Level Up Coding
@LevelUpCoding_
Level up your engineering & system design skills. Complex topics simplified. Thank you to our partner @getpostman who keep our content free to the community
Database Indexing Explained Most databases require some form of indexing to keep up with performance benchmarks. Searching through a database is much simpler when the data is correctly indexed, which improves the system's overall performance. A database index is a lot like…

A big moment for Postgres.
If I had to choose a database for AI agents, here’s what I’d consider: Developers love Postgres (myself included). But AI is changing what we require from databases. They now need to handle time, meaning, and memory. All in one place. Traditional systems weren’t built for…

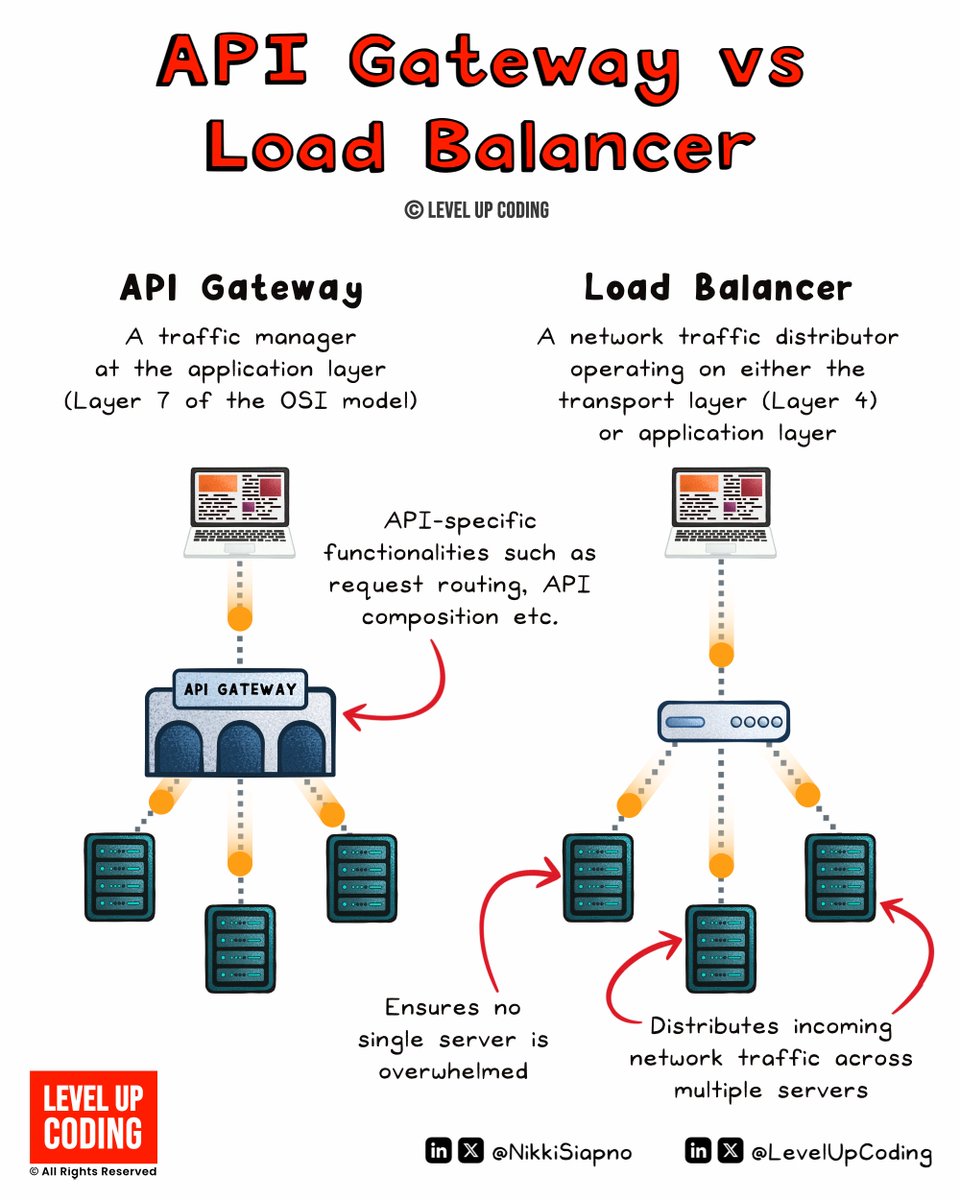
