#vulnerabilities 搜尋結果
#AI can detect malicious chip #vulnerabilities with a 97% success rate - but will that be enough? - buff.ly/dHxXrcU #ML #hardwarevulnerabilities #semiconductors #security #supplychain

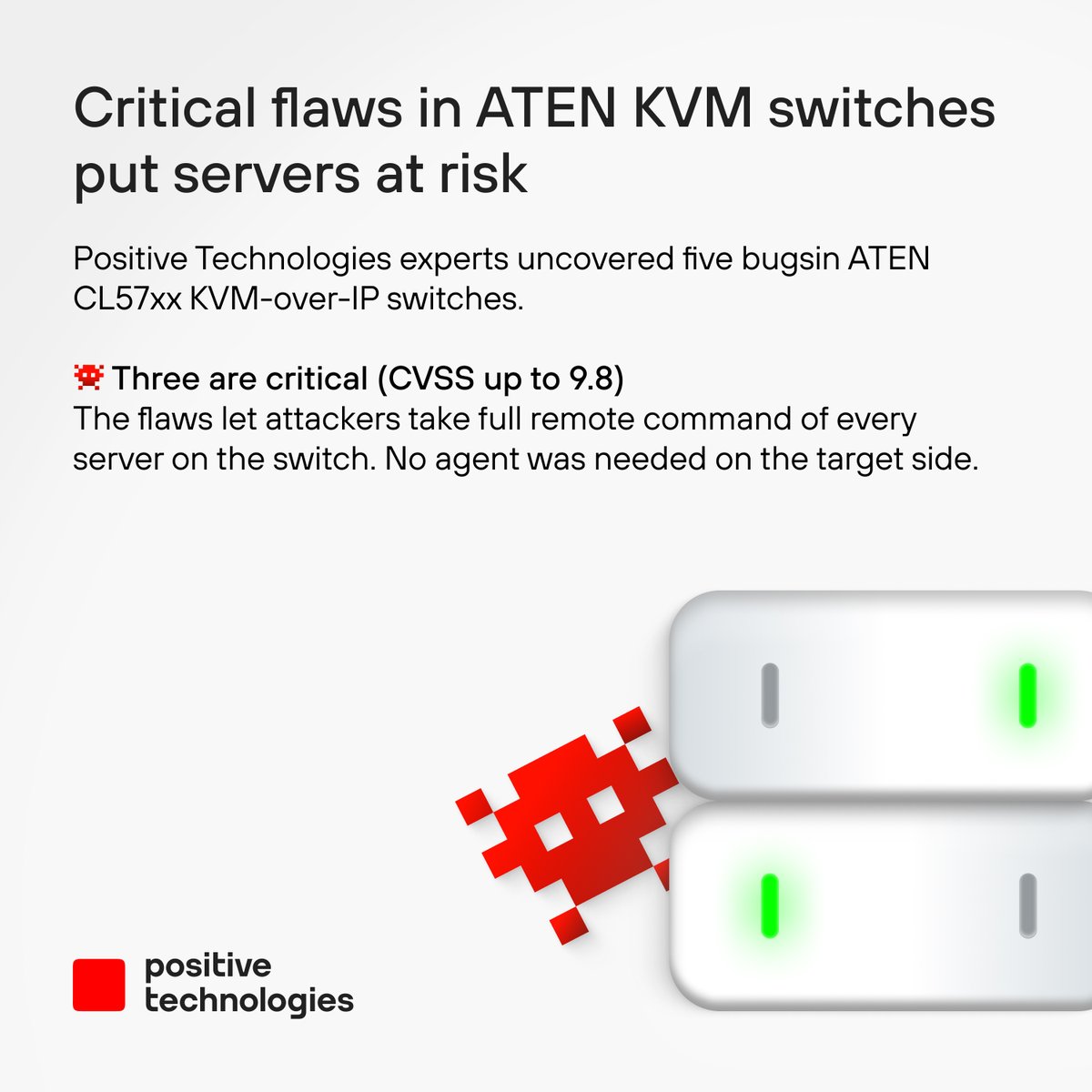
Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies



