
Ragnar Security
@RagnarSecurity
Shielding you from security vulnerabilities!
You might like
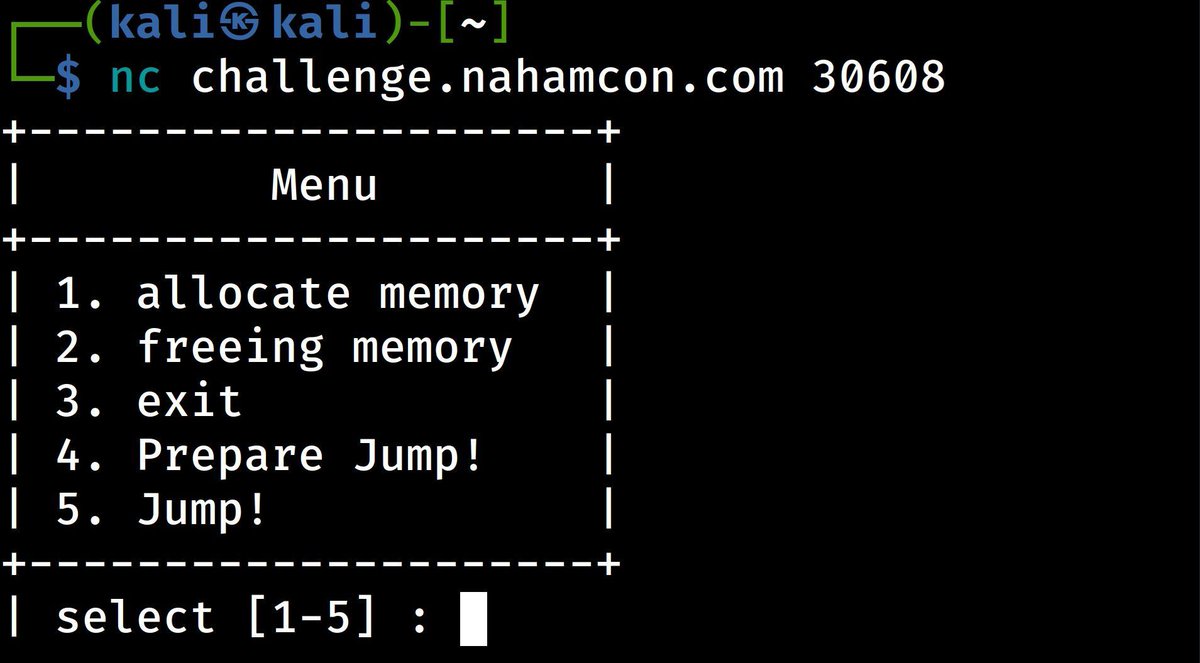
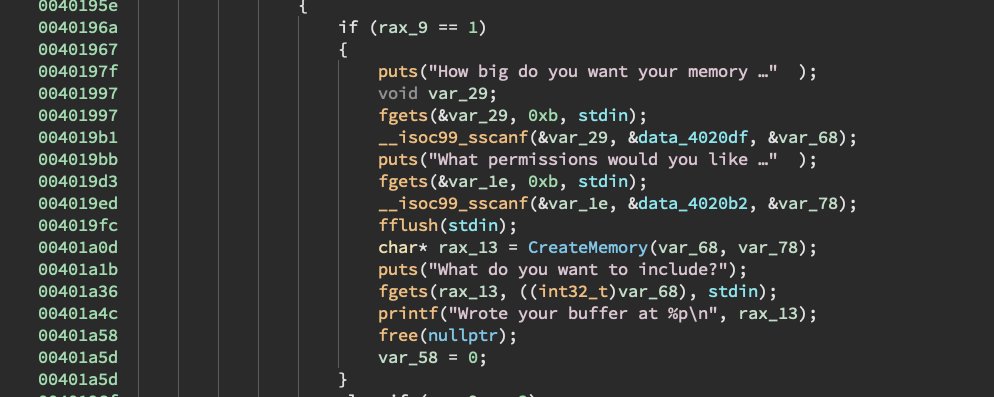
But we could never forget about those Binary Exploitation buffs! In fact we've got something fun for you: @RagnarSecurity 's latest predicament: "So Much Cache!" Pwn this challenge and more at #NahamCon2024 CTF jh.live/nahamcon-ctf (5/23-5/25)
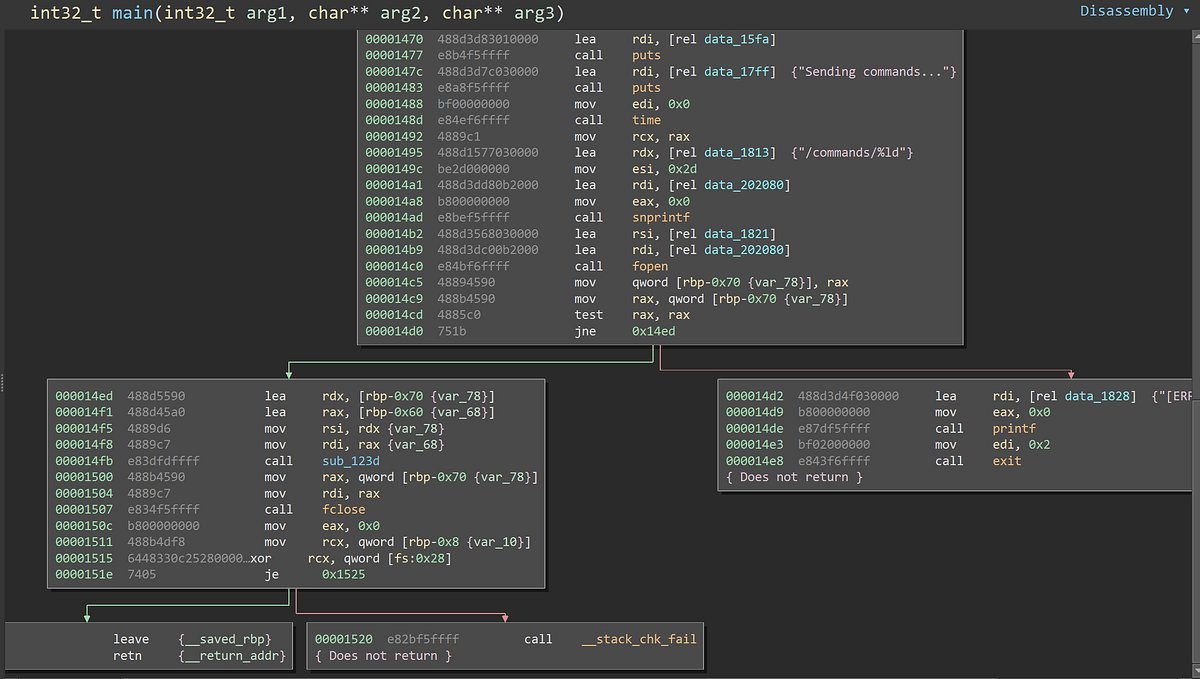
Leveraging Netsh Helper DLLs for living-off-the-land code execution (and optional persistence), staged with shellcode for a Sliver C2 session! Showcases built with both C++ and Nim... and boy I love getting practice with Nim 👑 youtu.be/lMihdys4jw8

WittsEnd2 created a new article about one of the CTF challenges he wrote. It is a basic code injection challenge using ptrace! ragnarsecurity.medium.com/limited-resour…
It's that magical time of year again - UMDCTF 2022!!! Starting March 4th check out some incredible challs from the folks at UMDCSEC! Visit umdctf.io for more details <3
WittsEnd2 wrote an article comparing vulnerabilities in Rust and C. Go check it out! ragnarsecurity.medium.com/rust-vs-c-how-…
How to make money and be successful in #infosec and #bugbounty without any knowledge and skills of hacking, coding. #bugbountytips #bugbountytip A thread. 🧵👇
