The whitepaper is live! Learn how to win the HTTP desync endgame... and why HTTP/1.1 needs to die: http1mustdie.com
⚡️XBOW found LFI where most tools would have given up. Photo download endpoint blocked all path traversal attempts. But JavaScript analysis revealed /photo/proxy?url= - vulnerable to file:// scheme access. Successfully read a password file via proxy endpoint. Technical…
Day 2 is packed with some 🔥 talks! Check out the entire schedule on NahamCon.com! Remember this is 100% free, no tickets or anything needed. Just show up and watch the talks!

🎉 Hyped for #NahamCon2025! ✨ Day 1: Full AI x Offensive Security track with @jhaddix, @rez0__ , @DanielMiessler,@wunderwuzzi23, @monkehack, @xssdoctor. Details: NahamCon.com #InfoSec #bugbounty #CyberSecurity

the research paper is out: Next.js and the corrupt middleware: the authorizing artifact result of a collaboration with @inzo____ that led to CVE-2025-29927 (9.1-critical) zhero-web-sec.github.io/research-and-t… enjoy the read!

You might have noticed that the recent SAML writeups omit some crucial details. In "SAML roulette: the hacker always wins", we share everything you need to know for a complete unauthenticated exploit on ruby-saml, using GitLab as a case-study. portswigger.net/research/saml-…
Let me share our latest "Gudifu" paper and tool about a new search technique for parsing discrepancies between HTTP servers. The Gudifu tool has discovered several previously unknown attack vectors on popular server pairs such as Request Smuggling, Access Control Bypass and

Per popular demand, Turbo Intruder 1.51 now inserts results at the top of the table so you can watch them arrive without scrolling! Let me know how you find it. If you prefer the old behaviour, you can change it back using: table.setSortOrder(0, False)
Critical vulnerabilities doesn't have to be complex or have a CVE - @deepseek_ai publicly exposed their internal ClickHouse database to the world, without any authentication at all, and leaked sensitive data. No one is safe from security mistakes, follow along to learn more 🧵

One more example for bad behavior / Scam in paid subscription for bugbounty santimillionaire.com I was there for the last 5 months trying to find something useful but unfortunately nothing , just a ready payloads and some tips filtered for each bug and this month I found…


🎉✨ Big News for GOLDEN PLAN License Winners! ✨ Congratulations again to our 10 lucky winners! We have an important update: out of the 10 winners, only 9 have completed all the required steps to claim their license. 🕒 To the selected winners: Please ensure you message us…
🛑 GIVEAWAY ALERT 🛑 ⬇️ Today is day SIX of EIGHT days of @arcanuminfosec and friends Black Friday and Cyber Monday giveaways! Today game recognizes game. If you’ve taken my classes, you know I always recommend @LearnPrompting. Today, I’m giving away one free seat to their…
🛑 GIVEAWAY ALERT 🛑 Today is day THREE of FIVE days of @arcanuminfosec and friends Black Friday and Cyber Monday giveaways! Today we are giving away FIVE seats to our NEW training: "Hacking Your Career" HYC releases in January and is PACKED with actionable advice to…

🚀Black Friday Giveaway!🤗 *** 𝗙𝗼𝗹𝗹𝗼𝘄 𝗼𝘂𝗿 𝗽𝗮𝗴𝗲, 𝗥𝗲𝗽𝗼𝘀𝘁, 𝗟𝗶𝗸𝗲 𝗮𝗻𝗱 𝗖𝗼𝗺𝗺𝗲𝗻𝘁 𝘄𝗵𝗶𝗰𝗵 𝗲𝘅𝗮𝗺 𝘆𝗼𝘂 𝘄𝗼𝘂𝗹𝗱 𝗹𝗶𝗸𝗲 𝘁𝗼 𝘄𝗶𝗻 𝗮𝗻𝗱 𝟱 𝗹𝘂𝗰𝗸𝘆 𝘄𝗶𝗻𝗻𝗲𝗿𝘀 𝘄𝗶𝗹𝗹 𝗴𝗲𝘁 𝗮 𝗳𝗿𝗲𝗲 𝗲𝘅𝗮𝗺 𝗼𝗳 𝘁𝗵𝗲𝗶𝗿 𝗰𝗵𝗼𝗶𝗰𝗲! *** Get…

