David Andro Rivera
@ITSecAnalyst
CISSP, GCIH, Information Security Professional, Incident Respomse, Athlete, Gamer. #Security,#Infosec, #Hacking, #Technology.
Bạn có thể thích
#MagicRAT is the latest #malware from the well-known #LazarusGroup (a suspected North Korean APT). More on this new threat and Lazarus Group's overall goals here cs.co/6010MM7ng

Well this is going to be interesting - has @tiktok_us been breached?
#TikTok has allegedly suffered a data breach 🆘 Now is a good time to turn on 2-step verification if you haven't yet. Here's how you can secure your account: support.tiktok.com/en/safety-hc/a…

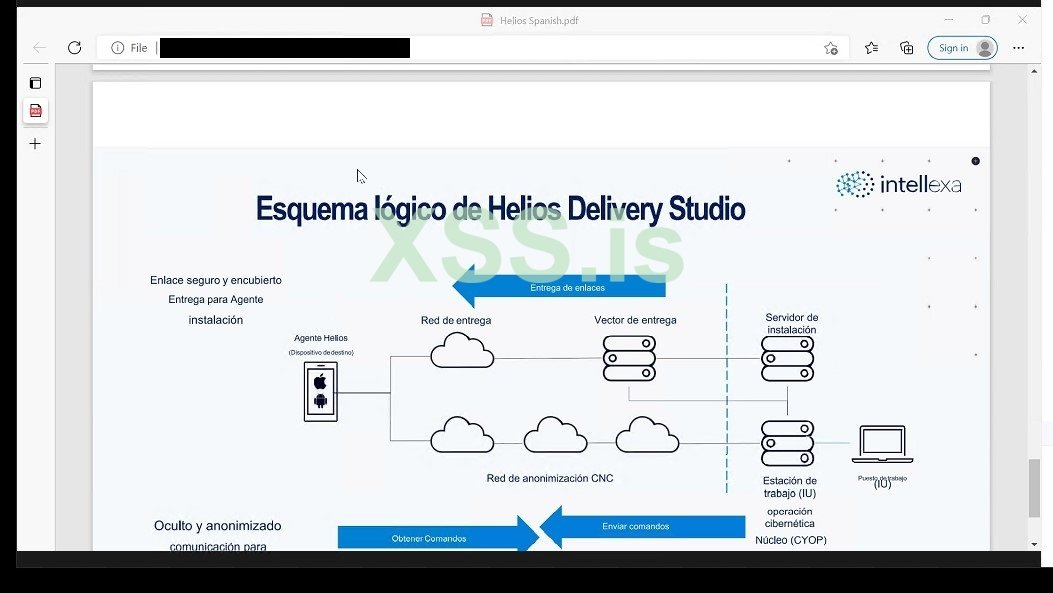
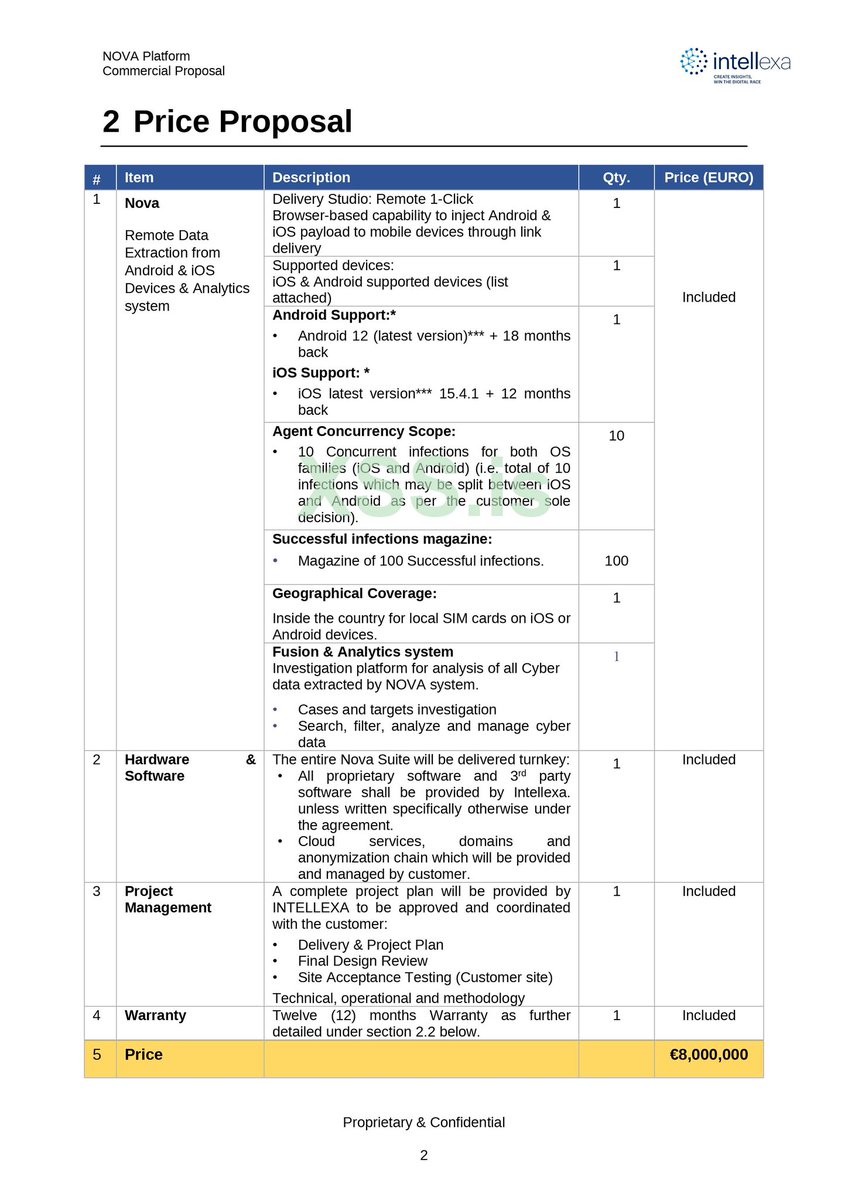
Leaked documents online show the purchase (and documentation of) an $8,000,000 iOS Remote Code Execution 0day exploit

Twilio discloses data breach after SMS phishing attack on employees - @serghei bleepingcomputer.com/news/security/…
Chinese hackers use new Windows malware to backdoor govt, defense orgs - @serghei bleepingcomputer.com/news/security/…
New PACMAN hardware attack targets Macs with Apple M1 CPUs - @serghei bleepingcomputer.com/news/security/…
2022-06-09 (Thursday) - #TA578 #Bumblebee malware infection led to #CobaltStrike activity on 23.82.141[.]226:443 using zupeyico[.]com - IOCs available at: bit.ly/3tuGY9v