⚠️ CVE-2025-7775 🖥️ Citrix NetScaler ADC/Gateway memory overflow 💬 allows unauthenticated remote code execution on vulnerable NetScaler appliances, enabling full system takeover and lateral movement 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

Critical #Android #vulnerabilities patched - update as soon as you can: malwarebytes.com/blog/news/2025…

When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

Sophos and SonicWall Patch Critical RCE Flaws Affecting Firewalls and SMA 100 Devices dlvr.it/TMdqcm #CyberSecurity #Vulnerabilities #RCE #Firewall #SonicWall

"Let’s draw attention to places where people can act." Tyler Reguly of Fortra weighs in on where CISOs should focus during May's Patch Tuesday. Read his full take via @CSOonline: hubs.la/Q03n7n4N0 #PatchTuesday #infosec #vulnerabilities

🚨 We uncovered #security #vulnerabilities in #Windows graphics. #CVE-2025-30388 and CVE-2025-53766 are #BufferOverflows enabling #RemoteCodeExecution. CVE-2025-47984 leaks memory over the network due to an incomplete fix. 👇research.checkpoint.com/2025/drawn-to-…
✅ #PrecisionMedicine is IMPORTANT in #Lupus, but PERSONALIZED medicine, - taking into account the personal socio-economic determinants & patient #vulnerabilities-, is even MORE IMPORTANT. Check our latest PAPER with @G_O_Daniel & Zoe from @LupusEurope at: sciencedirect.com/science/articl…

A new, weaponized exploit for critical #SAP #vulnerabilities CVE-2025-31324 and CVE-2025-42999 is now public. If your systems are unpatched, they're at high risk. Act now: apply SAP security notes 3594142 and 3604119. Get the full story ➡️ bit.ly/45R1ogq #cybersecurity



Ausgrid cuts Java vulnerabilities by 99% in major security uplift... Read more: australiancybersecuritymagazine.com.au/ausgrid-cuts-j… @AzulSystems #Ausgrid #OracleJava #vulnerabilities #compliance #cybersecurity #electricity #technology

New Linux Flaws Enable Full Root Access via PAM and Udisks Across Major Distributions dlvr.it/TM1TH1 #Linux #Cybersecurity #Vulnerabilities #RootAccess #PrivilegeEscalation

⚠️ Atenție! Mai multe vulnerabilități critice afectează Google Chrome și alte browsere bazate pe Chromium. 👉 Citește avertizarea completă pe site-ul DNSC: dnsc.ro/citeste/averti… #DNSC #CyberSecurity #Vulnerabilities #UpdateNow #SigurantaOnline

The #Swagger You Forgot Is the Risk You Inherited Sometimes the biggest #vulnerabilities aren’t hidden behind layers of #obfuscation, they’re sitting in plain sight, waiting for someone curious enough to look. That’s exactly what happened during a recent grey-box web application…

BitsLab’s AI Audit Agent Discovers Multiple Vulnerabilities in Story Protocol’s Smart Contracts @0xbitslab #AI #Vulnerabilities #Web3Security chainwire.org/2025/11/04/bit…
CISA Adds Erlang SSH and Roundcube Flaws to Known Exploited Vulnerabilities Catalog dlvr.it/TLsYSL #Cybersecurity #Vulnerabilities #CISA #Erlang #SSH

Larger enterprises often operate with more complex networks, which make for a demanding task of patching #vulnerabilities. In our 2025 Cyber Risk Report, we show how Trend Vision One™ helps security teams act fast with configurable playbooks across multiple controls:⬇️…

