Jacob Jackson
@psionicjake
Security hardening 🛡️| Making AD and Azure bulletproof 🕸️ | Computer nerd, security hobbyist, gamer, “I prefer to be called a hacker”
SCCM attack paths are messy until you can see them. 👀 ConfigManBearPig from @_Mayyhem extends BloodHound with SCCM nodes + edges using OpenGraph, plus queries to surface hierarchy takeovers and escalation paths. Check it out! ghst.ly/4svbcWO
Hi friends! I've finally written the third part of the Impacket Programming Guide! We explored several MSRPC protocols and also created our own tool for Lateral Movement! Read on medium: medium.com/@cicada-8/impa… POC: github.com/CICADA8-Resear…

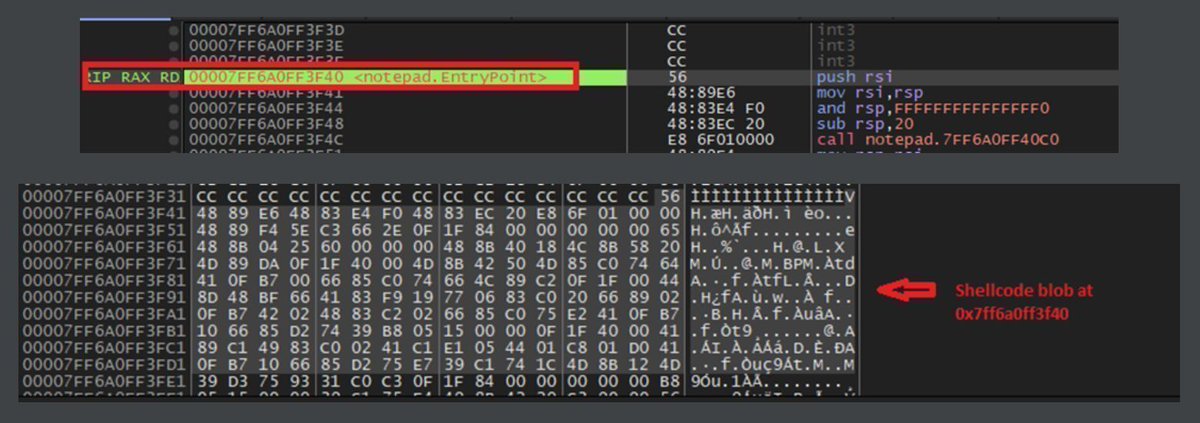
Leveraging program entry points for process injection in Windows (2023) bohops.com/2023/06/09/no-… Credits @bohops #infosec #Windows
SCOM is one of the most deployed, but least researched, System Center products. @synzack21 breaks down how it works + how to build a lab to test new tradecraft. ghst.ly/4prZMRI
A C# tool for requesting certificates from ADCS using DCOM over SMB. This tool allows you to remotely request X.509 certificates from CA server using the MS-WCCE protocol over DCOM and It bypasses the traditional endpoint mapper requirement by using SMB directly.…
Attackers don’t exploit tools—they exploit identities. Learn how to defend where it matters. Join operators and defenders for one of our hands-on training courses at #SOCON2026. In-person attendees also receive a free conference pass. Save your spot ➡️ ghst.ly/socon-2026

SCCM is one of the most relied-on enterprise tools, but that legacy comes with risk. Join @unsigned_sh0rt this Friday at #BSidesPDX as he discusses how attackers can abuse #SCCM Entra integrations to gain admin access. ➡️ ghst.ly/3L4nkwG

United States Trends
- 1. Dodgers N/A
- 2. #PowerForce N/A
- 3. Tariq N/A
- 4. #TheTraitorsUS N/A
- 5. Colton N/A
- 6. Mets N/A
- 7. Gabe Vincent N/A
- 8. #DONTBEDUMB N/A
- 9. Hornets N/A
- 10. World Series N/A
- 11. #TNAiMPACT N/A
- 12. Jenard N/A
- 13. Baseball N/A
- 14. Yankees N/A
- 15. Lamelo N/A
- 16. Nobel Peace Prize N/A
- 17. Ohtani N/A
- 18. Rocky N/A
- 19. Draymond N/A
- 20. LINGLING EUCERIN ASEAN PST N/A
Something went wrong.
Something went wrong.















![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)