Nathan Swift
@SwiftSolves
Somewhere between last GenX and first Millennial. Living in the Azure Cloud.
내가 좋아할 만한 콘텐츠
So there is this thing, it is called the theory of planned behavior. You start to predict an individual's intentions to engage in a behavior at a specific time and place. I don't know if you've been looking at your phones or looking at your screens but be careful with your info.
Our team at Microsoft are hiring in Australia & New Zealand! If you want to come work with some super smart people, solve some of the biggest cyber security problems in the world and talk about NBA with me on Teams, we would love to hear from you! jobs.careers.microsoft.com/global/en/job/…
Following the guidance in these two articles, you can detect two of the most common password attacks against Active Directory: 1. Detect Password Spraying using a Honeypot account: trustedsec.com/blog/detecting… 2. Detect Kerberoasting using a Honeypot account: adsecurity.org/?p=3513

Many commented that determining when a breach began depends on how long the victim retains its logs. That’s simply not true. Log data is just one piece of forensic evidence, and often not even the most reliable. Analysts can build timelines from dozens of other artifacts – file…
What really bothers me is that neither F5’s statement nor the attestation letters from NCC Group or IOActive mention when the breach actually happened. They only say that F5 “learned” about it in August 2025. That’s not when it started. There must be forensic evidence pointing…
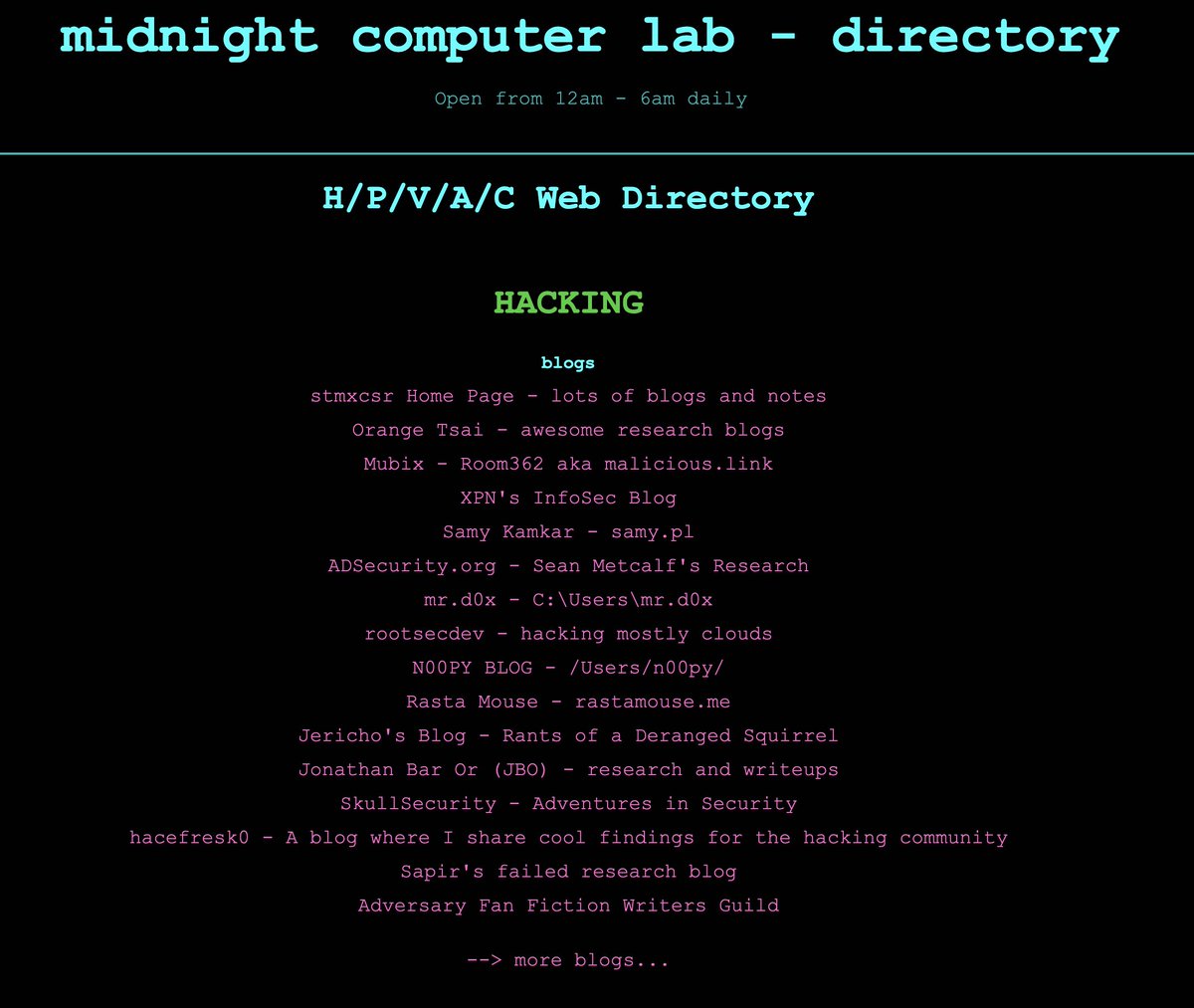
If you're needing some reading, I have a list of good hacker blogs here. midnightcomputerlab.net/directory/
Attacker infrastructure evolves in real time. Your defenses should too. Introducing GreyNoise Block, ensuring your blocklists update automatically. 🦾 greynoise.io/blog/introduci…
Grandfather Mountain, NC area today. Absolutely beautiful!

