
Level Up Coding
@LevelUpCoding_
Level up your engineering & system design skills. Complex topics simplified. Thank you to our partner @getpostman who keep our content free to the community
Database Indexing Explained Most databases require some form of indexing to keep up with performance benchmarks. Searching through a database is much simpler when the data is correctly indexed, which improves the system's overall performance. A database index is a lot like…

How CI/CD pipelines work (explained in 2 mins or less): A CI/CD pipeline is an automated workflow that facilitates continuous integration (CI) and continuous delivery or deployment (CD) by managing code building, testing, and release processes. It integrates the various stages…

If I had to load balance traffic, here are 6 algorithms I'd consider: 1) Round robin 2) Weighted round robin 3) Least connections 4) IP hash 5) Random 6) Least response time There's no one-size-fits-all solution. When choosing, consider these key factors: ↳ Workload…

Myth: One model fits all. Reality: Pick Claude/GPT/Gemini/Llama for the task. AI models aren’t interchangeable. Each has different strengths in reasoning, latency, cost, and privacy. Treating them all the same leads to wasted tokens, inconsistent results, and frustrated…

8 Popular Network Protocols Explained. Network protocols operate at different layers of the OSI model. The protocols below operate at different layers, this is important to note. The OSI model is a conceptual framework that defines a networking system as a series of layers,…

