#cve search results
🚨Sitecore CVE-2025-53690 (CVSS 9.0) POC I just dropped a blog about CVE-2025-53690 🔹 Fully weaponized POC 🔹 Sneaky MemShell persistence tricks 🔹 Nuclei template I built to scan at scale eriklearningsec.com/p/cve-2025-536… Feedbacks are welcome! #infosec#sitecore #rce #cve

🚨 CVE-2025-64446 - critical 🚨 FortiWeb - Authentication Bypass > A relative path traversal vulnerability in Fortinet FortiWeb 8.0.0 through 8.0.1, For... 👾 cloud.projectdiscovery.io/library/CVE-20… @pdnuclei #NucleiTemplates #cve
Christine @x71n3 and JBO (@yo_yo_yo_jbo ) (& Alexia Wilson) from @Microsoft showed #OBTS how Spotlight just got too bright. 😬 They found a macOS TCC bypass (#CVE-2025-31199) that abuses Spotlight to get your private data - locally and remotely - and showed how to detect!


Ian Beer (@i41nbeer) from @Google’s Project Zero spoke again at #OBTS! Zero’ing read-only pages in XNU - possible? Yes! Weaponizing the bug ( #CVE-2025-24203 ) to get root? Yes!!

⚠️#INCIBEaviso | Cross-Site Scripting (XSS) en Omnichannel de #xCally #CVE CVE-2025-40681 incibe.es/incibe-cert/al… #AvisosDeSeguridad #TI #CNA

I no longer test VDP programs. However, since this is an open-source project and vulnerabilities found can be assigned CVEs, I spent some time last week reviewing it. I'm also glad that these are my first 4 CVEs #bugbounty #CVE

Sal (@malwarezoo) from @jamf gave an excellent talk at #OBTS of how Apple tracks and revokes malicious apps. But Revoked doesn’t always mean Vanquished! Sal found a Gatekeeper/CDHash weakness that brings blocked apps back to life — no re-signing required. #CVE-2025-43296

Just got 2 CVEs assigned from a major CRM software application (5 Million+ users): 1. CVE-2025-64489 2. CVE-2025-64490 Can't disclose much, public release is pending. #CVE



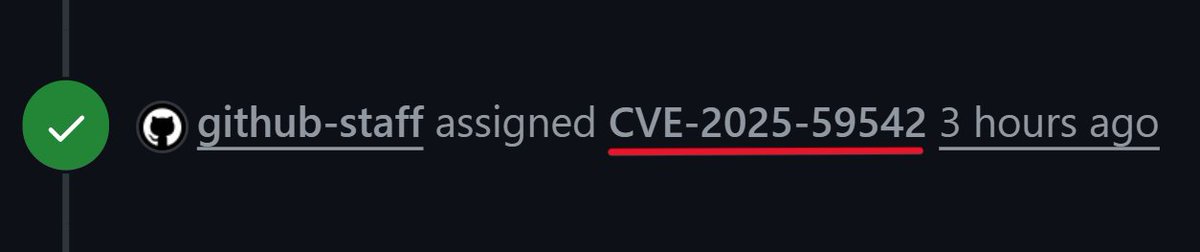
Just got 3 CVEs assigned for 0-days i discovered in a major LMS (30 Million+ users): 1. CVE-2025-59541 : CSRF (High 🟠) 2. CVE-2025-59542 : Account Takeover (Critical🔴) 3. CVE-2025-59543 : Account Takeover (Critical🔴) Can’t disclose much, public release is pending. #CVE

⚠️#INCIBEaviso | Cross-Site Scripting (XSS) en #SOPlanning #CVE CVE-2025-41001 incibe.es/incibe-cert/al… #AvisosDeSeguridad #TI #CNA

Update for #CVE-2025-52970 a RCE in Fortinet - Fortiweb web application firewall. We have signs of active exploitation of this CVE in the wild. Check our advisory: bit.ly/4oNuS6e #patch #patch #patch
Tanium is now a CVE Numbering Authority (CNA) assigning CVE IDs for Tanium products & in 3rd-party software discovered by Tanium that are not in another CNA’s scope cve.org/Media/News/ite… #CVE #CNA #Vulnerability #VulnerabilityManagement #Cybersecurity @CVEnew @Tanium

ooooooooh 🟥 CVE-2025-10230, CVSS: 10.0 (#Critical) Samba New CVE reported for a critical vulnerability in WINS hook handling. Unsanitized NetBIOS names from registration packets can lead to remote command execution by unauthenticated attackers. #CyberSecurity #CVE…