Report reveals US energy companies overlook thousands of exposed services, including non-standard ports and IPv6 addresses, with over 5,700 CVEs, some exploited by threat groups like Silent Chollima and ExCobalt. #EnergySecurity #US #Vulnerabilities ift.tt/VXOkWyh
XXE #vulnerabilities happen when a misconfigured XML parser processes an XML input containing external entities. This exposure allows attackers to read local files or conduct SSRF attacks. Disable external entity processing in XML parsers and consider using JSON-based formats…

Ausgrid cuts Java vulnerabilities by 99% in major security uplift... Read more: australiancybersecuritymagazine.com.au/ausgrid-cuts-j… @AzulSystems #Ausgrid #OracleJava #vulnerabilities #compliance #cybersecurity #electricity #technology

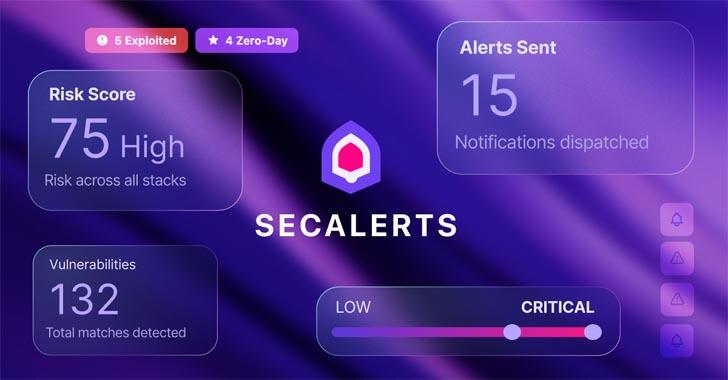
SecAlerts Cuts Through the Noise with a Smarter, Faster Way to Track #vulnerabilities thehackernews.com/2025/12/secale…
If you have a specific question about PHP security, WordPress plugin vulnerabilities, FTP security, or other cybersecurity topics, please rephrase your query clearly and I'll be happy to provide a detailed response. 🔍 #CyberSecurity #PHP #Vulnerabilities
CISA Adds Actively Exploited XSS Bug CVE-2021-26829 in OpenPLC ScadaBR to KEV thehackernews.com/2025/11/cisa-a… #CyberSecurity #Vulnerabilities #CSCIS
Legacy Python Bootstrap Scripts Create Domain-Takeover Risk in Multiple PyPI Packages thehackernews.com/2025/11/legacy… #CyberSecurity #Vulnerabilities #CSCIS
"Vulnerabilities in runc could lead to major container breakouts! 🔒 Stay informed and update ASAP! #ContainerSecurity #Vulnerabilities #Cybersecurity #Kubernetes" cncf.io/blog/2025/11/2…
Unauthenticated DoS Flaw Allows Attackers to Crash Next.js Servers with One HTTP Request gbhackers.com/unauthenticate… #CyberSecurity #Vulnerabilities #CSCIS
An anonymous security researcher has identified at least a dozen juror websites made by government software maker Tyler Technologies that can easily expose jurors' personal data. buff.ly/HfJEACc #Vulnerabilities #PrivacyBreach #DataBreach #Cybersecurity

Multiple #critical #vulnerabilities have been identified in #VMware products, with evidence of active exploitation by #ransomware groups. Organizations using these products should urgently apply the recommended patches to mitigate potential risks. 1. CISA Adds Four Known…

Pentesting 101 📚 Do you want to gain the fundamental skills to conduct a #penetrationtesting engagement but don't know where to start? This free Module is the answer for all the beginners out there! Explore practical techniques for finding #vulnerabilities and exploiting them…

Vulnerability Management Challenges in #IoT & #OT Environments - buff.ly/Jy2Wm8I #vulnerabilities #security #OTsecurity #infosec #IIoT #edge #edgecomputing
Did you know that all Social Media sites come with psychosocial #vulnerabilities that antimalware can protect you from! Check out: Trick or Tweet? The Vulnerabilities Inherent to Twitter and All Social Networks - ow.ly/PNmw50X2xoF
Critical #Android #vulnerabilities patched - update as soon as you can: malwarebytes.com/blog/news/2025…

