Challenge: How to deploy browser adblocking company-wide without possibly hitting our own global properties, internal sites, or getting noticed by marketing? Push a uBlock Origin policy with Hroup Policy including a RegEx that disables it on domains with our company name.
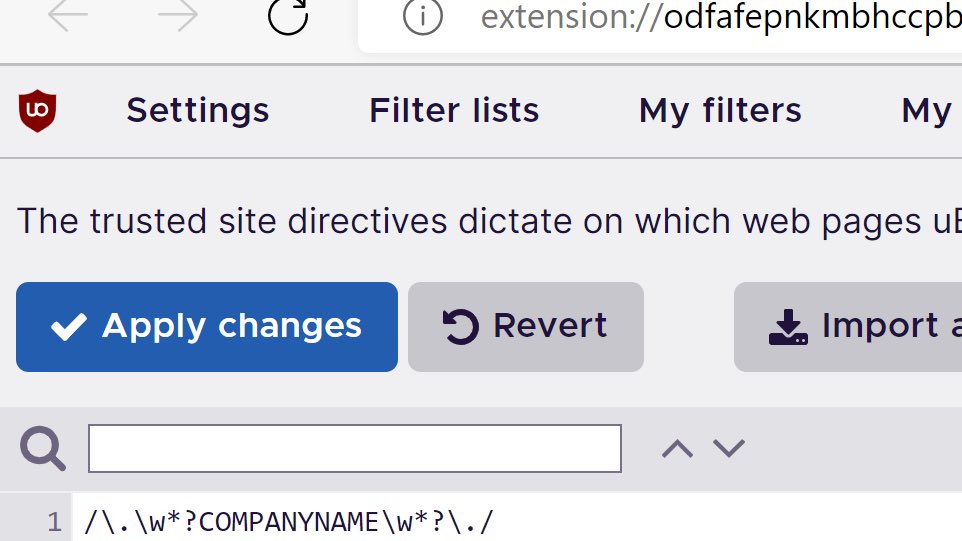
Adblocking is hyper-effective at quenching network threat alarms, massively reducing proxy log volume during threat investigations, and stopping users redirected to phishing and malware. Current corporate uBlock Origin configuration. I may move us to AdGuard instead of EasyList.

Yes I'm writing a blog on How We Do Browsers from top to bottom, but I use Twitter because I'm too impatient. I've been doing this for many many years and have even given feedback/bugs to the Chrome, Edge, and Firefox teams.
AS I WAS SAYING. If you have MDE/ATP and your SOC is getting deluged with alerts recently, it's because you don't have adblocking deployed to those machines yet. Adblocking STOPS THE BEGINNING OF THE ATTACK FROM EXISTING.
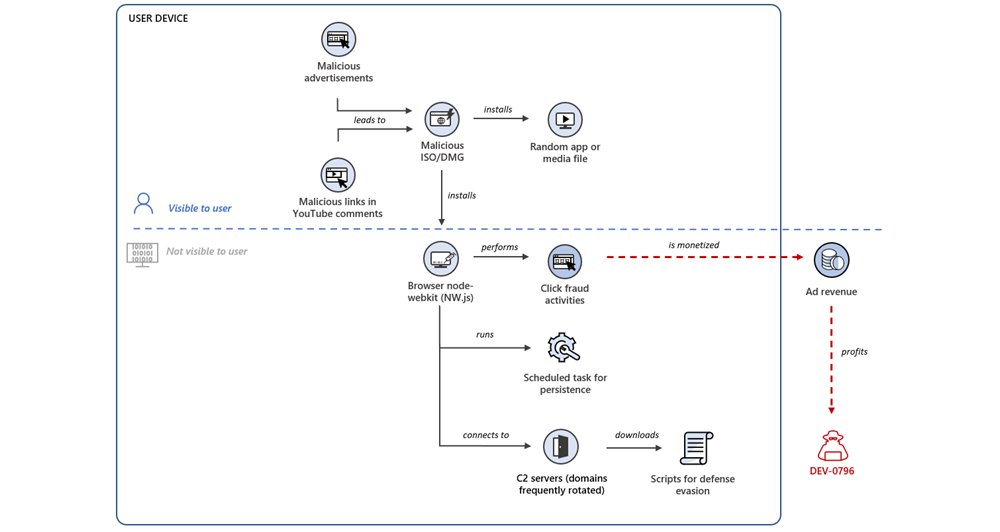
Microsoft researchers are tracking an ongoing wide-ranging click fraud campaign where attackers monetize clicks generated by a browser node-webkit or malicious browser extension secretly installed on devices. Microsoft attributes the attack to a threat actor tracked as DEV-0796.