Django Software Foundation is now a CVE Numbering Authority (CNA) assigning CVE IDs for only supported and end-of-life Django versions, and projects, excluding distributions maintained by third-party redistributors. cve.org/Media/News/ite… #CVE #CNA #Cybersecurity @CVEnew

Warning: Privilege Escalation flaw in #Cisco Catalyst Center VA. #CVE-2025-20341 CVSS:8.8. Authenticated attackers with Observer role can send crafted HTTP requests to gain Administrator privileges! This enables unauthorized system changes & account creation. #Patch #Patch #Patch
🔴 Triofox, Improper Access Control, #CVE-2025-12480 (Critical) dailycve.com/triofox-improp…
Altera is now a CVE Numbering Authority (CNA) assigning CVE IDs for Altera products only cve.org/Media/News/ite… #CVE #CNA #Vulnerability #VulnerabilityManagement #Cybersecurity @CVEnew @AlteraFPGA_

Offensive SIEM 👊🏽 Flip your SIEM mindset from reactive detection to proactive hunting. Uncover local privilege escalations, hidden misconfigs, and even potential #CVE before attackers do 🔥🔥 🎥 youtu.be/5nfL_4ek4dY #BlueTeam #SIEM #CyberSecurity #ThreatHunting #DFIR

youtube.com
YouTube
SEC-T 0x11: Erkan Ekici & Shanti Lindström - Offensive SIEM: When the...
⚠️#INCIBEaviso | Cross-Site Scripting (XSS) almacenado en #Smart School #CVE CVE-2025-41107 incibe.es/incibe-cert/al… #AvisosDeSeguridad #TI #CNA