GreyNoise Feeds are here: real-time webhook alerts for CVE status changes, exploitation spikes, and IP classification changes. No more polling. Respond the moment threats emerge. 🦾 greynoise.io/blog/introduci…
What’s much more interesting to me than detecting vulnerable services from server responses is detecting exploited services from log files. Detecting services by server responses is useful, especially for red teams and anyone scanning their own network, but it’s only the first…
🚨 Critical zero-day tagged as CVE-2025-61882 (CVSS 9.8) affecting Oracle E-Business Suite I've created a vulnerability detection script here: github.com/rxerium/CVE-20… This vulnerability is remotely exploitable without authentication. Patches are available as per Oracle's…

Another day another fighting a website’s pointless AI chatbot like it’s a text-based RPG just to get a simple link.
For those of you who don’t know: I’m a native hillbilly from Haywood County. My background is littered with poverty and trauma. That includes watching my baby sister go into foster care after the death of my Daddy. Thankfully, one of her placements was at Black Mountain Home…
Help Black Mountain Home for children raise $350,000 with just a couple of clicks to vote for them for the @ChickfilA True inspiration award. Also Sharing and commenting on this is free!! Thank you guys! Share share share.
Your next team building exercise will be...
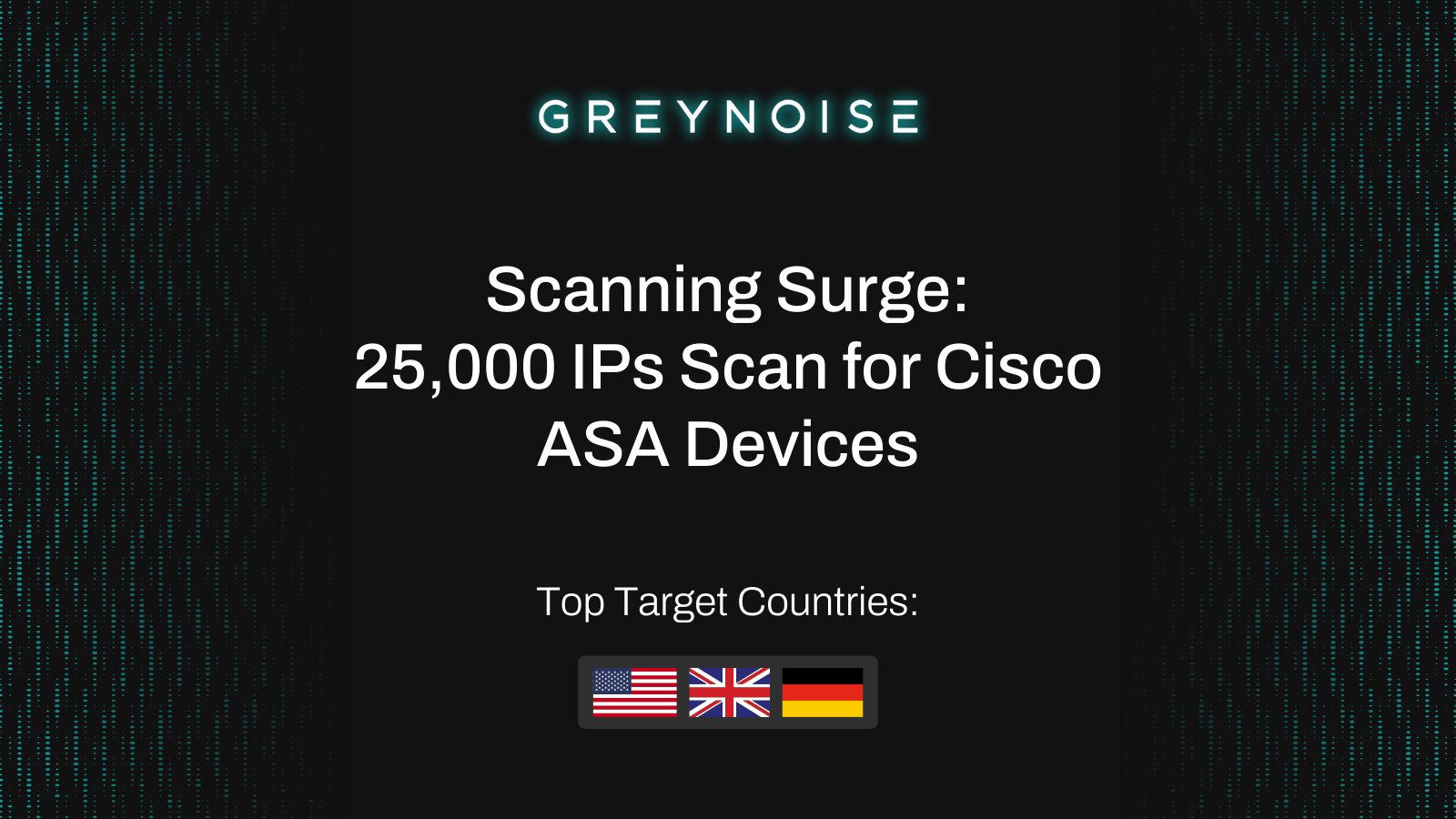
Sept 25: Cisco disclosed two ASA/FTD zero-days (#CVE-2025-20333, #CVE-2025-20362). Weeks earlier, GreyNoise saw 25k IPs scanning ASA — another case of recon surges preceding disclosures. Read the update: greynoise.io/blog/scanning-… #CiscoASA #ZeroDay #Cisco
tl;dr of today > @rastalandTV gets crypto drained > he has stage 4 cancer > hes targeted specifically for his cancer treatment money > loses $32,000 > nerds band together > @ZssBecker donates $30,000 to him > malware nerds come together > drainer infra found > pull all victim…
Want 4 hours of training on security roles and careers for a buck!?!? Join me for a half day training session at BSides St. Pete (near Tampa FL) on Friday October 3 bsides-st-pete.sessionize.com/schedule