API gateway vs load balancer (explained in 2 mins or less): An 𝗔𝗣𝗜 𝗚𝗮𝘁𝗲𝘄𝗮𝘆 acts as a single entry point for clients, handling request routing, composition, and protocol translation. It simplifies client interactions with microservices and offers features like rate…
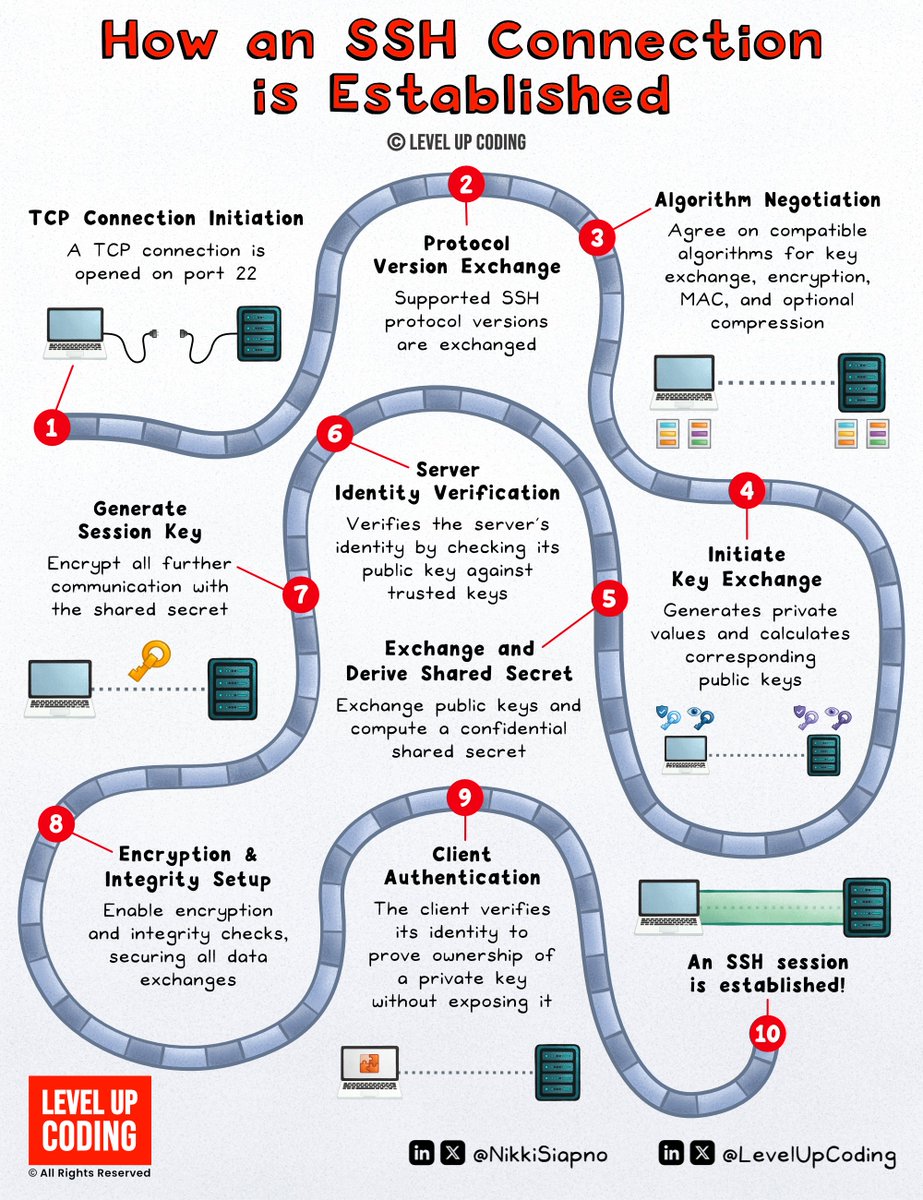
How SSH works (explained in 2 mins or less): SSH (Secure Shell) is a network protocol used to securely connect to remote machines over an unsecured network. It ensures confidentiality, integrity, and authentication for remote access, file transfers, and command execution,…
Concurrency vs parallelism (explained in 2 mins or less): Parallelism and concurrency are two terms that often create confusion. One is about managing multiple tasks at once, intermixing them to optimize resource usage. The other involves executing multiple tasks…

