Jean-Pierre LESUEUR
@DarkCoderSc
Security & Malware Researcher / Developer. Microsoft MVP 🇫🇷 🇵🇹 🇬🇧 Bluesky : darkcodersc
Anda mungkin suka
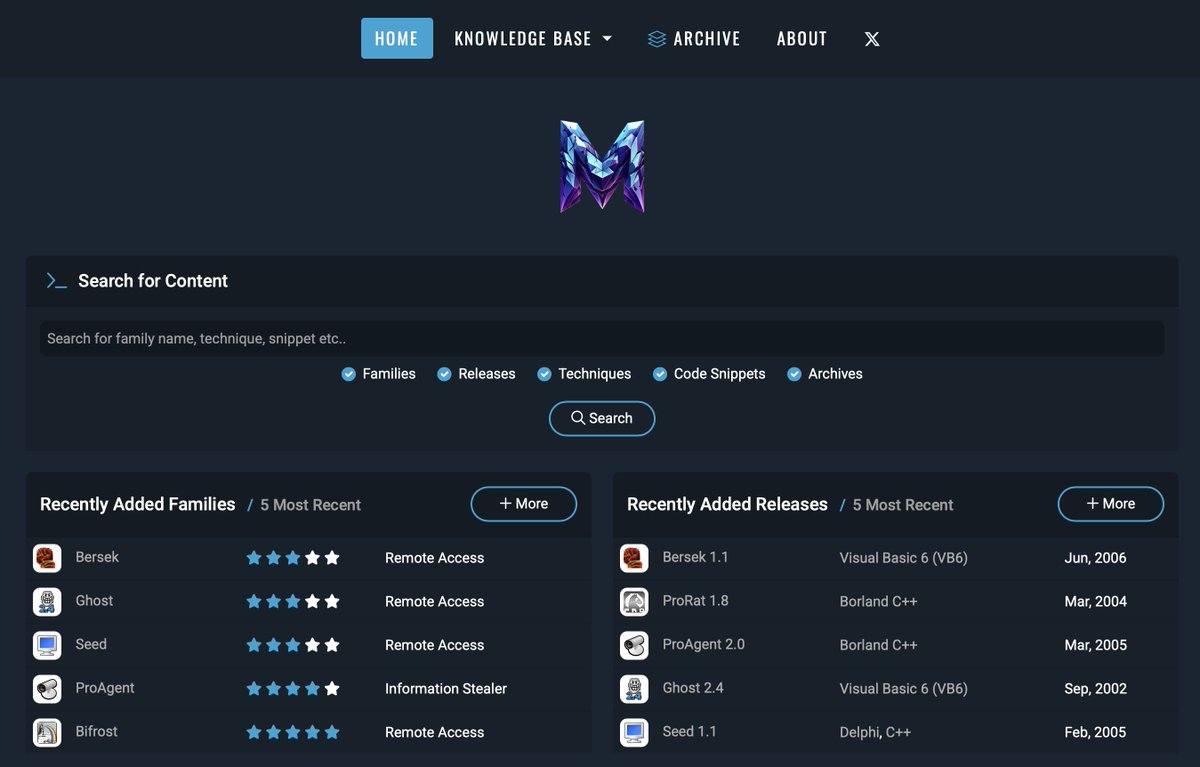
🚀You can now search for malware families, releases, techniques, and code snippets, including archives on Malware Gallery: malwaregallery.com #InfoSec #Malware #DFIR
Remember, for the "veterans" among us, when we used to call those piece of arts "Trojans" (even though it wasn’t always accurate)? With the support and blessing of MegaRat (creator of Mega Security, now back online), I've launched malwaregallery.com/archive , a full reconstruction…

Just received my copy of « Evasive Malware » by Kyle Cucci (@d4rksystem) @nostarch ! If you're looking to deepen your understanding of malware evasion techniques, this book is a must-read. Can’t wait to dive into every single page! #malware #infosec #offsec


🚀This is a significant milestone for Arcane: I've successfully captured the secure desktop (auto desktop switching from default to winlogon) without the need for a separate process or third-party tool. This achievement requires the Arcane Server to run as the SYSTEM user, which…
The first version of Arcane, formerly known as PowerRemoteDesktop is now available. For those unfamiliar with the project, Arcane is a fully functional remote desktop server for Windows, entirely written in PowerShell. I've now migrated the viewer/client to Python with a…

DLest v3.0 has been released with numerous new features, including performance improvements, process spy (for debugging processes and listening for DLL load events), a file hashing tool, anonymous export function enumeration and an improved filtering system. If you are not yet…

