9. #LifeAITestnet 7,455 posts
- 10. #MCWonyoungAAAte 19.5K posts
- 11. 5 YEARS WITH MC WONYOUNG 17.9K posts
- 12. Flag Day 3,489 posts
- 13. Yunho 29.5K posts
- 14. Tulane 14.7K posts
- 15. Dizzy 6,587 posts
- 16. fnaf 2 66.6K posts
- 17. Occupied 39.6K posts
- 18. Rivals Rewind 12.1K posts
- 19. St. Nicholas 5,983 posts
- 20. Johnny Carson N/A