🚨 CVE-2025-58083: General Industrial Controls Lynx... Authentication-free device reset in Lynx+ Gateway exposes industrial systems to complete remote takeover with zero barr... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-58083 - Security Alert
General Industrial Controls Lynx+ Gateway is missing critical authentication in the embedded web server which could allow an attacker to remotely re...
🚨 CVE-2021-4470: TG8 Firewall Unauthenticated RCE ... Trivial root RCE via direct syscmd parameter injection in runphpcmd.php - zero auth required, zero sanitation, maximum i... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2021-4470 - Security Alert
TG8 Firewall contains a pre-authentication remote code execution vulnerability in the runphpcmd.php endpoint. The syscmd POST parameter is passed dire...
🚨 CVE-2025-13188: D-Link DIR-816L authentication.c... Stack-based overflow in DIR-816L's authentication.cgi lets attackers bypass auth with a crafted Password parameter - pu... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-13188 - Security Alert
A vulnerability was detected in D-Link DIR-816L 2_06_b09_beta. Affected by this vulnerability is the function authenticationcgi_main of the file /auth...
🚨 CVE-2025-64446 - critical 🚨 FortiWeb - Authentication Bypass > A relative path traversal vulnerability in Fortinet FortiWeb 8.0.0 through 8.0.1, For... 👾 cloud.projectdiscovery.io/library/CVE-20… @pdnuclei #NucleiTemplates #cve
Update for #CVE-2025-52970 a RCE in Fortinet - Fortiweb web application firewall. We have signs of active exploitation of this CVE in the wild. Check our advisory: bit.ly/4oNuS6e #patch #patch #patch
[CVE-2025-54339: CRITICAL] An Incorrect Access Control vulnerability was found in the Application Server of Desktop Alert PingAlert version 6.1.0.11 to 6.1.1.2 exploitable remotely for Escalation of Privileges.#cve,CVE-2025-54339,#cybersecurity cvefind.com/CVE-2025-54339
![CveFindCom's tweet image. [CVE-2025-54339: CRITICAL] An Incorrect Access Control vulnerability was found in the Application Server of Desktop Alert PingAlert version 6.1.0.11 to 6.1.1.2 exploitable remotely for Escalation of Privileges.#cve,CVE-2025-54339,#cybersecurity cvefind.com/CVE-2025-54339](https://pbs.twimg.com/media/G5vVcZ6WgAAJr1a.jpg)
[CVE-2025-54343: CRITICAL] An Incorrect Access Control vulnerability was found in the Application Server of Desktop Alert PingAlert version 6.1.0.11 to 6.1.1.2 exploitable remotely for Escalation of Privileges.#cve,CVE-2025-54343,#cybersecurity cvefind.com/CVE-2025-54343
![CveFindCom's tweet image. [CVE-2025-54343: CRITICAL] An Incorrect Access Control vulnerability was found in the Application Server of Desktop Alert PingAlert version 6.1.0.11 to 6.1.1.2 exploitable remotely for Escalation of Privileges.#cve,CVE-2025-54343,#cybersecurity cvefind.com/CVE-2025-54343](https://pbs.twimg.com/media/G5vVa8SXQAAN6ZO.jpg)
HackerOne Bug Bounty Disclosure: -authentication-token-theft-via-open-redirect-in-callback-url-parameter-sle-pyhead - redpacketsecurity.com/hackerone-bugb… #HackerOne #CVE #Vulnerability #OSINT #ThreatIntel #Cyber
Post-#FreeSyria Prevent Strategy: Glorifying violence is OK as long as you're a pro-LGBT mentally ill leftist retard 😂 #cve
[CVE-2025-64446: CRITICAL] Security alert: Fortinet FortiWeb versions 8.0.0 through 8.0.1, 7.6.0 through 7.6.4, 7.4.0 through 7.4.9, 7.2.0 through 7.2.11, and 7.0.0 through 7.0.11 vulnerable to relative path...#cve,CVE-2025-64446,#cybersecurity cvefind.com/CVE-2025-64446
![CveFindCom's tweet image. [CVE-2025-64446: CRITICAL] Security alert: Fortinet FortiWeb versions 8.0.0 through 8.0.1, 7.6.0 through 7.6.4, 7.4.0 through 7.4.9, 7.2.0 through 7.2.11, and 7.0.0 through 7.0.11 vulnerable to relative path...#cve,CVE-2025-64446,#cybersecurity cvefind.com/CVE-2025-64446](https://pbs.twimg.com/media/G5usHXAWgAAm6s0.jpg)
🚨 CVE-2025-64446: Fortinet (CVSS: 9.1)... Path traversal in FortiWeb's HTTP handler grants admin command execution across multiple versions - prime target for pe... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-64446 - Security Alert
A relative path traversal vulnerability in Fortinet FortiWeb 8.0.0 through 8.0.1, FortiWeb 7.6.0 through 7.6.4, FortiWeb 7.4.0 through 7.4.9, FortiWeb...
🚨 CVE-2025-36251: AIX Command Execution (CVSS: 9.6... Nimsh SSL/TLS flaws in AIX/VIOS enable remote command execution with CVSS 9.6 - expanding on previous CVE-2024-56347 at... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-36251 - Security Alert
IBM AIX 7.2, and 7.3 and IBM VIOS 3.1, and 4.1 nimsh service SSL/TLS implementations could allow a remote attacker to execute arbitrary commands due t...
Warning: Privilege Escalation flaw in #Cisco Catalyst Center VA. #CVE-2025-20341 CVSS:8.8. Authenticated attackers with Observer role can send crafted HTTP requests to gain Administrator privileges! This enables unauthorized system changes & account creation. #Patch #Patch #Patch
Warning: Insecure Temporary File flaw in #Alienware Command Center 6.x. #CVE-2025-46369 CVSS/7.8. Affects versions < 6.10.15.0. A low-privilege local attacker can exploit it for Privilege Escalation. #Patch #Patch #Patch
🚨 CVE-2025-36096: AIX Insufficiently Protected Cre... NIM private keys in AIX/VIOS exposed to MITM attacks - classic case of key material stored without proper crypto protec... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-36096 - Security Alert
IBM AIX 7.2, and 7.3 and IBM VIOS 3.1, and 4.1 stores NIM private keys used in NIM environments in an insecure way which is susceptible to unauthorize...
🚨Sitecore CVE-2025-53690 (CVSS 9.0) POC I just dropped a blog about CVE-2025-53690 🔹 Fully weaponized POC 🔹 Sneaky MemShell persistence tricks 🔹 Nuclei template I built to scan at scale eriklearningsec.com/p/cve-2025-536… Feedbacks are welcome! #infosec#sitecore #rce #cve

