Nathan D.
@Sec_Distilled
Community | Leadership | Cyber | Infosec | CISSP, PMP - I love meeting new people and talking about cyber | Opinions are my own
You might like
My SCCM BloodHound OpenGraph collector, ConfigManBearPig, is finally ready to share! It can enumerate all of the relay TAKEOVERs and a few CRED and ELEVATE techniques from Misconfiguration Manager with just a domain account. Let me know what you find! specterops.io/blog/2026/01/1…
My On Detection series continues. In part 14 I look at a “special” subset of operations that require a bit more detail to facilitate accurate detection. While this topic is more focused on the model, I finish the post by analyzing one of the variants of PoolParty Injection!…
In this week’s #BloodHoundBasics, learn how to quickly audit kerberoastable accounts in Active Directory using one of BloodHound’s included cypher queries. Check out the full tutorial from Carlo Alcantara 👉 ghst.ly/4c2alDW
I've released another post in my On Detection series. This edition builds on the previous post where I introduced "execution modalities." Here we look at how modalities, like behavior, can impact detection efficacy and how we can deal with that fact. posts.specterops.io/part-13-415c4d…
I'm excited to get my latest blog post about purple team efficacy out into the wild! You may feel like the point I'm making is obvious, but I'd argue that a lot of concepts seem obvious only when you're faced with an argument on it's behalf. posts.specterops.io/to-infinity-an…
#BloodHoundBasics is back! This week we are talking ➡️ Risk Filtering ⬅️ Got a lot of AD domains & Azure tenants? BloodHound Enterprise allows you to filter environments based on risk level so you can focus remediation efforts where they have the most impact. s/o @sec_distilled
My On Detection series is back! In this edition I explore how the same behavior (operation chain) can be implemented using several different execution modalities and the implications of this for detection engineers. posts.specterops.io/behavior-vs-ex…
It’s Friday and we’re bringing back the #BloodHoundBasics series! @KayDaskalakis kicks us off with 🔥Attack Path Edge Filtering🔥 Stay laser-focused on specific #AttackPaths and discover new edges you didn't even know existed! 👀✨
Last year I shared how to convert BloodHound JSON to PowerShell objects. Here's a proper function: ConvertFrom-BHJSON gist.github.com/martinsohn/1f3… Examples in this new 🧵
Exporting nodes in #BloodHoundCE and #BloodHoundEnterprise is easy - click the Export button and select JSON ⬇️ JSON is nice but I prefer PowerShell objects, so I simply run... 1/2

New to Cypher queries in BloodHound Enterprise? Do you enjoy references to Lord of the Rings? Want both in one place? This one's for you: posts.specterops.io/cypher-queries…
Open-ended Cypher searches are available in BHE! Learn from @sec_distilled how BHE customers have leveraged Cypher for additional value realization in both understanding Attack Paths & contextualizing their enterprise environments for greater security. ghst.ly/48jDjxL
You don't want to miss @_wald0 & @Jonas_B_K as they take the stage at #SOCON2024 to share how BHE simplifies the discovery, analysis, & execution of attack paths traversing AD CS objects. Register today & get 50% off. This special rate ends this Friday! specterops.io/so-con

Part 11 of the On Detection series is now available! This post is a bit more theoretical than some of the previous articles, but I think it helps provide an important conceptual foundation that we will build on over the next couple of posts. posts.specterops.io/on-detection-t…
How can defenders reclaim control over the domain after discovering a #cyberattack where the adversary has domain persistence? ⚔️ @synth_nic0 & @Praga_Prag share how adversaries gain and sustain access within a domain as well as recovery strategies. ghst.ly/473jauU
💡 WHAT IS PURPLE TEAMING AT SPECTEROPS? SpecterOps recently introduced our Purple Team service offering, but what is it? We define it as "the evaluation of security control efficacy through atomic testing using deliberately selected test cases." ghst.ly/3EUVRHB
specterops.io
New Purple Team Assessments Service | SpecterOps News
SpecterOps announced new Purple Team Assessment Services, a two-week assessment that evaluates how well an organization’s security controls can detect and prevent common attack techniques...
.@MITREengenuity's Submitting the Pyramid project created a methodology that scores analytics against the #pyramidofpain & scrutinizes the components within the analytic. We are proud to have contributed our Capability Abstraction analysis to this project. ghst.ly/3Lo66rq
Stay up-to-date on #crypto domains. Crypto Census provides a fully open-source, self-maintaining, crypto domain indicator resource. @sou_predictable shares an overview of the tool in our latest blog post: ghst.ly/44pOdzi

