Nate Robb
@NateRobb
Senior Threat Enablement Operator @BishopFox
You might like
Ever feel overwhelmed by the constant firehose of newly disclosed vulnerabilities? Check out my latest blog post where I outline the methodology our Threat Enablement team at Bishop Fox uses to cut through the noise: bfx.social/3GcLIdz
bishopfox.com
Sipping from the CVE Firehose: How We Prioritize Emerging Threats for…
Prioritize high-impact CVEs fast. Learn how Bishop Fox filters noise to detect real threats and protect customer attack surfaces in real time.
Our Threat Enablement and Analysis team built a better way to cut through the noise. This is how we triage the firehose, turning chaos into action. By Senior Operator Nate Robb: bfx.social/45Ltri1
bishopfox.com
Sipping from the CVE Firehose: How We Prioritize Emerging Threats for…
Prioritize high-impact CVEs fast. Learn how Bishop Fox filters noise to detect real threats and protect customer attack surfaces in real time.
My team is hiring at @bishopfox! Come join the Adversarial Operations team for the Cosmos continuous attack surface testing platform. bishopfox.com/jobs?gh_jid=36…
bishopfox.com
Job Listing
Current job listings at Bishop Fox, the leading cyber security company. Come work with us!
Want to go #OnAFoxHunt? Find @NateRobb at Café Belle in Paris Las Vegas to grab some Bishop Fox swag! #FoxesInTheWild

We're looking for a Senior Back-End Software Engineer with strength in Golang. Interested? Know anyone? Please RT for reach 🙏 bishopfox.com/careers/?gh_ji…
bishopfox.com
Explore Careers with Bishop Fox, the Leader in Offensive Security
Looking for one-of-a-kind professional opportunities and rewarding work, coupled with the chance to grow your skills? this is the place. Explore our open…
A tale of the #security perils of using URL shorteners for sensitive info in 3 parts from @_BalthazarBratt: Read how our CAST team used shortened URLs to show a client how they could be leveraged in an #attackchain leading to full compromise. hubs.la/H0KwZwV0

