Sprite
@Sprite970
锁推必BAN
Вам может понравиться
大企业不都是这样吗,美国大多数企业也是这样的policy
据内部人士爆料,快手研发线紧急限制Cursor、Claude Code等第三方编程工具使用,办公端直接闪退,仅特殊需求可申请严格审核。核心原因是防范内部代码、业务逻辑通过AI工具泄露。 你怎么看?
这东西怎么越看越像国内搞黑产的猫池…?
The Secret Service dismantled a network of more than 300 SIM servers and 100,000 SIM cards in the New York-area that were capable of crippling telecom systems and carrying out anonymous telephonic attacks, disrupting the threat before world leaders arrived for the UN General…



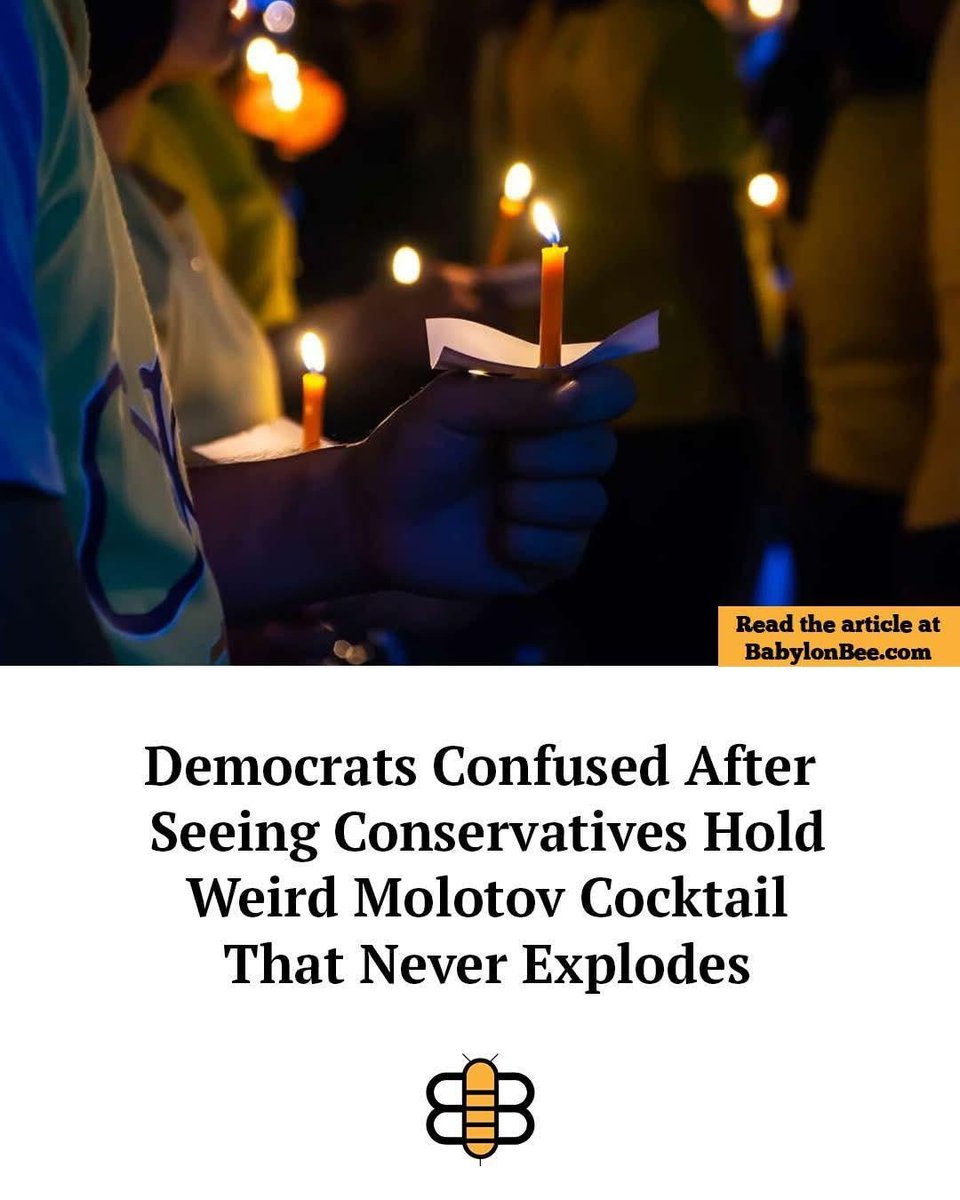
Babylon Bee ftw
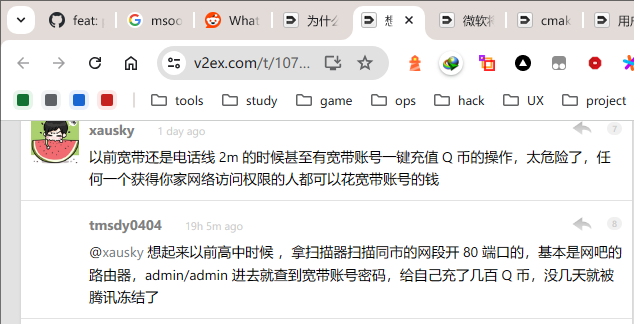
当年这些人为了盗刷QB不仅仅是用互联星空,好多孩子带着便携电话,带着鳄鱼夹子的那种到老小区一楼的交换箱盗打电话冲QB
这种行为是入侵+盗窃吧,V2EX还有人敢发出来炫耀 不过这也是中国👮很多时候都对于小偷小摸小骗等事情的不作为的结果
不是很理解, 猪肝红护照搞网络军火不是给自己找麻烦么?
