Mathilde Venault
@MathildeVenault
Security researcher at @CrowdStrike, living off cheese and adventures. Opinions are my own.
You might like
Thank you @reconmtl for this wonderful conference, what a way to discover Canada! Following up my talk, here are the slides & tool from the demo: github.com/MathildeVenaul… Blogpost on @CrowdStrike's blog coming up soon!
I often am asked for pointers on building a VM for malware analysis. I wrote a 40+ page chapter on this in my book Evasive Malware. You can download this chapter from the book on my blog for free here: evasivemalware.com/EvasiveMalware… Thanks @nostarch for allowing me to give it away 🤓
Looks like @BlueHatIL talks are online now, so here’s my talk for anyone who wanted to learn about the latest episode of KASLR and couldn’t make it: youtu.be/Dk2rLO2LC6I

youtube.com
YouTube
BlueHat IL 2025 - Yarden Shafir - Look, Ma—No Privileges! How Windows...
FYI if you’re willing to link with ntdll or dynamically resolve it there’s a ton of APIs that return TEB/PEB or leave them in one of the registers. (Don’t believe official return values. MSDN is a liar!)

Daax, being the traditional memesteroni he is, shared a cool proof-of-concept which demonstrates how to get a pointer to the Process Environment Block without using the GS and/or FS register. Look at the full thread. It's interesting.
WinDbg doesn’t have to win the battle!🧠💥 Join @MathildeVenault at SINCON 2025 for a hands-on reverse engineering workshop that helps you make sense of the Windows debugger. 📅22-23 May 2025 | 📍voco Orchard, SG 🎟️Pass: event.cybersecuritysg.com/39kL3 #SINCON2025 #WindowsDebugging



Really excited to give a talk at SINCON this year! I'll be presenting my tool github.com/CrowdStrike/dr…, that helps making the most of WinDbg in a minimum amount of time
Join @MathildeVenault at SINCON 2025 to discover how DrawMeATree helps reverse engineers visualise & decode complex systems faster. 📅22-23 May 2025 | 📍voco Orchard, SG 🎟️Pass: event.cybersecuritysg.com/39kL3 #SINCON2025



Save the date - @Blackhoodie_RE is partnering with @offensive_con this year to bring a BlackHoodie training to Berlin! Students will learn how to place compiler backdoors in innocent code. Mark your calendars for May 15th! Registration opens tomorrow, space is very limited ☺️
Windbg keyboard shortcuts docs have been updated recently. Includes both new and old bindings that were never documented: learn.microsoft.com/windows-hardwa…
I’m not saying you definitely have to go to @BlueHatIL this year, I’m just letting you know it’s free, by the beach and I’ll be there dropping kernel pointers to anyone who asks nicely

#CVE-2025-21419 2025-Feb Windows Setup Files Cleanup Windows Setup Files Cleanup Elevation of Privilege #ghidriff uncovering arbitrary delete vulnerabilities 👀 🔍 Patch introduced new function DeleteFileEx_MSRC. Not your typical function name... 🧐 A patch diffing 🧵...


Today I’m sharing a blog post on the implementation of kernel mode shadow stacks on Windows! This post covers actively debugging the Secure Kernel and also outlines why VTL 1 is relied on to help maintain the integrity of the supervisor shadow stacks! connormcgarr.github.io/km-shadow-stac…
So glad to have been part of 44con this year!
There’s a brand new conference which means you get another chance to take my Windows Internals class, this time in the US 😄 RE//verse, February 2025, Orlando Florida
Uncover how GRU bootkits and PLA supply chain implants work in Yarden Shafir’s @yarden_shafir Windows Internals course. re-verse.io/windows-24/
I'm happy to share that I'll be giving a workshop at @44CON about WinDbg, where I'll introduce a tool I've developed to make debugging much easier. Time to tame the Windows debugger together! 44con.com/44con-2024-tal…
In my new blog for @_CPResearch_ I propose a new injection technique, using the Thread Name API - check it out! 💙
In this blog we introduce Thread-Name Calling - A new process injection technique using Thread Name. We also discuss various scenarios in which this not widely-known API can be used for offense. research.checkpoint.com/2024/thread-na…
look what they took from us

Recently I was writing up a blog about Secure Kernel and NT working together to initialize Kernel CFG. I realized there were a lot of concepts in SK I was unfamiliar with. Because of this I wrote a post on one of those topics - Secure Image Objects. Enjoy! connormcgarr.github.io/secure-images/
Thanks to everyone who attended my talk! @offensive_con was an incredible experience. Couldn't make it? Don't worry- here are my slides! Recommend them to anyone wanting to learn more about Secure Boot's third-party risks. nbviewer.org/github/microso…
Ecstatic to share that my talk was accepted to Offensive Con. Excited to have an excuse to visit the city I was born in. Hope to see you there!