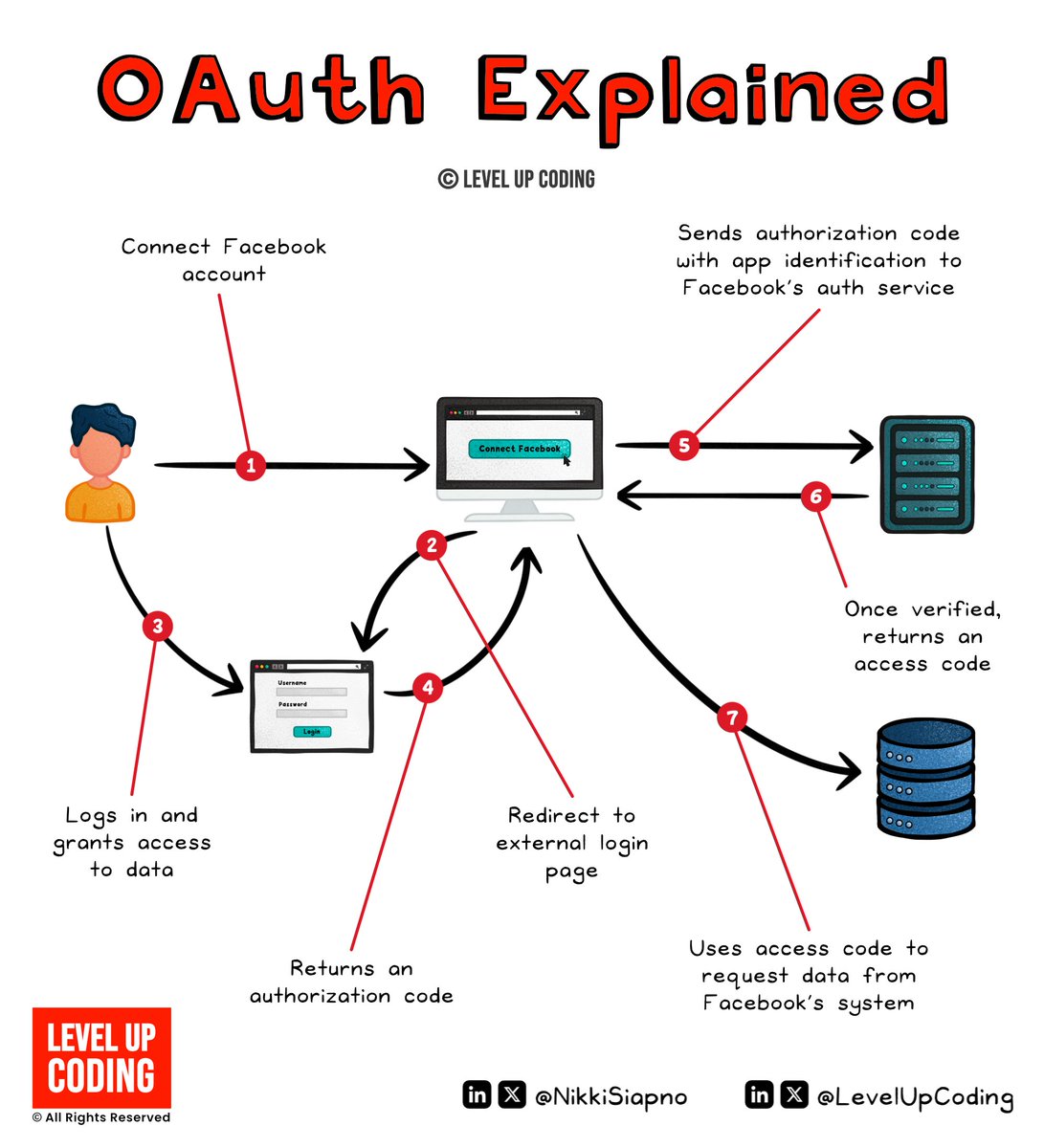
How OAuth 2.0 works (explained in 3 mins or less): It can be thought of as a digital handshake between the app, service, and user, with everyone agreeing on what is shared. It's an authorization framework that enables applications to access a user’s data on another service…
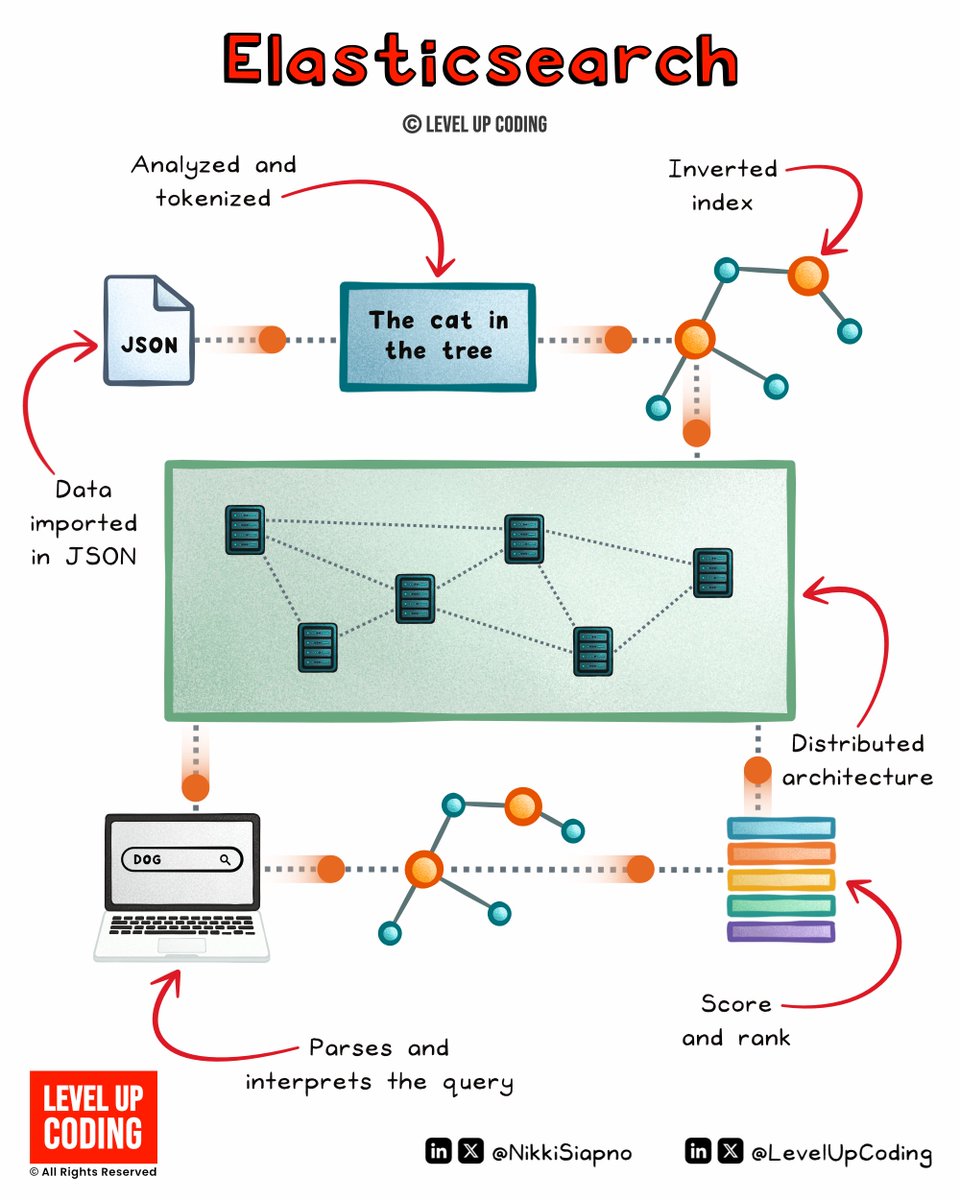
Elasticsearch Clearly Explained. Elasticsearch uses an inverted index to facilitate rapid full-text searches, enabling fast and efficient data access. It works similarly to how a book index works. Its distributed architecture not only enhances speed but also ensures high…
Things Every Developer Should Know: JSON Web Token (JWT). JWTs are one of the most widely used methods for API authentication, providing a secure, stateless and scalable way to verify clients. Here’s a simple-to-understand breakdown of how it works (step by step): 𝟭)…

