
MITRE ATT&CK Defender (MAD)
@MITREattackDef
Built by MITRE's own ATT&CK® experts, MAD is a hub for defenders to train, take assessments, and get certified on their mastery in the application of ATT&CK.
你可能会喜欢
Our ATT&CK® Evaluations: Managed Services 2023 has finalized its cohort! Welcome @Bitdefender @BlackBerry @CrowdStrike @FieldEffectSoft @microsoft @PaloAltoNtwks @Secureworks @SecurityHQ @SentinelOne @Sophos @todylprotection @trendmicro Read more: hubs.ly/Q027GVfT0
This year, the FBI's Operation #MEDUSA disrupted "Snake," sophisticated malware used by #Turla, a threat operating out of Russia. See how ATT&CK® Evals recent Turla emulation is providing critical insight for #cyber defenders. #cybersecurity hubs.ly/Q025mSKJ0
Together with @MITREcorp, @MITREengenuity celebrates #CyberSecurityAwarenessMonth. We are especially proud of our #CTID, #ATTCKEvals, and #eCTF2024 teams, which all work to bring superior #cybersecurity tactics to the public. Find our more here: hubs.ly/Q02533SZ0
If you missed last week's webinar, no fear! Cat and Kate's Dark Knight discussion was covered during #BlackHat. Click below to watch Becoming a Dark Knight: #AdversaryEmulation Demonstration for #ATTCKEvals #TURLA hubs.ly/Q024hR7h0
youtube.com
YouTube
Becoming a Dark Knight: Adversary Emulation Demonstration for ATT&CK...
Starting soon: DarkKnight 2.0: Guide for #CTIReporting Webinar Join the BlackBerry and MITRE #ATT&CKEvals to talk successful #adversaryemulation (or as Batman would say, “becoming a dark knight”) through excellent #cyberthreatintelligence (CTI). hubs.ly/Q0246ZgV0

We’re spinning out our #training and credentialing program to a venture-based startup, MAD20, who can scale it and help more cyber defenders worldwide better understand @MITREattack hubs.ly/Q024vzkq0