🌟Pleased to announce the release of the second part of my Understanding Malware Patching series! This time, we talk about Application Resources as a malicious vector. The lengthy article is accompanied by a bonus project that demonstrates how a threat actor could leverage…

👽 A new technique, named "FuncIn", has been integrated to #UnprotectProject, showcasing a sophisticated evasion technique with a working open-source demo. In short, FuncIn employs a payload staging strategy, diverging from the conventional method where all malicious…

In the past, our "Malware Retrospective" series has thrown light on some well-known Trojans like SubSeven and 👽 Beast, names that almost anyone in the Cyber Security field would recognize. However, today, we venture off the beaten path to look at a lesser-known yet highly…

🛸 Introducing "Malware Gallery" - A living museum of "trojan/malware's" most infamous masterpieces from past decades! Currently in BETA. The collection will grow over time (many) so stay tuned! Feedback & suggestions really appreciated! phrozen.io/malware-galler…

Best Malware author comment so far 🤣 - Quoted from SubSeven 2.2 source code.

Who remember or still use that old trick 😂 ?

🕵️Step into the world of #Malware history with my latest article! Uncover the secrets of #SubSeven, the game-changing Remote Access Trojan of the early 2000s. Hear from the elusive creator, Mobman, and discover how this software continues to inspire: darkcodersc.medium.com/a-malware-retr…

🛸👽 Interested in C2 over FTP(S)? Explore my new project, SharpFtpC2, which enables execution of shell commands on remote systems via FTP(S). Currently in beta and lacking encryption, but it's on the way: github.com/DarkCoderSc/Sh… #InfoSec #Malware #Network #Evasion #FTP

🚀 I just published the first article in my Malware retrospective series, kicking off with the notorious Beast RAT. Get ready for a deep dive into its history, impact, and legacy! Check it out here: medium.com/@darkcodersc/a… #Malware #InfoSec #cybersecurity #trojan

👽 Remember the infamous Beast Remote Access #Trojan from the early 2000s? I've recently had the privilege to talk with Tataye, its creator, to relive those thrilling times. Paper coming soon! In the meantime, explore the complete Beast 2.07 UI flowchart: phrozen.io/image/beast-20…

🌟 As requested, the #SubSeven Legacy service source code has been released to the official repository: github.com/DarkCoderSc/Su…. The project is now entirely open-source.
github.com
GitHub - DarkCoderSc/SubSeven: SubSeven Legacy Official Source Code Repository
SubSeven Legacy Official Source Code Repository. Contribute to DarkCoderSc/SubSeven development by creating an account on GitHub.
United States Tren
- 1. #UFC323 113K posts
- 2. Indiana 101K posts
- 3. Merab 37.9K posts
- 4. Mendoza 39.4K posts
- 5. Ohio State 61.3K posts
- 6. Roach 30.1K posts
- 7. Petr Yan 21.2K posts
- 8. Pantoja 32.8K posts
- 9. Bama 84.5K posts
- 10. Joshua Van 9,248 posts
- 11. Curt Cignetti 9,909 posts
- 12. Heisman 18.5K posts
- 13. Manny Diaz 2,737 posts
- 14. #iufb 8,245 posts
- 15. Miami 302K posts
- 16. The ACC 36.2K posts
- 17. Tulane 18.2K posts
- 18. Virginia 46.7K posts
- 19. Sayin 89.2K posts
- 20. Fielding 8,614 posts
Anda mungkin suka
-
 /r/netsec
/r/netsec
@_r_netsec -
 d1rkmtr
d1rkmtr
@d1rkmtr -
 Kuba Gretzky
Kuba Gretzky
@mrgretzky -
 Alice Climent
Alice Climent
@AliceCliment -
 Zero-Point Security
Zero-Point Security
@_ZeroPointSec -
 Swissky
Swissky
@pentest_swissky -
 an0n
an0n
@an0n_r0 -
 Kyle Cucci
Kyle Cucci
@d4rksystem -
 Josh
Josh
@passthehashbrwn -
 Outflank
Outflank
@OutflankNL -
 Ivan Kwiatkowski
Ivan Kwiatkowski
@JusticeRage -
 Thomas Roccia 🤘
Thomas Roccia 🤘
@fr0gger_ -
 BC Security
BC Security
@bcsecurity -
 Karsten Hahn
Karsten Hahn
@struppigel -
 SEKTOR7 Institute
SEKTOR7 Institute
@SEKTOR7net
Something went wrong.
Something went wrong.