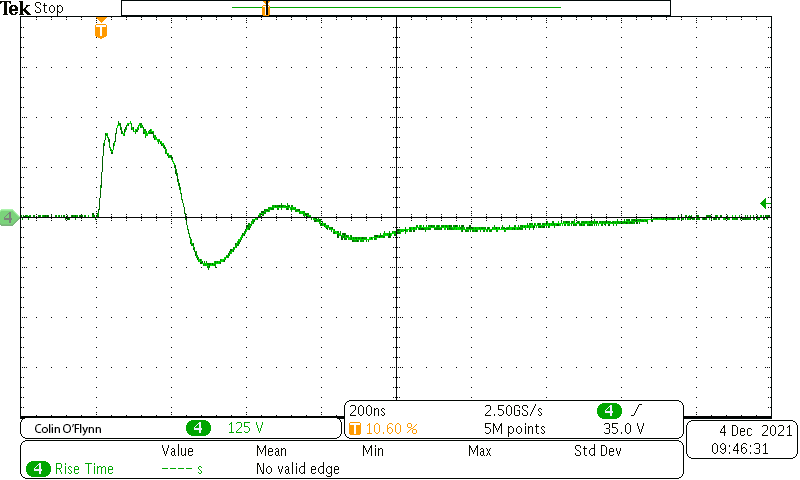
Something to finish off 2021 with a bang for you: It's now possible to build a (mostly safe) #EMFI tool for ~$50. Details are in the new 'PicoEMP' repository, including gerbers + design decision notes. Inspired from my @hackaday remoticon talk! github.com/newaetech/chip…


ShmooCon 2022 postponed to March 24-26. More information here: shmoocon.org/2021/12/30/shm…
WittsEnd2 is writing a series about developing baremetal firmware. He just completed his first article. You can read it here: ragnarsecurity.medium.com/writing-bareme…
I completed the Kerberoasting on an Open Fire challenge! holidayhackchallenge.com Don't miss out on SANS #HolidayHack x @KringleCon holidayhackchallenge.com
Interesting writeups from @cor_ctf challenge writers Will's Root and D3v17 on their challenges Fire of Salvation and Wall of Perdition (Linux Kernel Pwn CTF Challenges): willsroot.io/2021/08/corctf… syst3mfailure.io/wall-of-perdit…
Ever wanted to know how the kernel security feature Seccomp works? WittsEnd2 will teach you and go through a CTF challenge involving Seccomp! link.medium.com/LDKEzneI5ib
Interesting writeup from the Hack-A-Sat 2 Qualifiers CTF. This writeup is for the challenge Mars or Bust, which is an embedded reverse engineering challenge: gist.github.com/ZetaTwo/d437be…