![Unit42_Intel's tweet image. 2022-06-09 (Thursday) - #TA578 #Bumblebee malware infection led to
#CobaltStrike activity on 23.82.141[.]226:443 using zupeyico[.]com -
IOCs available at:
bit.ly/3tuGY9v](https://pbs.twimg.com/media/FU5d7NmXsAAPCfF.jpg)
Here’s my entry for the @nftmakerio art contest: Lost Relic. 🪨 GM Space Frens! 🖖 #NFTCommunity #CNFT #nftart #NFTartists #CardanoNFT #1millionNFTs
NFT-MAKER FAN ART CONTEST 🏆 Win a @spacebudzNFT 🖼 Get it featured in a collection in the upcoming NFT-MAKER Marketplace! 🗓Deadline: May 4th 🗳 Submit here: forms.gle/ixwBCNPaUPmTL7… 👨🎨 Artist: @whanepnft #Cardano #NFTCommunity #1millionNFTs
Stealer Malware Intelligence Report - Government 1,753,658 credentials of 49K+ government sites have been leaked from users infected with Stealer malware. *The users may include government users or public users of gov public services* TOP 10,000 sites: bit.ly/3sA7f6s


a quick mind map where I tried to group all previously shared Lsass cred access detection traces using Windows Logs (via sparce tweets) github.com/sbousseaden/Sl… Example of logs can be found here github.com/sbousseaden/EV…

Critical GitLab vulnerability lets attackers take over accounts - @serghei bleepingcomputer.com/news/security/…
Google has so little money that they had to fill this page with ads to the point of only having 1 actual result. One result on the entire page. The rest is ads.

