Challenge: How to deploy browser adblocking company-wide without possibly hitting our own global properties, internal sites, or getting noticed by marketing? Push a uBlock Origin policy with Hroup Policy including a RegEx that disables it on domains with our company name.
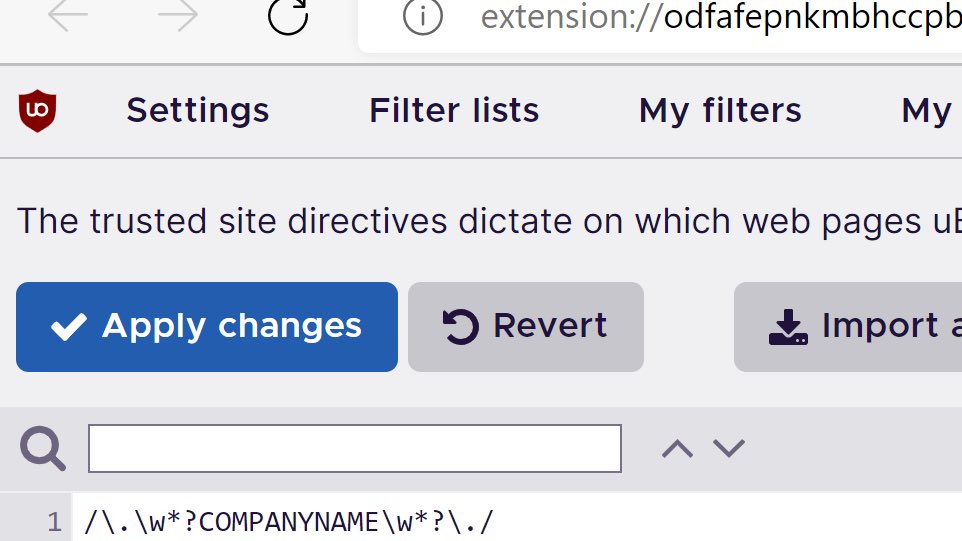
Adblocking is hyper-effective at quenching network threat alarms, massively reducing proxy log volume during threat investigations, and stopping users redirected to phishing and malware. Current corporate uBlock Origin configuration. I may move us to AdGuard instead of EasyList.

Yes I'm writing a blog on How We Do Browsers from top to bottom, but I use Twitter because I'm too impatient. I've been doing this for many many years and have even given feedback/bugs to the Chrome, Edge, and Firefox teams.
AS I WAS SAYING. If you have MDE/ATP and your SOC is getting deluged with alerts recently, it's because you don't have adblocking deployed to those machines yet. Adblocking STOPS THE BEGINNING OF THE ATTACK FROM EXISTING.
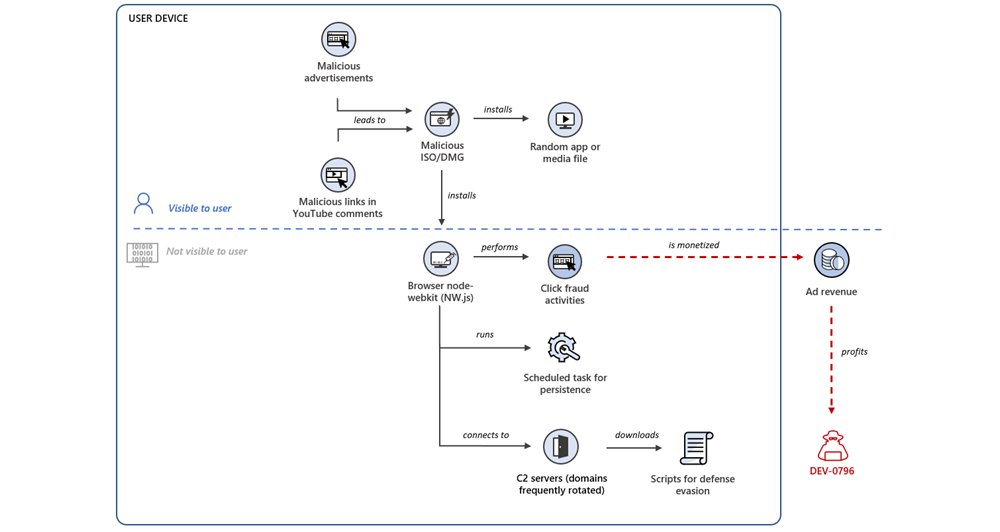
Microsoft researchers are tracking an ongoing wide-ranging click fraud campaign where attackers monetize clicks generated by a browser node-webkit or malicious browser extension secretly installed on devices. Microsoft attributes the attack to a threat actor tracked as DEV-0796.
I don't just make this shit up you know like I'm a human person with experiences and feelings.
Your users are getting these malicious advertising redirects and workflow captures, browsing local news sites. All the time.