🗨️ “As we move into 2025, security teams face a growing wave of AI-powered threats, social engineering attacks, identity exploitation, and supply chain #vulnerabilities”. In their session 'Future‑Proofing Against Cybercrime: The Six Trends Every Organisation Must Know',…

✅ #PrecisionMedicine is IMPORTANT in #Lupus, but PERSONALIZED medicine, - taking into account the personal socio-economic determinants & patient #vulnerabilities-, is even MORE IMPORTANT. Check our latest PAPER with @G_O_Daniel & Zoe from @LupusEurope at: sciencedirect.com/science/articl…

✅ Very happy to report that we have completed STEP 2 of #LUPUSALERT, asking a large international panel to triage & prioritize #lupus #vulnerabilities suggested during step 1, for inclusion in the final screening questionnaire 👍 Thanks to you all for your contributions 👏

#AI can detect malicious chip #vulnerabilities with a 97% success rate - but will that be enough? - buff.ly/dHxXrcU #ML #hardwarevulnerabilities #semiconductors #security #supplychain

Critical flaws in ATEN KVM switches gave attackers full control remotely. Thanks to the team for the catch and @Sc4rlet9 especially! Patch now and stay protected. #Cybersecurity #Vulnerabilities #PositiveTechnologies




"Let’s draw attention to places where people can act." Tyler Reguly of Fortra weighs in on where CISOs should focus during May's Patch Tuesday. Read his full take via @CSOonline: hubs.la/Q03n7n4N0 #PatchTuesday #infosec #vulnerabilities

#Nvidia #Triton #Vulnerabilities Pose Big Risk to #AI Models - ift.tt/9QulTS4 #genAI #IT #security #infosec #GPUs #AIsecurity #ML

Sophos and SonicWall Patch Critical RCE Flaws Affecting Firewalls and SMA 100 Devices dlvr.it/TMdqcm #CyberSecurity #Vulnerabilities #RCE #Firewall #SonicWall

When #Vulnerabilities Pile Up - Finding the Real Value in #Security #Assessments Every year, a familiar pattern emerges. An organization invests in #penetration #testing. The report comes back. Dozens, sometimes hundreds, of findings. Fast forward 12 months... the same…

⚠️ CVE-2025-7775 🖥️ Citrix NetScaler ADC/Gateway memory overflow 💬 allows unauthenticated remote code execution on vulnerable NetScaler appliances, enabling full system takeover and lateral movement 🔗 cve.mitre.org/cgi-bin/cvenam… #ransomNews #vulnerabilities #security #CVE

A new, weaponized exploit for critical #SAP #vulnerabilities CVE-2025-31324 and CVE-2025-42999 is now public. If your systems are unpatched, they're at high risk. Act now: apply SAP security notes 3594142 and 3604119. Get the full story ➡️ bit.ly/45R1ogq #cybersecurity



Just picked up my holiday photos! 50% landscapes, 50% Grype being @GrypeProject 👽📷 #vulnerabilities #security #family


Something went wrong.
Something went wrong.
United States Trends
- 1. Chris Paul 7,439 posts
- 2. Pat Spencer 2,667 posts
- 3. Kerr 5,579 posts
- 4. Podz 3,293 posts
- 5. Shai 15.6K posts
- 6. Jimmy Butler 2,647 posts
- 7. Seth Curry 4,920 posts
- 8. The Clippers 10.3K posts
- 9. Hield 1,586 posts
- 10. Carter Hart 4,111 posts
- 11. #DubNation 1,428 posts
- 12. Mark Pope 1,966 posts
- 13. #SeanCombsTheReckoning 5,109 posts
- 14. Lawrence Frank N/A
- 15. #AreYouSure2 132K posts
- 16. Kuminga 1,492 posts
- 17. Derek Dixon 1,306 posts
- 18. Brandy 8,294 posts
- 19. Elden Campbell N/A
- 20. Connor Bedard 2,450 posts