CipherTechs, Inc.
@CipherTechs
CipherTechs is a global Cyber Security service provider founded in 2001 that remains privately held with headquarters in New York City.
CipherTechs discovered an admin authentication bypass 0day in JFrog Artifactory. ciphertechs.com/jfrog-artifact…. Patches and work around are available. Be sure to find out if your in-house dev team uses Artifactory. Shout-outs to @jfrog for their vuln disclosure process!
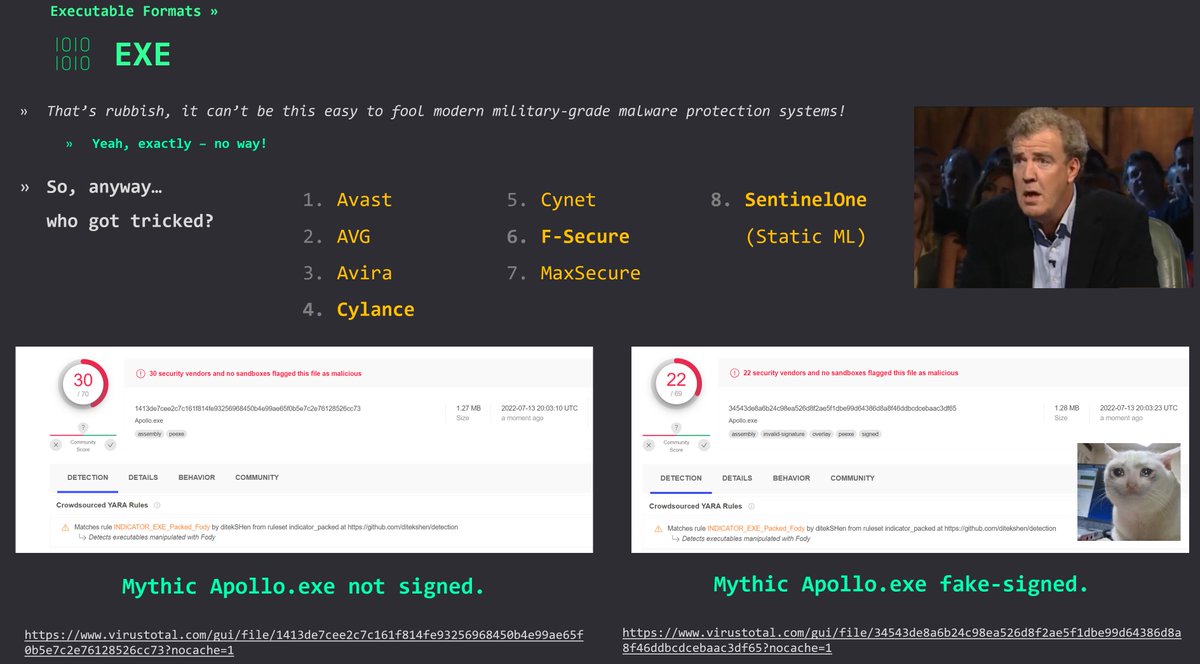
- "... and then he said to sign my malware.exe with faked Microsoft cert to evade AVs/EDRs. Would you believe?" ( ̄y▽ ̄)╭ Ohohoho..... Sign-Artifact.ps1 - based on @mattifestation research & implementation shamelessly borrowed here: github.com/mgeeky/Penetra…
zyxel.com/support/Zyxel-… Pedro and Darren from CipherTechs Red Team credited in Zyxel advisory
cisa.gov/known-exploite… sort by date added. These are actively exploited bugs - good priority list for patching.
cisa.gov/uscert/ncas/al… there's been a few of these. Along with patching, be sure to remove management interfaces from the Internet.
WSO2 exploit for CVE-2022-29464 is now public github.com/hakivvi/CVE-20… Patch details here docs.wso2.com/display/Securi…
LAPSUS$ extortion group claims to have breached @Okta. They have released 8 photos as proof. The photos we are sharing has been edited so no sensitive information or user identities are displayed. Image 1 - 4 attached below.


Sandy Bacik, Director of Audit and Compliance at @CipherTechs, will present on PCI 4.0 next week at SecureWorld Philadelphia. See the conference agenda and register here: hubs.li/Q0168mQt0 #SWPHL22 #GRC

container escape unit42.paloaltonetworks.com/cve-2022-0492-…. "Containers running with AppArmor, SELinux or Seccomp are protected"
Zabbix RCE
Our researchers discovered a high-severity code vulnerability in the open-source monitoring platform Zabbix. Learn more about this authentication bypass in our latest publication🔥 blog.sonarsource.com/zabbix-case-st… #appsec #cve-2022-23131 #cve-2022-23134
blog.qualys.com/vulnerabilitie… Polkit LPE. Reminder to make removing setuid part of your standard Linux builds.
Can confirm! ➡️Splashtop SRUtility.exe ➡️AnyDesk AnyDesk.exe AnyDeskMSI.exe ➡️Atera AteraAgent.exe AgentPackageSTRemote.exe AgentPackageHeartbeat.exe AgentPackageWindowsUpdate.exe AgentPackageADRemote.exe Thanks for sharing @AltShiftPrtScn!
#Conti ransomware affiliates using AnyDesk, Atera, Splashtop, Remote Utilities and ScreenConnect to maintain network access. During initial stage of IR I recommend blocking ALL remote access tools via Application Control policies, allow only the ones required & monitor their use.
Arbitrary file write on Windows domain controllers bugs.chromium.org/p/project-zero…. Microsoft guidance here msrc.microsoft.com/update-guide/v…
This could be like shellshock where it takes weeks to find all the appliances and SaaS that are affected. If you use log4j (and you probably do) check out github.com/nice0e3/log4j_… and . This is a juicy bug.
United States 趨勢
- 1. Jets 114K posts
- 2. Sauce 80.2K posts
- 3. Colts 54.6K posts
- 4. Courtois 37K posts
- 5. Breece Hall 10.3K posts
- 6. Quinnen Williams 24.4K posts
- 7. Garrett Wilson 5,114 posts
- 8. $JFB N/A
- 9. Cheney 229K posts
- 10. Luis Diaz 27.1K posts
- 11. Liverpool 206K posts
- 12. Beane 4,662 posts
- 13. AD Mitchell 6,458 posts
- 14. Bayern 109K posts
- 15. Hakimi 26K posts
- 16. Veach 5,245 posts
- 17. Shaheed 16.6K posts
- 18. Mazi Smith 5,665 posts
- 19. Brad Holmes 1,123 posts
- 20. Jermaine Johnson 3,256 posts
Something went wrong.
Something went wrong.










































































![remco_verhoef's profile picture. Founder DutchSec // SANS ISC Handler // GIAC // OSC[P|E] // Rustician // Gopher // ML / DL / Deception / 🍯 / Evil Emacs](https://pbs.twimg.com/profile_images/1055171039272099846/cp6p307C.jpg)