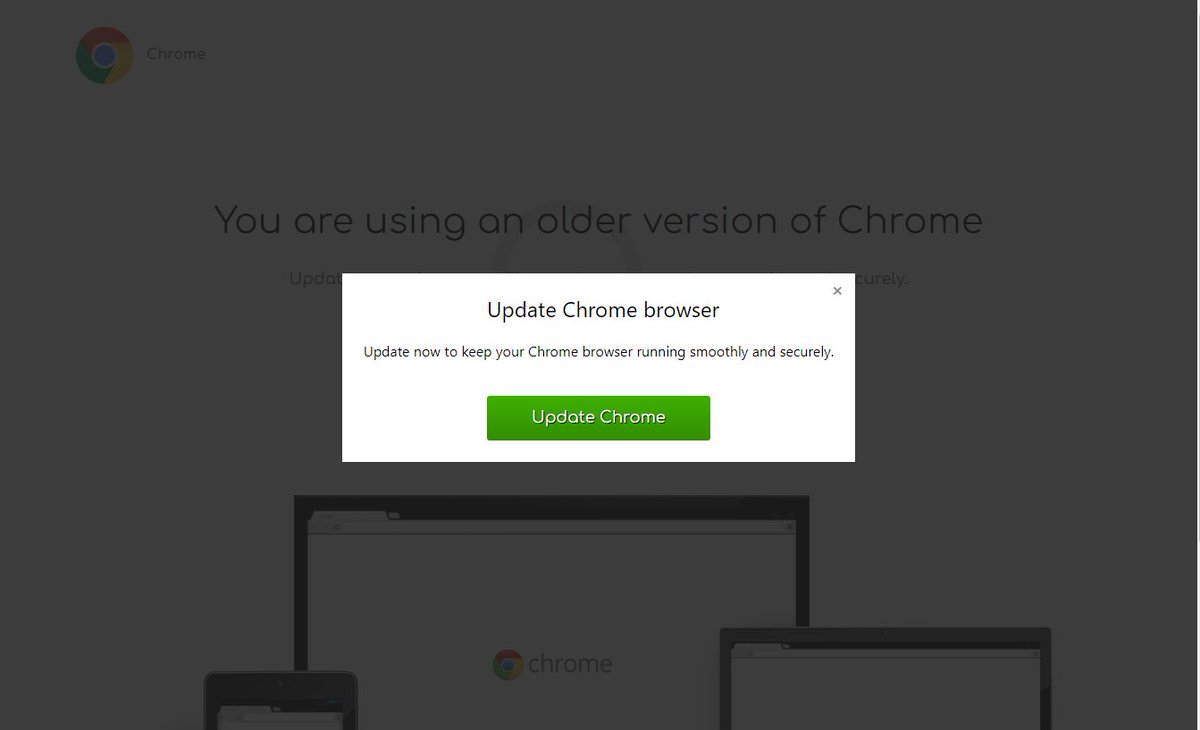
#SolarMarker pretending to be a chrome update. #Signed "Game Warriors Limited" tria.ge/220926-xqpq8sc… Back to PowerShell, file in the startup directory, PowerShell registry. C2: 146.70.53.146 Dropper: virustotal.com/gui/file/bb71d… Backdoor: virustotal.com/gui/file/db9dd… @JAMESWT_MHT

Note that uBO ships with a reduced version of AdGuard Base filter, it is supposed to be used with EasyList, not instead.
But browser level is so much more powerful and lets users fix broken websites
Am with you and have been wanting to put this to work, but it breaks several high profile sites here in Sweden while ordering goods and paying. Maybe related to our reliance on BankID for authentication, not sure yet.
I’m sending this over to our engineers that implement this who occasionally let me tag along.
i believe the adguard filters on ubo require a separate easylist (compared to their own addon) or something like that. could be wrong tho
Any reason you don't use the phishing URL block list, have you seen FPs there etc?
Firefox Android... Imported ones are: AdGuard Russian, AdGuard German, Disconnect malvertising
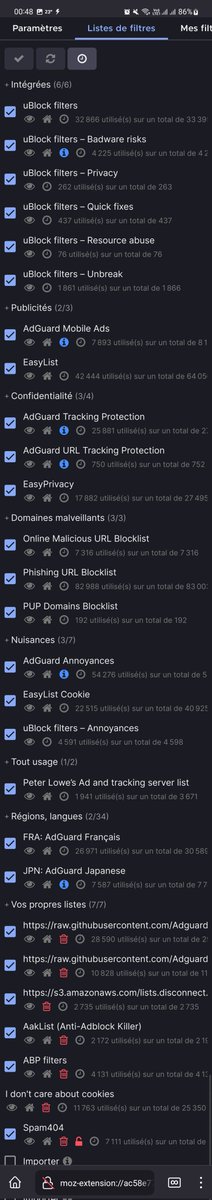
Why AdGuard? I use EasyList and no complaints yet
United States Trends
- 1. #GMMTV2026 1.83M posts
- 2. MILKLOVE BORN TO SHINE 302K posts
- 3. Good Tuesday 25.1K posts
- 4. WILLIAMEST MAGIC VIBES 46K posts
- 5. #tuesdayvibe 1,828 posts
- 6. Barcelona 153K posts
- 7. TOP CALL 9,410 posts
- 8. AI Alert 8,194 posts
- 9. Alan Dershowitz 2,983 posts
- 10. Barca 80.6K posts
- 11. Moe Odum N/A
- 12. Unforgiven 1,149 posts
- 13. Check Analyze 2,436 posts
- 14. Token Signal 8,610 posts
- 15. Brock 42.9K posts
- 16. Purdy 28.8K posts
- 17. Market Focus 4,661 posts
- 18. Enemy of the State 2,536 posts
- 19. Bryce 21.5K posts
- 20. Dialyn 8,299 posts
Something went wrong.
Something went wrong.