If I had to build auth, here's what I'd consider: Building auth properly means you need to: 1) Integrate with OAuth providers 2) Build signup, password reset, CAPTCHA flows 3) Support SAML, SSO, account recovery 4) Implement rate-limiting and 2FA 5) Detect fraud and secure…

API Gateway vs Load Balancer vs Reverse Proxy (explained in under 2 mins): • Load Balancer ↳ Distributes incoming traffic across multiple servers to ensure reliability and performance. • Reverse Proxy ↳ Sits in front of servers, forwarding requests while hiding server…

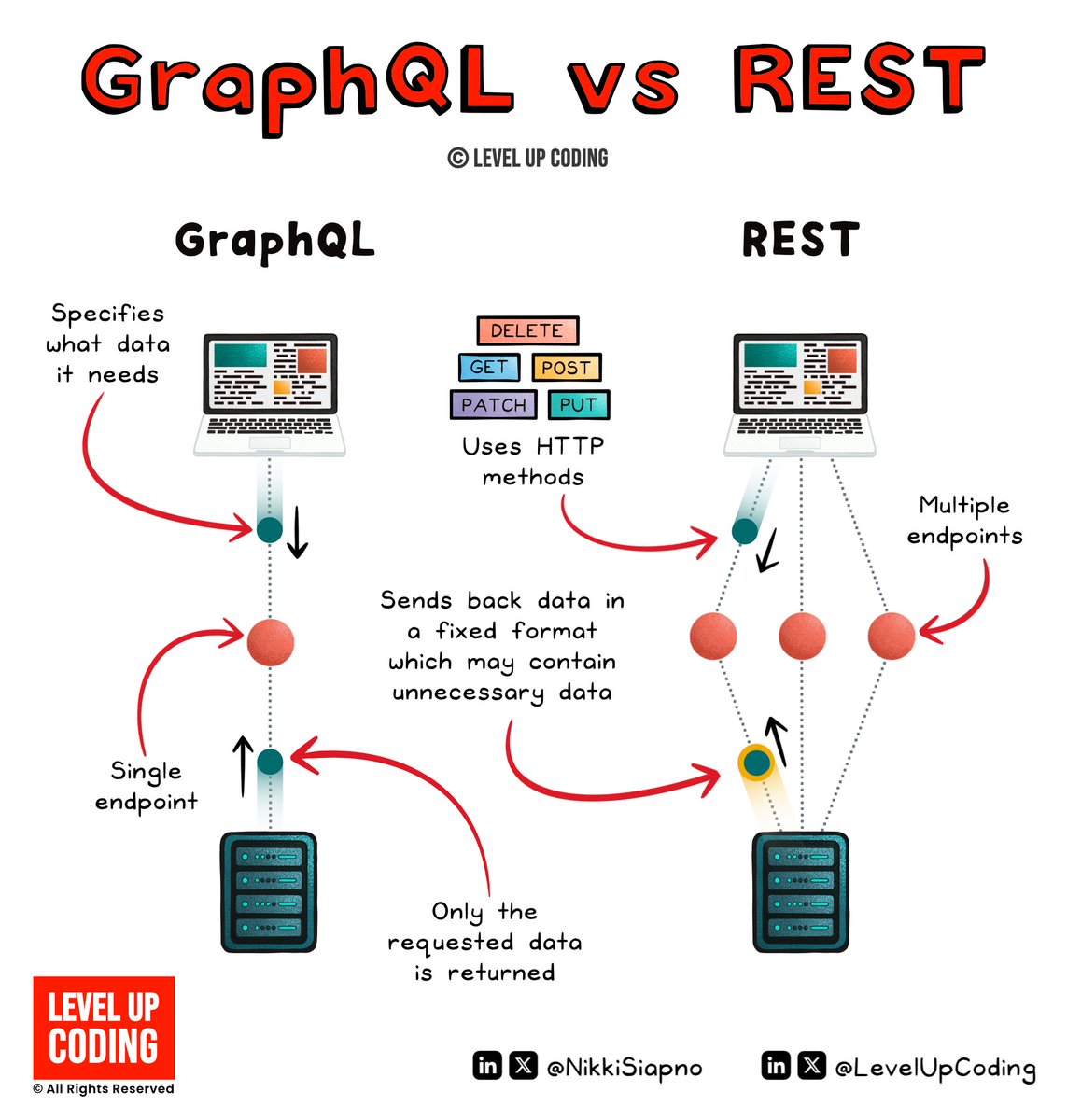
REST API vs GraphQL. Benefits and challenges of: 𝗥𝗘𝗦𝗧 🔹 Scalability Its stateless nature allows REST services to handle a large volume of requests and horizontally scale with ease. 🔹 Simplicity and flexibility Leveraging standard HTTP methods, makes it easy to…