I've finally added the next article in my On Detection series. I discussed Tool Graphs which are new way that we've created to represent a malware sample's functionality. The post demonstrates some of the use cases and explains how the graph is formed. posts.specterops.io/on-detection-f…
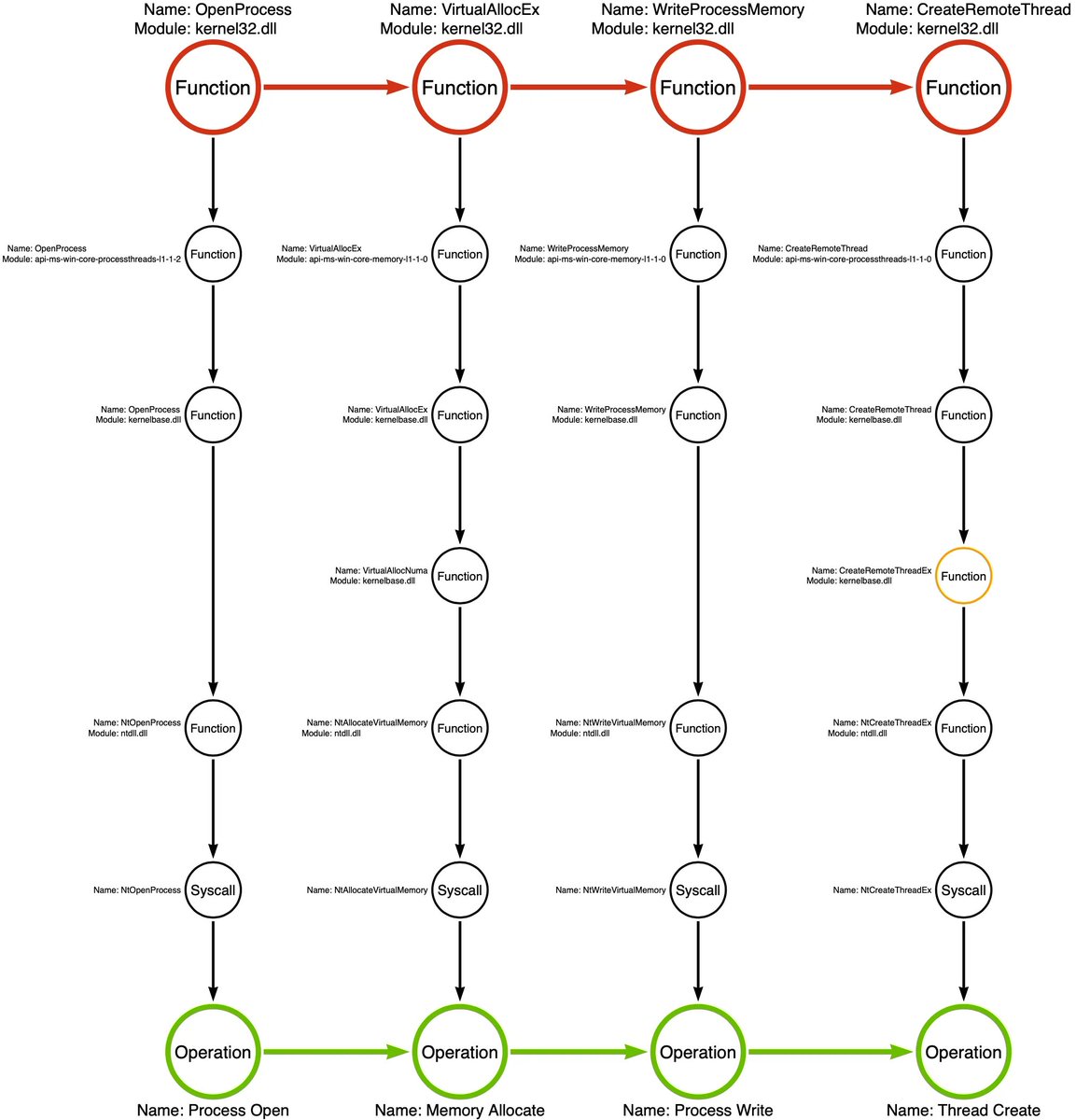
Join me this Thursday as I take a look at #security from a first principles perspective. Whether you’re a newcomer or a practiced professional, this talk will challenge some preconceived ideas about security, and attempt to strengthen your fundamental knowledge.
Ready to take your cybersecurity knowledge to the next level? Join us on Thurs., May 18 for a First Principles approach to understanding security. Register: ghst.ly/3LOVNMx

I've long been interested in how EDRs work under the hood and how we can apply a more evidence-based approach to evasion. I'm happy to announce that I've written a book covering these topics with @nostarch which is now available for preorder 🎉 nostarch.com/book-edr
United States Trends
- 1. Kentucky N/A
- 2. Arsenal N/A
- 3. Broncos N/A
- 4. Arteta N/A
- 5. Rick Barnes N/A
- 6. Jayda N/A
- 7. Martinelli N/A
- 8. The Jito N/A
- 9. Odegaard N/A
- 10. Jay Bilas N/A
- 11. Jake Lang N/A
- 12. Gillespie N/A
- 13. Go Bills N/A
- 14. Flyers N/A
- 15. Comeback Cats N/A
- 16. Georgetown N/A
- 17. #NFOARS N/A
- 18. Merino N/A
- 19. Mark Pope N/A
- 20. Mika N/A
Something went wrong.
Something went wrong.