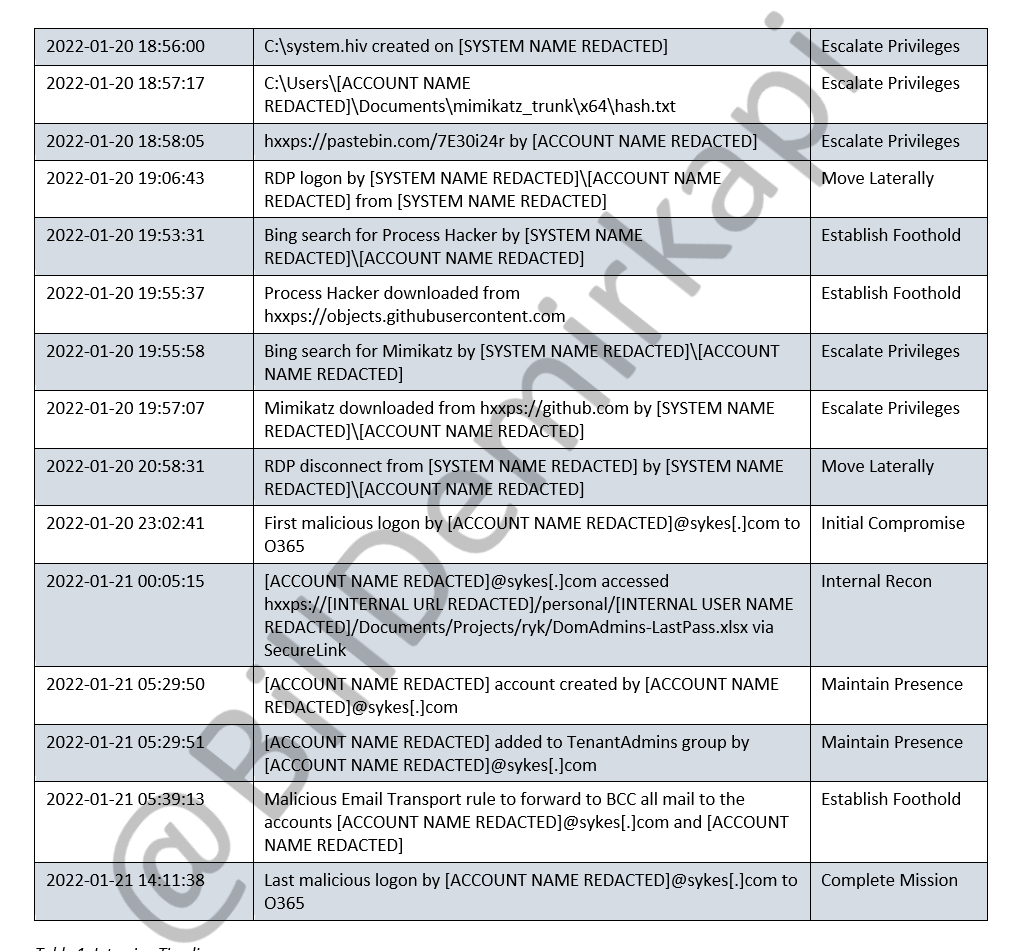
New documents for the Okta breach: I have obtained copies of the Mandiant report detailing the embarrassing Sitel/SYKES breach timeline and the methodology of the LAPSUS$ group. 1/N
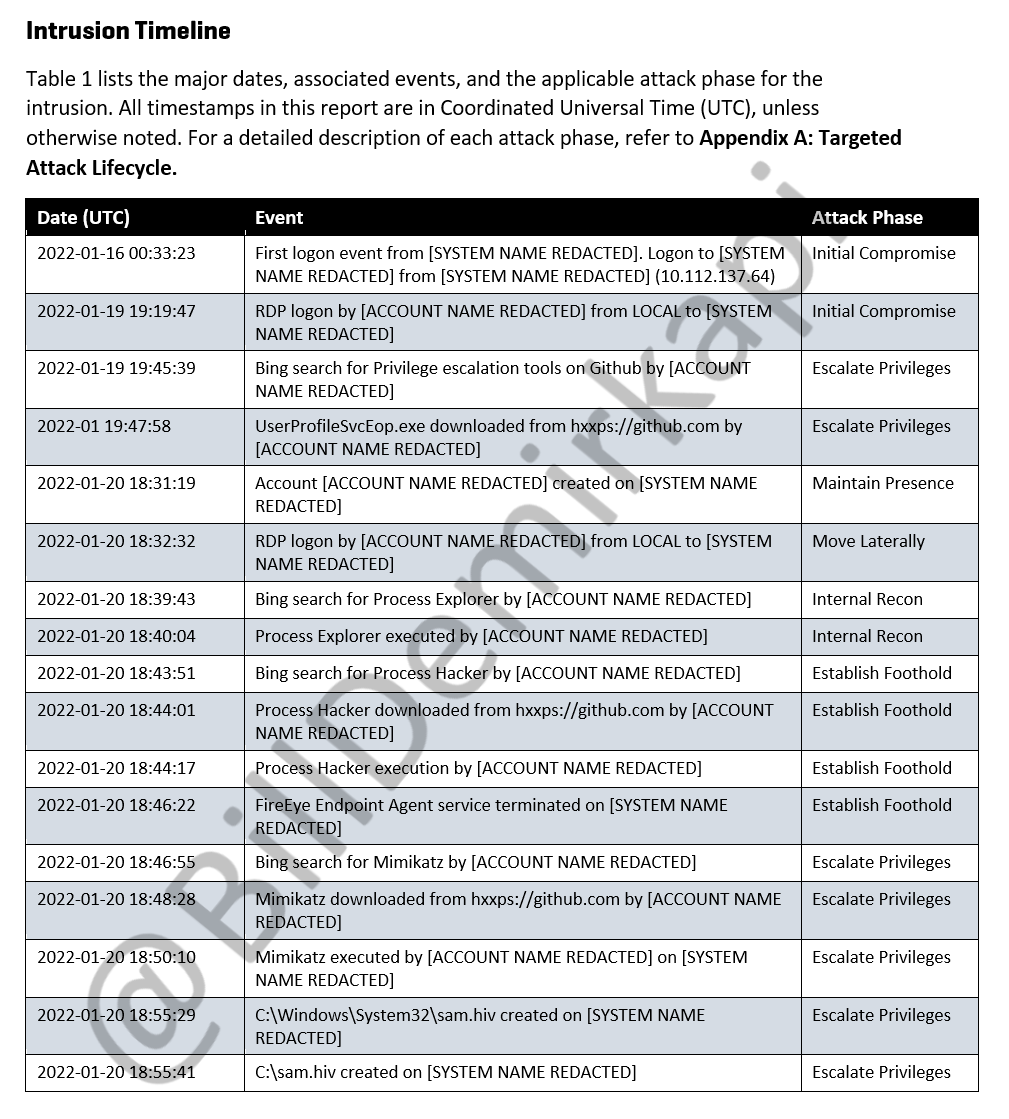
The LAPSUS$ ransomware group has claimed to breach Okta sharing the following images from internal systems.
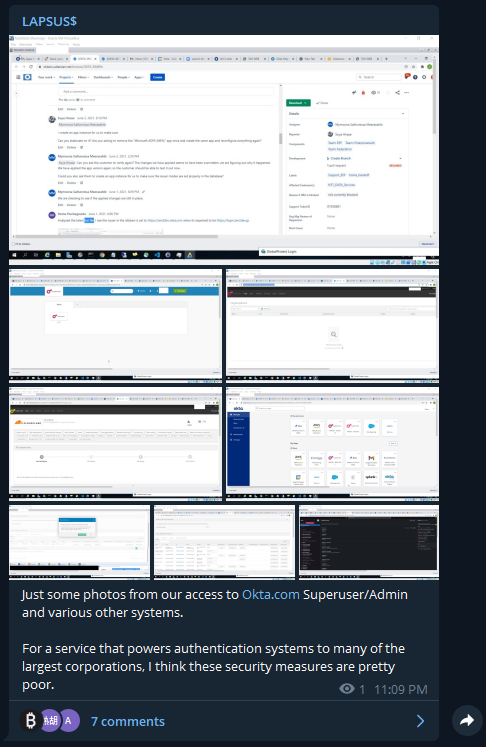

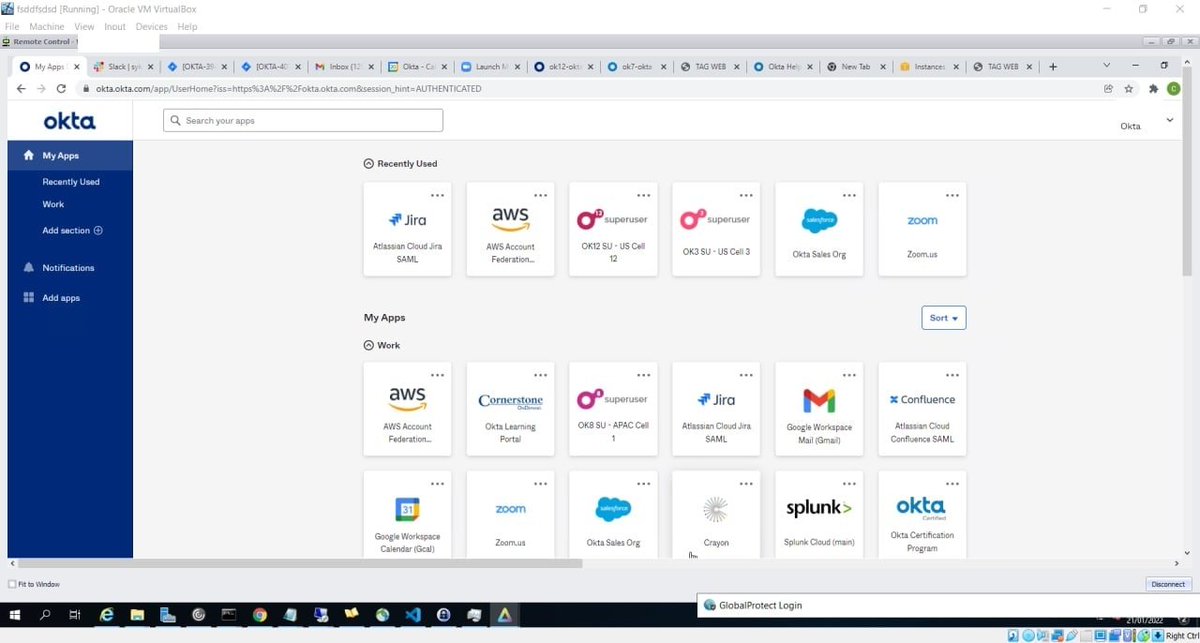

Microsoft Security has been tracking criminal actor DEV-0537 (LAPSUS$) targeting organizations with data exfiltration and destructive attacks - including Microsoft. Analysis and guidance in our latest blog: microsoft.com/security/blog/…