How do we design effective and safe APIs? APIs have increasingly become the backbone of modern software. To understand some of the key principles and best practices of API design, Let's analyze a social media platform example: 🔹 𝗥𝗲𝘀𝗼𝘂𝗿𝗰𝗲 𝗻𝗮𝗺𝗶𝗻𝗴 ↳ Clarity is…

6 Software architecture patterns you should know. Choosing the right architecture isn’t about following trends. It’s about aligning with your application’s needs, your team’s expertise, and long-term scalability and maintainability. And it's one of the biggest decisions you'll…

How CI/CD pipelines work (explained in 2 mins or less): A CI/CD pipeline is an automated workflow that facilitates continuous integration (CI) and continuous delivery or deployment (CD) by managing code building, testing, and release processes. It integrates the various stages…

If I had to load balance traffic, here are 6 algorithms I'd consider: 1) Round robin 2) Weighted round robin 3) Least connections 4) IP hash 5) Random 6) Least response time There's no one-size-fits-all solution. When choosing, consider these key factors: ↳ Workload…

Myth: One model fits all. Reality: Pick Claude/GPT/Gemini/Llama for the task. AI models aren’t interchangeable. Each has different strengths in reasoning, latency, cost, and privacy. Treating them all the same leads to wasted tokens, inconsistent results, and frustrated…

8 Popular Network Protocols Explained. Network protocols operate at different layers of the OSI model. The protocols below operate at different layers, this is important to note. The OSI model is a conceptual framework that defines a networking system as a series of layers,…

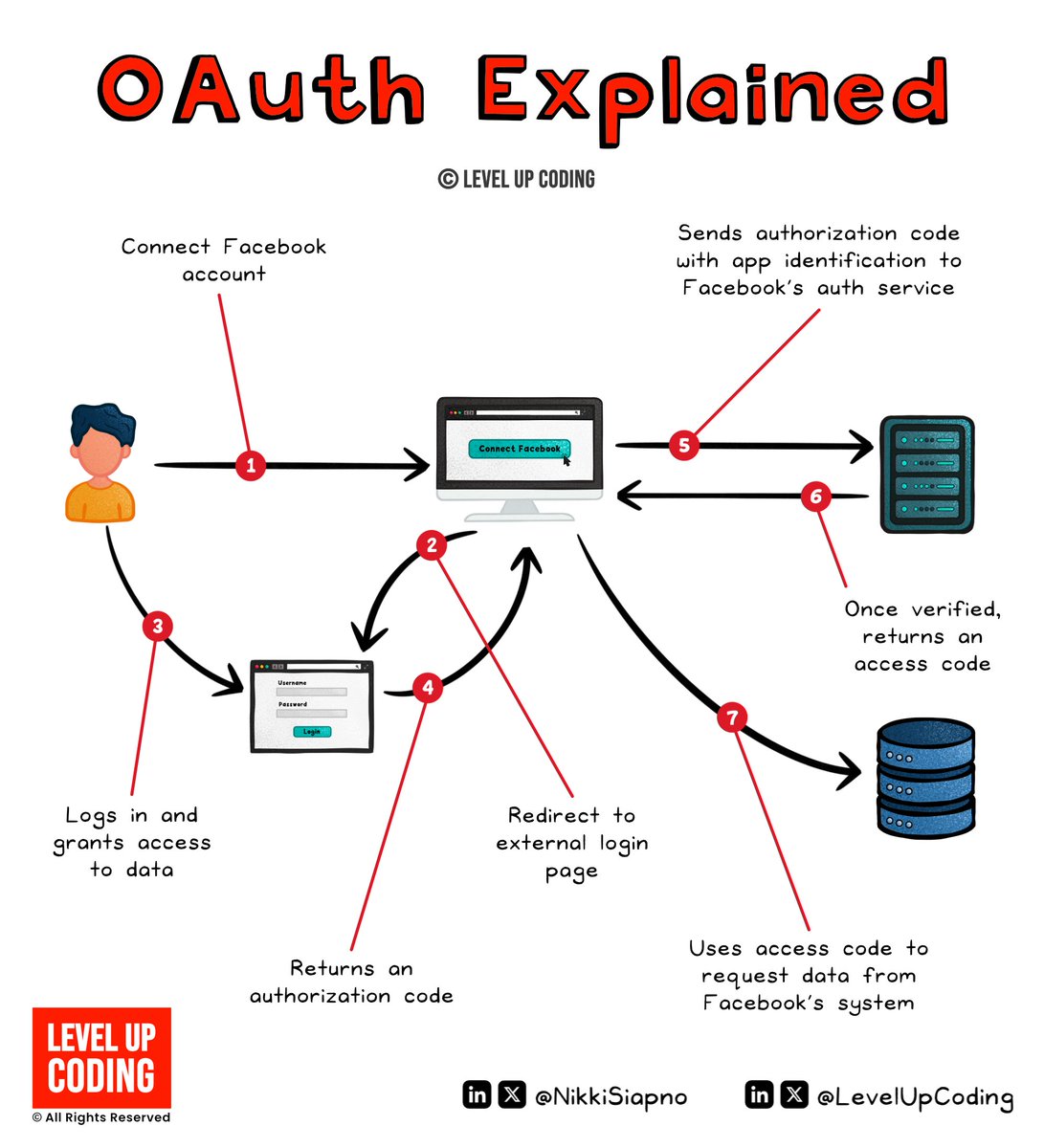