While newly released #CVEs & zero days demand attention, #security teams need to focus on other easily exploitable #vulnerabilities, too. These less newsworthy issues can post a real threat to organizations. CAST Operator Nate Robb (@naterobb) explains: hubs.la/H0CDJjK0

#Symfony's secret fragments: Learn how a configuration problem leads to Remote code Execution on Symfony-based applications : ambionics.io/blog/symfony-s…
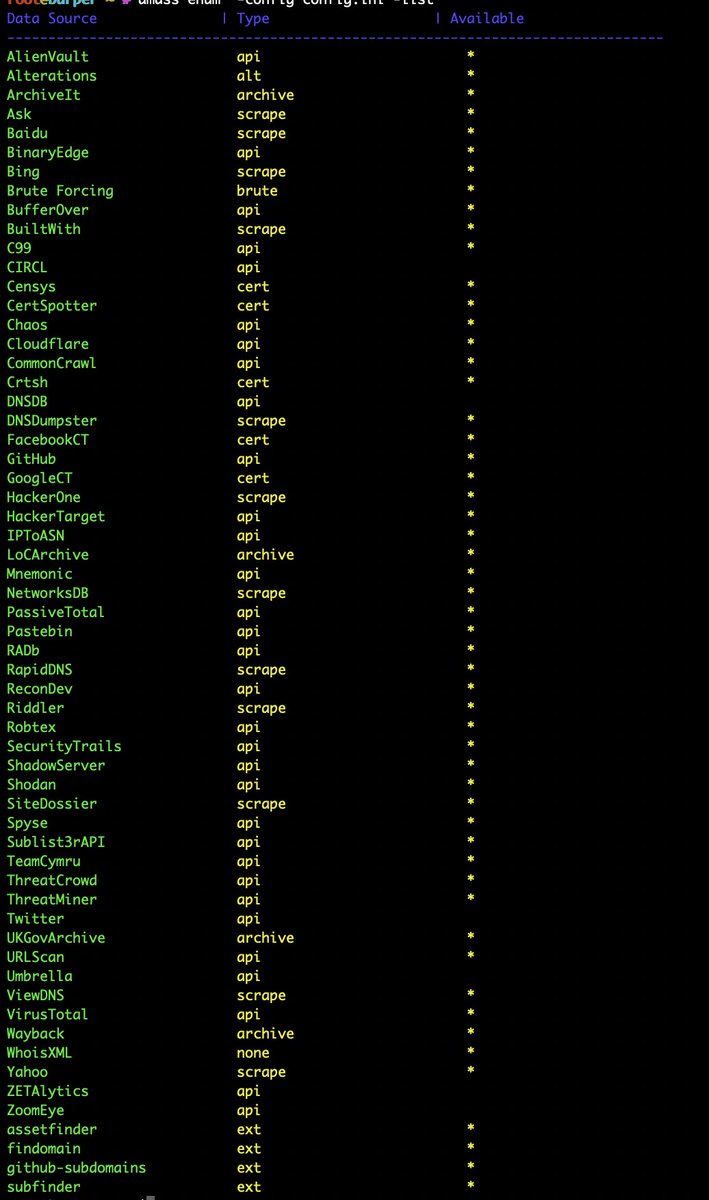
I am using the following Data sources in Amass: wonderful guide by @hahwul how to set up the API keys: hahwul.com/2020/09/23/ama…
samcurry.net/hacking-apple/ - this is one of the most comprehensive writeups I have seen from the bug bounty community, awesome work by a whole crew of people hacking on apple - lots of takeaways, worth reading thoroughly
⚡️New DNS Out-of-Band vector for MSSQL Injections in SELECT statement! Can be used for completely blind #sqli. Use fn_trace_gettable and #Burp Collaborator👍. #ptswarmTechniques

Ever wanted to use @hashcat -style masks in Burp Intruder? This extension makes it possible
Burp Brute Force like Hashcat 😀 Burp Suite Intruder Attack + Hashcat Maskprocessor. See github.com/quahac/burp-in… @hashcat @PortSwiggerRes @Burp_Suite #bruteforce
Proxyjump, the SSH option you probably never heard of #infosec #pentest #redteam medium.com/maverislabs/pr…
medium.com
Proxyjump, the SSH option you probably never heard of
Today, it is becoming more and more common for Penetration Testers, Security Researchers, Red Teams, and the like to require some sort of…
GET /admin HTTP/1.1 Host: site.com ... Access is denied GET /test HTTP/1.1 Host: X-Original-URL: /admin HTTP/1.1 200 OK
@tifkin_ and myself are happy to announce Seatbelt 1.1.0 ! Various fixes and 10 new modules means we've passed the 100 module mark. Full changelog at github.com/GhostPack/Seat…
Since it is Hacktoberfest, releasing a new research blog on hacking GitHub actions. I had a lot of fun writing this and researching on it and it is still not over 👀 sites.google.com/securifyinc.co…
I've designed labs so you can practice numerous HTTP Host header attacks including advanced password reset poisoning, host-header SSRF, and auth bypass! portswigger.net/web-security/h…
