
Nathan Swift
@SwiftSolves
Somewhere between last GenX and first Millennial. Living in the Azure Cloud.
Dit vind je misschien leuk
So there is this thing, it is called the theory of planned behavior. You start to predict an individual's intentions to engage in a behavior at a specific time and place. I don't know if you've been looking at your phones or looking at your screens but be careful with your info.
Since Sysmon is shipping with Windows 11 bump github.com/trustedsec/Sys…
github.com
GitHub - trustedsec/SysmonCommunityGuide: TrustedSec Sysinternals Sysmon Community Guide
TrustedSec Sysinternals Sysmon Community Guide. Contribute to trustedsec/SysmonCommunityGuide development by creating an account on GitHub.
In the Sandhills of NC, bees produce PURPLE honey. It’s the only place in the entire world where this happens. For my new followers…your Entomology lesson for the day.

CyberSec Trends Q4/25🔮 ⬆️NPM/PyPi/VSCode supply chain attacks ⬆️Rust/Go hack tools/malware ↗️EDR Blinding ↗️Abuse of legit RMM tools ↗️Token persistence/cloud API abuse ↗️Malicious LNK files ↗️.NET Single File Host ↗️ClickFix & FileFix ↗️Phishing w/ Job Ads
CyberSec Trends Q1/25🔮 ⬆️Lumma Stealer ↗️EDR killers (vulnerable drivers) ↗️Abuse of legit remote access tools ↗️0days in Fortinet & Ivanti ↗️Token persistence/cloud API abuse ⬆️Sliver implants ⬆️Fake CAPTCHA pages ⬆️Malvertising
Regular reminder… this hardening series by Jerry Devore is super awesome. There’s no way you won’t learn things by reading these. Part 1 - Disabling NTLMv1 Part 2 - Removing SMBv1 Part 3 - Enforcing LDAP Signing Part 4 - Enforcing AES for Kerberos Part 5 - Enforcing LDAP…
If you are curious about what kind of questions I ask when interviewing for my team, I thought I would share some examples. I usually cover everything identity, whether that is on premises Active Directory, Entra, OAuth and everything in between. In general, I try to ask…
A penetration tester got root access to our Kubernetes cluster in 15 minutes. Here's what they exploited. The attack chain: - Found exposed Kubernetes dashboard (our bad) - Dashboard had view-only service account (we thought this was safe) - Service account could list secrets…
The Tail of the Dragon is an 11 mile stretch of Highway 129. It begins near Robbinsville, NC and ends Tabcat Creek Bridge in Tennessee. It’s famous for its switchbacks without guardrails and sought out by sports car and motorcycle enthusiasts. ✌🏼

Good morning from North Carolina! 📍Tail of the Dragon

Why the Web was Down Today - Explained by a Retired Microsoft Engineer...
I wish there were a PowerShell module like Pandas. It could make a huge impact in DFIR and other areas.
10/17/2025: Every week I share a curated list of red team-specific jobs (or similar/adjacent) that caught my attention or were shared with me by others in the community. My goal is to help job hunters in the offensive security space find a red team-specific role. 🏛 Company +…

So true. I tell people this all the time - there are phases in your life where you just grind. Repetitive work, endless testing, boring tasks that feel redundant or pointless. But that’s where you’re forged. You don’t jump straight to the rewarding, visible, “interesting” stuff.…
“Greatness does not come out of intelligence, it comes from character. Character is not formed out of smart people: it is formed out of people who have suffered.” — Nvidia CEO, Jensen Huang
A small number of samples can poison LLMs of any size anthropic.com/research/small…

Our team at Microsoft are hiring in Australia & New Zealand! If you want to come work with some super smart people, solve some of the biggest cyber security problems in the world and talk about NBA with me on Teams, we would love to hear from you! jobs.careers.microsoft.com/global/en/job/…
Following the guidance in these two articles, you can detect two of the most common password attacks against Active Directory: 1. Detect Password Spraying using a Honeypot account: trustedsec.com/blog/detecting… 2. Detect Kerberoasting using a Honeypot account: adsecurity.org/?p=3513