How OAuth 2.0 works (explained in 3 mins or less): It can be thought of as a digital handshake between the app, service, and user, with everyone agreeing on what is shared. It's an authorization framework that enables applications to access a user’s data on another service…
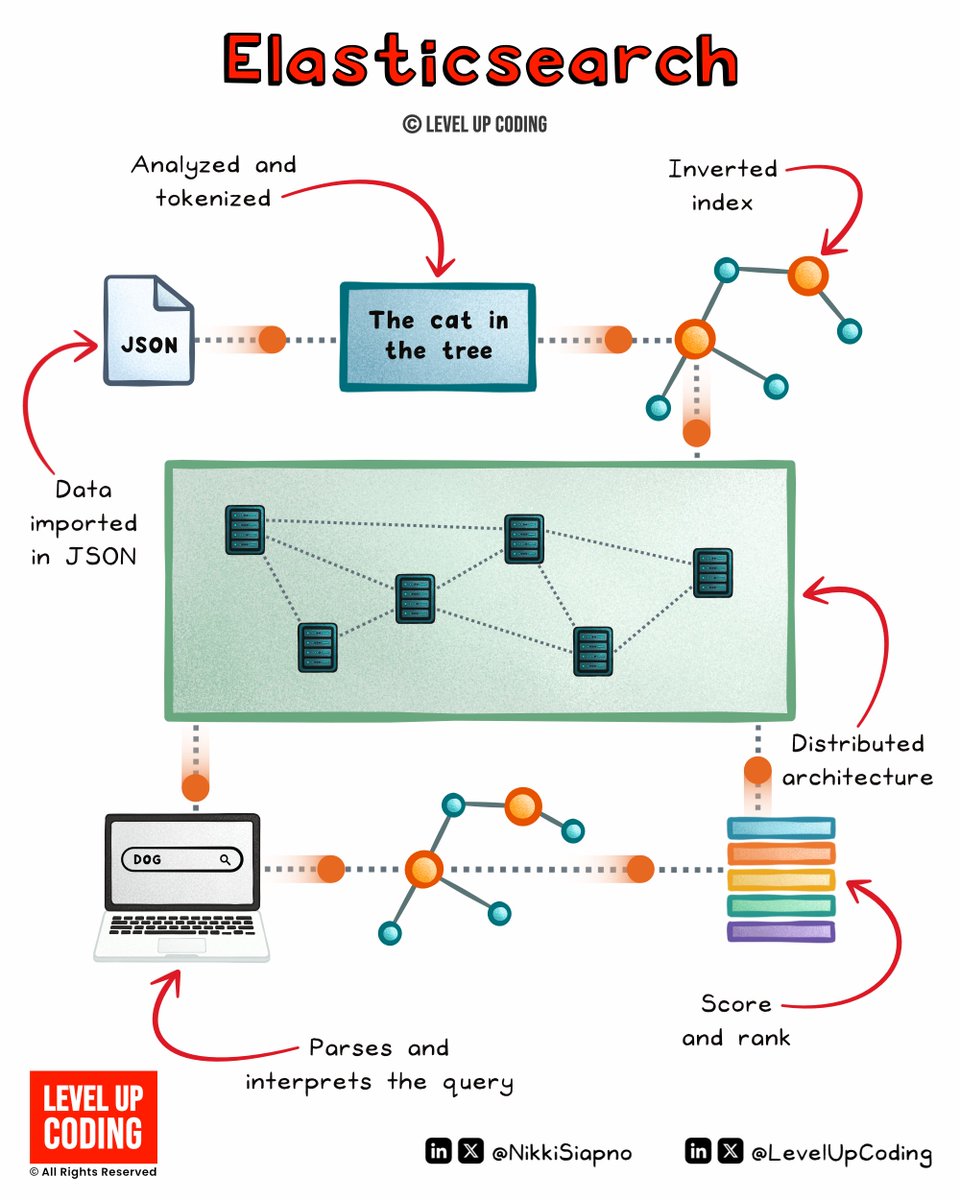
Elasticsearch Clearly Explained. Elasticsearch uses an inverted index to facilitate rapid full-text searches, enabling fast and efficient data access. It works similarly to how a book index works. Its distributed architecture not only enhances speed but also ensures high…
Things Every Developer Should Know: JSON Web Token (JWT). JWTs are one of the most widely used methods for API authentication, providing a secure, stateless and scalable way to verify clients. Here’s a simple-to-understand breakdown of how it works (step by step): 𝟭)…

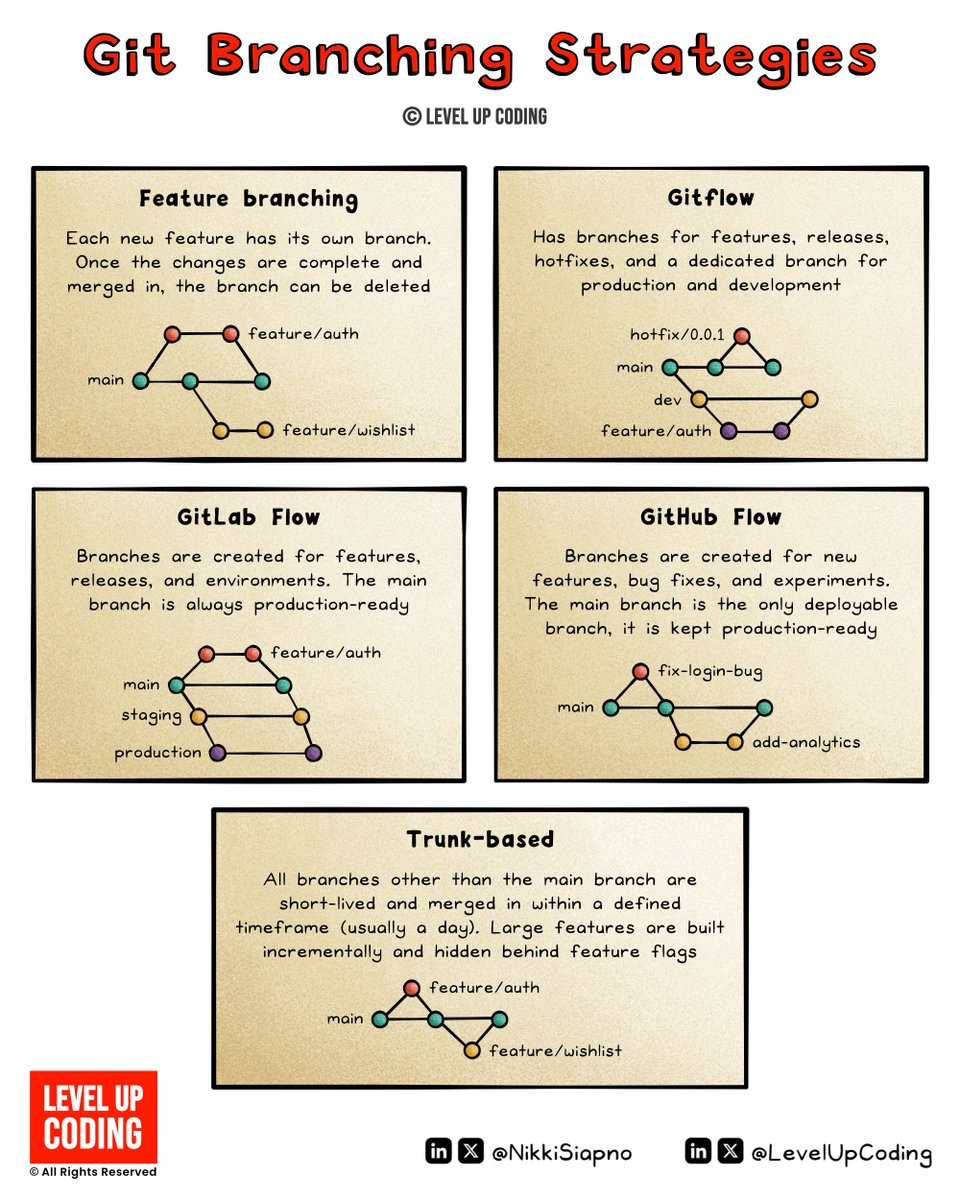