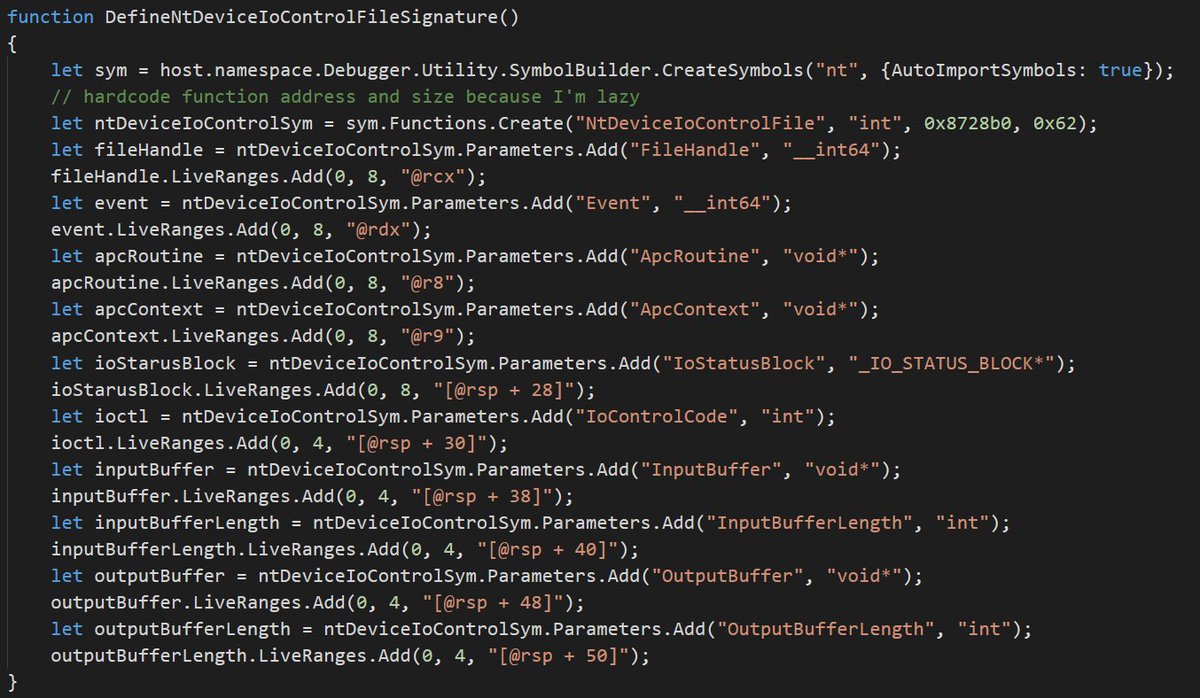
Anyone who uses WinDbg a lot should learn to use Symbol Builder (by @wmessmer). Using it here to define a function signature and combining it with FileSystem module to write log all IOCTL requests to a file.

United States Trends
- 1. Grammy 380K posts
- 2. #FliffCashFriday 1,511 posts
- 3. Dizzy 10.4K posts
- 4. James Watson 6,691 posts
- 5. Clipse 22.3K posts
- 6. #NXXT 1,135 posts
- 7. Kendrick 64.7K posts
- 8. #GOPHealthCareShutdown 9,358 posts
- 9. #FursuitFriday 12.5K posts
- 10. Thune 76K posts
- 11. Chase 89.8K posts
- 12. Orban 46.4K posts
- 13. Darryl Strawberry 1,172 posts
- 14. AOTY 23.1K posts
- 15. Carmen 48.5K posts
- 16. Alfredo 2 1,123 posts
- 17. Leon Thomas 22K posts
- 18. addison rae 25.8K posts
- 19. Laporta 13.7K posts
- 20. Bijan 2,956 posts
Something went wrong.
Something went wrong.