🚨Detect Actor Token Abuse (#CVE-2025-55241) After verifying the details with @_dirkjan, I created a query to detect Actor Token abuse, regardless of the activity involved. The idea is simple: If these activities are S2S, they should originate from Microsoft service IPs. 🧐…

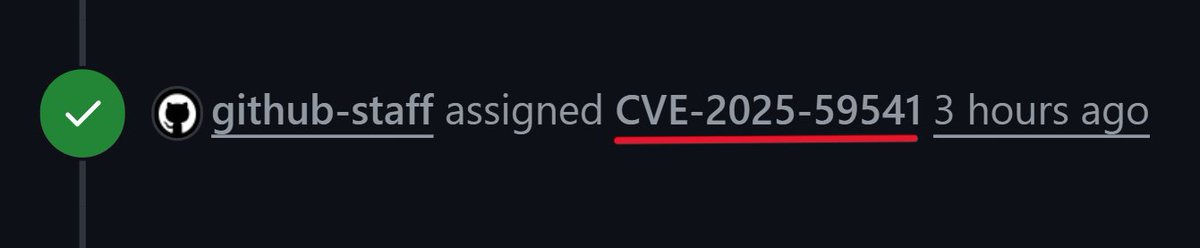
Just got 3 CVEs assigned for 0-days i discovered in a major LMS (30 Million+ users): 1. CVE-2025-59541 : CSRF (High 🟠) 2. CVE-2025-59542 : Account Takeover (Critical🔴) 3. CVE-2025-59543 : Account Takeover (Critical🔴) Can’t disclose much, public release is pending. #CVE



Excited 🎉 to share that I have been credited with my 4th CVE from Apple: CVE-2025-43356. This issue was addressed in Apple’s new security releases of iOS 26, iPadOS 26, and Safari 26. #Apple #CVE #BugBounty #iOS #ApplicationSecurity #iOS26



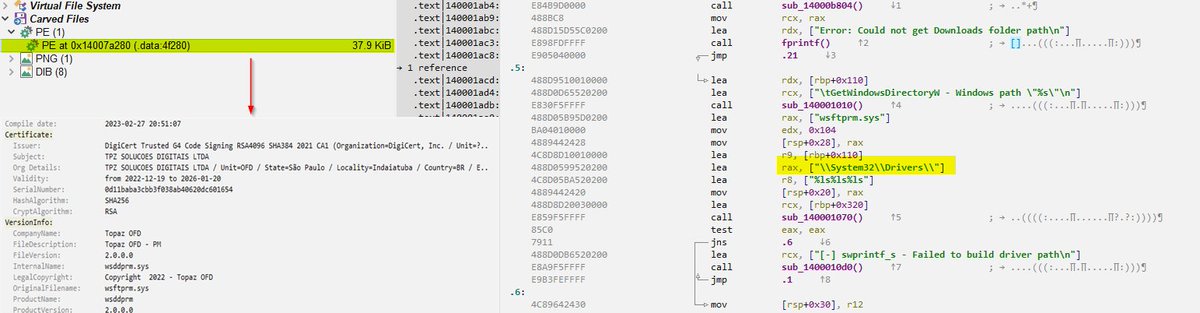
Observed threat actor abusing a vulnerable driver (wsftprm.sys, Topaz OFD – Brazilian antifraud vendor, #CVE-2023-52271) for defense evasion. Attack chain: cartel.exe → vulnerable driver → Lazarus.exe (final payload, extension ".cry"). First seen in Colombia. 1/3


