Code Autonomous🪂
@CodeAutonomous
Cybersecurity | AI | Aviation |
The @DeptofWar’s New Critical Technology Areas: 🤖 Applied Artificial Intelligence ⚛️ Quantum & Battlefield Information Dominance 🧬 Biomanufacturing 🚛 Contested Logistics Technologies ⚡ Scaled Directed Energy 🚀 Scaled Hypersonics Technological dominance loading…
The national security challenges we face today demand that the @DeptofWar innovate with uncompromising speed. Proven, tangible technologies must be placed into the hands of our warfighters so they never face a fair fight. That’s why today I’m announcing the @DeptofWar’s new…
100% 👇 Besides, work-life balance is meaningless if you truly love what you do
Please do NOT come work for any company I have founded or am investing in if this LMT pro-mediocracy ad appeals to you. We are deterring our adversaries to save millions of lives, and reshoring to build the next American century. Not whatever this is.

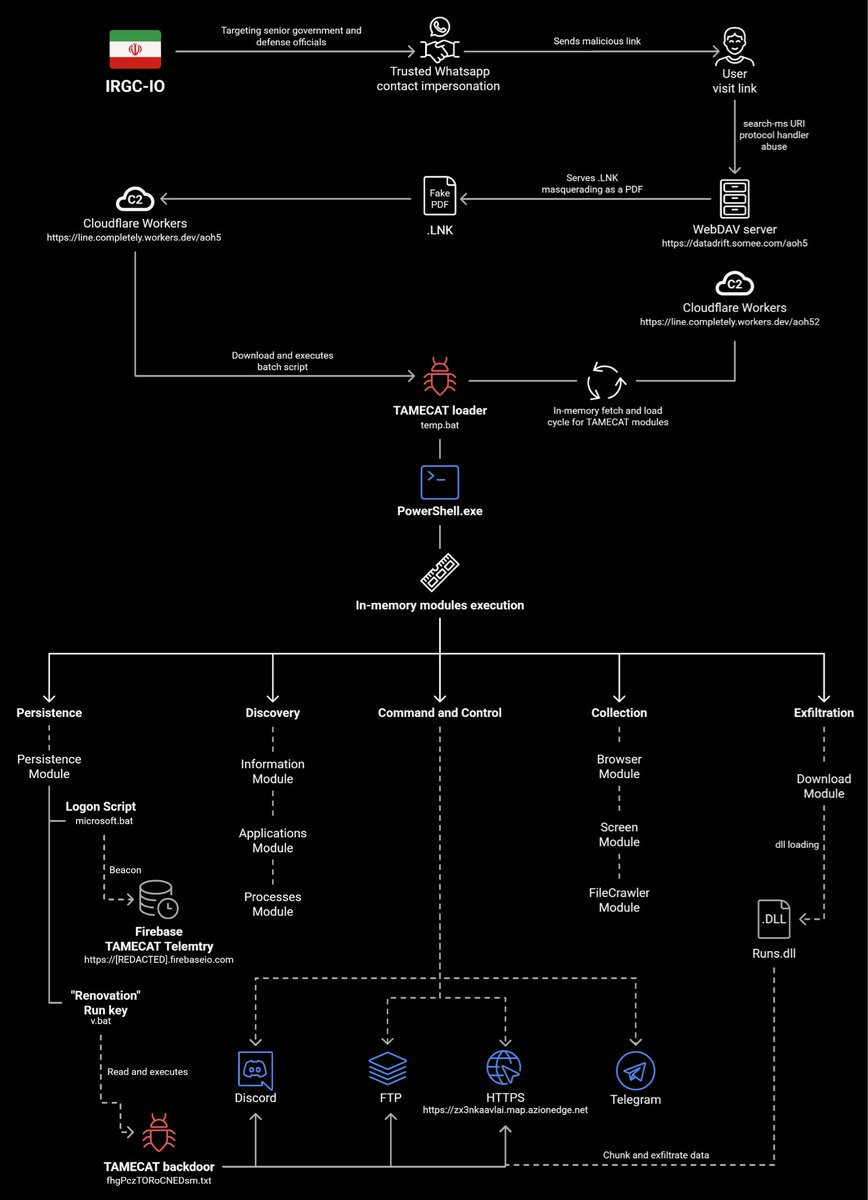
#APT42 Uses fake conference pages to capture credentials, redirects to OneDrive WebDAV shares, downloads LNK files disguised as PDFs, executes curl commands to fetch batch scripts (Temp.bat) from Cloudflare Workers, and loads the PowerShell-based TAMECAT backdoor: A modular,…
NVIDIA's $1 billion investment in Nokia to build an AI-powered 6G network is a significant signal for the future of infrastructure with AI.
The November 2025 security updates are available:
Security updates for November 2025 are now available! Details are here: msft.it/6018SZEg0 #PatchTuesday #SecurityUpdateGuide

Dive into the heart of threat intelligence as Principal Security Researcher @yo_yo_yo_jbo reveals how proactive security research powers Microsoft’s defenses: msft.it/6016tJxce. The relentless hunt for vulnerabilities—like the HM Surf exploit—spotlights how research doesn’t…
🏦 AI Bank Statement Analyzer (Made by the LangChain Community) Transform bank statements into queryable financial insights using AI. This system combines YOLO and LangChain's RAG to enable natural language analysis of your personal finances. Check it out here ⚡…

