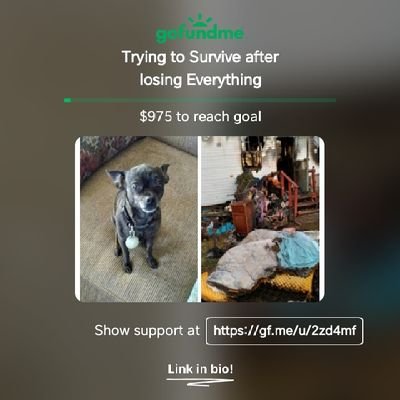
4tify Technologies
@4tifyTech
Security Consulting and Services firm providing Information Security expertise to help customers protect their business. Your Security is our Success.
You might like
Why should your business care about Cyber Security? Watch this video to find out. #4tifyTechnologies #CyberSecurity #CyberAttacks #SmallBusiness #InfoSec #Consulting #RiskAssessment #SecurityTesting #PenTesting #SecurityAwareness #Training #SecurityAudit #SecurityCompliance
Hackers exploit websites to give them excellent SEO before deploying malware Climbing up Google’s ranks is key to this new technique. By Charlie Osborne, via @ZDNet buff.ly/2MzVN8y

Hackers tied to Russia’s GRU targeted the US grid for years Sandworm-aligned group has breached US critical infrastructure a handful of times. By Andy Greenberg, via @ArsTechnica buff.ly/3uBdm9x

Axonius raises $100 million to protect IoT devices from cyberattacks By Kyle Wiggers, via @VentureBeat buff.ly/3bPJvBG

Scientists have built this ultrafast laser-powered random number generator Using a single laser, scientists have built a new system that generates random numbers fast and at scale. By Daphne Leprince-Ringuet, via @ZDNet buff.ly/3qa2ufg

Criminals are jumping on this niche programming language to write the latest malware Adoption of Go shows no signs of slowing down in the foreseeable future By Mayank Sharma, via @TechRadar buff.ly/300r7jV

Far-Right Platform Gab Has Been Hacked—Including Private Data The transparency group DDoSecrets says it will make the 70 GB of passwords, private posts, and more available to researchers, journalists, and social scientists. By Andy Greenberg, via @Wired buff.ly/3r5FWgX

Hackers are finding ways to hide inside Apple’s walled garden The iPhone’s locked-down approach to security is spreading, but advanced hackers have found that higher barriers are great for avoiding capture By Patrick Howell O'Neill, via @techreview buff.ly/3b4mXOv

Airplane maker Bombardier data posted on ransomware leak site following FTA hack Bombardier is the latest in a long string of hacks caused by companies using old versions of the Accellion FTA file-sharing server. By Catalin Cimpanu, via @ZDNet buff.ly/3ssFvxL

Free cybersecurity tool aims to help smaller businesses stay safer online NCSC tool aims to help small businesses develop a strategy to protect themselves from cyber crime. By Danny Palmer, via @ZDNet buff.ly/2MBEynt

Cyber CEO: Next war will hit regular Americans online By Nicholas Johnston, via @Axios buff.ly/3r5Bqiq

A Swiss Company Says It Found Weakness That Imperils Encryption By Ryan Gallagher, Bloomberg @Technology buff.ly/3aFPVmc

9 scary revelations from 40 years of facial recognition research By Rachel Kraus, @mashable buff.ly/36OcWlT

Security News This Week: Government Demands for Amazon Data Shot Up 800 Percent in 2020 Plus: Smartmatic lawsuits, a fake WhatsApp, and more of the week’s top security news. By Brian Barrett, via @Wired buff.ly/3txf9f3

Signal, WhatsApp and Telegram: Major security differences between messaging apps By Rae Hodge, via @CNET buff.ly/3pVtr7l

Going deep on the massive 2020 cyberattack on the United States By @FortuneMagazine buff.ly/2MYMZZT

How the United States Lost to Hackers America’s biggest vulnerability in cyberwarfare is hubris. By Nicole Perlroth, @NYTimes buff.ly/3pVqhAt

Chrome users have faced 3 security concerns over the past 24 hours A 0-day, malicious extension, and sync abuse are keeping Google developers busy. By Dan Goodin, @ArsTechnica buff.ly/2N0DUj5

A Second SolarWinds Hack Deepens Third-Party Software Fears It appears that not only Russia but also China targeted the company, a reminder of the many ways interconnectedness can go wrong. By Lily Hay Newman, @Wired buff.ly/36BOl3C

Microsoft Brings Autofill Password Management Tool to iOS and MacOS Autofill functions similarly to macOS's Keychain and is available in the Microsoft Authenticator app as well as Google Chrome and Microsoft Edge. By Brittany Vincent, @PCMag buff.ly/3oVciZR

New guidelines from NIST on how to avoid cyberattacks from a nation-state By Jackson Barnett, @fedscoop buff.ly/36PZUnN

United States Trends
- 1. #AskFFT N/A
- 2. Good Sunday 77.6K posts
- 3. Klay 35.7K posts
- 4. Raora 3,287 posts
- 5. #sundayvibes 6,549 posts
- 6. Full PPR N/A
- 7. Ja Morant 16.7K posts
- 8. Cornbread 1,550 posts
- 9. #FelizCumpleañosNico 6,230 posts
- 10. #AskBetr N/A
- 11. McLaren 145K posts
- 12. Michael Wilson N/A
- 13. Tuten 1,407 posts
- 14. Sunday Funday 3,128 posts
- 15. Leeds 15.9K posts
- 16. Kamara 1,629 posts
- 17. Beirut 11.9K posts
- 18. Fritos N/A
- 19. #FelizCumpleañosPresidente 5,026 posts
- 20. Pick 2 18.3K posts
You might like
-
 KSAHERO.COM
KSAHERO.COM
@ksahero_com -
 AttackSolutions, Inc.
AttackSolutions, Inc.
@attacksolutions -
 Stonebranch
Stonebranch
@Stonebranch -
 Sysblue Cyber Solutions
Sysblue Cyber Solutions
@CyberSysblue -
 The Great River Financial Services Inc.
The Great River Financial Services Inc.
@TheGreatRiverF1 -
 5GExchange.com LLC
5GExchange.com LLC
@Exchange5g -
 Cyber Villain 🛡️
Cyber Villain 🛡️
@VeryVillanous -
 QA Valley, Inc.
QA Valley, Inc.
@QAValley -
 CXOVoice
CXOVoice
@cxovoice -
 MeeLock: Adaptive XDR MFA, Secure, User-friendly
MeeLock: Adaptive XDR MFA, Secure, User-friendly
@mee_lock
Something went wrong.
Something went wrong.