I don't just make this shit up you know like I'm a human person with experiences and feelings.
Your users are getting these malicious advertising redirects and workflow captures, browsing local news sites. All the time.
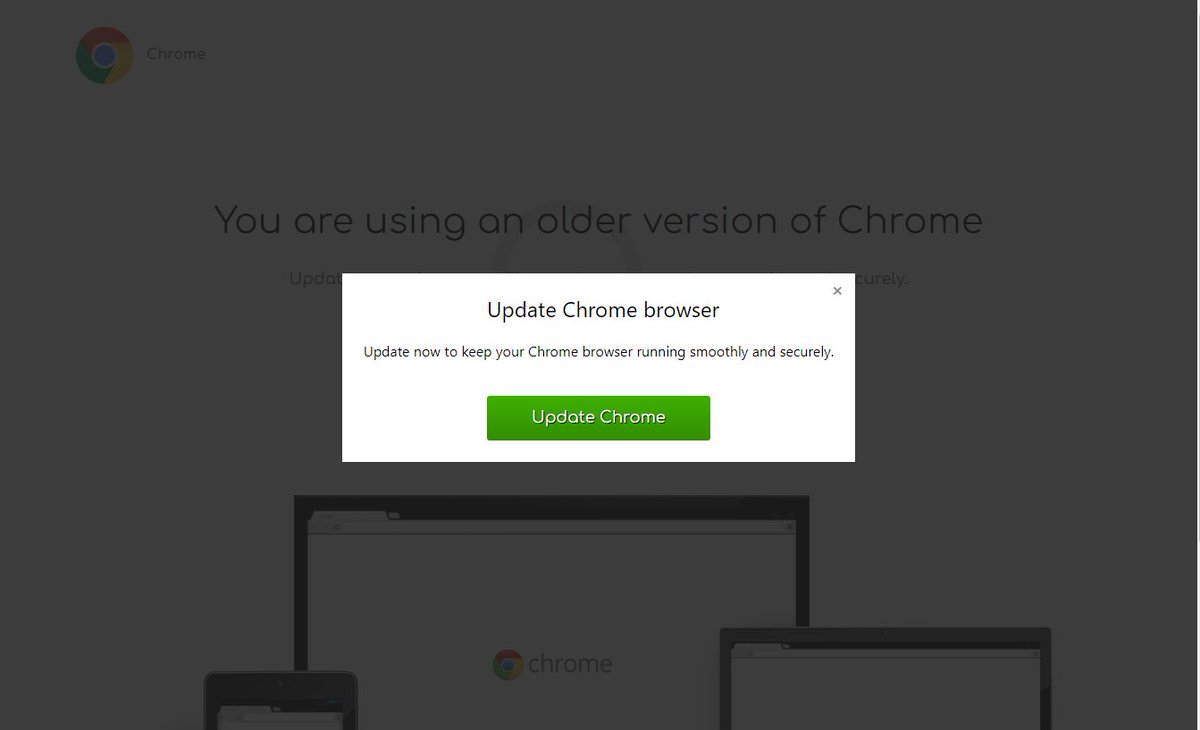
#SolarMarker pretending to be a chrome update. #Signed "Game Warriors Limited" tria.ge/220926-xqpq8sc… Back to PowerShell, file in the startup directory, PowerShell registry. C2: 146.70.53.146 Dropper: virustotal.com/gui/file/bb71d… Backdoor: virustotal.com/gui/file/db9dd… @JAMESWT_MHT

How are you handling news sites etc that require ads to work? I assume you get a lot of tickets at first?
Ublock origin allows you to disable it per site
can I ask what are you planning with the new manifest v3 changes knowing UBO may change significantly?
Seems like a targeted actor could use a domain containing the victims company name as part of the url?
United States Trends
- 1. Luka 56.8K posts
- 2. Lakers 43.7K posts
- 3. Clippers 16.6K posts
- 4. #DWTS 93K posts
- 5. #LakeShow 3,333 posts
- 6. Robert 131K posts
- 7. Kris Dunn 2,324 posts
- 8. Reaves 10K posts
- 9. Kawhi 5,779 posts
- 10. Jaxson Hayes 2,156 posts
- 11. Ty Lue 1,456 posts
- 12. Alix 14.9K posts
- 13. Elaine 45.7K posts
- 14. Jordan 116K posts
- 15. Collar 40.3K posts
- 16. Zubac 2,235 posts
- 17. Dylan 34.5K posts
- 18. NORMANI 6,050 posts
- 19. Colorado State 2,345 posts
- 20. Godzilla 36.3K posts
Something went wrong.
Something went wrong.