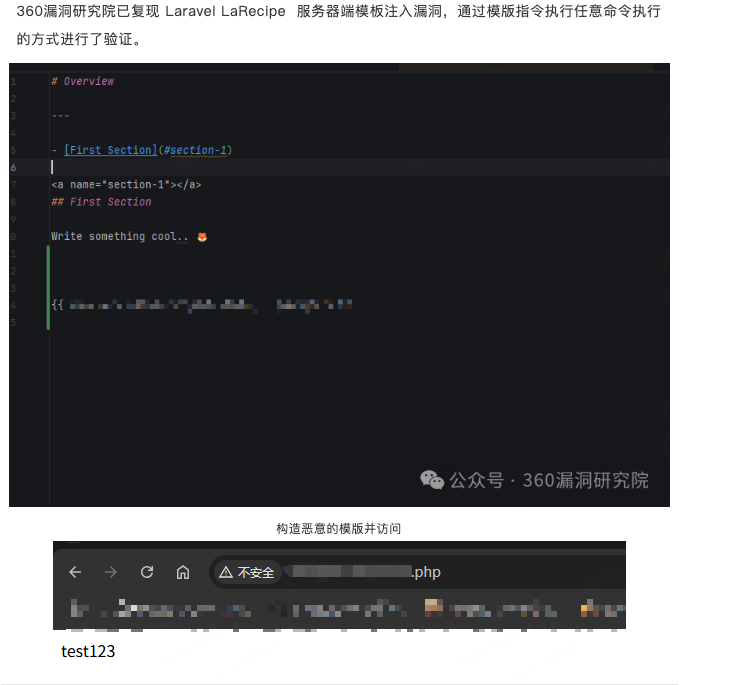
#CVE-2025-53833 挺直给的一个漏洞,直接官方demo即可快速复现,步骤见图1,和grok协同搞了个漏洞分析报告,见图2. 题外话,没看懂360这个复现。 github.com/saleem-hadad/l…


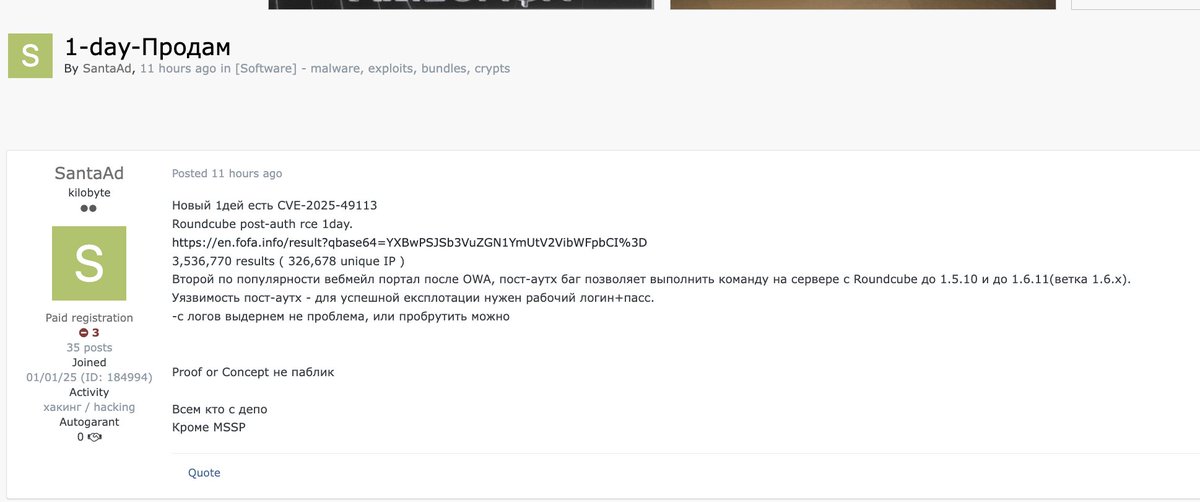
My research on CVE-2025-49113 is out. fearsoff.org/research/round…. Happy reading! #CVE #roundcube #poc @FearsOff

The exploit for CVE-2025-49113 is already available for sale on the dark web. I feel sorry for anyone who hasn’t upgraded to the newest version yet. Doomsday is coming, believe me. #roundcube #CVE @FearsOff
Looks like the patch for #CVE-2025-33073 might not fully resolve the issue... curious to see where this leads

🟥 CVE-2025-7775, CVSS: 9.2 (#Critical) NetScaler ADC and NetScaler Gateway, and NDcPP, Citrix. A memory overflow vulnerability leading to Remote Code Execution and/or Denial of Service. #CyberSecurity #CVE #Vulnerability #Citrix #RemoteCodeExecution #DenialOfService…