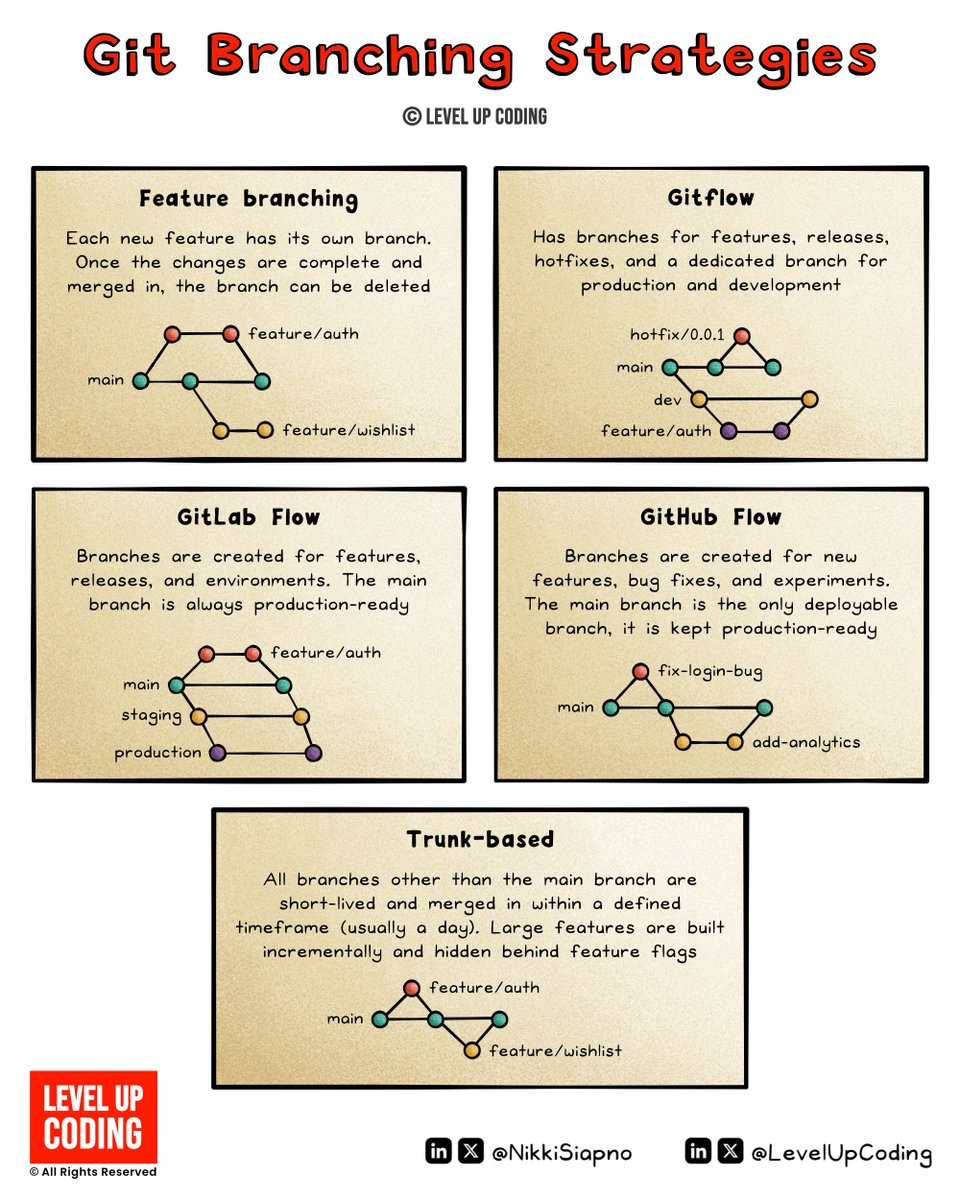
Git branching strategies clearly explained. A well-planned Git branching strategy helps coordinate the development team’s work and keeps the development process consistent. Let's take a look at some common approaches to branching: 𝗙𝗲𝗮𝘁𝘂𝗿𝗲 𝗯𝗿𝗮𝗻𝗰𝗵𝗶𝗻𝗴 is a popular…
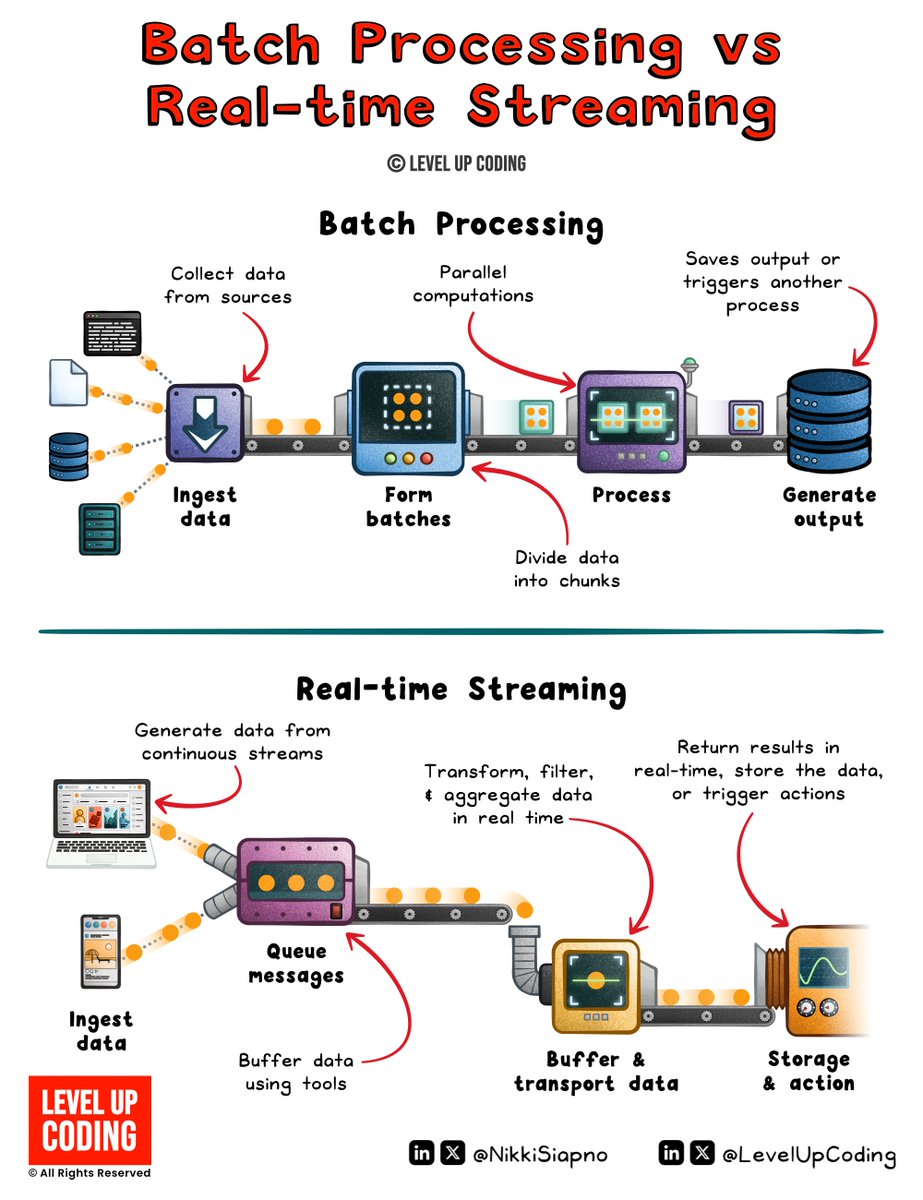
Batch Processing vs Real-time Streaming. Two approaches for your data pipelines, one goal: turning raw data into real insights. 𝗕𝗮𝘁𝗰𝗵 𝗽𝗿𝗼𝗰𝗲𝘀𝘀𝗶𝗻𝗴 handles large datasets at scheduled intervals. Think daily reports, monthly analytics, or ML model training. It’s…
How do we design secure and safe APIs? The rise in API-related security breaches highlights the necessity for robust API security. Let’s look at 12 essential tips for improving API security: 𝗥𝗮𝘁𝗲 𝗹𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗮𝗻𝗱 𝘁𝗵𝗿𝗼𝘁𝘁𝗹𝗶𝗻𝗴 ↳ Throttling and rate limiting…