Many commented that determining when a breach began depends on how long the victim retains its logs. That’s simply not true. Log data is just one piece of forensic evidence, and often not even the most reliable. Analysts can build timelines from dozens of other artifacts – file…
What really bothers me is that neither F5’s statement nor the attestation letters from NCC Group or IOActive mention when the breach actually happened. They only say that F5 “learned” about it in August 2025. That’s not when it started. There must be forensic evidence pointing…
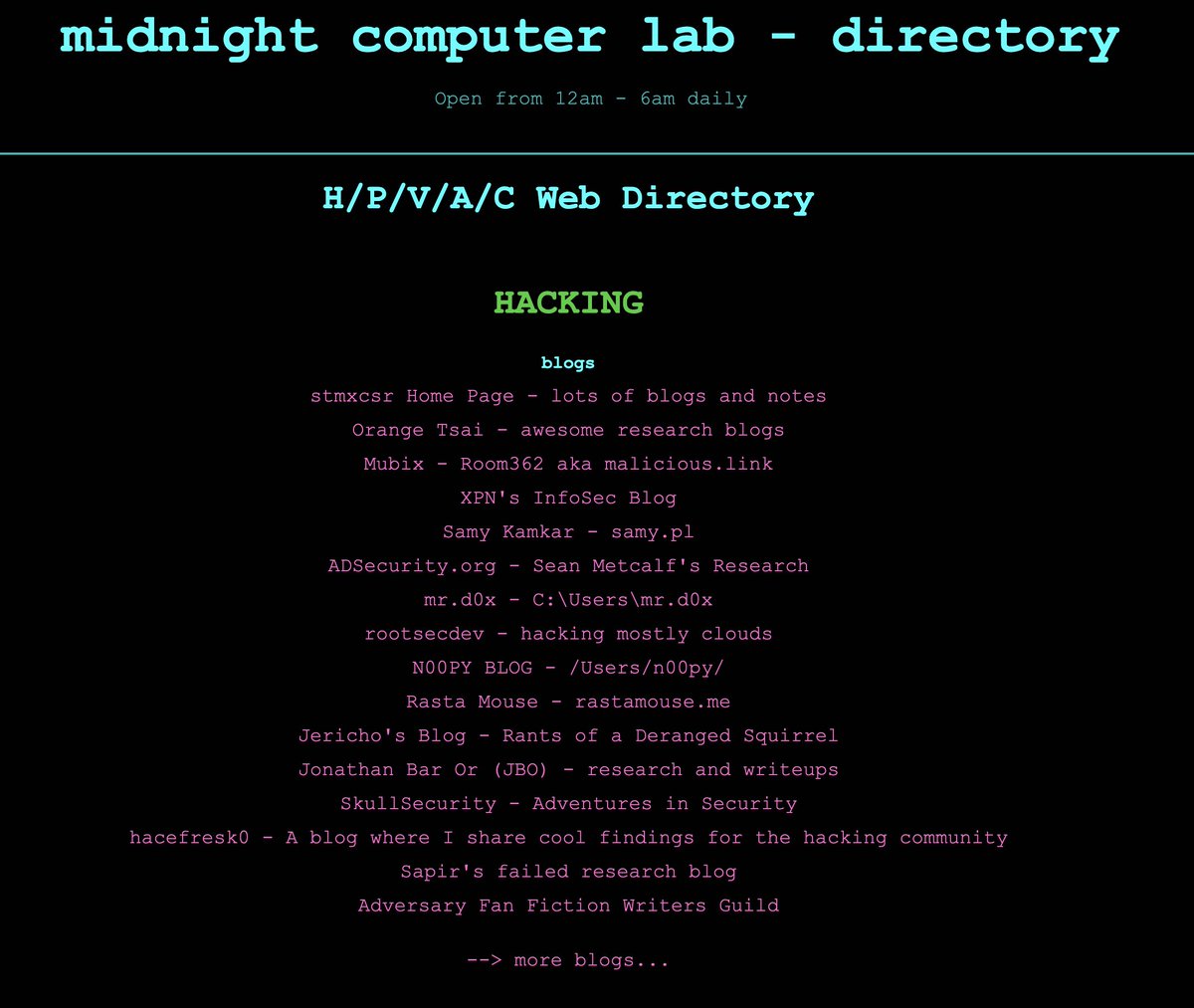
If you're needing some reading, I have a list of good hacker blogs here. midnightcomputerlab.net/directory/
Attacker infrastructure evolves in real time. Your defenses should too. Introducing GreyNoise Block, ensuring your blocklists update automatically. 🦾 greynoise.io/blog/introduci…
greynoise.io
Introducing GreyNoise Block: Fully configurable, real-time blocklists
Discover why traditional blocklists fail and how GreyNoise Block offers real-time, configurable, low-noise IP blocking powered by primary-sourced intelligence.
Grandfather Mountain, NC area today. Absolutely beautiful!

GreyNoise Feeds are here: real-time webhook alerts for CVE status changes, exploitation spikes, and IP classification changes. No more polling. Respond the moment threats emerge. 🦾 greynoise.io/blog/introduci…
greynoise.io
Introducing GreyNoise Feeds: Real-Time Intel for Real-Time Response
Learn how GreyNoise Feeds enable real-time, event-driven threat intelligence that eliminates polling delays—helping defenders react instantly to new exploits, IP threats, and zero-day activity.
United States Trends
- 1. Josh Allen 36.7K posts
- 2. Texans 57.5K posts
- 3. Bills 152K posts
- 4. Joe Brady 5,166 posts
- 5. #MissUniverse 407K posts
- 6. #MissUniverse 407K posts
- 7. Anderson 27.8K posts
- 8. McDermott 4,527 posts
- 9. Troy 12.4K posts
- 10. Maxey 12.6K posts
- 11. #TNFonPrime 3,680 posts
- 12. #StrayKids_DO_IT_OutNow 46K posts
- 13. Cooper Campbell N/A
- 14. Al Michaels N/A
- 15. Dion Dawkins N/A
- 16. Costa de Marfil 24.4K posts
- 17. Shakir 5,645 posts
- 18. #htownmade 3,835 posts
- 19. STRAY KIDS DO IT IS DIVINE 47.7K posts
- 20. Stroud 3,521 posts
Something went wrong.
Something went wrong.





















































































































