🔴 GIVEAWAY ALERT 🔴 Our AI Red Teaming cohort is over 50% full and starts in just 9 days! For Black Friday, we're giving away TWO seats to our course, which is led by the world's top AI Security Experts! RT this post & Comment below to enter! Winners announced on Dec. 1st!

🎁 End of Year Giveaway 🎁 Hack The Box 6-month VIP+ x1 - Follow, Like, and Retweet to join! - Winner will be picked randomly on December. #hackthebox #giveaway #projectsekaictf

🚨 I convinced my team to do one last giveaway! Options: hhub.io/eu2wxGj 🏆 Full Access: $199 💻 Lifetime Course: $39 (includes updates) 🎯 1-Month trial (no updates): $19 TWO WINNERS (1 each): - Full cert bundle - Lifetime access Enter: ↪️ RT + Reply with 🎯
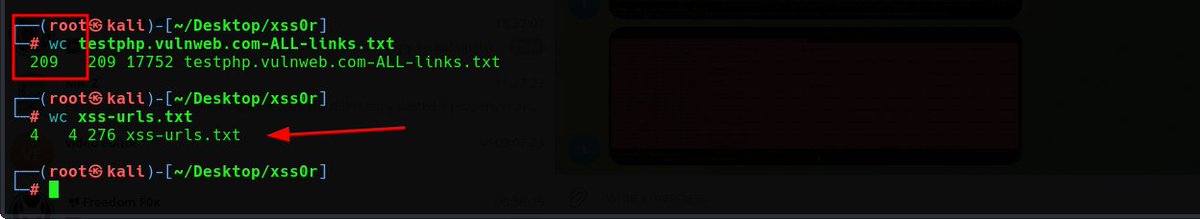
#xss0rRecon script ! From a total of 209 links crawled from the testphp.vulnweb.com site, xss0rRecon identified 4 URLs potentially vulnerable to reflected XSS attacks. This demonstrates the power and efficiency of xss0rRecon. Currently tested on Debian, with configurations…
youtube.com/watch?v=vPwV4x… I just came across an amazing video showcasing the XSS to Account Takeover process using the xss0r Tool! 😱 This video highlights just how powerful and effective the tool is when it comes to finding and exploiting XSS vulnerabilities. If you haven’t seen…

youtube.com
YouTube
From CSRF to Blind XSS | Self XSS to Blind XSS | XSS0R v2| XSS to ATO
📢 Feature Highlight from the xss0r Tool - Day 4 📢 Today, let’s explore the POST Request Features of the xss0r tool. With three supported formats, xss0r allows comprehensive testing for POST requests, ensuring every injection point is thoroughly checked. Let's break it down:…
United States 趨勢
- 1. #StrangerThings5 279K posts
- 2. Thanksgiving 709K posts
- 3. BYERS 65.6K posts
- 4. robin 100K posts
- 5. Afghan 311K posts
- 6. Dustin 78.1K posts
- 7. Reed Sheppard 6,613 posts
- 8. Holly 68.3K posts
- 9. Vecna 64.9K posts
- 10. Jonathan 76.2K posts
- 11. Podz 5,015 posts
- 12. hopper 16.9K posts
- 13. Erica 19.1K posts
- 14. Nancy 70.2K posts
- 15. Lucas 85.4K posts
- 16. noah schnapp 9,320 posts
- 17. Joyce 34.3K posts
- 18. mike wheeler 10.3K posts
- 19. National Guard 687K posts
- 20. Tini 10.5K posts
Something went wrong.
Something went wrong.