Kafka’s architecture made it fast, but not cheap. Diskless Kafka makes it both. The future of Kafka just shipped. Aiven Inkless, the first production-ready implementation of Diskless Kafka, is now GA. This is huge news for Kafka users looking for lower cost, simpler ops, and…

If I had to optimize a CI/CD pipeline, here’s what I’d consider: The first step in optimizing any system is to analyze its processes and 𝗶𝗱𝗲𝗻𝘁𝗶𝗳𝘆 𝘁𝗵𝗲 𝗯𝗼𝘁𝘁𝗹𝗲𝗻𝗲𝗰𝗸𝘀 𝗮𝗻𝗱 𝗶𝗻𝗲𝗳𝗳𝗶𝗰𝗶𝗲𝗻𝗰𝗶𝗲𝘀. One of the biggest culprits for CI/CD performance? Build…

SSO (Single Sign-On) Clearly Explained. SSO can be thought of as a master key to open all different locks. It allows a user to log in to different systems using a single set of credentials. To fully understand the SSO process, let’s take a look at how a user would log into…

Atlassian just brought agentic AI to your entire workflow. Here’s what you need to know, and why I’ve been so impressed. Rovo Dev isn’t just an AI coding assistant. It’s agentic AI across the Atlassian ecosystem that connects agents across your workflows. Because it 𝗵𝗮𝘀…

ACID clearly explained. ACID stands for Atomicity, Consistency, Isolation, and Durability. These are the foundations of transaction systems, 𝗲𝗻𝘀𝘂𝗿𝗶𝗻𝗴 𝗮𝗰𝗰𝘂𝗿𝗮𝘁𝗲 𝗱𝗮𝘁𝗮 𝗲𝘃𝗲𝗻 𝗶𝗻 𝘂𝗻𝗲𝘅𝗽𝗲𝗰𝘁𝗲𝗱 𝘀𝗶𝘁𝘂𝗮𝘁𝗶𝗼𝗻𝘀 𝗹𝗶𝗸𝗲 𝘀𝘆𝘀𝘁𝗲𝗺 𝗰𝗿𝗮𝘀𝗵𝗲𝘀…

Compiles ≠ Correct. The biggest risk with AI-generated code isn’t that it looks wrong. It’s that it looks right. Sonar assessed 4,000+ Java assignments to see how today’s popular LLMs perform. The findings show why validation is critical: ↳ 𝗛𝗮𝗿𝗱-𝗰𝗼𝗱𝗲𝗱…