JOIN US TOMORROW: Dark Knight 2.0: Guide for #CTI Reporting Join the BlackBerry and MITRE #ATT&CKEvals teams for a conversation on what makes CTI reporting useful and how it enables effective purple teaming. Mark your calendars. We hope to see you there! hubs.ly/Q0246_pB0

Following the release of #ATTCKEvals Enterprise #Turla emulation, dive into the history and future of ATT&CK with @MITREcorp's own Adam Pennington. "The goal is... to build a community of #cyber defenders," says Adam. See how we're doing that here: hubs.ly/Q023pBdh0
Did you miss our release of the fifth round of independent @MITREattack Evaluations: Enterprise? See how our #Turla emulation covered detection & protection capabilities (across 30 vendors). View the results: hubs.ly/Q02300wY0
Yesterday we released the fifth round of independent @MITREattack Evaluations Enterprise, where we evaluated detection & protection capabilities, highlighting results across 30 vendors. We focused on the Russia-based #Turla threat. View the results: hubs.ly/Q022__S30
We are excited to confirm that the ATT&CK® Evaluations: Enterprise 2023 has completed! This year, we emulated the #Russia based #Turla threat group. Results will be made public on Sept 20, 2023. Are you an enterprise provider looking to test your product? hubs.ly/Q021C__Q0
ATT&CK Workbench has a major update! Integrate your local knowledge with MITRE ATT&CK®. Advanced customization, improved collaboration, and streamlined workflows make it an essential tool for your organization's threat tracking. #ThreatInformeddefense hubs.ly/Q01_kj4c0
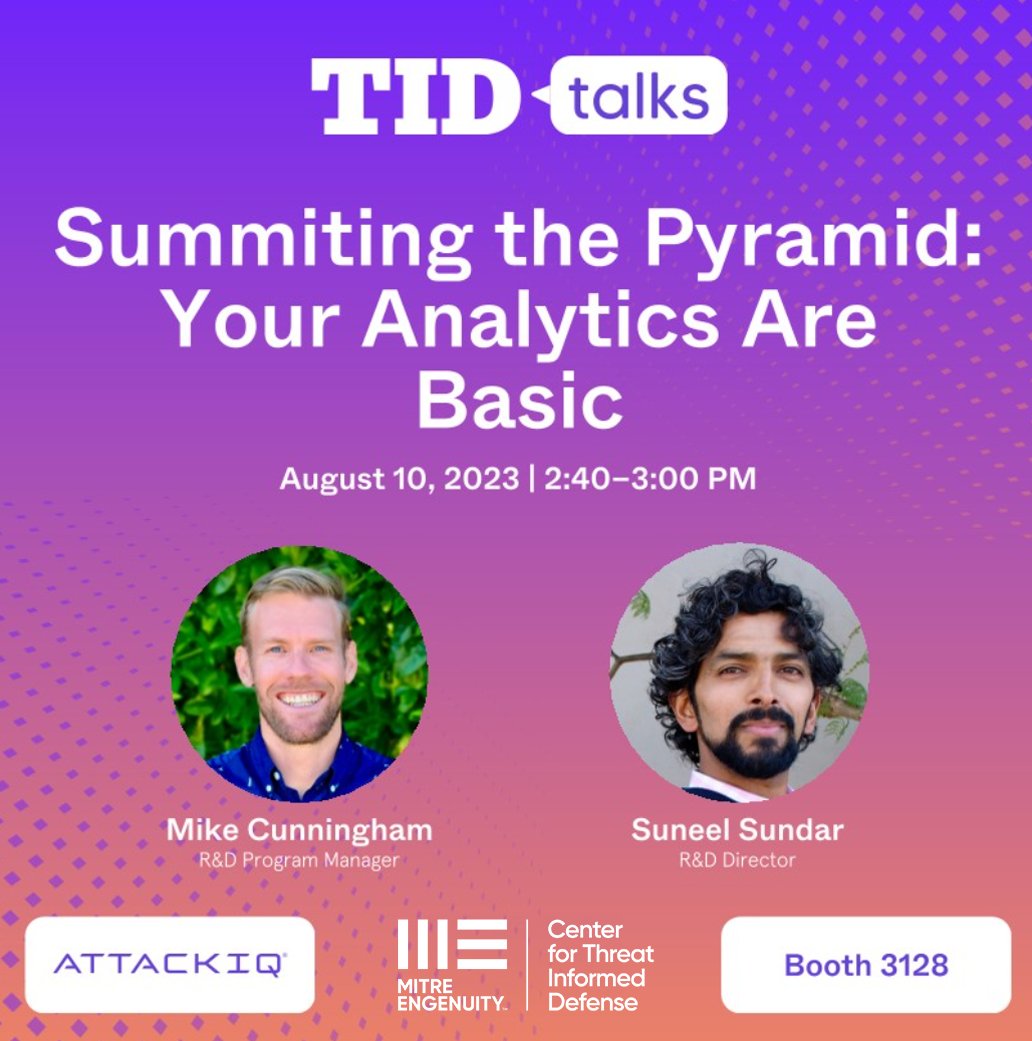
Let’s meet at Blackhat BSides and DEFCON! See MITRE Engenuity's schedule and meet us in person. hubs.ly/Q01ZNklh0 Catch us August 9 &10 with Research Partner @AttackIQ (Blackhat booth 3128) as we give 3 presentations on our open R&D #threatinformeddefense #BlackHat2023