Git branching strategies clearly explained. A well-planned Git branching strategy helps coordinate the development team’s work and keeps the development process consistent. Let's take a look at some common approaches to branching: 𝗙𝗲𝗮𝘁𝘂𝗿𝗲 𝗯𝗿𝗮𝗻𝗰𝗵𝗶𝗻𝗴 is a popular…
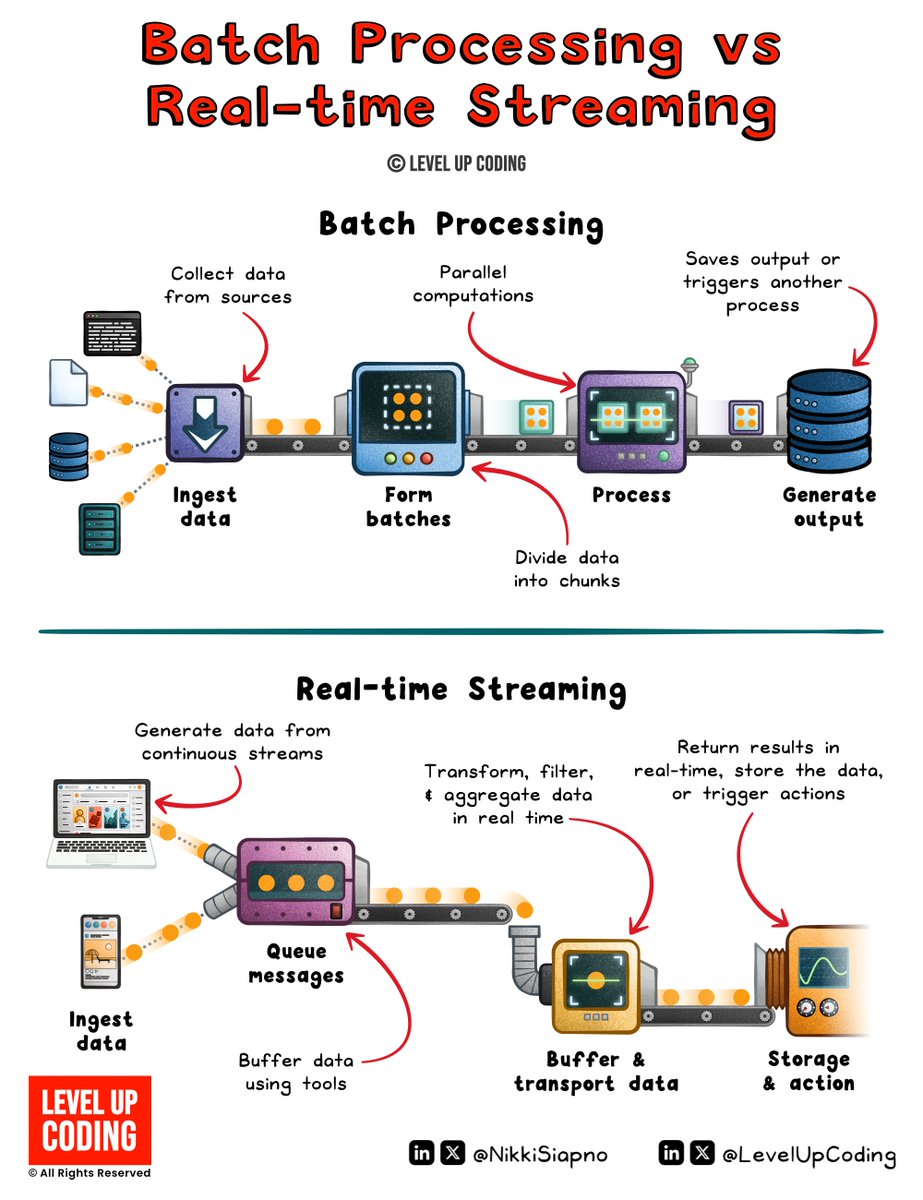
Batch Processing vs Real-time Streaming. Two approaches for your data pipelines, one goal: turning raw data into real insights. 𝗕𝗮𝘁𝗰𝗵 𝗽𝗿𝗼𝗰𝗲𝘀𝘀𝗶𝗻𝗴 handles large datasets at scheduled intervals. Think daily reports, monthly analytics, or ML model training. It’s…
How do we design secure and safe APIs? The rise in API-related security breaches highlights the necessity for robust API security. Let’s look at 12 essential tips for improving API security: 𝗥𝗮𝘁𝗲 𝗹𝗶𝗺𝗶𝘁𝗶𝗻𝗴 𝗮𝗻𝗱 𝘁𝗵𝗿𝗼𝘁𝘁𝗹𝗶𝗻𝗴 ↳ Throttling and rate limiting…

Kafka’s architecture made it fast, but not cheap. Diskless Kafka makes it both. The future of Kafka just shipped. Aiven Inkless, the first production-ready implementation of Diskless Kafka, is now GA. This is huge news for Kafka users looking for lower cost, simpler ops, and…

United States Trendler
- 1. Sedition 203K posts
- 2. Texans 21.8K posts
- 3. Lamelo 8,825 posts
- 4. Cheney 96.6K posts
- 5. Treason 109K posts
- 6. Seditious 112K posts
- 7. Commander in Chief 60K posts
- 8. Constitution 127K posts
- 9. TMNT 5,330 posts
- 10. Coast Guard 27.6K posts
- 11. UCMJ 11.6K posts
- 12. UNLAWFUL 87.1K posts
- 13. Seager 1,566 posts
- 14. Last Ronin 2,858 posts
- 15. Justin Faulk N/A
- 16. Trump and Vance 38.3K posts
- 17. First Take 49K posts
- 18. Jay Jones 2,570 posts
- 19. Dizzy 7,724 posts
- 20. Hornets 8,364 posts
Something went wrong.
Something went wrong.