What a 🤡
Update: Crowdstrike came out and released a technical report confirming my analysis. They were reading in a bad data file and attempting to access invalid memory. This global crash was a two-part bomb. The detonator apparently, was NOT new.. it was PRE-INSTALLED. /1
This is what hell looks like according to AI
同意。如果不是当年看到墨西哥讲话,我不可能把出国重新提上日程。
独立各服务+1 AIO的话,容易一台机器爆炸所有的服务全爆炸….
在一个独立开发者的交流群里,看到有人问,做好了 Chrome 插件,如何实现免费/付费的接入,他不想过于复杂地折腾 OAuth 登录和支付模块,在研究 Chrome 插件排行榜(extpose.com/top-grossing)的时候,恰好看到一个有趣的玩法: 1)在后端实现一个最简单的邮件注册和登录模块,用于记录用户付费状态…
I had an inquiry about ACPI checks, and decided to run through how they work and how to mitigate them on VMware and QEMU. It's a quick and dirty write-up, so excuse the brevity. revers.engineering/evading-trivia…
⛓️#BlackLotus bootkit illustrates how the UEFI ecosystem supply chain complexity negatively impacts the industry. EFI bootloader tricks from 10+ years ago still work over new Secure Boot bypasses (CVE-2022-21894). @TheWack0lian PoC: github.com/Wack0/CVE-2022…
#ESETResearch analyze first in-the-wild UEFI bootkit bypassing UEFI Secure Boot even on fully updated Windows 11 systems. Its functionality indicates it is the #BlackLotus UEFI bootkit, for sale on hacking forums since at least Oct 6, 2022. @smolar_m welivesecurity.com/2023/03/01/bla… 1/11
我是在自己内网里跑一个ESXi,然后把这些国产软件放到虚拟机里运行,如果需要访问桌面只需要3389登进去就好。
Patchguard: Detection of Hypervisor Based Instrospection co-authored with @nickeverdox revers.engineering/patchguard-det… revers.engineering/patchguard-det…
revers.engineering
Patchguard: Detection of Hypervisor Based Introspection [P2] - Reverse Engineering
No Errata For U! If you haven’t already, read Part 1 which outlines three neat tricks used by Patchguard. KiErrata420Present The LSTAR MSR can be intercepted using a hypervisor to trap on reads and...
Some crazy idiot did it! #w2k3builder v1 released! a virtual machine for debugging and building your own version of Windows 2003 (using leaked microsoft src). Batteries included. via @w2k3builder vimeo.com/759543579
Intel AlderLake Gen 12 (Desktop/Laptop) BIOS firmware leaked: * Tooling for tweaking BIOS images * Insyde's framework for customization (compatible with EDK2) * Intel reference code and OEM's implementation * Binary blobs: Intel CSME, ACMs (including the one for BootGuard)
垃圾国家
United States Тренды
- 1. Sinners N/A
- 2. Oscar N/A
- 3. Jack Smith N/A
- 4. FINALLY DID IT N/A
- 5. The REKT N/A
- 6. Best Picture N/A
- 7. Kate Hudson N/A
- 8. Delroy Lindo N/A
- 9. No Other Choice N/A
- 10. He-Man N/A
- 11. Jared Leto N/A
- 12. METLIFE N/A
- 13. #fancymedia N/A
- 14. Chase Infiniti N/A
- 15. Nekima Levy Armstrong N/A
- 16. #MountainOfBusch N/A
- 17. Wicked N/A
- 18. Jim Jordan N/A
- 19. Academy N/A
- 20. #BTS_ARIRANG N/A
Something went wrong.
Something went wrong.