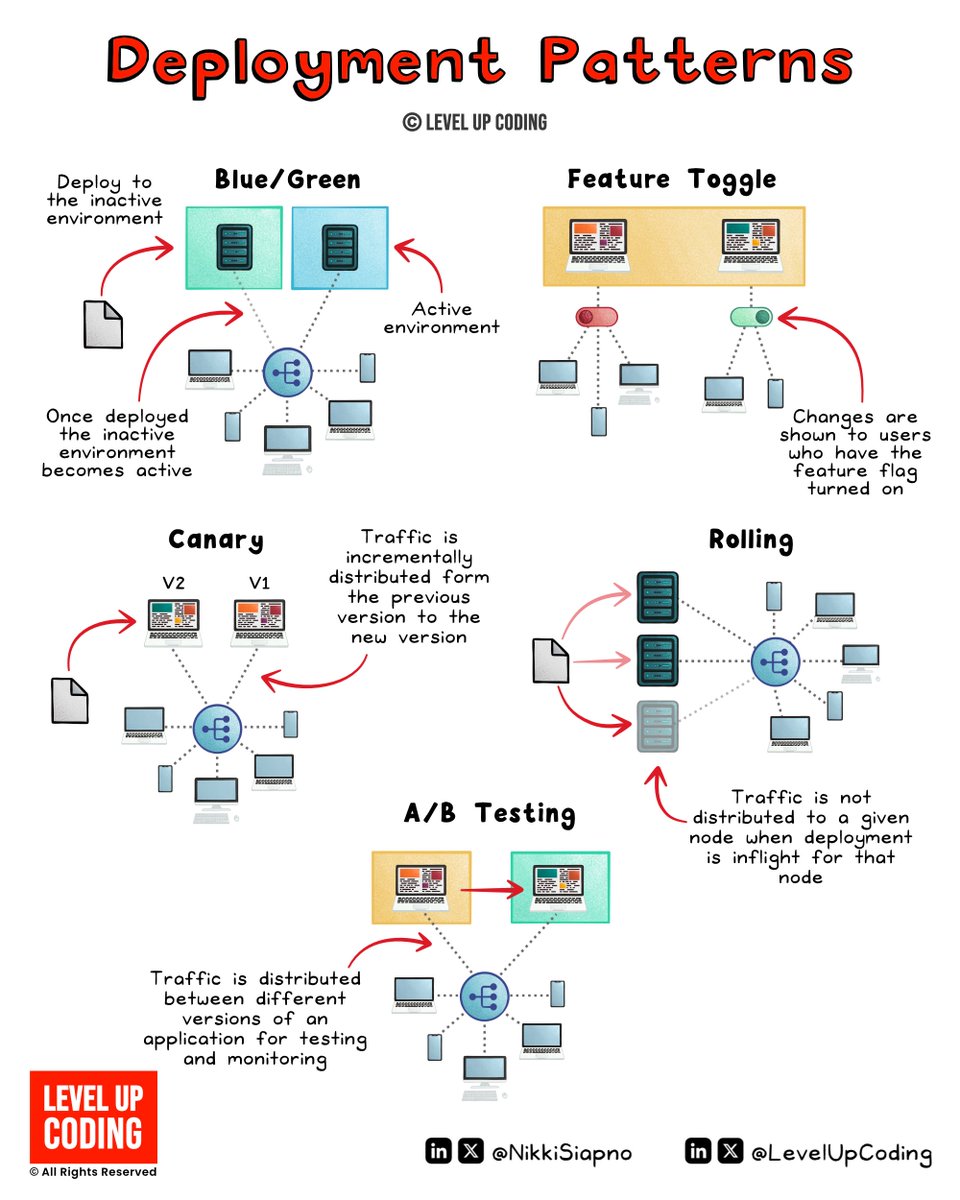
The most popular deployment strategies explained. There are many possible approaches. Here's a breakdown of five of the most popular. Each stands out for specific strengths. • Blue/Green for safety and zero downtime. • Canary for controlled, low-risk rollouts. • Rolling…
If you’re serious about learning agentic AI, here’s a practical pathway I’ve found highly effective: I’ve been diving deeper into how to build multi-agent systems. A lot of courses out there are shallow in coverage. To build real AI agents, you need more than just tool usage…

Postman and AI are no longer adjacent tools, they’ve evolved into fully integrated solutions. AI is most useful when it’s grounded in your real workflows. That’s why AI requests in collections is a big deal. Instead of running experiments in isolation, you can call models…

Things Every Developer Should Know — SQL Execution Order. A SQL query executes its statements in the following order: 1) FROM / JOIN 2) WHERE 3) GROUP BY 4) HAVING 5) SELECT 6) DISTINCT 7) ORDER BY 8) LIMIT / OFFSET 𝗧𝗵𝗲 𝘁𝗲𝗰𝗵𝗻𝗶𝗾𝘂𝗲𝘀 𝘆𝗼𝘂 𝗶𝗺𝗽𝗹𝗲𝗺𝗲𝗻𝘁 𝗮𝘁…

United States Тренды
- 1. Cowboys 58.6K posts
- 2. #WWERaw 54.4K posts
- 3. Cardinals 26.1K posts
- 4. Jerry 41.5K posts
- 5. Logan Paul 8,675 posts
- 6. Koa Peat 5,522 posts
- 7. Jacoby Brissett 3,624 posts
- 8. Kyler Murray 2,779 posts
- 9. Javonte 3,454 posts
- 10. Pickens 5,967 posts
- 11. Bland 11K posts
- 12. Cuomo 154K posts
- 13. Walter Nolen 1,269 posts
- 14. Dak Prescott 4,082 posts
- 15. Calais Campbell N/A
- 16. Eberflus 1,818 posts
- 17. Bethune 3,775 posts
- 18. #MondayNightFootball 1,260 posts
- 19. Steele 5,739 posts
- 20. Pacers 10.2K posts
Something went wrong.
Something went wrong.














