Will you be in Las Vegas for #BSides, #BHUSA, or #defcon? Fill out this form to schedule a potential meeting with our team who will be there discussing: - ATT&CK Evaluations - Center for Threat-Informed Defense - Embedded Capture the Flag (eCTF) hubs.ly/Q01Z2Hn00

CTI reporting is critical, but challenging due to manual processes, lack of guidance, and a myriad of stakeholder types. CTI Blueprints empowers analysts to create quality, actionable reports more efficiently. hubs.ly/Q01TlVlJ0 #cybersecurity #threatintelligence #ATTACK
“When a system is hacked, there’s an anomaly that switches your day-to-day device activity. I want to find the difference between a normal day and a not-normal day.” Lex Crumpton, #TeamMITRE principal #cybersecurity engineer. #MITREattack mitre.org/impact-report#…

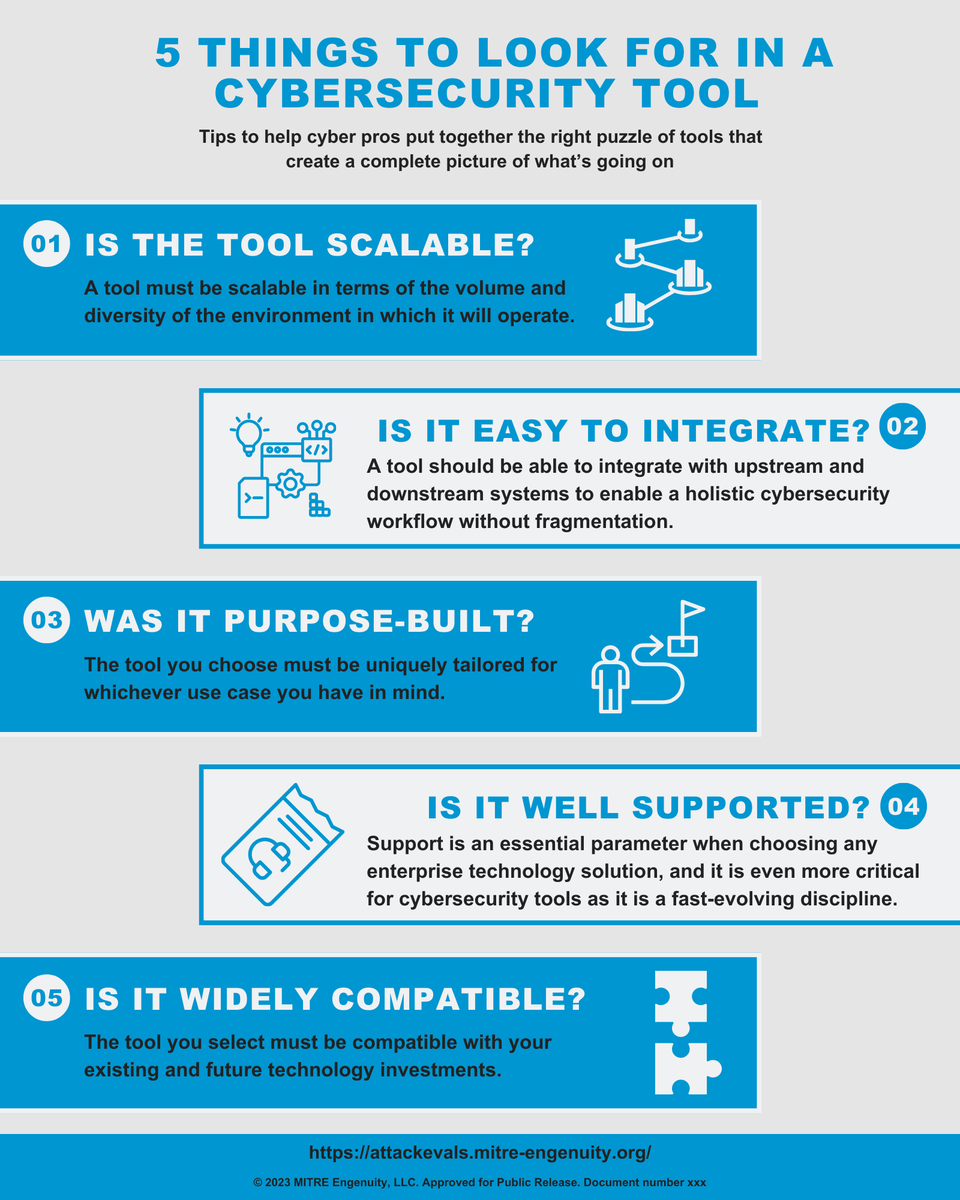
Our ATT&CK Evaluations blue team lead, Lex Crumpton, released the second blog of her blue teaming series where she outlines, "5 Things to look for in a Cybersecurity Tool." Read the blog here: hubs.ly/Q01T1nKk0
Read the update to the upcoming @MITREattack Evaluations Managed Services Round where the team discusses solving problems, improvements in round 2, and next steps: hubs.ly/Q01SVg2B0

For those that missed "Cyber Resiliency in Practice using the MITRE CREF Navigator Tool", it's now available on-demand: hubs.ly/Q01Ng9jL0
Learn from @MITREattack subject matter expert @jamieantisocial as he explores various examples of using adversary emulation to identify and deliver impactful business outcomes on Thursday, April 27, 10:15-11:40 PT at @RSAConference. hubs.ly/Q01Mh-0Y0

United States 趋势
- 1. #DWTS 19K posts
- 2. Chet 13.7K posts
- 3. Elaine 20.1K posts
- 4. Whitney 9,349 posts
- 5. Rockets 39.2K posts
- 6. Shai 17.4K posts
- 7. Robert 114K posts
- 8. #NBAonNBC 2,267 posts
- 9. #WWENXT 10.9K posts
- 10. #RHOSLC 3,442 posts
- 11. Amen Thompson 4,389 posts
- 12. Alix 3,365 posts
- 13. Michael Jordan 10.9K posts
- 14. Sengun 5,027 posts
- 15. Reed Sheppard 1,740 posts
- 16. Kevin Durant 15.4K posts
- 17. Ajay Mitchell N/A
- 18. Brad Marchand 7,177 posts
- 19. #ThunderUp 3,623 posts
- 20. Russ 33.5K posts
你可能会喜欢
-
 ATT&CK
ATT&CK
@MITREattack -
 Alexandre Borges
Alexandre Borges
@ale_sp_brazil -
 The DFIR Report
The DFIR Report
@TheDFIRReport -
 Unit 42
Unit 42
@Unit42_Intel -
 Blue Team News
Blue Team News
@blueteamsec1 -
 CyberDefenders®™
CyberDefenders®™
@CyberDefenders -
 SpecterOps
SpecterOps
@SpecterOps -
 inversecos
inversecos
@inversecos -
 SANS Cyber Defense 🧢
SANS Cyber Defense 🧢
@SANSDefense -
 Black Hills Information Security
Black Hills Information Security
@BHinfoSecurity -
 Red Canary, a Zscaler company
Red Canary, a Zscaler company
@redcanary -
 LetsDefend
LetsDefend
@LetsDefendIO -
 Mandiant (part of Google Cloud)
Mandiant (part of Google Cloud)
@Mandiant -
 Velociraptor
Velociraptor
@velocidex -
 13Cubed
13Cubed
@13CubedDFIR
Something went wrong.
Something went wrong.
























































































