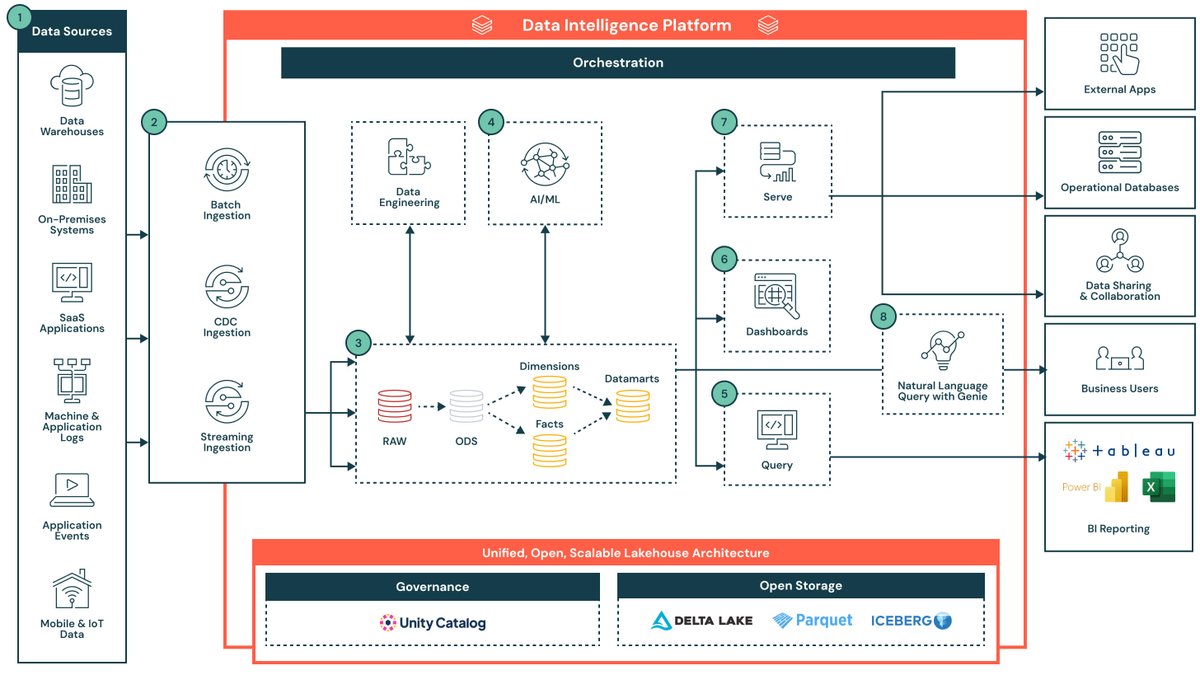
You asked for it. We built it. A library of architectural diagrams that show practical ways to build pipelines, dashboards, and AI models. Find designs for common data and AI builds across use cases and industries, including: - Data Ingestion - AI Security Framework - Next Best…
Three large #drones conducted targeted surveillance over Belgium’s #KleineBrogel airbase—which stores US #nuclear weapons—on the night of November 1-2, 2025, evading Belgian military #drone jammers and police helicopter pursuit in what Defense Minister... dronexl.co/2025/11/02/bra…
🔍 OpenAI released Aardvark - an autonomous security agent powered by GPT-5 that hunts for vulnerabilities in code 🧵 Been waiting for them to do this.... openai.com/index/introduc…
The old paradigm: go to a good school, get a degree and get a good job... is dead. The new paradigm: find your purpose, start a company, create and lead is our future Entrepreneurship is the only future career .
As an engineer crunching growth models daily, Prof. Albert Bartlett's "bacteria in a bottle" demo is a brutal wake-up: Exponential growth isn't linear—it's a system killer. Rule of 70 says 1% doubles in 70 years. Recalibrate your forecasts NOW.Mind-blowing watch:…

youtube.com
YouTube
Our inability to understand the exponential function is our biggest...
🚀 The #USAF's Collaborative Combat Aircraft (CCA) program is transforming the future of air dominance! With AI-powered autonomous drones teaming with 5th/6th gen fighters, the CCA initiative aims for scalable, cost-effective airpower to outpace threats. First CCAs expected in…
Israel’s F-35I Adir ‘Mighty One’ Fighter Has a Message for Every Air Force on Earth - nationalsecurityjournal.org/israels-f-35i-… #F35 #IsraelAirForce #Adir #AerospaceTech
CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
Get Rich Scheme For Techies - practice training small LLMs - produce a small LLM (3B model) that is SOTA - use common crawl data for pre-training - perform some basic fine-tuning with open-source, good-quality datasets - make a post on X and show off your benchmarks - create a…
Azure Blob Storage is a high-value target for threat actors due to its critical role in storing and managing massive amounts of unstructured data at scale across diverse workloads: msft.it/6012s7pip. Threat actors are actively seeking opportunities to compromise…
We’re acquiring @Arduino to make edge computing and #AI more accessible. Arduino will remain independent, supporting multiple silicon vendors and its community. Launching today: Arduino UNO Q, powered by Qualcomm #Dragonwing. Discover more: bit.ly/4nE0rP2

United States Tren
- 1. #RiyadhSeason 14.4K posts
- 2. Mason 37.9K posts
- 3. Syracuse 8,191 posts
- 4. Lincoln Riley 1,543 posts
- 5. Oregon 27.7K posts
- 6. #AEWTailgateBrawl 1,795 posts
- 7. #AEWFullGear 7,070 posts
- 8. Arch Manning 3,111 posts
- 9. #TheRingIV 4,153 posts
- 10. Joe Jackson 1,171 posts
- 11. Stoops 1,700 posts
- 12. Kansas State 3,094 posts
- 13. Arkansas 9,907 posts
- 14. #GoBlue 2,513 posts
- 15. Vandy 3,422 posts
- 16. Jonathan Smith N/A
- 17. Jeremiyah Love 3,828 posts
- 18. Fran Brown N/A
- 19. Sadiq 8,162 posts
- 20. Harden 31.4K posts
Something went wrong.
Something went wrong.