WittsEnd2 just posted part 3 of his reverse engineering bare-metal tutorial series. This tutorial goes into reading ARM assembly code and exploiting bare-metal firmware vulnerabilities. ragnarsecurity.medium.com/reverse-engine…
WittsEnd2 just posted Part 2 of his Bare-Metal Firmware Reverse Engineering series: ragnarsecurity.medium.com/reverse-engine…
WittsEnd2 just published a new article related to reverse engineering bare-metal kernel images using QEMU. Click here to read: link.medium.com/uZWZOnQkpfb
New reverse engineering CTF Challenge walkthrough from WittsEnd2 - Babymix from Dicegang ctf: youtube.com/watch?v=uJQoQr…

youtube.com
YouTube
DiceGang CTF - BabyMix Reverse Engineering Challenge Walkthrough
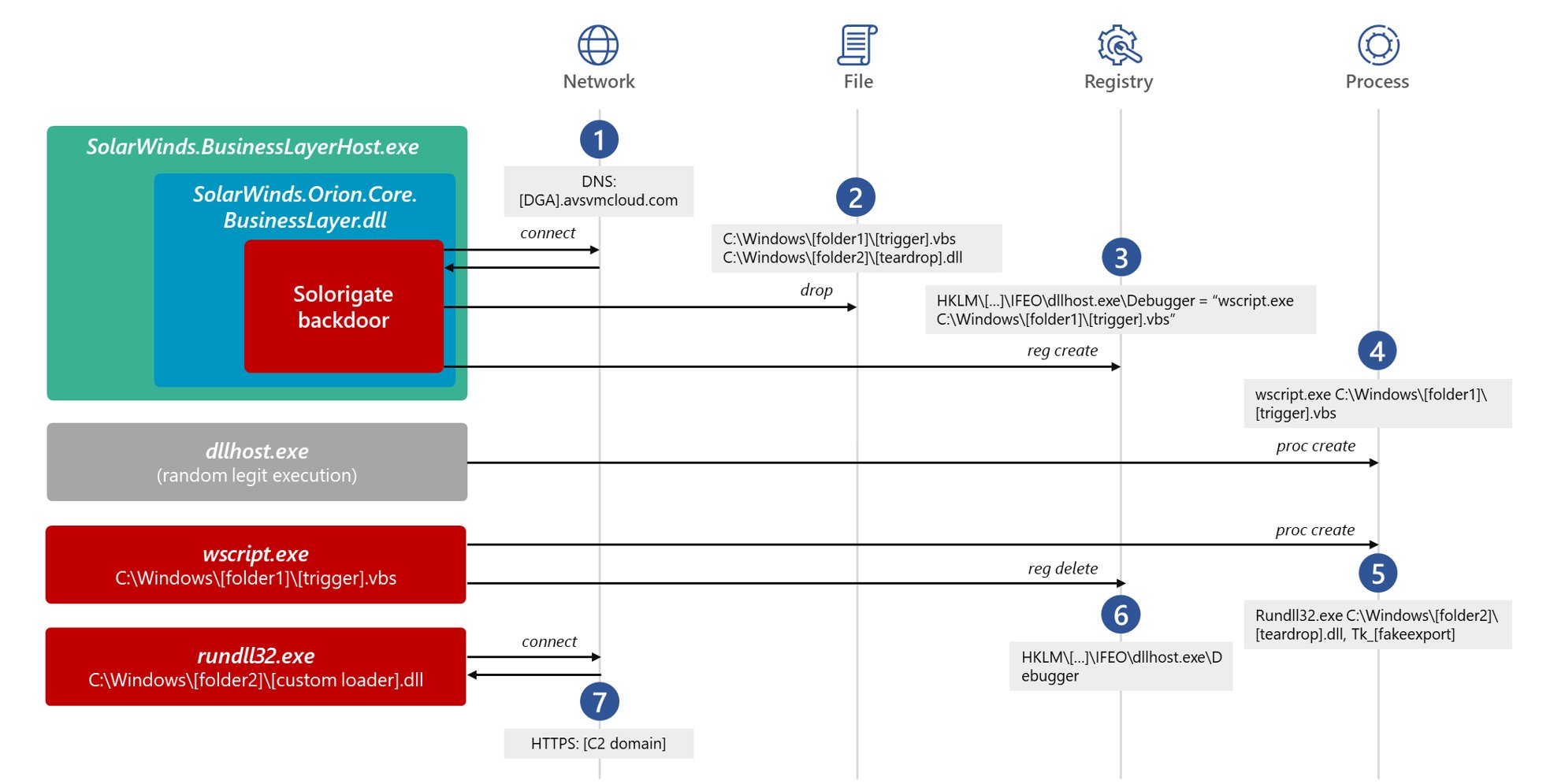
The attackers behind Solorigate detached the execution of the 2nd-stage payload, a custom Cobalt Strike loader, from the compromised binary’s process by creating an IFEO Debugger registry value for dllhost.exe and waiting for it run. ICYMI, our analysis: msft.it/6013psLtW
WittsEnd2 created a blog post about why you should start learning Reverse Engineering: ragnarsecurity.medium.com/why-you-should…
United States Trends
- 1. Jameis 31.7K posts
- 2. Chiefs 58.1K posts
- 3. Giants 68.1K posts
- 4. JJ McCarthy 5,614 posts
- 5. Lions 46.5K posts
- 6. Colts 25.8K posts