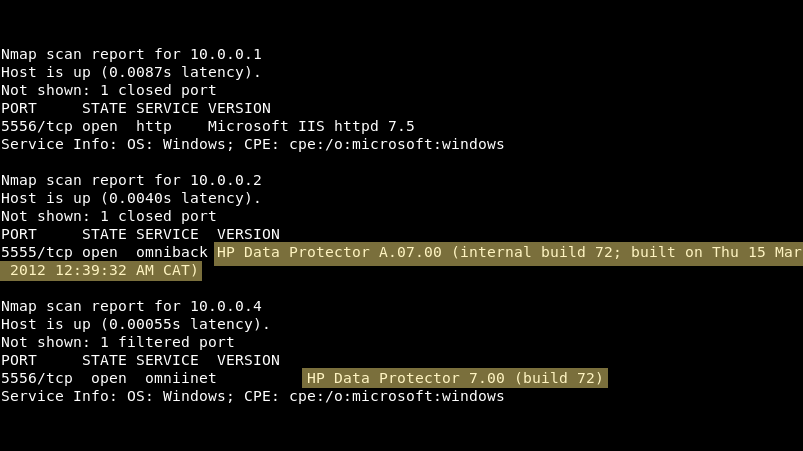
💥Easy RCE Ports Java RMI: 1090,1098,1099,4444,11099,47001,47002,10999 WebLogic: 7000-7004,8000-8003,9000-9003,9503,7070,7071 JDWP: 45000,45001 JMX: 8686,9012,50500 GlassFish: 4848 jBoss: 11111,4444,4445 Cisco Smart Install: 4786 HP Data Protector: 5555,5556 #ptswarmTechniques
New blog post by me on exploiting MFA inconsistencies on Microsoft services: blackhillsinfosec.com/exploiting-mfa… And here's a new tool (MFASweep) to find them: github.com/dafthack/MFASw…
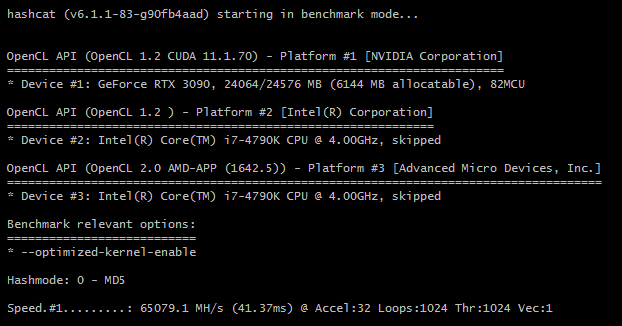
The #TITAN Killer! First @hashcat benchmarks on the @NVIDIAGeForce #RTX 3090! This is the fastest single GPU ever benchmarked! With an incredible 1.1MH/s WPA2, 121GH/s NTLM, and 96kH/s BCRYPT. Full benchmarks posted here(credit: blazer): gist.github.com/Chick3nman/e4f…
United States Trends
- 1. #FanCashDropPromotion N/A
- 2. Good Friday 55.6K posts
- 3. #FridayVibes 4,317 posts
- 4. LINGORM DIOR AT MACAU 494K posts
- 5. Happy Friyay 1,167 posts
- 6. #ElMundoConVenezuela 3,471 posts
- 7. #TheWorldWithVenezuela 3,425 posts
- 8. RED Friday 3,144 posts
- 9. #FridayFeeling 2,345 posts
- 10. Kenyon N/A
- 11. Josh Allen 46K posts
- 12. Ja Rule N/A
- 13. Sedition 349K posts
- 14. Dubai Air Show 43.4K posts
- 15. Haier EST SUPHA 157K posts
- 16. Parisian 2,079 posts
- 17. Tejas 77.9K posts
- 18. Niger 66.1K posts
- 19. Commander in Chief 90.6K posts
- 20. Traitor 126K posts
You might like
-
 Japz (h4nt3rx) 🕷️🏴☠️
Japz (h4nt3rx) 🕷️🏴☠️
@japzdivino -
 Tanto Security
Tanto Security
@TantoSecurity -
 Vipin Panchal
Vipin Panchal
@dirtycoder0124 -
 Shubham Gupta 🇮🇳
Shubham Gupta 🇮🇳
@hackerspider1 -
 BugBot
BugBot
@BugBot4 -
 Austin
Austin
@ilove2pwn_ -
 Tony
Tony
@TJ_Null -
 ramsexy
ramsexy
@plmaltais -
 Jack Halon
Jack Halon
@jack_halon -
 Ozgur Alp
Ozgur Alp
@ozgur_bbh -
 Fatin Sirat
Fatin Sirat
@fatinsourav1 -
 KNOXSS
KNOXSS
@KN0X55 -
 Rahul Maini
Rahul Maini
@iamnoooob -
 Fisher
Fisher
@Regala_ -
 animesh
animesh
@an1msh_
Something went wrong.
Something went wrong.