Spent past 2 days reading 14 months worth of leaked chats from the Conti ransomware group (so you don't have to). Today's Part I focuses on the group's internal efforts to evade actions by law enforcement & intel agencies. This is a bottomless gold mine. krebsonsecurity.com/2022/03/conti-…
VMware issues security patches for multiple high-severity vulnerabilities affecting ESXi, Workstation, Fusion, and Cloud Foundation products. ✅CVE-2021-22040 ✅CVE-2021-22041 ✅CVE-2021-22042 ✅CVE-2021-22043 ✅CVE-2021-22050 ✅CVE-2022-22945 thehackernews.com/2022/02/vmware… #infosec
United States Xu hướng
- 1. Good Thursday 27.6K posts
- 2. Happy Friday Eve N/A
- 3. ESPN Bet N/A
- 4. #thursdayvibes 2,144 posts
- 5. #thursdaymotivation 1,332 posts
- 6. #ThursdayThoughts 1,346 posts
- 7. #Talus_Labs N/A
- 8. #ThankfulThursday N/A
- 9. Lakers 85.7K posts
- 10. Vatican 10.7K posts
- 11. $APDN $0.20 Applied DNA N/A
- 12. $SENS $0.70 Senseonics CGM N/A
- 13. Grapefruit 1,522 posts
- 14. Unplanned 6,352 posts
- 15. Wemby 28.8K posts
- 16. Marcus Smart 6,992 posts
- 17. Blazers 9,989 posts
- 18. Captain Kangaroo 1,282 posts
- 19. Russ 12.2K posts
- 20. Shroud 5,855 posts
Something went wrong.
Something went wrong.