- 7. Vikings 27.1K posts
- 8. Mahomes 15.1K posts
- 9. Steelers 41.2K posts
- 10. Ravens 20.8K posts
- 11. Bears 54.1K posts
- 12. Gibbs 6,538 posts
- 13. Tony Romo 2,756 posts
- 14. Bengals 19.1K posts
- 15. Campbell 15.8K posts
- 16. #GoPackGo 4,828 posts
- 17. Daniel Jones 2,655 posts
- 18. Caleb 31K posts
- 19. #Skol 2,844 posts
- 20. Tomlin 4,335 posts
You might like
-
 RussianPanda 🐼 🇺🇦
RussianPanda 🐼 🇺🇦
@RussianPanda9xx -
 Vector 35
Vector 35
@vector35 -
 ptr-yudai
ptr-yudai
@ptrYudai -
 ringzerø.training && @[email protected]
ringzerø.training && @[email protected]
@_ringzer0 -
 EMBA Firmware Analyzer
EMBA Firmware Analyzer
@securefirmware -
 Jiří Vinopal
Jiří Vinopal
@vinopaljiri -
 FuzzingLabs
FuzzingLabs
@FuzzingLabs -
 rev.ng
rev.ng
@_revng -
 🆆 🅷 🅸 🅳 -𝙒𝙚 𝙃𝙖𝙘𝙠 𝙄𝙣 𝘿𝙞𝙨𝙜𝙪𝙞𝙨𝙚
🆆 🅷 🅸 🅳 -𝙒𝙚 𝙃𝙖𝙘𝙠 𝙄𝙣 𝘿𝙞𝙨𝙜𝙪𝙞𝙨𝙚
@whid_ninja -
 Rizin
Rizin
@rizinorg -
 Clay
Clay
@0xClayHax -
 eShard
eShard
@eshard -
 [email protected]
[email protected]
@BehroozParhami -
 Phan Thanh Duy 🇻🇳
Phan Thanh Duy 🇻🇳
@PTDuy -
 Joshua Pearce
Joshua Pearce
@ProfPearce
Something went wrong.
Something went wrong.







































































































![hh86_'s profile picture. hh86.msc [at] gmail](https://pbs.twimg.com/profile_images/1256682516766998530/1uFM2Vll.jpg)