Linn Cove Viaduct looking perty today. Ridge tops are starting to turn colorful. Still mostly green below.
Microsoft has removed the recommended vulnerable driver lists from its page and started providing them as XML/p7b files inside a ZIP. I've developed an automation that extracts, transforms, and stores the data as a CSV and JSON on a weekly basis. github.com/Cyb3r-Monk/Mic…
Folks, I'm super excited to announce a three part webinar series from Microsoft that involves some of your favorite folks from the Entra community. @NathanMcNulty and @rucam365 will be joining me and others from Microsoft to talk about implementing Zero Trust for identity and…

Here's a video guide for my scheduled Logic App to exclude emergency access accounts from Conditional Access! :) github.com/nathanmcnulty/… I mostly fixed my potato audio quality - OBS was capturing audio from both my microphone and the monitor output causing reverb/echo last time
I just update Mark's List (of Cybersecurity resources frequently sent to customers and colleagues) Share and Enjoy! aka.ms/markslist
United States 트렌드
- 1. Prince Andrew 17.6K posts
- 2. Duke of York 8,620 posts
- 3. No Kings 254K posts
- 4. zendaya 8,188 posts
- 5. Apple TV 11.9K posts
- 6. Zelensky 60.7K posts
- 7. trisha paytas 3,198 posts
- 8. Andrea Bocelli 12.7K posts
- 9. #FursuitFriday 16K posts
- 10. #DoritosF1 N/A
- 11. Arc Raiders 6,440 posts
- 12. #CashAppFriday N/A
- 13. #FridayVibes 9,219 posts
- 14. My President 53.7K posts
- 15. Karoline Leavitt 48.7K posts
- 16. $NXXT 1,524 posts
- 17. TPOT 20 SPOILERS 7,379 posts
- 18. F-bomb 1,177 posts
- 19. Trevon Diggs 1,324 posts
- 20. Shabbat Shalom 10.9K posts
내가 좋아할 만한 콘텐츠
Something went wrong.
Something went wrong.