I’m excited to announce that I've been credited with my third CVE from @Apple CVE-2025-43228 Funny thing is, I reported this vulnerability back in August 2024 It has been addressed in the new iOS 18.6 and Safari 18.6 security update support.apple.com/en-us/124147 #CVE #BugBounty


🎉 We are excited to welcome Leonardo Spa as a #CVE Partner to help disseminate vulnerability information! For more info on efforts to protect #ICS or how your org can become a CVE Numbering Authority, visit 👉 cve.org/PartnerInforma…

6/21 SJ @darksheikftf @JordanCruzPro @KoTalphazo @DaveDutra @SandraMoonepie @kiddbanditpro @BrookeHavok @chrisnastyy_ @GinSevani @fatu_journey @JuicyFinau @link2futureftf @niczanderyb @boynamedrichie #cve #ddrefresh +more! Tickets⬇️ eventbrite.com/e/125868065070…

Christine @x71n3 and JBO (@yo_yo_yo_jbo ) (& Alexia Wilson) from @Microsoft showed #OBTS how Spotlight just got too bright. 😬 They found a macOS TCC bypass (#CVE-2025-31199) that abuses Spotlight to get your private data - locally and remotely - and showed how to detect!


I no longer test VDP programs. However, since this is an open-source project and vulnerabilities found can be assigned CVEs, I spent some time last week reviewing it. I'm also glad that these are my first 4 CVEs #bugbounty #CVE

📊 #VulnReport Security Summary - April 16, 2025. Today's vulnerability report shows over 200 new #CVE's across various platforms 🧵👇 ⚠️ Oracle Critical Patch Update released today with 50+ security fixes. Most critical: CVE-2025-30727 (CRITICAL 9.8) in Oracle Scripting.…

Ian Beer (@i41nbeer) from @Google’s Project Zero spoke again at #OBTS! Zero’ing read-only pages in XNU - possible? Yes! Weaponizing the bug ( #CVE-2025-24203 ) to get root? Yes!!

Just got 2 CVEs assigned from a major CRM software application (5 Million+ users): 1. CVE-2025-64489 2. CVE-2025-64490 Can't disclose much, public release is pending. #CVE



Just got 3 CVEs assigned for 0-days i discovered in a major LMS (30 Million+ users): 1. CVE-2025-59541 : CSRF (High 🟠) 2. CVE-2025-59542 : Account Takeover (Critical🔴) 3. CVE-2025-59543 : Account Takeover (Critical🔴) Can’t disclose much, public release is pending. #CVE



I propose to force people adding their own identity to each #CVE request the do. Someone have to be responsible, someone have to pay

Something went wrong.
Something went wrong.
United States Trends
- 1. Kevin James 5,623 posts
- 2. Bubba 35.6K posts
- 3. Bill Clinton 129K posts
- 4. Jack Hughes 2,290 posts
- 5. Metroid 12.5K posts
- 6. #BravoCon 5,593 posts
- 7. RIP Coach Beam 1,161 posts
- 8. $EDEL 1,123 posts
- 9. Marlene 5,257 posts
- 10. Last Chance U 5,802 posts
- 11. Vatican 16.2K posts
- 12. $GOOGL 21K posts
- 13. Matt Taylor 3,085 posts
- 14. Wale 46.7K posts
- 15. Oakland 11.8K posts
- 16. Donica Lewinsky 2,606 posts
- 17. Crooks 82.7K posts
- 18. Samus 6,491 posts
- 19. Hunter Biden 23.2K posts
- 20. Big Beautiful Bill 13.5K posts

















































































![vermaden's tweet image. New 𝗙𝗿𝗲𝗲𝗕𝗦𝗗 𝗝𝗮𝗶𝗹𝘀 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 (𝘃𝗲𝗿𝘀𝘂𝘀 𝗣𝗼𝗱𝗺𝗮𝗻) [FreeBSD Jails Security (versus Podman)] article on the blog.
vermaden.wordpress.com/2025/04/11/fre…
#verblog #containers #CVE #docker #freebsd #jail #jails #linux #podman #security #server #vnet](https://pbs.twimg.com/media/GoNnqdaX0AAAqdL.jpg)